Block Websites for some users, but not others.
-
Good day,
I hope everyone is well. First off, apologies if this has been asked before.
I want to block access to specific websites, while allowing a select few users to browse freely. I am new to pfsense and pfblockerng, and I would sincerely appreciate guidance on how I can accomplish this.
Thank you in advance.
-
@Hyperion_Cyber There is a “group policy” section in pfBlocker where you can allow IPs. I believe you must select Python mode to see it.
-
@SteveITS Ok great! I found the group policy option. Do I need to do anything in port forwarding or firewall rules to ensure everything takes effect?
-
@Hyperion_Cyber Run an update in pfBlocker.
In general devices need to use pfSense and not DOH/DOT for DNS, or they bypass blocking. pfBlocker has a checkbox in DNSBL to block that.
-
@Hyperion_Cyber said in Block Websites for some users, but not others.:
I found the group policy option
Be aware :
For all your LAN (multiple) devices, if a request host name is present in one of your DNSBL lists, it will get rejected (DNS/unbound/the resolver ) returns 0.0.0.0 (or 10.10.10.1).
So far, so good, but, there is a but ...
If any of the policy listed devices, like these :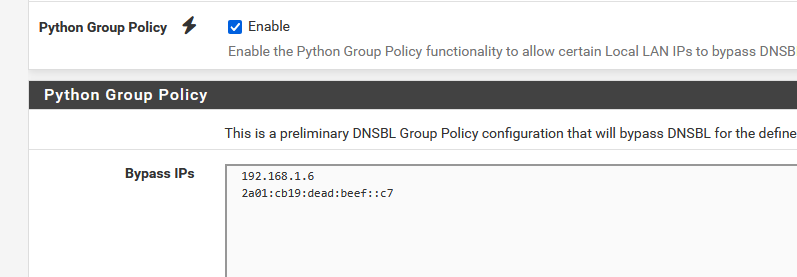
is asking for a DNS host name to be resolved, it will be done without any DNSBL filtering.
Great.
But the DNS resolver's answer will also be stored in the resolver (pfSense) cache also. That's what DNS is all about after all : for later identical requests, if the TTL is still non zero, the resolver can serve the answer right away.Here it comes : all you LAN devices that are not listed in the "Python Group Policy" will now also be served with an same answer, even if the host name was listed in a DNSBL list.
DNSBL handling will 'prohibited' resolving, not from answering from the resolver cache.edit : Of course, I hope to be wrong here.
This 'issue' is easy to test .... chances are great that I'm right. -
Thank you all. I managed to solve this issue by adding IPs under the Python Group Policy.