Another vlan w/o network access issue
-
I swear I have watched about every darn video and googled the junk out of this but I just can't figure it out. On my main box/home firewall I have this problem where sometimes it works, sometimes not until I reboot, sometimes after the reboot the vlan works but others stop. Everything works fine on the main LAN, but I can't get the vlans to work consistently... So I reproduced it on a physical box and small managed switch in my home lab with the same results.
Create vlans
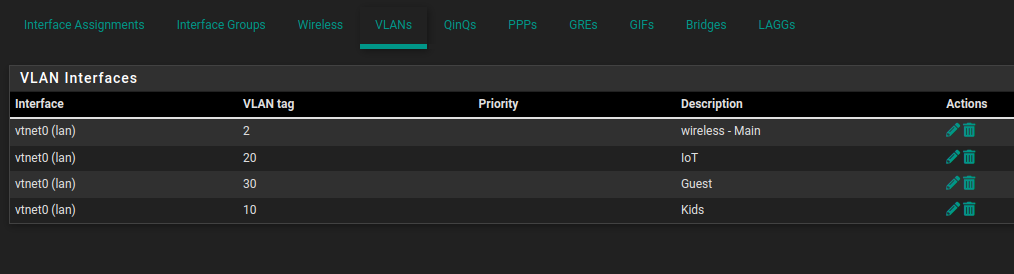
Set up interfaces
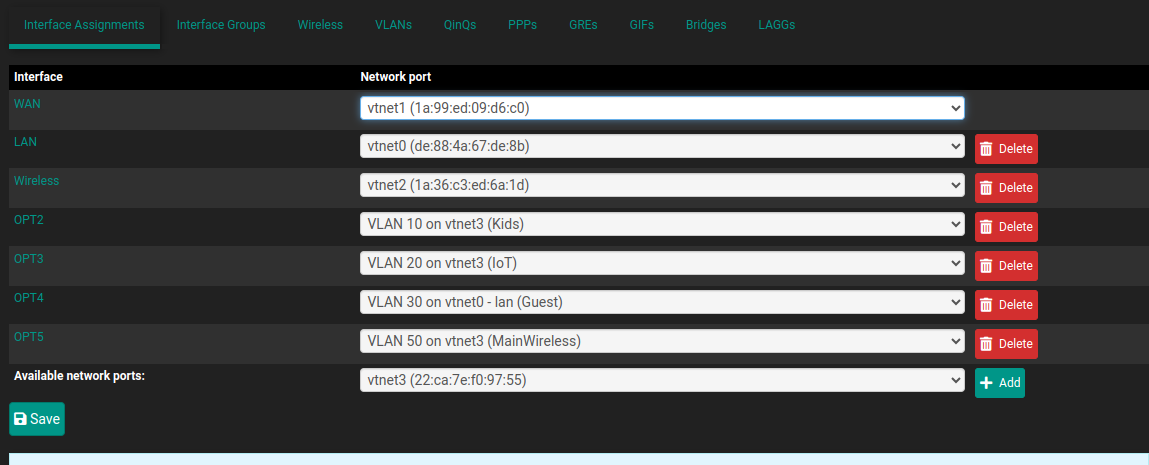
Set up DHCP on the vlan
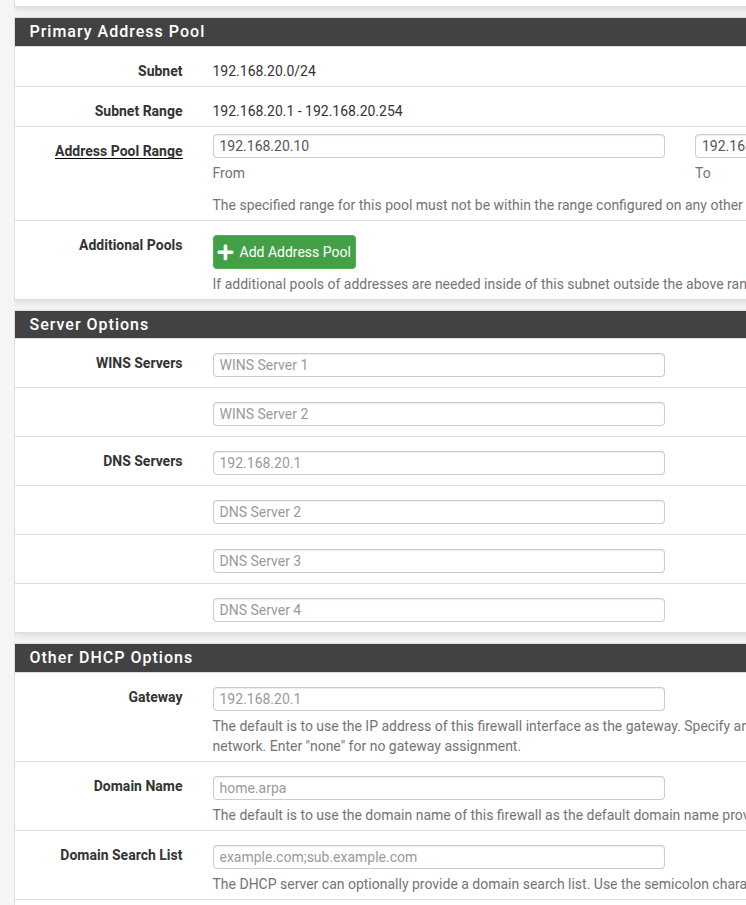
Set up the firewall wide open (for now)
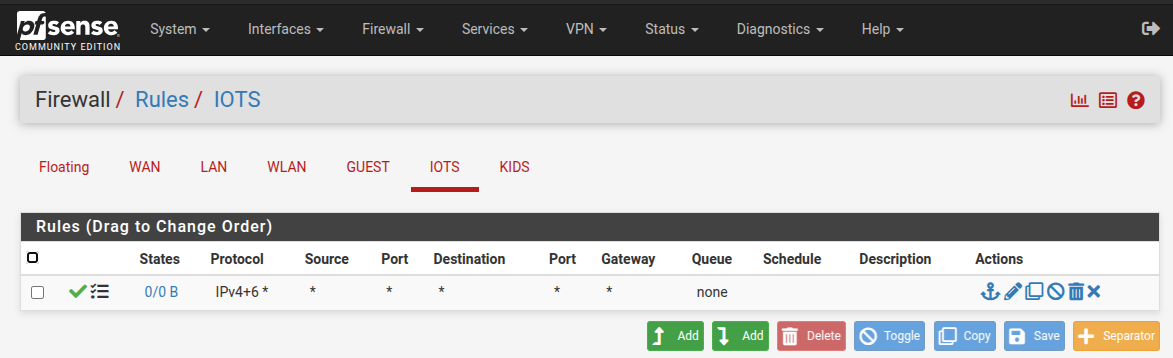
Tag my ports
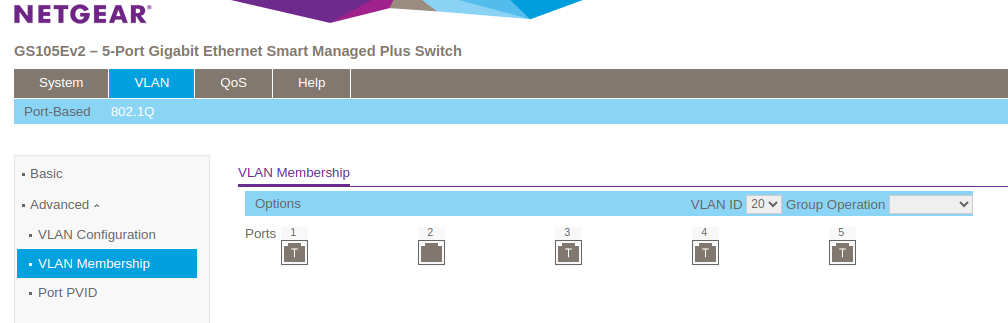
Assign those ports to vlans to test each one
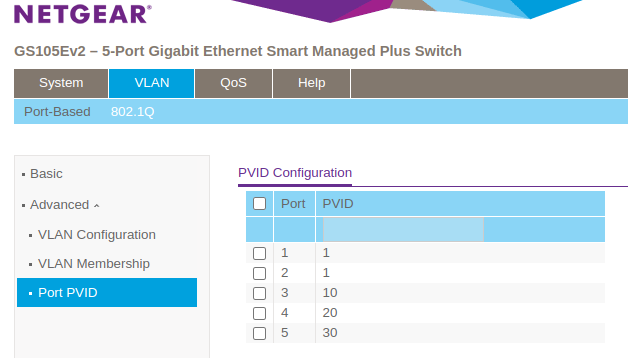
Plug my machine into port 4 on the switch for the IoT vlan (other act the same) and I get the appropreate IP
But can't get out
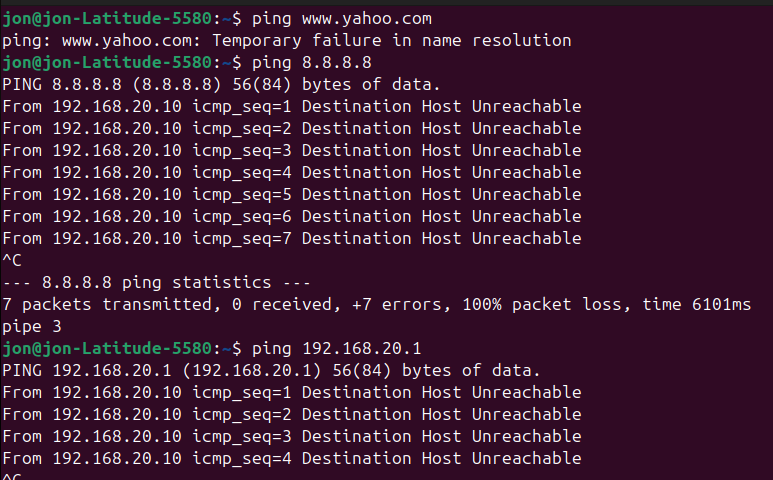
I swear I did all the right things. Thoughts?
-
@masonje the screenshots seem to be from different installations and stages (and not from the phyisical box)?
In the first all the VLANs are on vtnet0, then in the second VLAN10 & 20 are on vtnet3 and VLAN30 is on vtnet0 and Wireless is on it's own interface vtnet2. Then in the firewall rules the before named IOT/IoT is now IOTS.Would you mind posting the actual screenshots from one installation that showed the issue?
After that we probably need more screenshots of the switch VLAN configuration (VLAN Configuration & VLAN Membership)
-
@patient0 Just to add, vtnet3 is also listed as an available interface. Meaning it's not even being used.
-
I have an edit but this web site's edit policy isn't letting me get it in. Here's what I want to put.
I swear I have watched about every darn video and googled the junk out of this but I just can't figure it out. On my main box/home firewall I have this problem where sometimes it works, sometimes not until I reboot, sometimes after the reboot the vlan works but others stop. Everything works fine on the main LAN, but I can't get the vlans to work consistently... So I reproduced it on a physical box and small managed switch in my home lab with the same results.
Create vlans
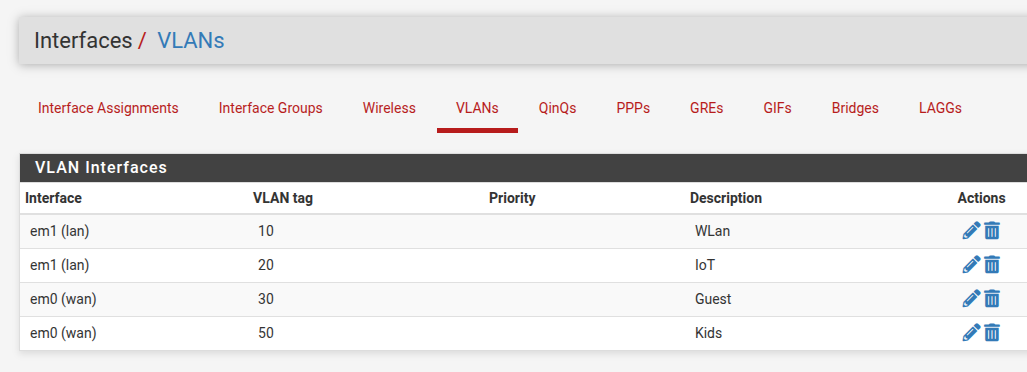
Set up interfaces
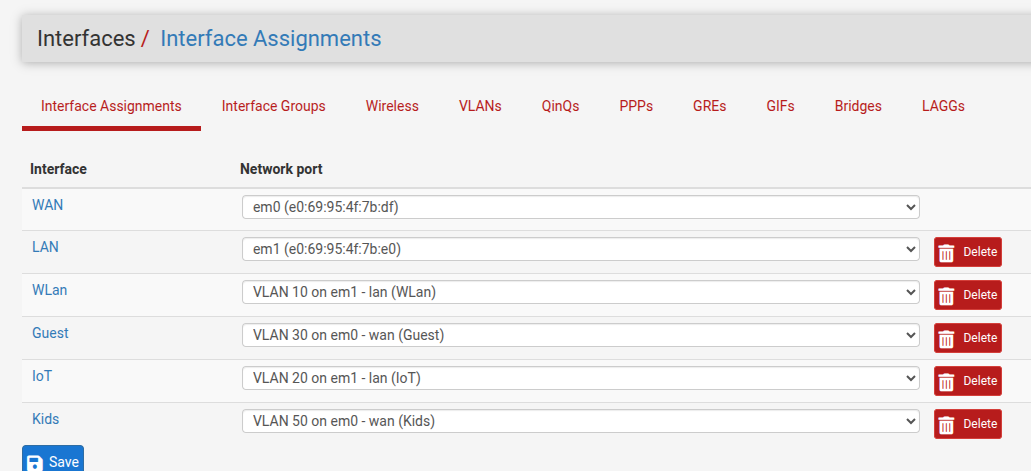
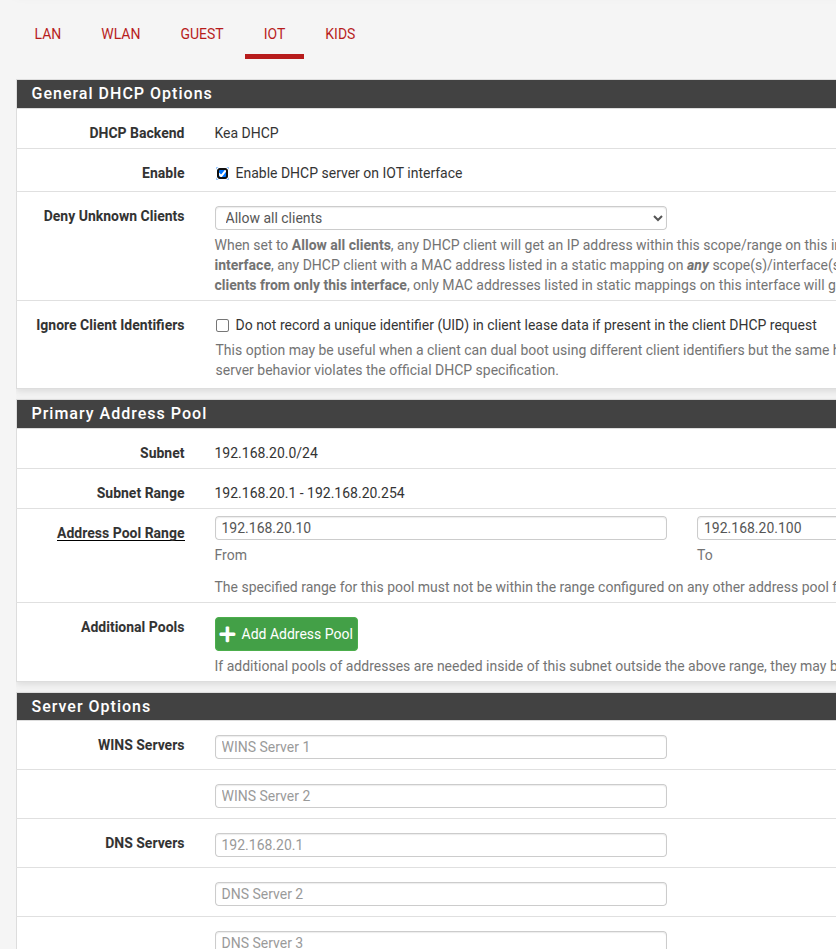
Set up DHCP on the vlan
Set up the firewall wide open (for now)
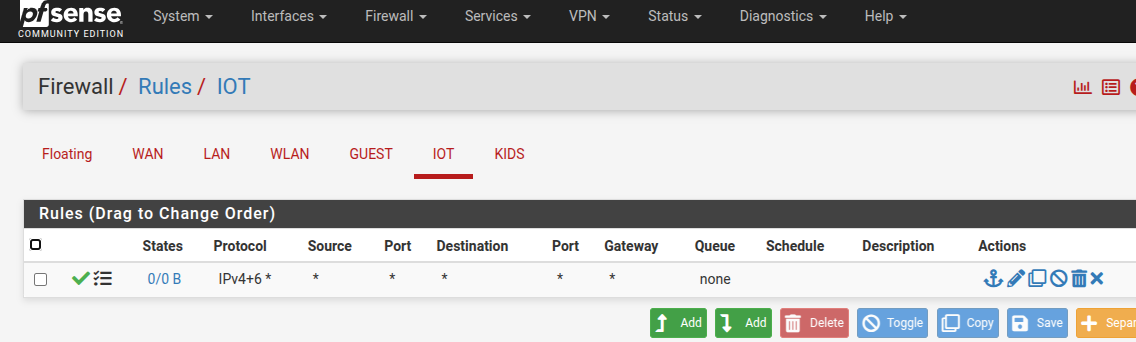
Tag my ports. Pfsense plugged into port 1. Working off of port 2 with my laptop (vlan1) but working with test laptop on port 4 for IoT network.

Assign those ports to vlans to test each one

Plug my machine into port 4 on the switch for the IoT vlan (other act the same) and I get the appropreate IP

But can't get out

I swear I did all the right things. Thoughts?
I've updated the screenshots/notes. The other screen shots were from when I started this thread and was going to report my proxmox/pfsense setup, but decided to try this physical box and getting the same results.
-
@masonje A few things that I think of looking at your pictures are:
VLAN Membership (Netgear UI) : Ports 3, 4 and 5 should be showing a U (Untagged) unless you are connecting to some other managed switch. Or possibly Proxmox in order to have different VM's in different VLANs.
Also, you are not showing the VLAN Configuration tab, so not sure if that is correct. But each VLAN ID needs to have both ports 1 and 3, 4 or 5 respectively, as members. So ID 20 has ports 1 and 4 as Members, ID 10 has 1 and 3 etc.
Finally, you seem to have placed Guest and Kids VLAN on the WAN parent interface, that can't be intentional? They should all be living off the LAN right?
-
@masonje pfSense-wise IoT seems ok, why you put VLAN 30 (Guest) and 50 (Kids) onto the WAN interface, only you can know.
You wouldn't tag port 4 on the Netgear switch if you want to have VLAN20 to leave port 4 untagged. If you set PVID to 20 on port 4, all the untagged traffic that flows into that port will be tagged with VLAN20.
Edit: Gblenn beat me to it
-
On your trunk between switch and pfsense...
The default vlan (usuaĺly pvid 1) should be untagged, alle others tagged.
On switch ports connected to a client, vlan x goes untagged.
Seems you have that wrong in your screenshot.Why is your interface WAN for guest and kids vlan???
-
@masonje
In addition to above:
Don't use KEA DHCP. Just gonna give you problems until it's ready for release.
Did you enable the DNS resolver on all interfaces? -
@Gblenn Yea I messed up on the guest and kids vlans, but I wasn't focusing on those. Mainly just 20 but good eye. Fixed.
Here is the over all configuration. From what I know/told it doesn't matter totally on untagged part. Important part for this is the PVID and it forces that poart to that vlan.
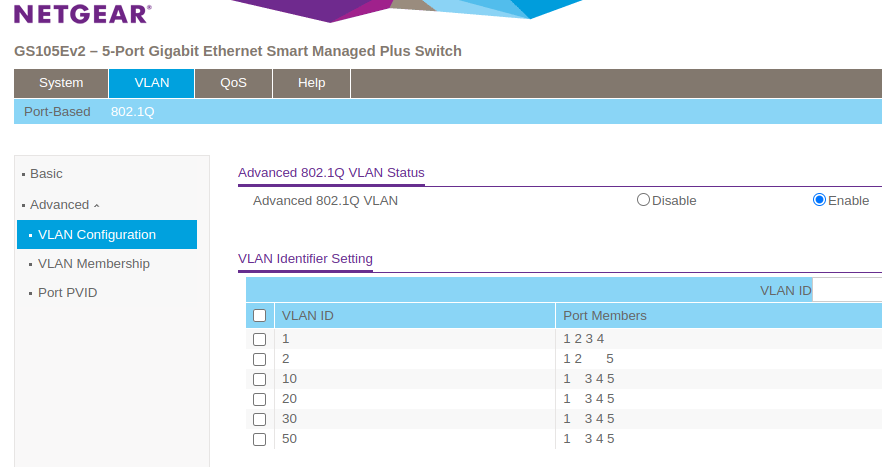
-
@masonje it does matter if you tag a port or not. If you want port 4 to act as a VLAN20 access port (untagged traffic entering port 4 to be tagged with VLAN20) you have to set port 4 in the 'Port PVID' as untagged and (leave) the PVID as 20.
-
@patient0 Well there you go.... That was the fix.
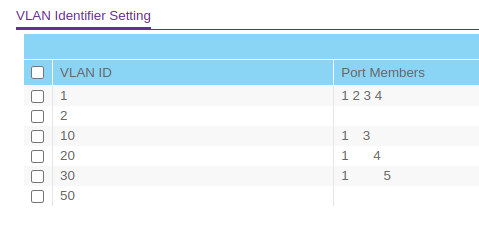

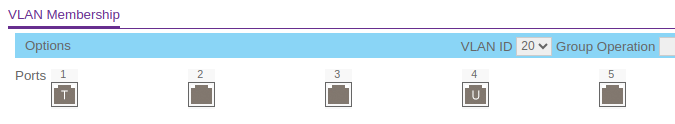
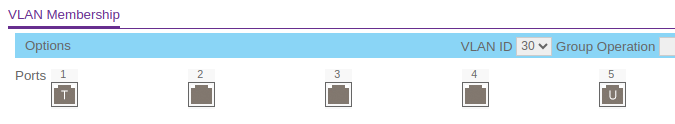
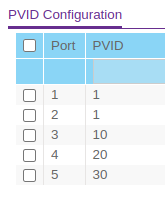
I guess where I confused is why. Why did I get an IP address before, but couldn't get out?
-
@masonje said in Another vlan w/o network access issue:
I guess where I confused is why. Why did I get an IP address before, but couldn't get out?
I agree it's odd that DHCP worked, unfortunately I'm not knowledgable enough to answer that.
The DHCP client sends out a DHCPDISCOVER broadcast via UDP. Sending should work since PVID on port 4 was set to 20, the request was tagged for VLAN20. How the answer from pfSense made it back, I don't know.
The answer is tagged with VLAN20 by pfSense but on the switch the packet get's to port 4 which was set to (T)ag. I'd assume that the tagged packet would reach your client with the packet still tagged as VLAN20. And your client would drop it since he is not configured to handle VLAN20 tagged traffic. But the Netgear does handle it different it seems.
Well, lots of words just to say: "I don't really know". Maybe someone with more inside can answer it.
-
@patient0 said in Another vlan w/o network access issue:
@masonje said in Another vlan w/o network access issue:
I guess where I confused is why. Why did I get an IP address before, but couldn't get out?
I agree it's odd that DHCP worked, unfortunately I'm not knowledgable enough to answer that.
The DHCP client sends out a DHCPDISCOVER broadcast via UDP. Sending should work since PVID on port 4 was set to 20, the request was tagged for VLAN20. How the answer from pfSense made it back, I don't know.
I suppose it's not so much that the answer made it back, but rather the fact that the device actually picked it up, even though it was tagged.
My understanding is that many (most?) NICs are designed to accept both tagged and untagged DHCP responses. And DHCP broadcast, response and ack goes on in layer 2, which is before VLAN is involved... -
It's always Netgear. Their VLAN configuration is always a PITA. Ran into almost the exact issue today.
-
@algo7 said in Another vlan w/o network access issue:
It's always Netgear. Their VLAN configuration is always a PITA. Ran into almost the exact issue today.
What issue? There was nothing wrong with Netgear, just the port assignments...