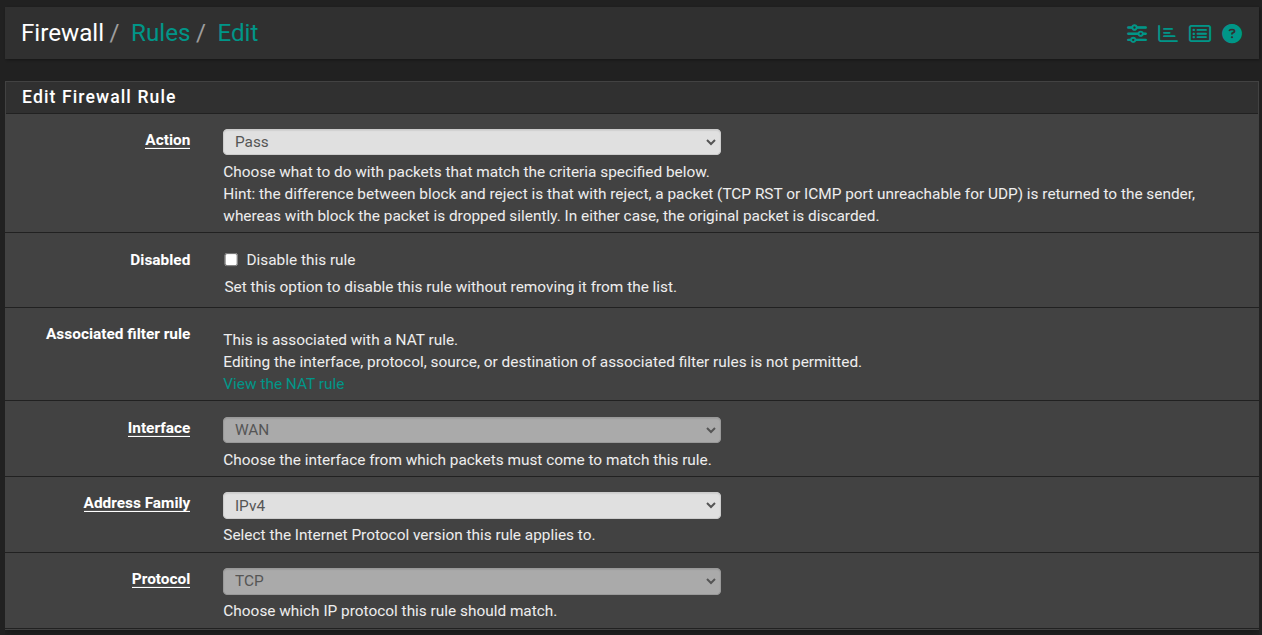
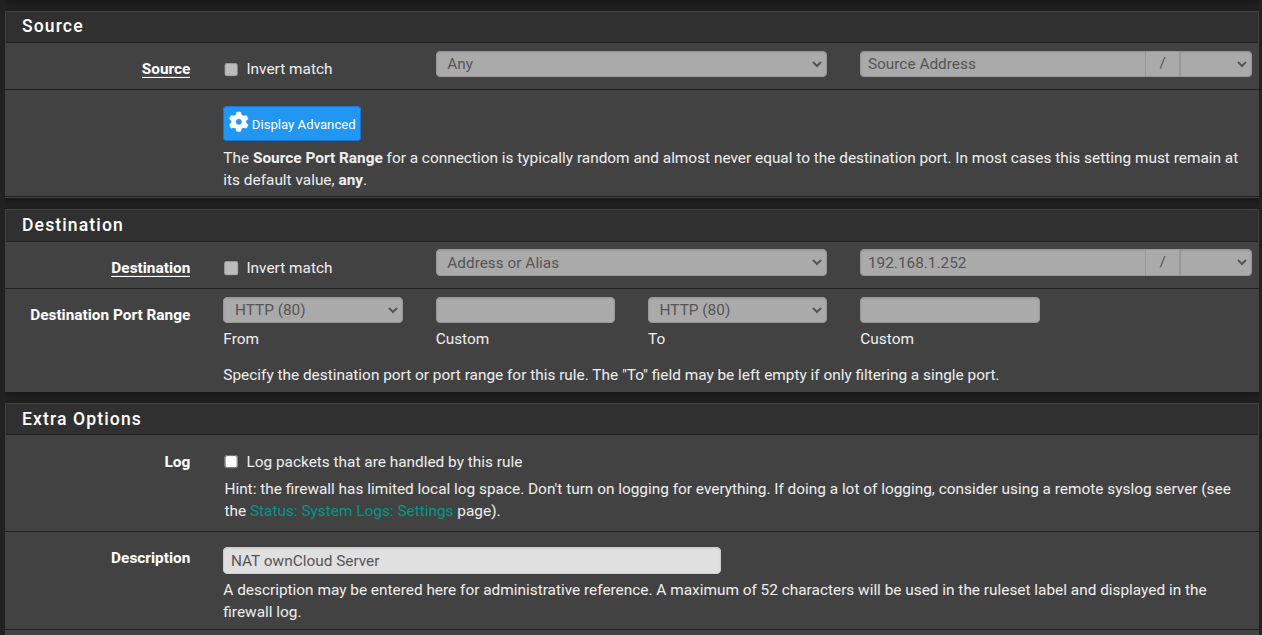
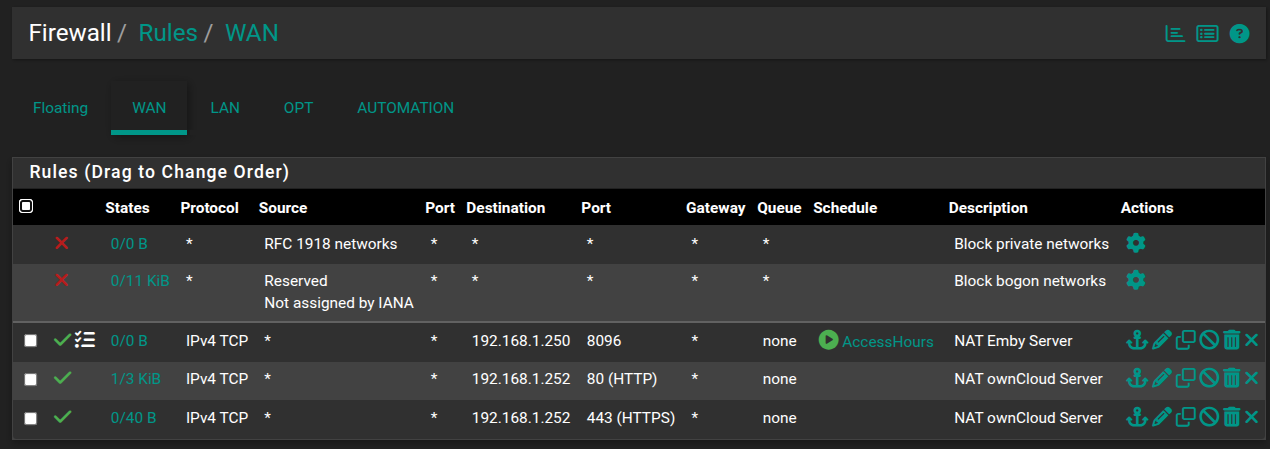
Why is port 80 being blocked by pfSense?
-
@johnpoz Yes, I know that's not the firewall log. I just observed that as I ran Certbot, an entry appeared in the dynamic firewall log showing that an attempt to connect to 192.168.1.252:80 was blocked. At the same time, Certbot returned an error that it could not retrieve the temporary file it created on my server and that the likely cause was a router firewall issue.
-
@NGUSER6947 said in Why is port 80 being blocked by pfSense?:
attempt to connect to 192.168.1.252:80 was blocked
Well lets see this block - go to can you see me dot org and send traffic to port 80.. Does it even show up on your wan. Do a packet capture..
That rule looks correct, and shows there was a state created.. Maybe you have a host firewall blocking it? Only thing I would do different is the port forward should be to your wan address, not any.
-
@NGUSER6947 LE has a rate limit, I suggest testing yourself if possible.
Agree, show the block. Could be https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html#out-of-state-web-server-packets.
-
Ok thanks folks. I'm away from home currently but will do as you suggest when I return and post the results here.
Truly appreciate the assistance.
-
@johnpoz Ok with my VPN disconnected I was able to get through Certbot and my SSL certificate has been installed!
Now, how do I go about implementing it? If I go to the https address, my web browser says it's untrusted. I suppose I need to take another step to submit my certificate so that the PC will consider it trusted?
-
@NGUSER6947 what cert? What is showing you some selfsigned cert most likely?
Lets encrypt CAs are normally out of the box trusted.. Validate your using the right cert for your service - its prob just still using its selfsigned vs the one from lets encrypt your trying to use.
Your browser should show you the details of the cert being presented.
Here is a cert from lets encrypt I use for one of my services.
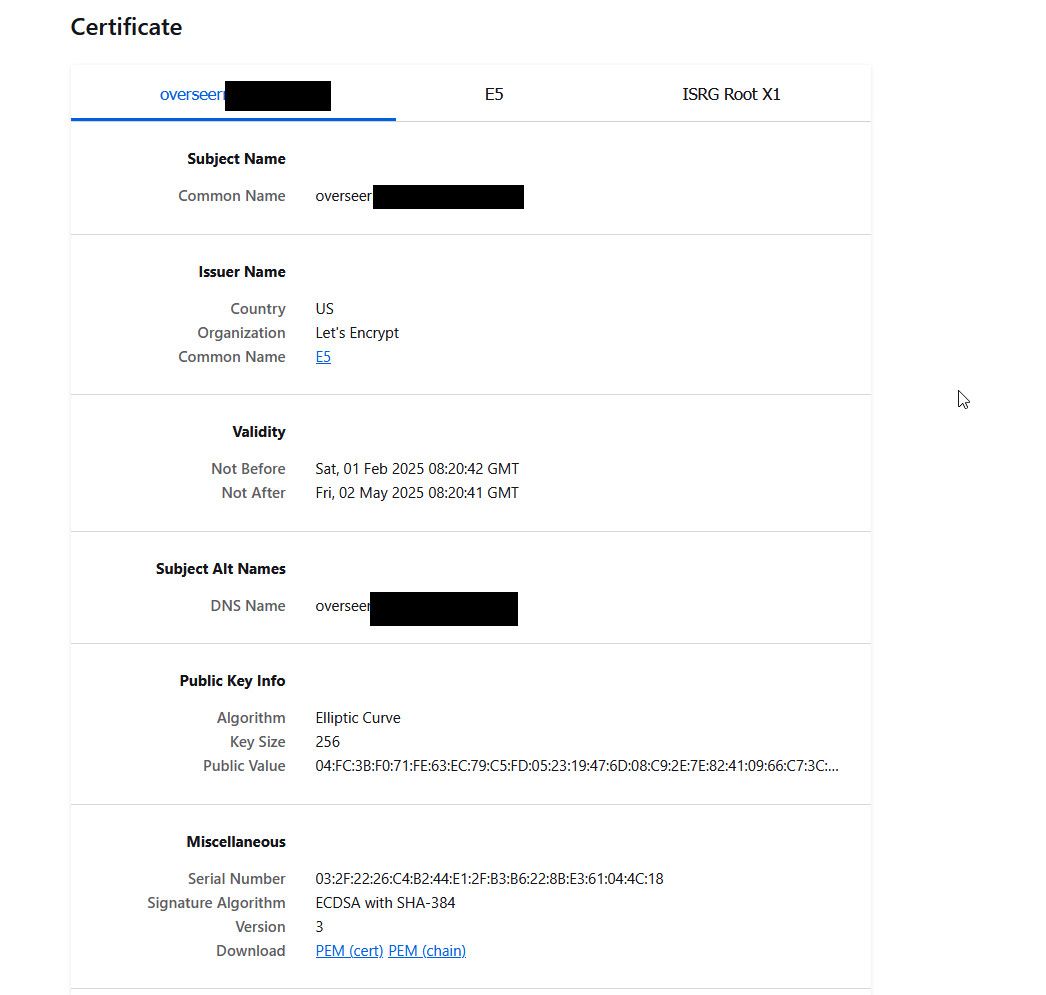
-
@johnpoz I think you are correct. This is what it shows:
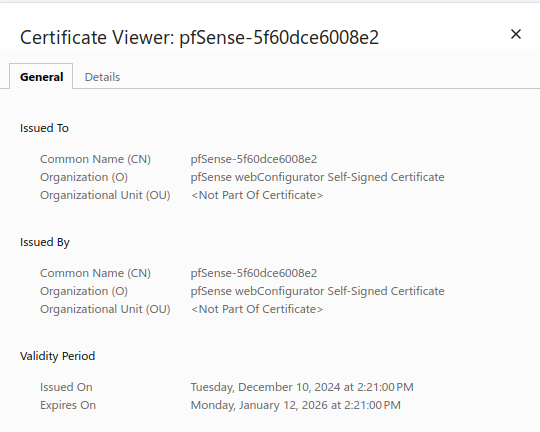
Also, if I try to connect from my phone (using cellular data, not my home wifi) it reports the same thing for the certificate info.
How do I get it to retrieve the certificate from my domain or switch it to use the LE certificate, do I need to upload the certificate to my DNS provider (DynaDot, who registered my domain) so that it serves up the certificate when clients connect to the domain, before they even get to the pfSense router? Or am I way off base with that idea?
-
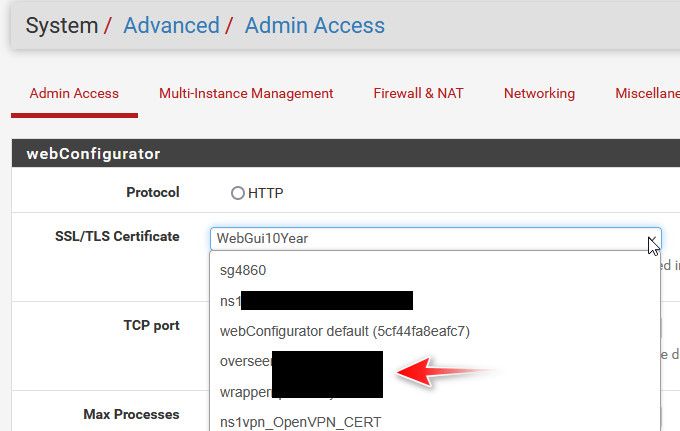
@NGUSER6947 that is your pfsense gui cert - set it to use the cert you want.
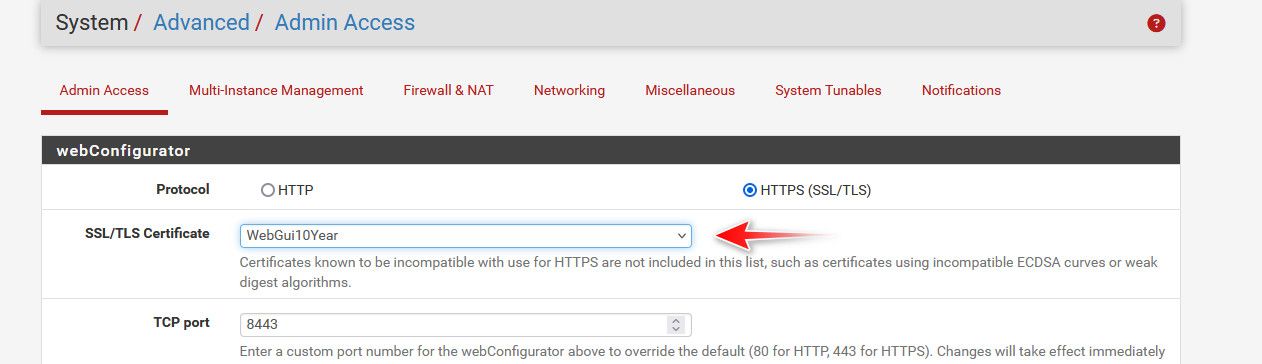
I use a cert I signed with pfsense CA, that my browser trust.. But you can have it use the lets encrypt cert.
Just click the drop down and change it.
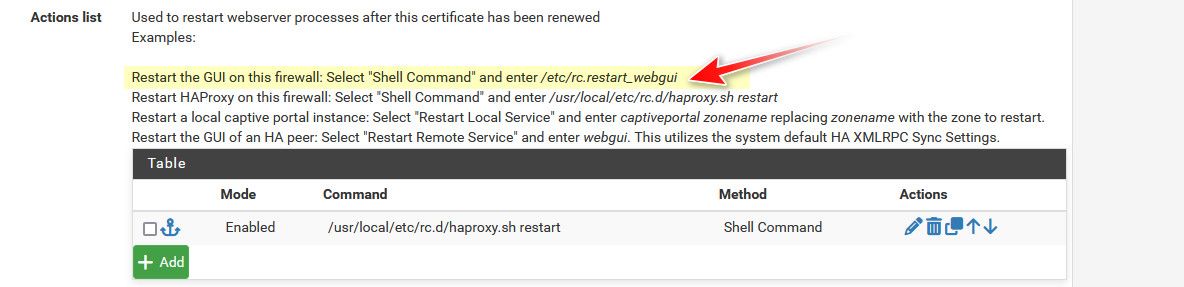
Once you set the gui to use your acme cert - you prob going to want to add the cron that restarts the gui when cert has been updated in the acme client.
-
I only see the default certificate, there's nothing else.
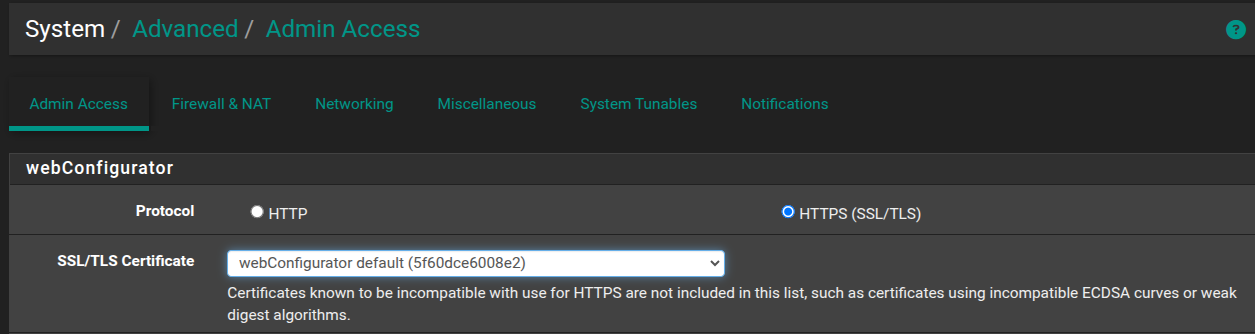
Well but now, the certificate information I see in the web browser is showing that it is coming from my domain, but still insecure:
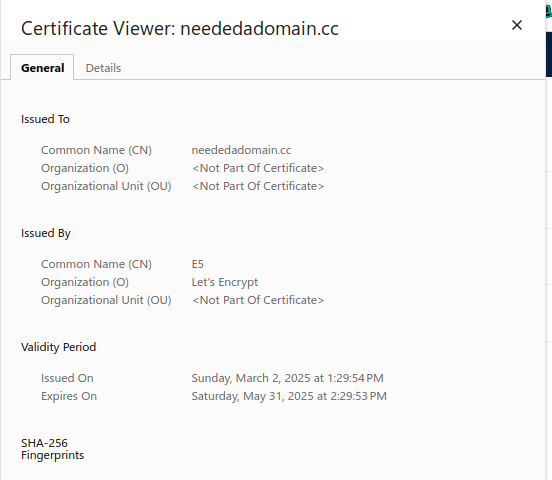
-
@NGUSER6947 if there is nothing else - how are you now seeingg the neededomain.cc ?
How would you get a cert for that from lets encrypt?
Did you hide that - that is not a valid public domain.. acme doesn't work without a valid public domain name.
If you are running the acme client on pfsense and got a cert it would be listed.
Here are the 2 certs I use for other things via haproxy - they are listed in pfsense cert manager..
If you want help you're going to need to provide a bit more info.
-
@johnpoz I am not using the Acme package. I used Certbot to obtain the LE certificate. Didn't hide anything in the Advanced setup:
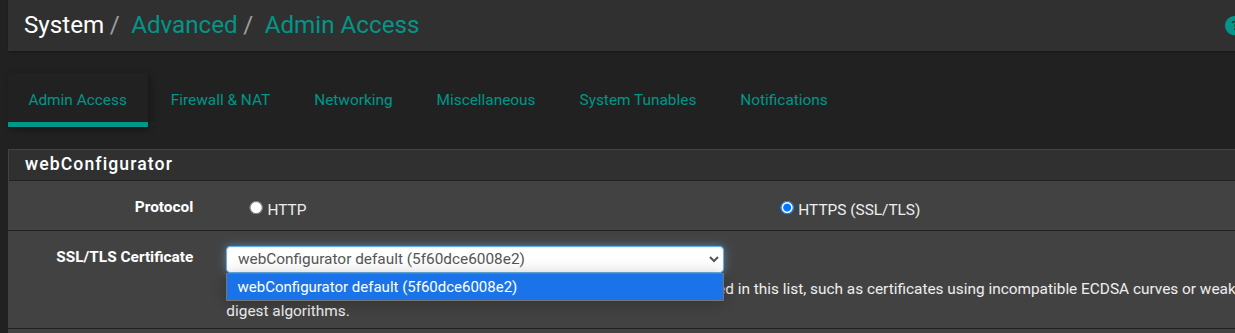
So I see this when accessing the site from my phone currently. It says it is using the Let's Encrypt certificate:
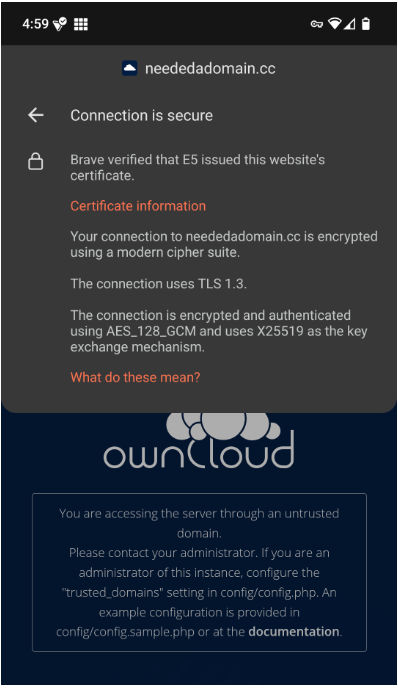
So it seems like it's almost there. Do I need to go into an apache config file and enter this domain into the trusted domain section maybe?
-
@NGUSER6947 Are you running haproxy? And letting it do the cert..
Oh my bad - typo.. That is a public domain. But its serving up apache - that is not the web gui

So your forwarding 80 through pfsense?
And on 443 its serving up owncload. And that is not browser complaining about the cert, that is owncload

If your trying to get to that from inside your own network you would either need to do nat reflection, haproxy or just setup your local domain to resolve that to the local IP your serving it up on.
There is nothing wrong with the cert, your browser trusts it - that is some internal config you need to do on owncloud.
that config/config.php has nothing to do with pfsense.
-
@johnpoz I was going to remove the port forward for 80 once I got the certificate and 443 set up.
-
@NGUSER6947 well configure owncloud then - says there is an example.
-
@johnpoz Got it, yes I know I was mixing up pfSense and OC setup things here. I had only gotten to the part where the phone would even show a valid connection about 20 minutes ago. Thanks for sticking with me.
Really appreciate the help.
-
@NGUSER6947 I wouldn't use the port 80 way to validate to be honest.. Just use DNS to get your cert, then you never have to open up port 80 at all.
-
Do you switch away the pfSense GUI ports first.
There are 80/443 used per default.
At the moment you expose the pfSense GUI to the Internet, very bad Idea! -
@NOCling Yes, fixed. Thanks.