OpenVPN Layer 2 with VLANs - How to Set Up?
-
Hi everyone,
I have a CARP cluster of pfSense firewalls at my headquarters, with multiple VLANs routed through pfSense.
I am adding some cloud servers that I want to connect to the headquarters via an OpenVPN Layer 2 tunnel. My goal is to pass multiple VLANs through a single VPN tunnel.
The cloud servers will be running Proxmox as the virtualization platform, and the virtual machines will use dedicated VLANs on virtual interfaces within Proxmox.
Essentially, I want to have VLANs dedicated to cloud servers, which are routed through pfSense via a single VPN interface. This way, the cloud servers would have only one interface and use pfSense as their default gateway for each VLAN.
However, I noticed that pfSense does not allow VLANs to be created on OpenVPN interfaces. So, I’m wondering how I can achieve this setup.
Do you have any recommendations on how to build this infrastructure?
Thanks!
-
You route the individual subnets to the other end, where there will be corresponding VLANs to use. The VLAN IDs don't have to match.
-
@JKnott thank you for your answer.
I don't want to route, because I don't have a router on the client end.
On the client end I have a Proxmox instance with a bridge on the
tap0.150interface and another on thetap0.151interface.
This way I expect that packets go through the OpenVPN TAP tunnel tagged with the VLANs 150 and 151, and arrive tagged on pfSense which have other two bridges on the OpenVPN interface.Anyway, I see that tagged packages do not enter the tunnel (I debugged with tcpdump).
I enabled the VLAN feature on the OpenVPN server with the
vlan-taggingcustom option.Do you have any idea?
Thank you!
-
@decibel83 said in OpenVPN Layer 2 with VLANs - How to Set Up?:
I enabled the VLAN feature on the OpenVPN server with the vlan-tagging custom option.
That requires using TAP rather than TUN VPN. With TAP, you essentially bridge the 2 networks together. This means both sites will have to be on the same subnet.
Here's what the manual says:
--vlan-tagging
Server-only option. Turns the OpenVPN server instance into a switch that understands VLAN-tagging, based on IEEE 802.1Q.
The server TAP device and each of the connecting clients is seen as a port of the switch. All client ports are in untagged mode and the server TAP device is VLAN-tagged, untagged or accepts both, depending on the --vlan-accept setting.
Ethernet frames with a prepended 802.1Q tag are called "tagged". If the VLAN Identifier (VID) field in such a tag is non-zero, the frame is called "VLAN-tagged". If the VID is zero, but the Priority Control Point (PCP) field is non-zero, the frame is called "prio-tagged". If there is no 802.1Q tag, the frame is "untagged".
Using the --vlan-pvid v option once per client (see --client-config-dir), each port can be associated with a certain VID. Packets can only be forwarded between ports having the same VID. Therefore, clients with differing VIDs are completely separated from one-another, even if --client-to-client is activated.
The packet filtering takes place in the OpenVPN server. Clients should not have any VLAN tagging configuration applied.
The --vlan-tagging option is off by default. While turned off, OpenVPN accepts any Ethernet frame and does not perform any special processing for VLAN-tagged packets.
This option can only be activated in --dev tap mode.
-
Yes, I am using the
tapmode.This is my server configuration file on pfSense:
dev ovpns8 verb 1 dev-type tap dev-node /dev/tap8 writepid /var/run/openvpn_server8.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local <my-ip-address> tls-server server 192.168.144.0 255.255.255.0 client-config-dir /var/etc/openvpn/server8/csc tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'vpn-cloud-server' 1" lport 30677 management /var/etc/openvpn/server8/sock unix remote-cert-tls client capath /var/etc/openvpn/server8/ca cert /var/etc/openvpn/server8/cert key /var/etc/openvpn/server8/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server8/tls-auth 0 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC allow-compression no explicit-exit-notify 1 inactive 300 vlan-taggingThis is my client configuration file:
dev tap persist-tun persist-key ncp-ciphers AES-256-GCM:AES-128-GCM:AES-256-CBC cipher AES-256-CBC auth SHA256 tls-client client resolv-retry infinite remote <my-ip-address> <my-port> udp nobind verify-x509-name "<server-cert-name>" name remote-cert-tls server explicit-exit-notify <ca> -----BEGIN CERTIFICATE----- <certificate> -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- <certificate> -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- <private_key> -----END PRIVATE KEY----- </key> key-direction 1 <tls-auth> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- <key> -----END OpenVPN Static key V1----- </tls-auth>Thank you!
-
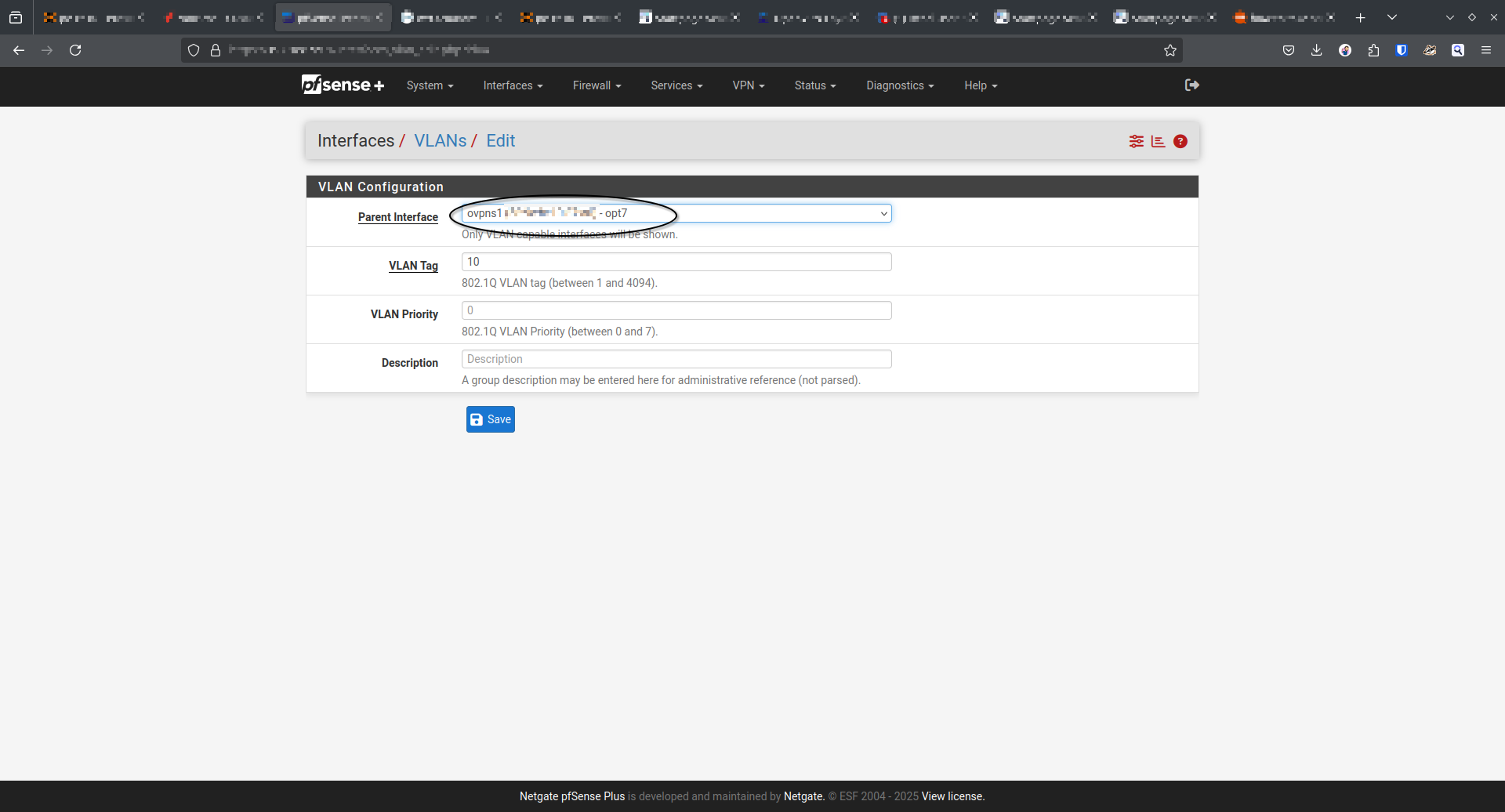
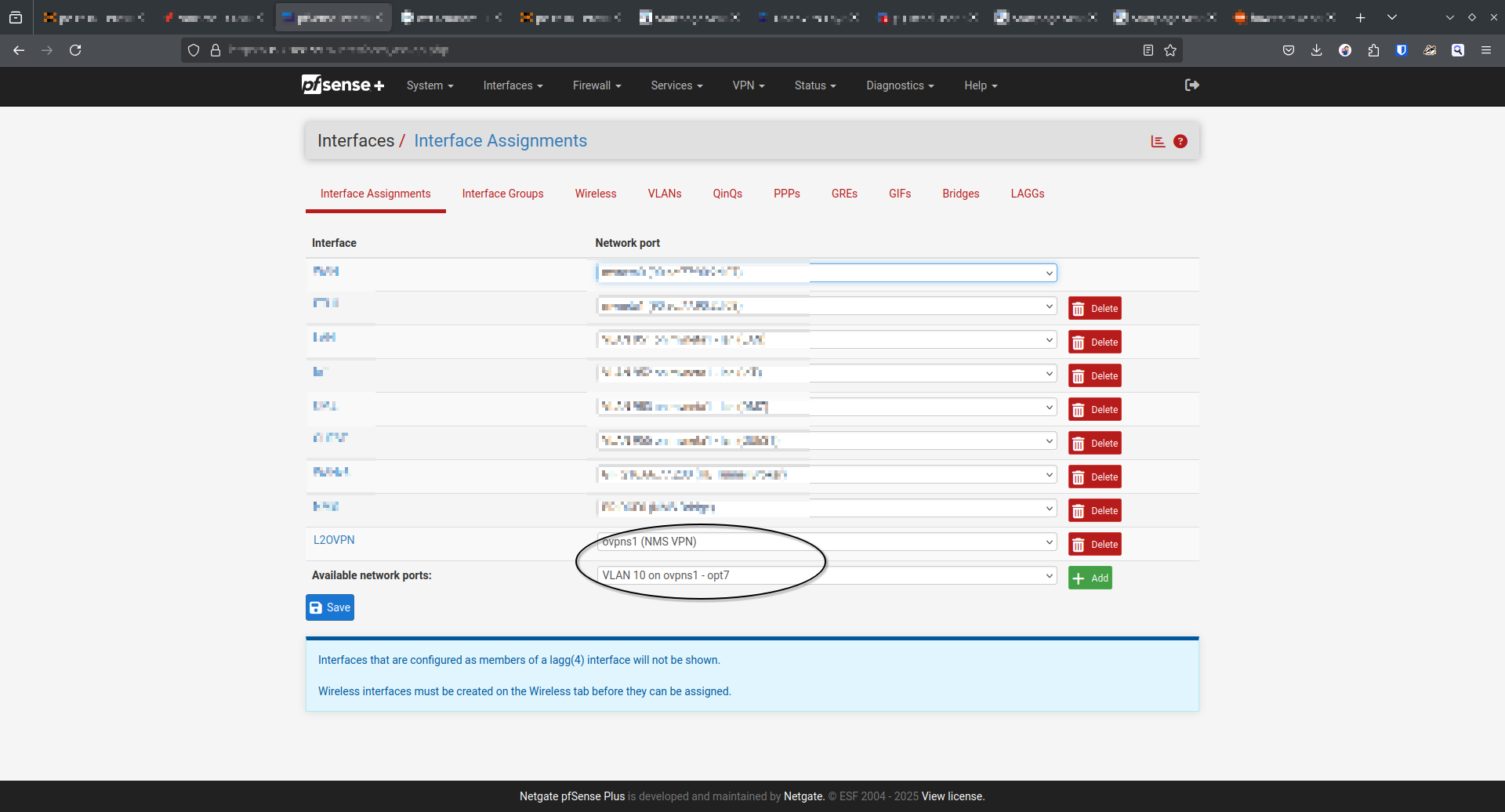
@decibel83
My pfSense lets me put a VLAN tag on my L2 VPN
-
@crazily9892 said in OpenVPN Layer 2 with VLANs - How to Set Up?:
My pfSense lets me put a VLAN tag on my L2 VPN
Thank you.
I tried to set the VLANs on the OpenVPN tap interface:
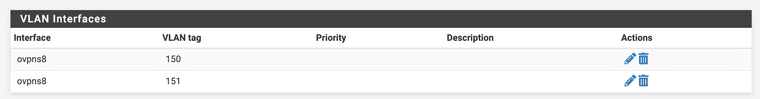
And then I added a bridge from the newly created VLAN to the existing interface which is tagged on the switch:
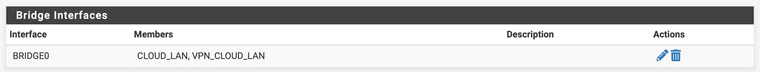
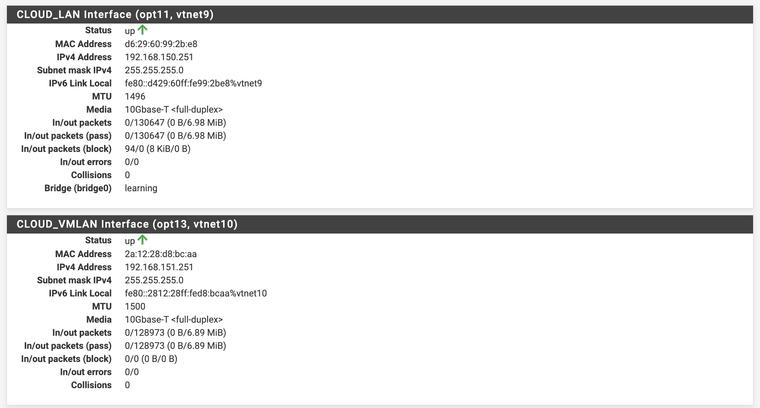
The
CLOUD_LANinterface has a CARP Virtual IP Address: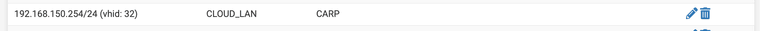
On the other end, I have a
vmbrinterface:24: tap0.150@tap0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr150 state UP group default qlen 1000 link/ether e6:43:98:64:45:36 brd ff:ff:ff:ff:ff:ff 25: vmbr150: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether e6:43:98:64:45:36 brd ff:ff:ff:ff:ff:ff inet 192.168.150.1/24 scope global vmbr150 valid_lft forever preferred_lft forever inet6 fe80::e443:98ff:fe64:4536/64 scope link valid_lft forever preferred_lft foreverWhich is bridged to the
tap0OpenVPN interface:root@node1:~# brctl show bridge name bridge id STP enabled interfaces vmbr0 8000.107c614c4e64 no enp5s0 vmbr150 8000.e64398644536 no tap0.150Anyway, if I try to ping the pfSense
CLOUD_LANIP address from the OpenVPN client, it does not work:root@node1:~# ping 192.168.150.254 PING 192.168.150.254 (192.168.150.254) 56(84) bytes of data. From 192.168.150.1 icmp_seq=1 Destination Host Unreachable From 192.168.150.1 icmp_seq=2 Destination Host Unreachable From 192.168.150.1 icmp_seq=3 Destination Host UnreachableAnd tcpdump only see the ARP request:
root@node1:~# tcpdump -i tap0.150 tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on tap0.150, link-type EN10MB (Ethernet), snapshot length 262144 bytes 10:03:23.636095 ARP, Request who-has 192.168.150.254 tell 192.168.150.1, length 28 10:03:24.659991 ARP, Request who-has 192.168.150.254 tell 192.168.150.1, length 28 10:03:25.683845 ARP, Request who-has 192.168.150.254 tell 192.168.150.1, length 28 10:03:26.708073 ARP, Request who-has 192.168.150.254 tell 192.168.150.1, length 28This let me think that the problem is on the client, because packages are not exiting from it.
Do you have any idea?
Thank you!