Best way of finding top talker live
-
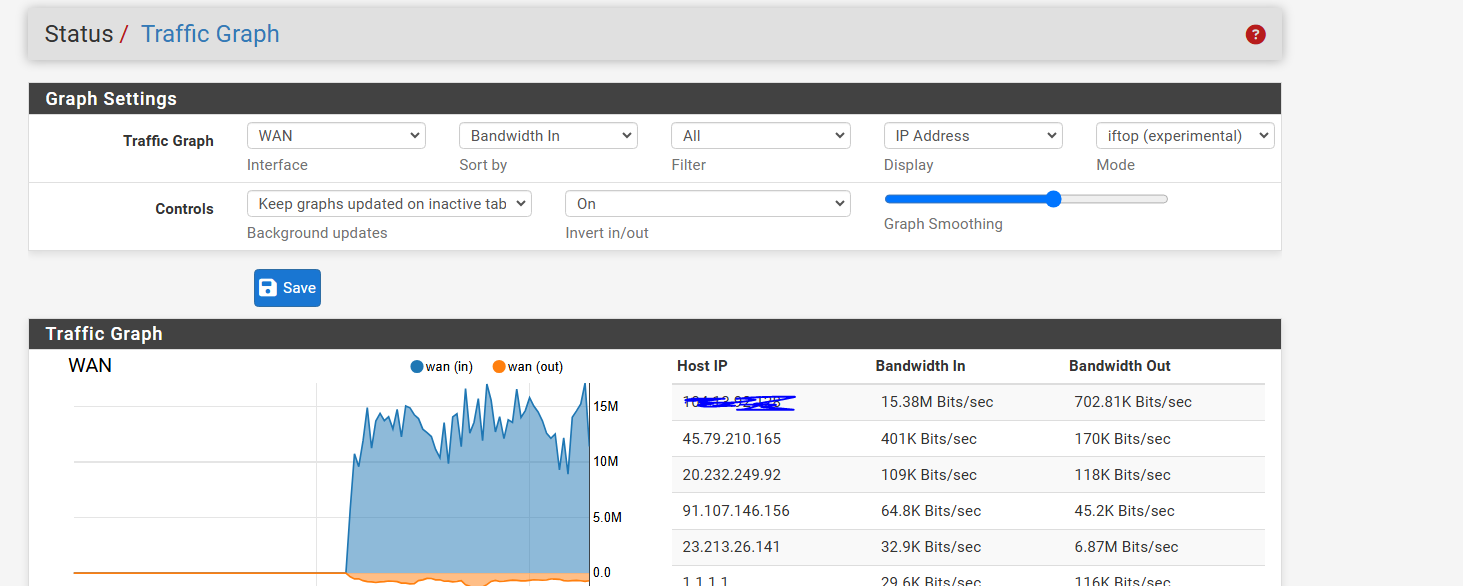
I have a pfsense with multiple interfaces. I have a traffic graph below for the wan interface.
How do I find out which downstream interface is receiving this traffic?
I blured out one of the Host IPs because its my WAN address as I am sorting by 'Bandwidth In' which makes sense as pfsense is receiving this traffic.
This is a small network with not a lot of intense flows going across so if 15Mbps of data is coming in its easy enough to assume its coming from a single downstream interface. Im just curious as to finding out which interface is the culprit.As a workaround, I can add multiple traffic graphs to the dashboard and correlate that data but is there a better way of figuring this out?
-
@michmoor NtopNG package
-
@keyser copy that. thanks !
-
@michmoor One piece of advice: NtopNG is designed and created as a tool for monitoring the traffic to/from internet from a LAN perspective. That means - it should be configured to monitoring your LAN(s) interfaces only. DO NOT configure it to also monitor WAN as that will make it report all traffic double. It will also make it borderline useless in diagnosing whats going on as it’s NOT meant to see all the packet that your firewall just blocks on WAN (Packet that are not part of sessions)
-
@keyser Because i've seen it can be pretty intensive, I'm going to enable it only when the needs come up. Ive seen folks leave it on which i guess you can do but seems a bit much.
I appreciate your advice!