Open VPN no longer working after certificate reissue
-
Hello, our VPN is no longer working after I had to reissue the certificates.
Wed Feb 12 10:56:06 2025 VERIFY ERROR: depth=1, error=self signed certificate in certificate chain: CN= OPENVPN_CA, C=AU, ST=XXX, L=XXX, O=XXX, serial=8977035700566280363
Wed Feb 12 10:56:06 2025 OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
Wed Feb 12 10:56:06 2025 TLS_ERROR: BIO read tls_read_plaintext error
Wed Feb 12 10:56:06 2025 TLS Error: TLS object -> incoming plaintext read error
Wed Feb 12 10:56:06 2025 TLS Error: TLS handshake failed
Wed Feb 12 10:56:06 2025 SIGUSR1[soft,tls-error] received, process restarting
Wed Feb 12 10:56:08 2025 SIGTERM[hard,init_instance] received, process exitingI downloaded a new install and when doing so I just get a time out error.
Wed Feb 12 10:59:11 2025 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Wed Feb 12 10:59:11 2025 TLS Error: TLS handshake failed
Wed Feb 12 10:59:11 2025 SIGUSR1[soft,tls-error] received, process restarting
Wed Feb 12 10:59:14 2025 SIGTERM[hard,init_instance] received, process exitingI have read that you need to restart services to get this to work, but also read that you don't, can anyone help me with this?
-
These are the errors from the OpenVPN Logs
Feb 11 14:35:06 openvpn 24417 138.217.235.34:52939 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Feb 11 14:35:06 openvpn 24417 138.217.235.34:52939 TLS Error: TLS handshake failed
Feb 11 14:38:40 openvpn 24417 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]199.195.248.205:36771
Feb 11 14:38:40 openvpn 24417 TLS Error: cannot locate HMAC in incoming packet from [AF_INET]199.195.248.205:36772
Feb 11 14:40:07 openvpn 24417 138.217.235.34:57083 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) -
@Aenimma said in Open VPN no longer working after certificate reissue:
our VPN is no longer working after I had to reissue the certificates.
That was step one.
Step 2 : re create for every OpenVPN an new "ovpn" file, to be imported by every OpenVPN user - you've done that ?
Remember : if you change secret password (certificate, whatever) on one side, the 'using' other side has to know about it

Otherwise, as the your logs is telling you : they try but can't access the server anymore.And now you tell us you have hundreds or more VPN clients ... ^^
Now you know why the OpenVPN server certificate and everything related to it should be set up with a max life time, if possible. -
Hello thanks for the reply.
I have downloaded a new installer for the users and when I use that the OPENVPN times out and gives me an error message saying that it timed out.
Wed Feb 12 10:59:11 2025 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Wed Feb 12 10:59:11 2025 TLS Error: TLS handshake failed
Wed Feb 12 10:59:11 2025 SIGUSR1[soft,tls-error] received, process restarting
Wed Feb 12 10:59:14 2025 SIGTERM[hard,init_instance] received, process exitingI have not changed any passwords or done anything to the system other than "reissue certificate"
-
This :
@Aenimma said in Open VPN no longer working after certificate reissue:
Wed Feb 12 10:59:11 2025 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Wed Feb 12 10:59:11 2025 TLS Error: TLS handshake failed
Wed Feb 12 10:59:11 2025 SIGUSR1[soft,tls-error] received, process restarting
Wed Feb 12 10:59:14 2025 SIGTERM[hard,init_instance] received, process exitingis the log from the client side ?
The log should also show the IP it want to connect to. That IP must be your pfSense WAN IP.
If it is the WAN IP, you can then look at the OpenVPN server at the same moment, and see the connection being negotiated. The IP shown in the server logs should be the IP of the client connecting.
Is this all the case ? -
Hello,
This is the client side error I am getting now
Wed Feb 12 10:59:11 2025 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Wed Feb 12 10:59:11 2025 TLS Error: TLS handshake failed
Wed Feb 12 10:59:11 2025 SIGUSR1[soft,tls-error] received, process restarting
Wed Feb 12 10:59:14 2025 SIGTERM[hard,init_instance] received, process exitingThis is the server side error I am getting now
Feb 11 19:51:17 openvpn 20340 59.100.162.219:5292 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Feb 11 19:51:17 openvpn 20340 59.100.162.219:5292 TLS_ERROR: BIO read tls_read_plaintext error
Feb 11 19:51:17 openvpn 20340 59.100.162.219:5292 TLS Error: TLS object -> incoming plaintext read error
Feb 11 19:51:17 openvpn 20340 59.100.162.219:5292 TLS Error: TLS handshake failed
Feb 11 19:57:18 openvpn 20340 59.100.162.219:24217 VERIFY ERROR: depth=0, error=unable to get local issuer certificate: C=AU, ST=Queensland, L=Southport, O=EDMO, CN=murry, serial=7Also the OpenVPN was working fine 2 weeks ago. This has all stopped as the certificates expired. I have just clicked on Reissue Certificates in the system and re-installed the OpenVPN client once more on the end used
-
Ok for the log lines, but your listing a time stamp of
...Feb 12 10:59:11
for the client and
Feb 11 19:51:17
for the server.Hence the lines are not related, even if the 'look' the same.
Did you saw this :
@Gertjan said in Open VPN no longer working after certificate reissue:
The log should also show the IP it want to connect to. That IP must be your pfSense WAN IP.
You've used OpenVPN and Certificates ? and Renew or Reissue a CA or Certificate ?
The easy way out :
Create a new "CA" for your OpenVPN server.
And then create a certificate for your server.Then set them to be used by your server : these two :
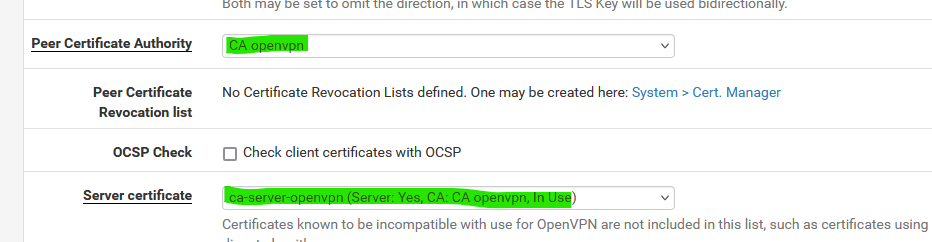
When saved, the OpenVPN server will restart and use the new certs.
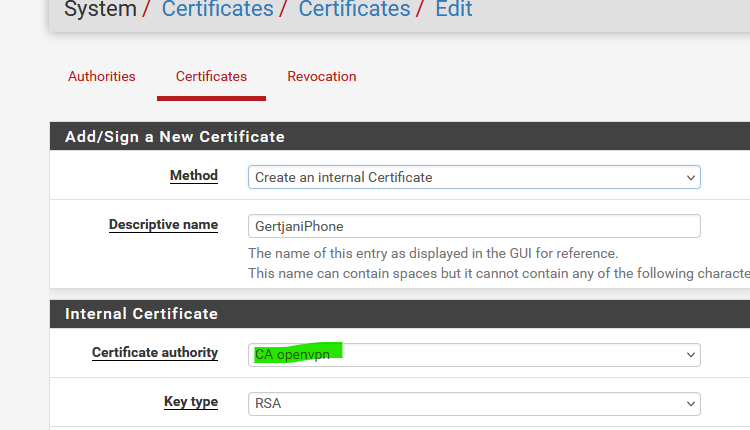
Now, go to a OpenVPN user ( System> User Manager> Users ) and edit a user.
Remove the existing certificate under "User Certificates" and add a new one.Select the correct certificate :
Now, goto OpenVPN > Client Export Utility and locate your user.
Export a config (the one youi normally use) - I only export this one :
and import it on your device.
This should work, as the procedure is the same as setting up a new OpenVPN server.
Btw : Afaik, I never renewed OpenVPN certs. But I must have done it over the past 15+ years or so.
I would not have touched the existing OpenVPN setup (and wouldn't waited until the edge : datea expired).
I would crate a new CA
A new certificate.
Then set up with these two an OpenVPN server, listing on another port, like 1195 (the original server listens on 1194).
And now you have two Openserver instances running on pfSense. The difference is the port used (of course) and certs used.Made sure NAT and/or firewall rules, if needed, are in place.
Then I would have created a new openvpn user.
Client exported its config, and import it into a openvpn client.
Select the new config when making a connection.
At this moment, the client has both configs, so you can test-and-compare.
What can now be easier to test things out , ^^You can also restart from scratch : delete the VPN stuff.
Then follow the Netgate Blog that shows you how to set up a server and client access using certs.
Watch also the 3 videos about OpenVPN on the Youtube official Netgate channel. They are old, but still very valid. -
Thanks for your help and assistance, I will be working on this today.
-
I followed some of your instructions and it is working once more.
I made a new CA as stated
I made a new Server Cert
I changed the OPENVPN to use the new CA & Cert
I changed 1 user to use the new CA & Cert
I downloaded and installed a fresh installed and it is now working.@Gertjan Once more, thank you for time help time and assistance with helping me get this fixed. I really appreciate it.