Simple way to open up SSH port from LAN to DMZ
-
@JonathanLee I have no clue to what you are talking about???
-
Assuming ACL is a pfsense ACL rather than Anterior Cruciate Ligament, the answer is "No".
Most of the pfsense setup is out of the box. Didn't even know pfsense did ACL's until now.
https://docs.netgate.com/tnsr/en/latest/acl/standard.html#standard-acl-example
I think the issue was with my Macbook, no idea what happened, but suspect it was a networking config on the client and the firewall was OK. I could connect to 192.168.1.1 (the pfsense firewall) from the Macbook, but it was the 192.168.2.x connection that was the issue.
Thanks
Rob
-
@johnpoz This reply was related to the any any rule comment
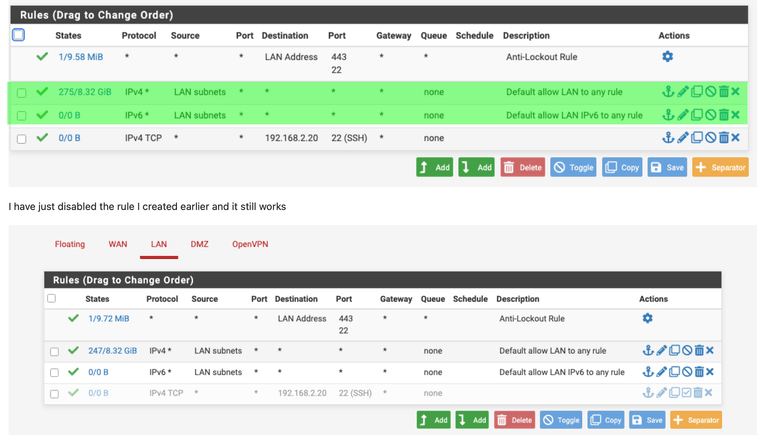
I did not see this before its any any rules so why have any rules at all it allows any thing and everything out.
Now that it is working try, working on making it more granular too so it is just not approving everything and anything.
Make it more specific to your needs. This is an example, I have time based rules, specific areas are blocked from being accessed. I have rules I enable when I need outbound vpn ports to the university. Some default blocks etc.
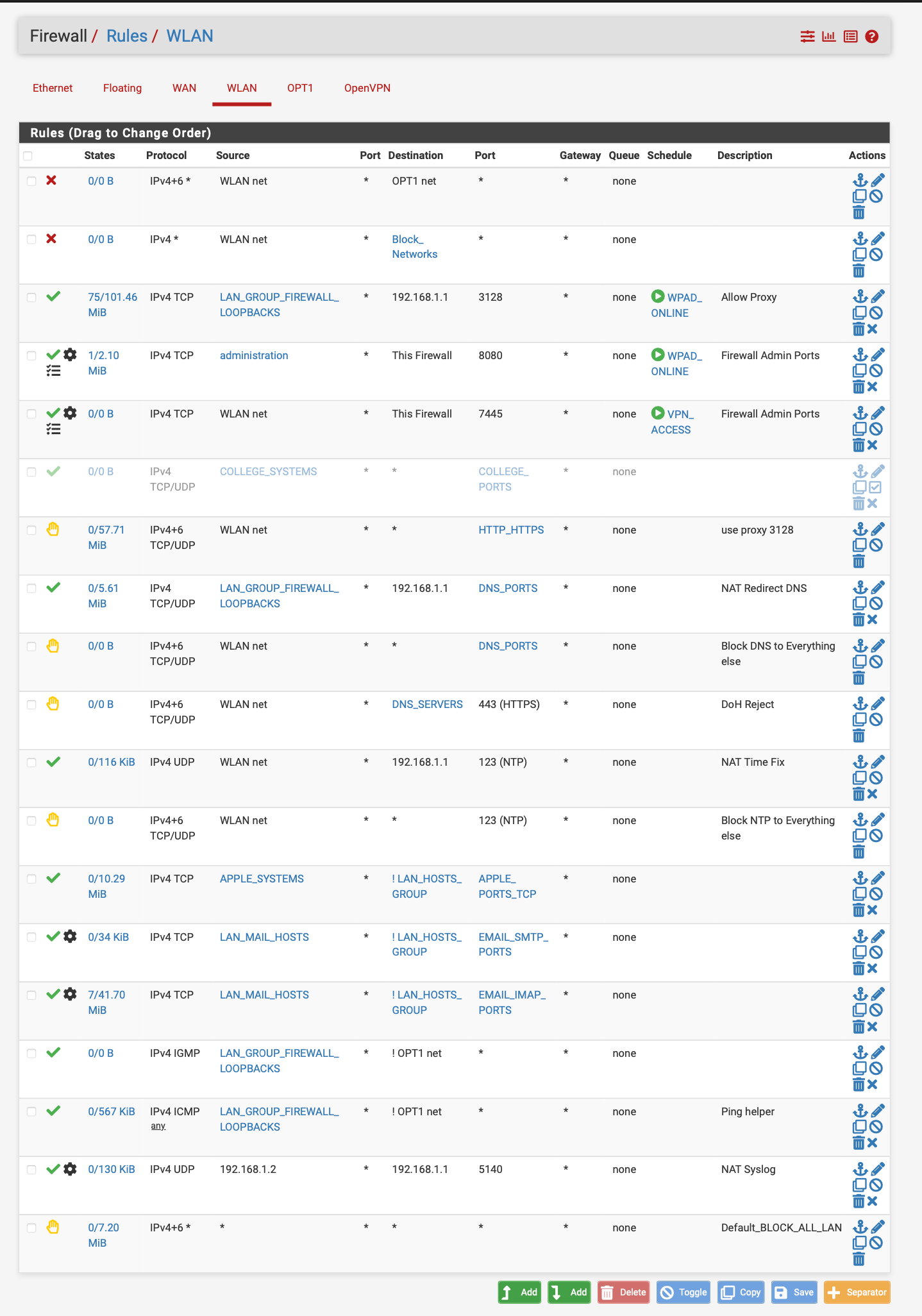
pfsense can do so much why just leave it as approve everything.... At least set some time rules up. You lock a door when you leave right so why not lock a network when you leave or are not using it. I have time rules for my proxy see WPAD online or VPN access hours...
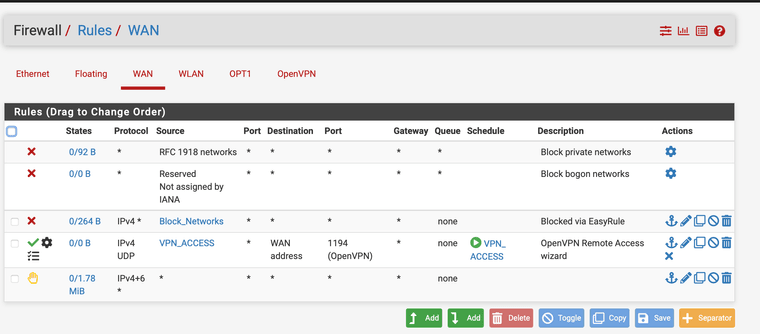
Another example of use of time based restrictions. Especially if you have a vpn to access your network set up for like a private cloud or whatever it may be.. lock it down or hypothetically lock the door when you are not using it.. -
Thanks for the information. I didn't set this rule up. This is what came out of the box.
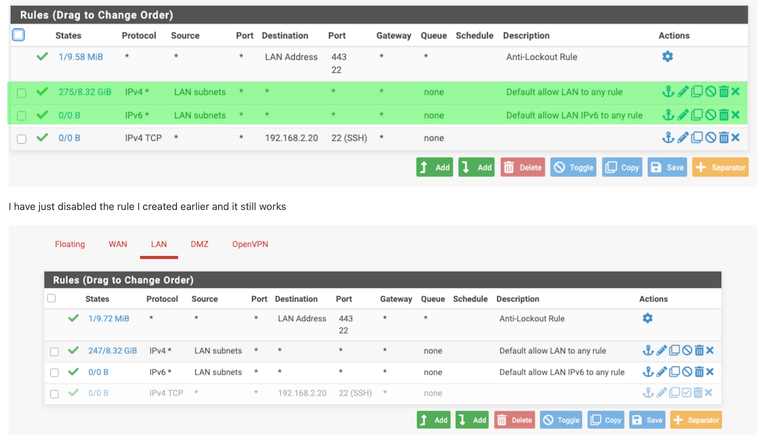
I'll read it through and see what I need. Since I work from home and have two teenage daughters, I tend to need the network 24/7 :)
Your point on being granular is well made and I've been lazy. I'll look at how to take as much access oput as I can.
Thanks
Ron
-
@rwillett said in Simple way to open up SSH port from LAN to DMZ:
I'll look at how to take as much access oput as I can.
Why - blocking outbound is going to do what but make your life harder... Please explain the logic in locking down your own trusted devices.. Other than work for you to do that will most likely only break shit..
If you want setup a rule above your any any rule to only allow http/https - and then below that a rule to block all logging... And watch where your stuff tries to go..
His rule there at the bottom - is pointless, the default deny already does that rule. I could see if he turned off default logging and set that rule to log.. But that rule is doing nothing the default deny doesn't already do - vs send back a reject vs just dropping the traffic.
-
@rwillett it is very complex to configure it like this, I only do this because I have a NAS and access to it across the full US, plus the work from home stuff so I have a secure side where I do not want even my own devices doing stuff I do not allow. I also have a lazy access point that is configured with any any stuff ...
Not gonna lie... it does take forever to get it working right.
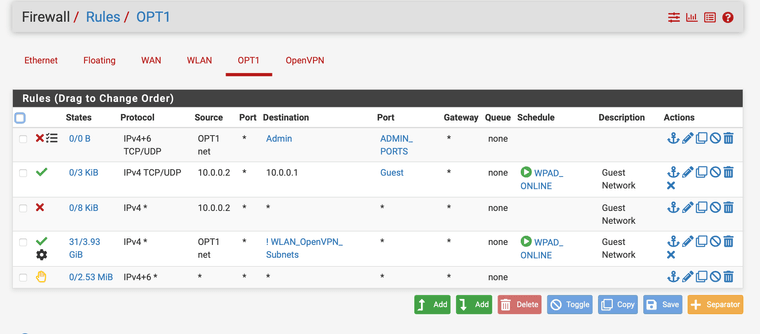
This is my lazy ap for the kids and game stuff... I at least block access to the admin ports so nothing can get to the gui on that interface, I allow only the ap to talk with pfsense on the dns npt DHCP etc. and my any any rule allows anything out but no access to vpn or secure devices and it is all on a schedule.
@johnpoz Yes my tinfoil hat fits perfectly....
In all reality I am a computer science student with an AA in cyber security so most of my stuff was done to learn and make it as complicated as possible. In the end I am sure there is easier ways to do it. But I wanted my secure side to be proxied and certificate intercepted just like a super maze on that side.
Long story short I have a lazy network too
-
-
@JonathanLee most of those rules are pointless.. If you only allow proxy 3128, there is no specific reason to block to dns 443, since there is not rule that allow 443 any anywhere on those rules - the default deny again blocks that traffic.
You do you - but in my 30+ years in the business, what the technical term for those set of rules would be is nonsense.
-
@johnpoz yea start off with 443 and port 80
-
@JonathanLee this for example
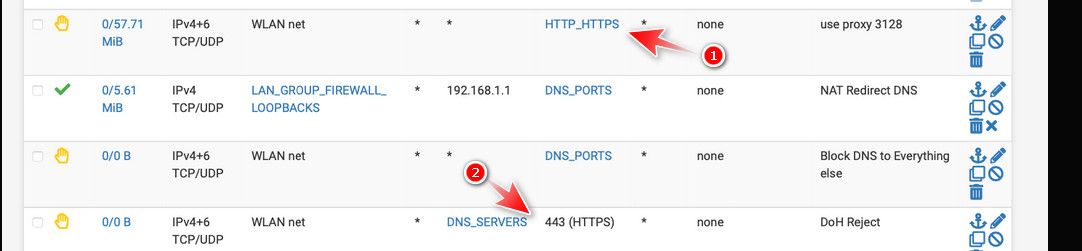
1 you block anything going to 80/443 - but then at 2 you also block traffic to dnsservers 443.. In what scenario would that traffic not already be blocked at rule 1.
edit: another example of not understanding how the rules work..
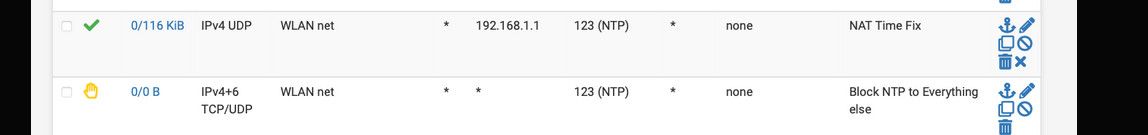
You allow ntp to 192.168.1.1, which is fine - but no where in the rule set do you have an any any rule that would allow 123, so blocking it specifically is pointless..
You know what a cluster of pointless rules do - they complex up trying to figure out what is actually going on.. So I would make a discussion point that if anything your making your network less secure - because clearly you do not understand how rules work at a basic level.. And you have what amounts to a bunch of noise in your rules you have to weed through any time your wanting to actually configure a valid rule, or troubleshoot why something isn't working.
-
@johnpoz ntp is a nat rule
-
@johnpoz thanks I forgot about the dns, that was created before I had the block all http https, I use to have a on system wpad and moved it to a raspberry pi zero wpad, after I moved it I just made a block rule and moved on. It looks like I still have some cleaning up to do. Thanks for the recommendations again..
-
Thanks for the recommendations, done I forgot about that before I had to have the ports open for WPAD so after I moved my wpad out of the system I just added a block and didn't look at the other rules. I do not need them anymore. Thanks
-
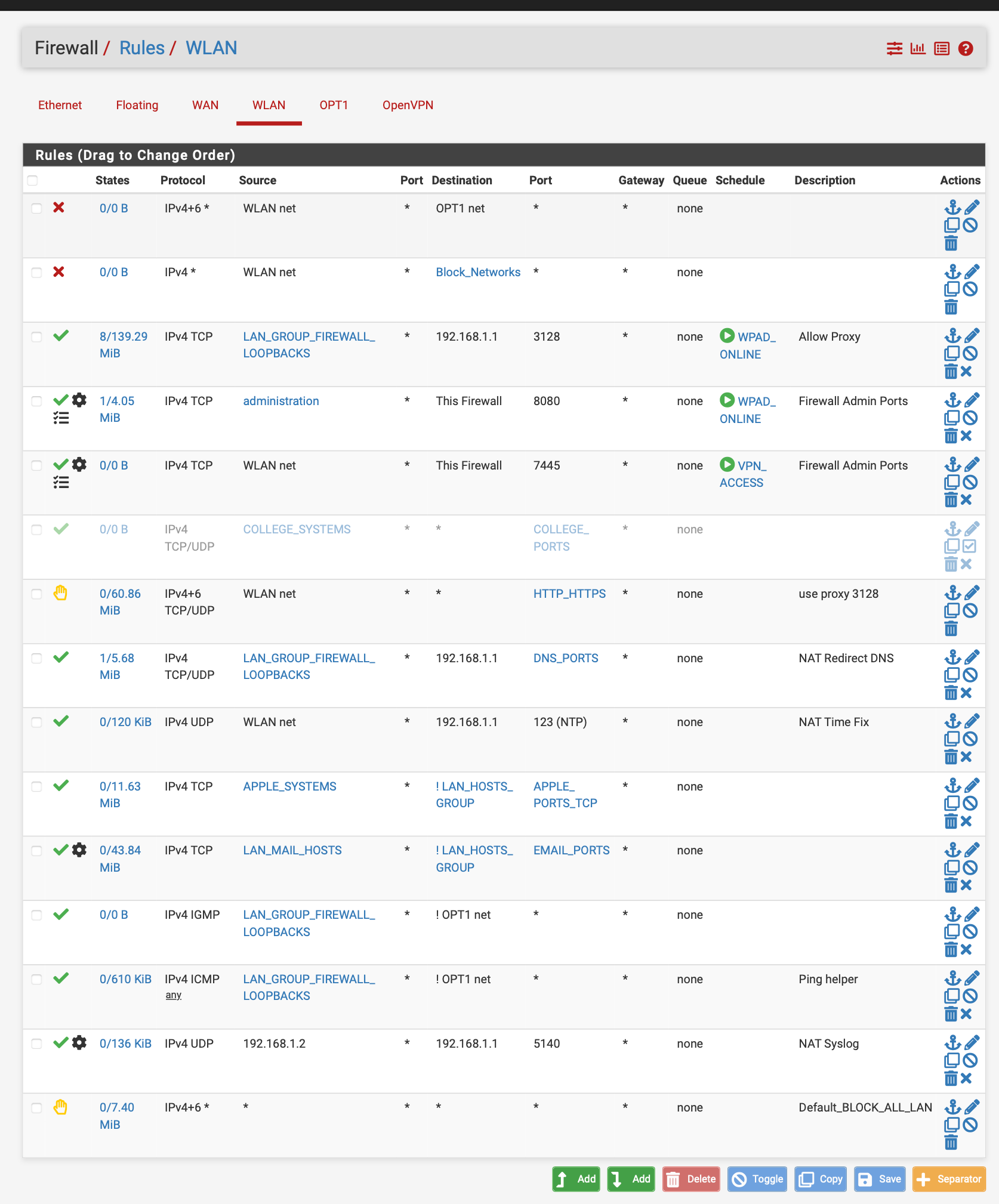
@JonathanLee how does allowing ntp to 192.168.1.1 fix ntp???
how is allowing 192.168.1.2 to talk to 192.168.1.1 have anything to do with nat syslog?? If your source is 192.168.1.2 - have to assume your wlan is 192.168.1/something - why would you need or want to nat syslog? Or ntp?
-
@johnpoz
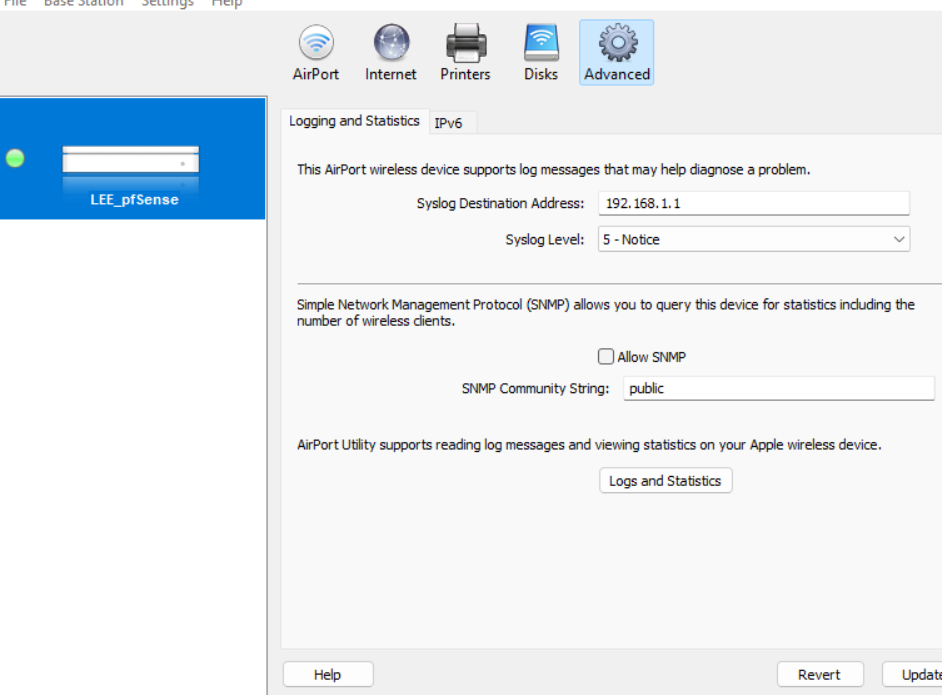
I have a fixed destination on the AP it only sends to 514 and won't use the package port 5140 so I nat it to it. Wireless AP to Firewall.For Syslog I have to nat it because the AP uses a different port that is fixed for sending syslogs that way I can view them only on the firewall and not have to log into the AP each time I want to see who is on the NAS. The device uses destination 514 but the package is 5140 so I had to make a nat rule. I got sick of logging in to view logs. After it is saved on my NVMe drive and not the SSD.
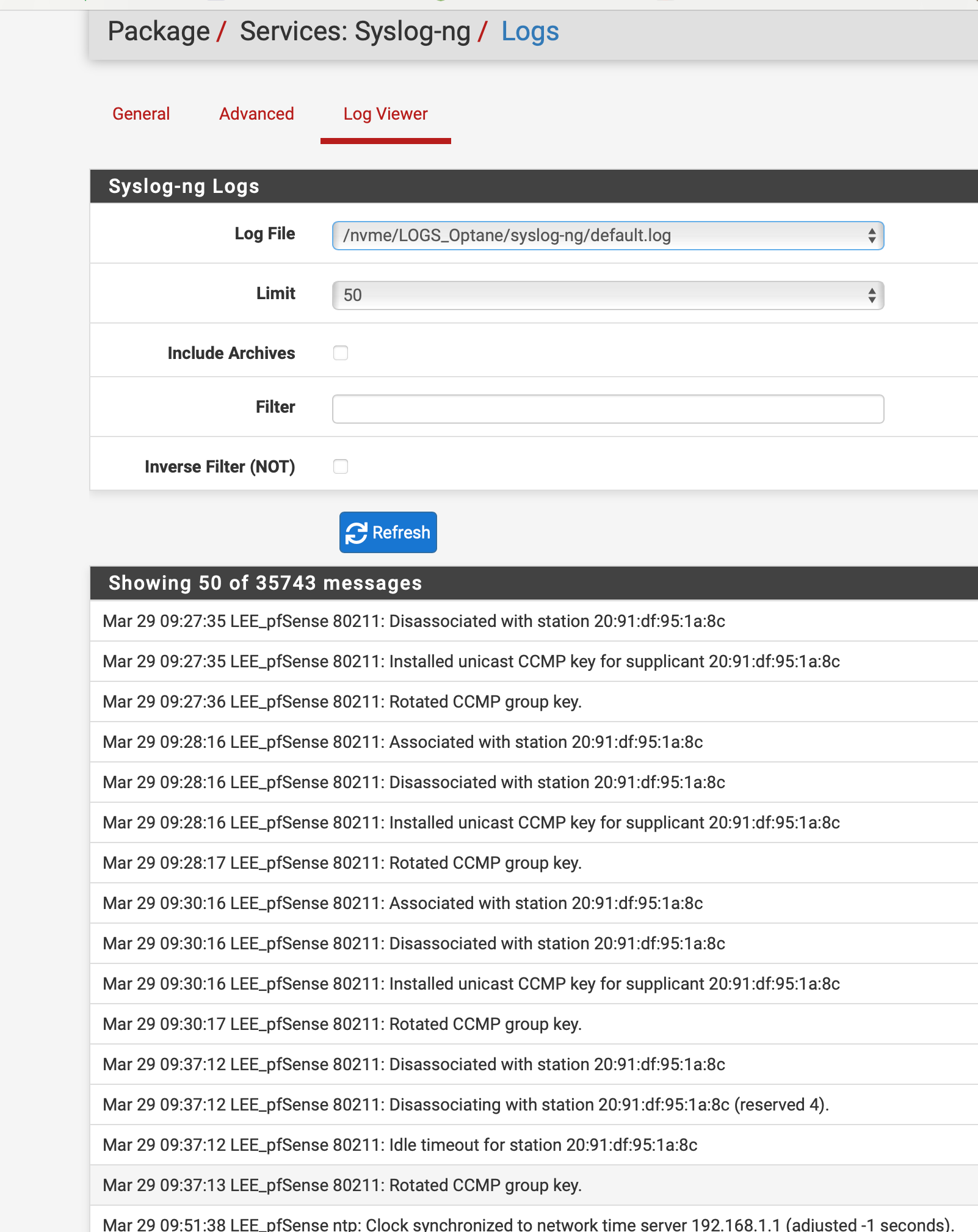
For NTP yes this works I have to NAT it for things and it functions forces everything to use the firewall and with the firewall it goes to the authenticated NTP with nist.gov
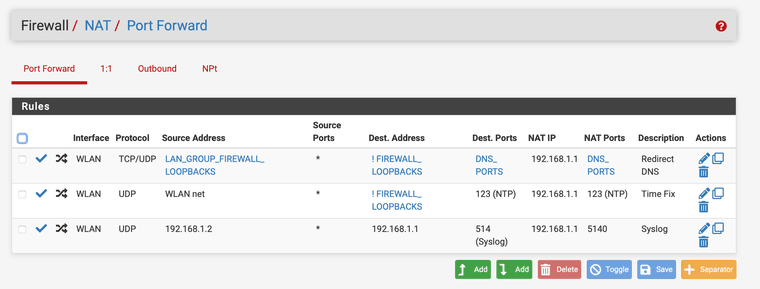
It works but you have to add the loopbacks into the nat rule also with it negated it would not work with only the firewall address. So it has to be not ! firewall/loopbacks and it works.
Something was messing with time on our network moving it 15-20 mins during tests and stuff, mean people. But this fixed it, NTP is an old protocol, with it authenticated and forced to be used I have not had a time jump issue in a long time.
-
@JonathanLee said in Simple way to open up SSH port from LAN to DMZ:
The device uses destination 514 but the package is 5140
You can change that
If you want to redirect things trying to use other ntp - then just do a redirect to localhost (127.0.0.1).. I have no idea what your talking about where ntp was jumping 15-20 minutes.. Ntp doesn't work like that..
What are you calling loopbacks - pfsense address on an interface?
Simpler solution for devices that use some other fqdn for dns is a simple host override so it resolves to the ntp server you want to point them too.
-
@johnpoz I can't use port 514 on the firewall it is already in use
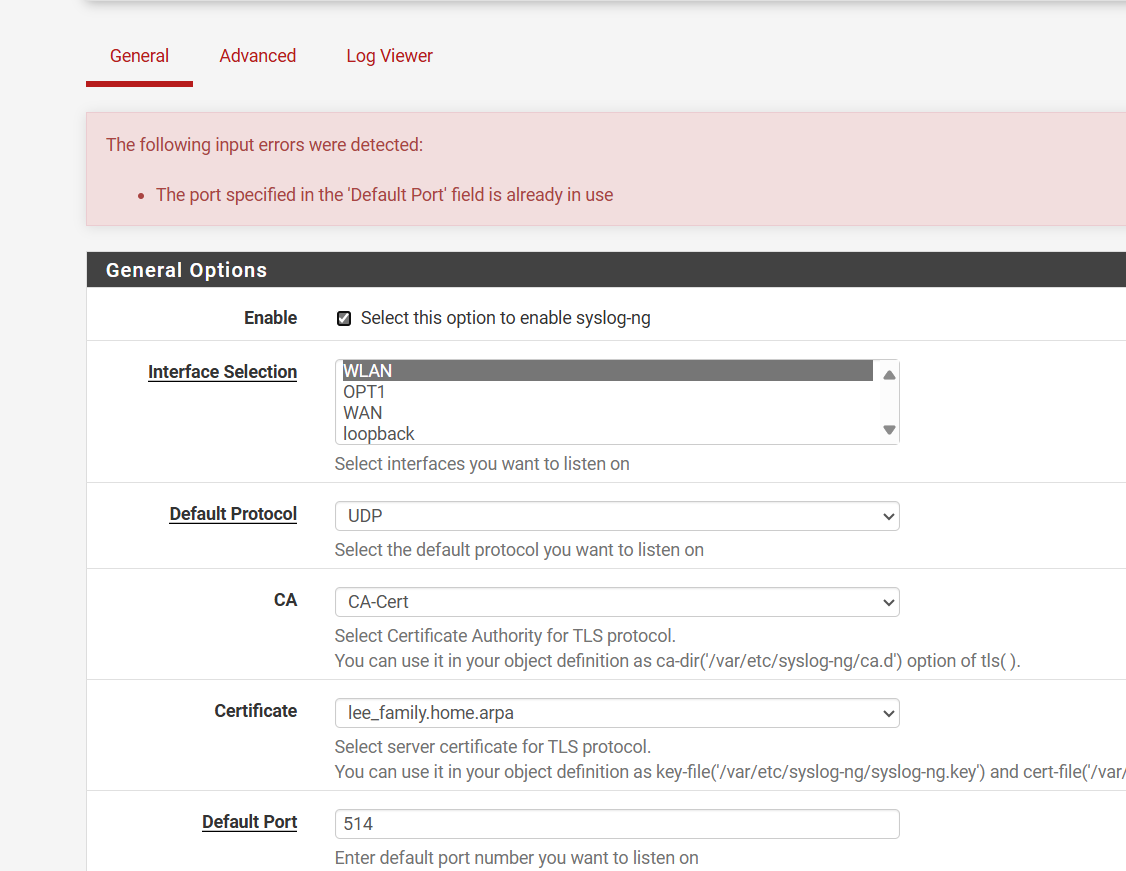
And I can't set the ap to use a different port..
I think the loopback or pfsense itself uses port 514 for something already
-
@johnpoz The time would move 15 mins..
Example your taking a timed test and all the sudden 15 mins is gone, there was something going on with it during cyber security classes. With it secure like this the time is correct and does not shift on the devices. Who knows maybe the professor was trying to teach us to use authenticated time services like auth NTP.
-
@JonathanLee well that 514 sure seems like a bug to me.. I can set syslog to not listen on all interfaces. So its only bound to localhost.
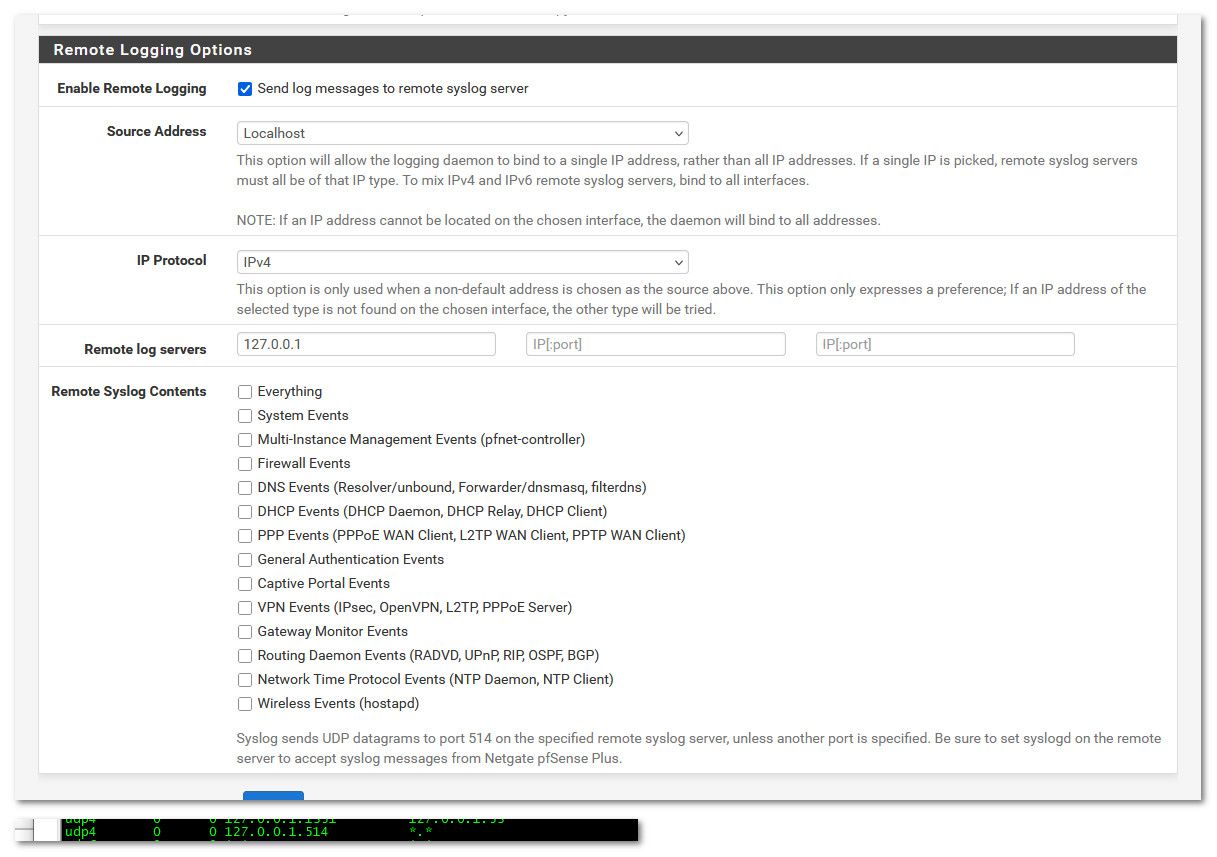
But then yeah your right still get the error even if I set syslog-ng to listen on different interface
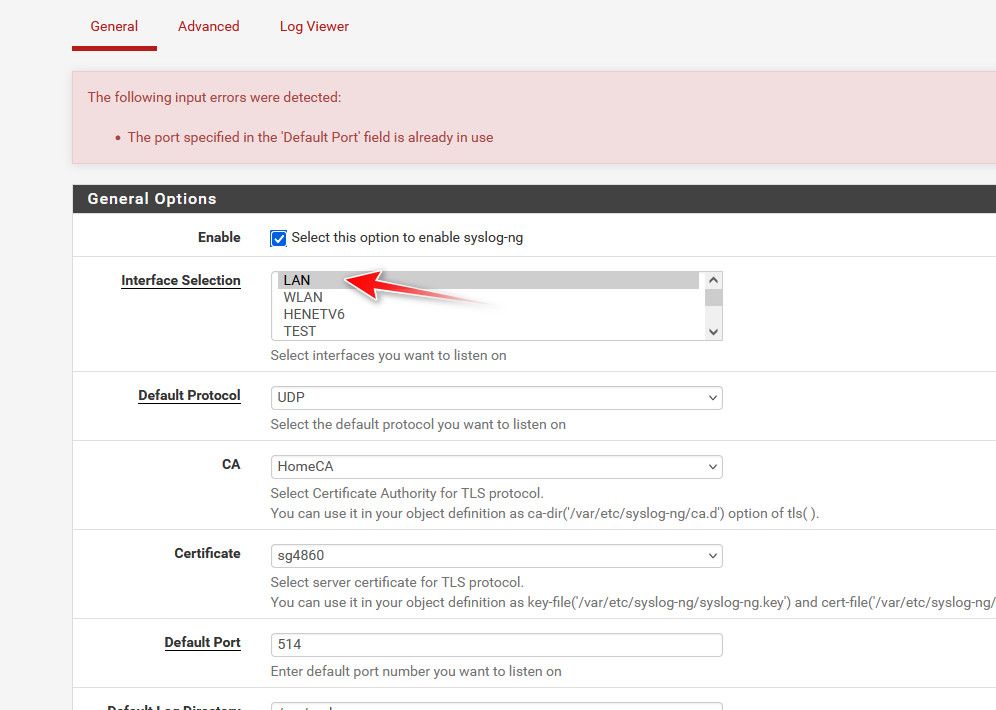
There is no way that should be an issue... Something wrong in the parsing of port in use in that package.
As to your ntp - have no idea what your going on about.. As to using authenticated ntp - sure ok, go for it.. But on your secure local network.. Seems pretty freaking tin foil hat to me.. Who and the F is going to mess with your ntp on your own local secure network, from a client talking to to your own firewall.. Come on - someone is watching too much mister robot..
So you were taking a test, and you lost 15 minutes.. Yeah that happens - you lost track of time, it wasn't your ntp server being hacked and time altered by 15 minutes ;)
Still don't get how natting ntp fixes that??
If your concerned about ntp being messed with on your own local network between a client and your firewall - you got bigger fish to fry if you ask me.. That is some paranoid level shit right there... Maybe lay off the recreational herb ;)
-
@johnpoz I saw it wouldn’t let me set it to the port I needed so I improvised. That time thing only occurred when I was doing my AA in cyber security we had so many labs and also a red blue team exercise so I would not be surprised if an instructor wanted to expand our knowledge and see if someone went to authenticated NTP. Who knows. It was cool to be part of the nist.gov stuff. I know the latest software revision now includes the ntp stuff. I wonder if others had concerns also.
The reason I NAT ntp is because not everything uses the firewall but it will use it when requests are NAT to it. Example Windows 11, Raspberry PI they request some specific sites yes I could add a dns override for them but I just NAT any requests to the firewall and it uses the nist.gov encrypted time system. So it gets secure time. The systems get the right time and it works. It seems tinfoil hat, but no issues with time jumps ever again.