VyOS to pfSense - OSPF - Wiregaurd tunnels
-
I am attempting to replace a VyOS device with pfSense version 2.7.2 for a branch location.
Below is the current VyOS configuration for the branch device.
interfaces { ethernet eth0 { address 192.168.178.205/30 description MPLS hw-id 00:90:27:e6:23:78 offload { gro gso sg tso } } ethernet eth1 { address 10.168.120.130/29 description ILL hw-id 00:90:27:e6:23:79 offload { gro gso sg tso } } ethernet eth2 { address 10.168.100.146/28 description LAN hw-id 00:90:27:e6:23:7a offload { gro gso sg tso } } ethernet eth3 { address 172.16.32.1/24 duplex auto hw-id 00:90:27:e6:23:7b offload { gro gso sg tso } speed auto } loopback lo { } wireguard wg100 { address 172.17.0.2/30 description Towards_MPLS peer to-wg_peer { address 10.60.81.131 allowed-ips 0.0.0.0/0 persistent-keepalive 2 port 50000 public-key eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee } private-key yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy } wireguard wg500 { address 172.19.0.2/30 description Towards_ILL peer to-wg_peer { address 1xx.124.117.yyyy allowed-ips 0.0.0.0/0 persistent-keepalive 2 port 55000 public-key xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx } private-key yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy } } policy { prefix-list Extended_LAN { rule 10 { action permit prefix 10.168.110.0/24 } rule 20 { action permit prefix 10.168.100.0/25 } rule 30 { action permit prefix 10.168.111.0/24 } } route-map Extended_LAN { rule 10 { action permit match { ip { address { prefix-list Extended_LAN } } } } } } protocols { ospf { area 0 { network 172.17.0.0/30 network 172.19.0.0/30 network 10.168.110.0/23 network 10.168.100.0/24 network 10.168.111.0/24 } interface wg100 { bfd { } cost 10 } interface wg500 { bfd { } cost 30 } redistribute { static { route-map Extended_LAN } } } static { route 0.0.0.0/0 { next-hop 10.168.120.129 { distance 210 } } route 10.9.99.96/27 { next-hop 192.168.178.206 { } } route 10.60.81.128/26 { next-hop 192.168.178.206 { } } route 10.168.6.0/24 { next-hop 192.168.178.206 { } } route 10.168.100.0/25 { next-hop 10.168.100.145 { } } route 10.168.110.0/24 { next-hop 10.168.100.145 { } } route 10.168.111.0/24 { next-hop 10.168.100.145 { } } route 192.168.36.0/24 { next-hop 192.168.178.206 { } } route 192.168.64.0/24 { next-hop 192.168.178.206 { } } route 192.168.71.0/24 { next-hop 192.168.178.206 { } } route 192.168.73.0/24 { next-hop 192.168.178.206 { } } route 192.168.75.0/24 { next-hop 192.168.178.206 { } } route 192.168.81.0/24 { next-hop 192.168.178.206 { } } route 192.168.151.0/24 { next-hop 192.168.178.206 { } } route 192.168.153.0/24 { next-hop 192.168.178.206 { } } route 192.168.154.0/24 { next-hop 192.168.178.206 { } } route 192.168.161.0/24 { next-hop 192.168.178.206 { } } route 192.168.162.0/24 { next-hop 192.168.178.206 { } } route 192.168.163.0/24 { next-hop 192.168.178.206 { } } route 192.168.177.0/24 { next-hop 192.168.178.206 { } } route 192.168.179.0/24 { next-hop 192.168.178.206 { } } } }My current frr.conf look like below
##################### DO NOT EDIT THIS FILE! ###################### ################################################################### # This file was created by an automatic configuration generator. # # The contents of this file will be overwritten without warning! # ################################################################### ! frr defaults traditional hostname AU99K7D8WSTK.aucbakola.local password AK0L@urb@N service integrated-vtysh-config service password-encryption ! ip router-id ! interface tun_wg1 description "ospfd: WG500_ILL" ip ospf network point-to-point ip ospf cost 30 ip ospf bfd ip ospf mtu-ignore ip ospf area interface tun_wg0 description "ospfd: WG100_MPLS" ip ospf network point-to-point ip ospf cost 10 ip ospf bfd ip ospf mtu-ignore ip ospf area ! router ospf ospf router-id redistribute static route-map Extended_LAN timers throttle spf 200 1000 10000 passive-interface tun_wg1 passive-interface tun_wg0 network 172.17.0.0/30 area 0.0.0.0 network 172.19.0.0/30 area 0.0.0.0 network 10.168.110.0/24 area 0.0.0.0 network 10.168.100.0/24 area 0.0.0.0 network 10.168.111.0/24 area 0.0.0.0 ! ip prefix-list Extended_LAN 10.168.110.0/24 10 permit ip prefix-list Extended_LAN 10.168.100.0/25 20 permit ip prefix-list Extended_LAN 10.168.100.0/25 30 permit ! route-map Extended_LAN permit 10 match ip address prefix-list Extended_LAN ! bfd ! line vty !If I remove the ip ospf area 0.0.0.0 setting from the interface configuration, the connection works, but I still encounter some challenges. The main issue is that OSPF Network is now deprecated, and we cannot rely on manual configurations in frr.conf because they often get overwritten.
Additionally, the ip prefix-list Extended_LAN 10.168.110.0/24 10 permit configuration is sometimes overwritten.
Another challenge is that I am at the spoke/branch location and do not have access to the hub location device. It seems that pfSense relies heavily on GUI-based configuration.
Could you please suggest the exact configuration steps I need to follow to successfully connect the branch device to the network without requiring manual intervention? Thank you.
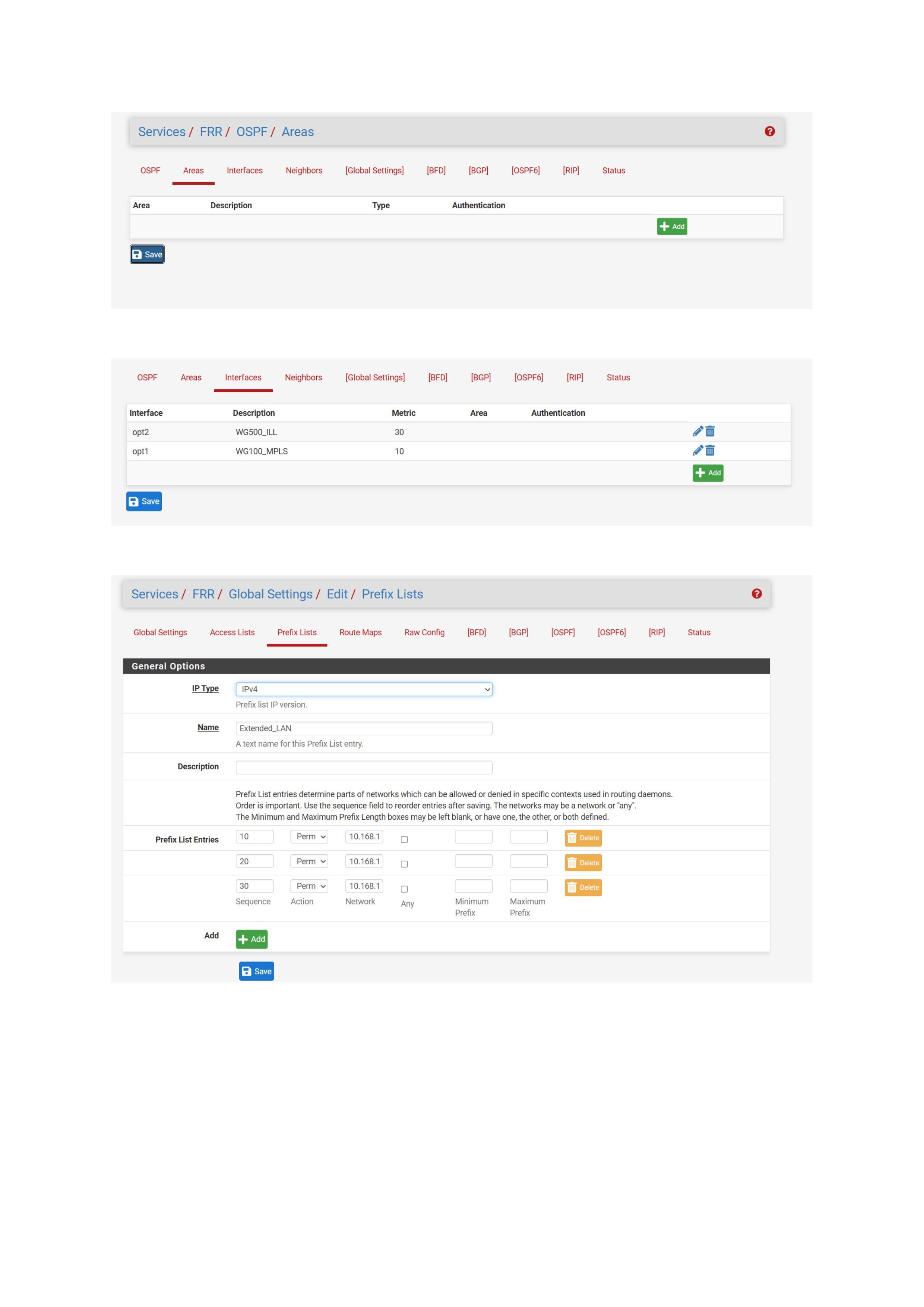
Below are current config in GUI.
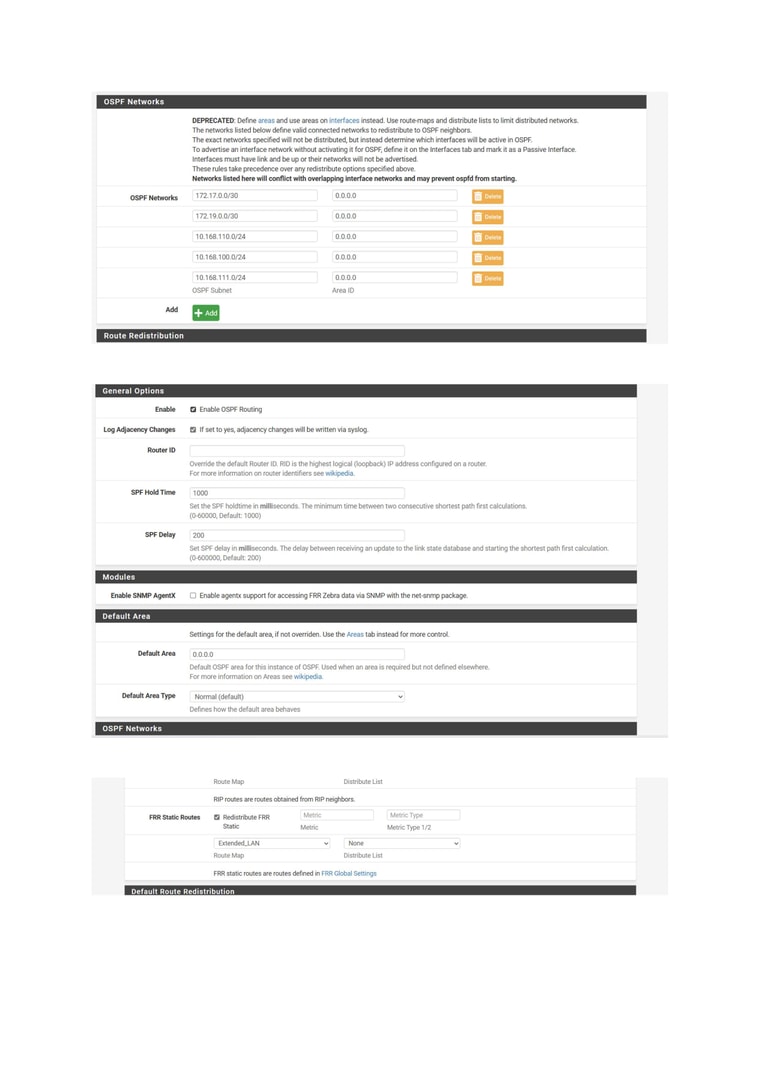

-
@pwabrat Sorry for the delayed reply,
the issue resolved by Route Redistribution in pfSense Kernel Routes of "Extended_LAN"
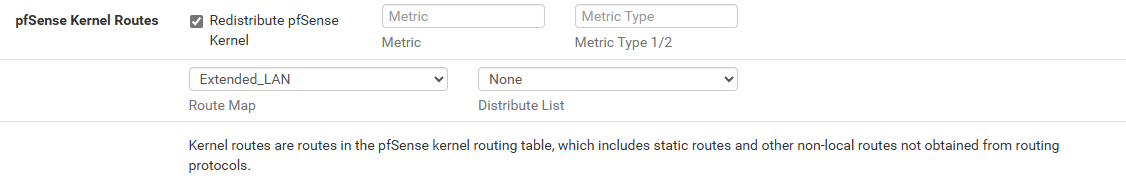
Thank you for the support.