Unable to connect to a docker container on host from a VM across VLAN
-
So i have an untagged VLAN with my server (172.25.0.2) that runs some containers and then i have a VM (172.25.10.129) on VLAN 10 that runs on this same server. I am trying a
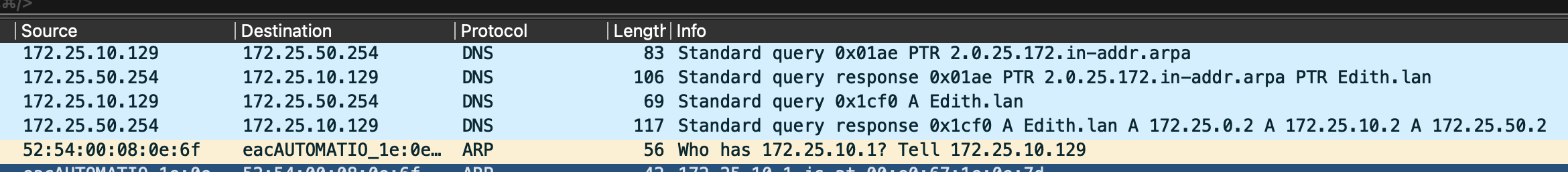
nc -vzcommand on a port that is mapped by a docker container but it doesn't work.I did a wireshark packet capture and I see from the VM perspective I see some DNS entries at first which doesn't make sense. I do want to keep in mind that my untagged VLAN uses pfsense as my DNS but my VLAN 10 uses an adguard as my DNS which lives in 172.25.50.254.
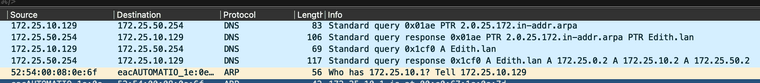
Here are my firewall rules below. As you can see its wide open and even I have an explicit firewall rule to allow traffic from my VM to my host
-
@immunize3320 said in Unable to connect to a docker container on host from a VM across VLAN:
So i have an untagged VLAN with my server (172.25.0.2) that runs some containers and then i have a VM (172.25.10.129) on VLAN 10 that runs on this same server.
What is an untagged VLAN for you? Is your server on a switch port which is configured as an VLAN (what number?) access port? And why is a VM on that server, with an IP out of the same range the server is in, on VLAN10?
-
What is an untagged VLAN for you?
So what i consider to be the untagged VLAN it is the LAN interface the default one basically. Am i correct to call that 'untagged' VLAN?
Is your server on a switch port which is configured as an VLAN (what number?)
Yes i have a unifi switch and I do allow other VLANs on it
why is a VM on that server, with an IP out of the same range the server is in, on VLAN10?
I am using VMs on VLAN 10 because I need them on that VLAN due to an application I am running OR because I imagine it should still work.
I use Unraid as my server and I have the VLAN 10 configured on the server.
-
Am i correct to call that 'untagged' VLAN?
I would say so, yes. Just wanted to make sure we're talking about the same thing.
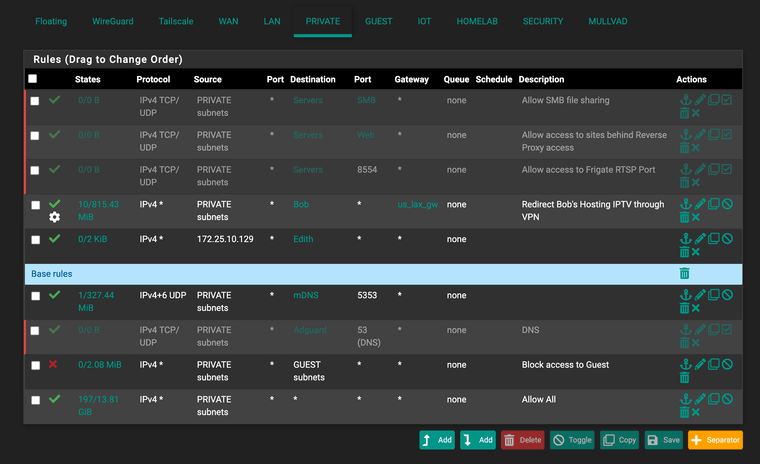
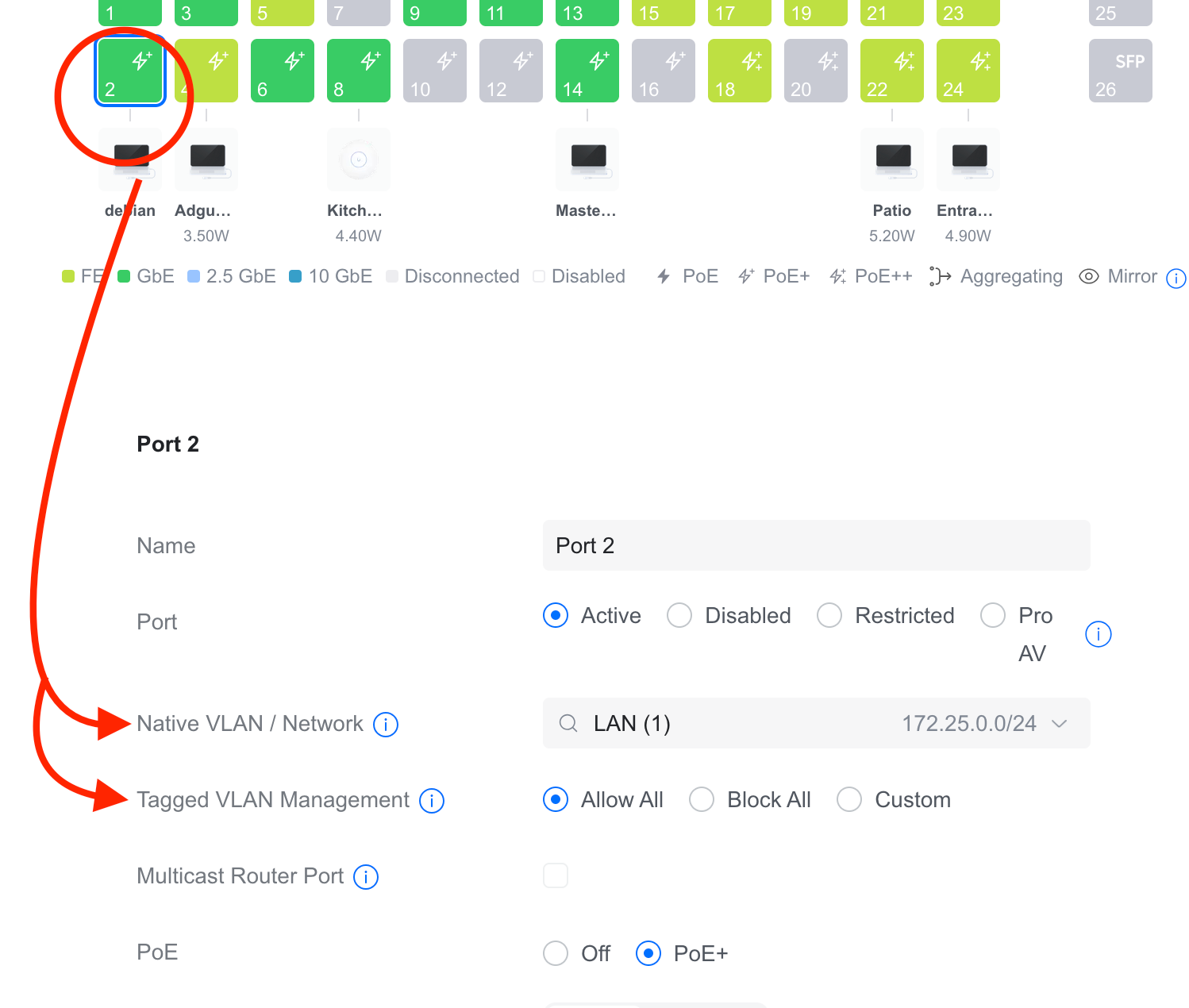
To further clarify, the server on 172.25.0.2 is on LAN (untagged VLAN 1 on port 2 of your unifi switch), as far as I can see.
The IP range of the PIRVATE network is 172.25.10.0/24 and that is VLAN10.Your package capture shows that your VM can query the AdGuard DNS and gets a response for Edith.lan. That would indicate that the VLAN10 setup is correct. Or is the AdGuard VM also running on your Unraid server (that is 172.25.0.2?)?
-
Or is the AdGuard VM also running on your Unraid server (that is 172.25.0.2?)?
No, it is not running on my Unraid server. It runs on a Pi on VLAN 50 which it's CIDR is 172.25.50.0/24
I will add that my LAN (Untagged VLAN) it's DHCP server uses 172.25.0.1 (pfsense) as the DNS server, but my Private VLAN (VLAN 10 and that is its name) has 172.25.50.254 and 172.25.50.253 as the DNS server.
I guess what confuses me is that if I do a netcat
ncfrom my laptop (on the VLAN10) to my unraid server (EDITH) in wireshark i do not see these DNS packets come through. I just checked right now unless i'm not looking right. -
I guess what confuses me is that if I do a netcat nc from my laptop (on the VLAN10) to my unraid server (EDITH) in wireshark i do not see these DNS packets come through.
Why would the DNS queries go to Edith.lan, they should go to 172.25.50253/4, no? Where do you connect that laptop to VLAN10, on the unifi switch?
In the first Wireshark capture you posted you can see that the VM (172.25.10.129) queries the DNS 172.25.50.254 for Edith.lan and get the responses, Edith.lan 172.25.0.2, 172.25.10.2, 172.25.50.2.
From what interface did you capture these packages? -
Why would the DNS queries go to Edith.lan, they should go to 172.25.50253/4, no?
Oh sorry that's not what i meant. I meant than when i do a netcat command from a different computer I don't see any DNS packets in wireshark, whereas with my VM i do see this which is odd.
Where do you connect that laptop to VLAN10, on the unifi switch?
Yea my laptop is connected via a Unifi AP > Unifi switch > VLAN 10.
From what interface did you capture these packages?
From igb.10 aka VLAN 10.
-
@immunize3320 then I'm out of idea right now, if all involved VMs, servers and clients are on VLAN10 then it should just work. That traffic will not even hit the pfSense.
Maybe someone else can step in with a more helpful approach.
-
@patient0 So the only server that is not on VLAN 10 is my host which is EDITH, but in this scenario all VMs are on VLAN 10.
The only thing that doesn't seem to work is connecting from VLAN 10 VM to a docker container port on the host.