WAN TO LAN
-
@jhmc93 then what you want to read up to is pfSense Docu: Port Forwards
You have to create port forwards for the services (SSH, DNS HTTP, etc) you want to forward to your pfSense LAN.
Is there a reason you don't move everything from the ISP LAN to the pfSense LAN?
-
Possibly OP is using the ISP’s wireless?
If so this would be the rare case where using “WAN network” would be correct as the NAT rule source.
-
@patient0 pfsense is running off a machine that does not have WiFi connectivity so I have to use my ISP WiFi to connect to internet. So basically pfsense is a Cabled machine.
So port forward on the ISP side or the PfSense side?
If so how would the rule be done? -
@patient0 can u help?
-
@jhmc93 said in WAN TO LAN:
So port forward on the ISP side or the PfSense side?
If so how would the rule be done?If you want only the ISP router LAN to have access then you would not want to forward on the ISP router also, since that would let the entire Internet in to the pfSense WAN.
NAT rule:
source: WAN network
destination: WAN IP
destination port: whatever unique port you want, say 2222
redirect target IP: your server on LAN
redirect target port: SSH/22then connect to pfSense-WAN:2222.
https://docs.netgate.com/pfsense/en/latest/nat/port-forwards.html#adding-port-forwards
-
@SteveITS what have i done wrong:
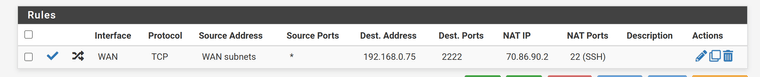
-
@jhmc93 NAT IP is the IP of the PC on LAN.
Dest Address is the IP of pfSense WAN.
You would SSH to pfSense WAN port 2222 and it forwards that to NAT IP port 22.
-
@SteveITS NAT IP is the pc on ISP LAN or the pfssense LAN? if so them rules are right and I'm getting nothing
-
@jhmc93 the NAT IP is the IP of the PC on the pfSense LAN.
Devices in front of the pfSense WAN can't see the device on the pfSense LAN, because of NAT. All they can see is the pfSense WAN IP, nothing behind it.
Port forwarding works by setting up a rule for e.g. "if a request to pfSense WAN to port 2222 arrives, redirect it to NAT IP on NAT port.
Dest. Address -> pfSense WAN IP (in the ISP router network)
Dest. Ports -> 2222 looks good
NAT IP -> IP of client on pfSense LAN you want to access
NAT Port -> TCP/22 in case of SSH -
@patient0 my bad ubuntu machine had ssh disabled. All working, Question, how will I be able to set the rule so it lets me use my traefik dns records stored on pihole
-
@jhmc93 said in WAN TO LAN:
Question, how will I be able to set the rule so it lets me use my traefik dns records stored on pihole
Similar to the SSH, you would have to forward DNS request to the pfSense WAN.
Let's say you forward port UDP/10053 on pfSense WAN to port UDP/53 on pihole. That way clients can query the pihole on pfSense-WAN:10053 and get the result from pihole.BUT knowing the IP (IPs?) of the Traefik in the pfSense LAN won't be of much use for you. You get back pfSense LAN IPs and you'll need port forwards again to access it. (I looked up traevik -> cloud native application proxy) Of course you can forward a range of port to it.
-
@patient0 So
traefik runs on pfsense LAN on IP: 10.84.62.5
Pihole instance is running on ISP LAN IP: 192.168.0.8
So my Pfsense has 192.168.0.8 as the dns server and then in the A record it points to my traefik IP,
hope this helps in helping me do a rule -
@jhmc93 said in WAN TO LAN:
So my Pfsense has 192.168.0.8 as the dns server and then in the A record it points to my traefik IP,
hope this helps in helping me do a ruleYes, is understand. But if a client on the ISP LAN asks the pihole for the traefik IP, it get's back a pfSense LAN IP, no - something like 192.168.0.x? What use is that IP for a ISP LAN device? It can't access it anyway, the whole 192.168.0.0/24 network is hidden behind the NAT of the pfSense?
-
@patient0 So my pihole that runs on ISP LAN is pointing to my Traefik on the PfSense LAN but... the IP of the Traefik instance that the A record is pointing to is a Tailscale IP
-
@jhmc93 said in WAN TO LAN:
pihole that runs on ISP LAN
Ah, sorry I got that mixed up, I'm old and almost senile :/
the IP of the Traefik instance that the A record is pointing to is a Tailscale IP
Okey, I have no idea how to make that work.
Tailscale has it's own DNS, MagicDNS or something, no? And the Tailscale IPs are 100.x.x.x IPs, no? Is Tailscale running on traevik itself?
pfSense has no route to that 100.x IP, it seems easier to use a Tailscale DNS if possible, but that is not something I know anything about.
-
@patient0 what if I changed it to the local IP on the A record, the rule u sent above could that be doable if the redirect ip was the pihole instance?
-
@patient0 did that make sense
-
@jhmc93 said in WAN TO LAN:
what if I changed it to the local IP on the A record, the rule u sent above could that be doable if the redirect ip was the pihole instance?
Mmhh, the issue would still be that the local IP is of the pfSense LAN (10.84.62.0/24?) and of no use for ISP LAN devices.
If you setup port forwarding on the pfSense to traevik, let's say port 9000 to 9500 will be forwarded to traevik, then the A record for traevik on pihole would be the pfSense IP 10.84.62.5.
I realize that I don't know how Traefik works, does it work with ports to choose to which service to forward or with URLs/paths?
-
@patient0 all ports are set in traefik config so local.example.com points to port 9000 in the traefik config so when u add the dns cname record it goes through pihole and traefik resolves local.example.com to port 9000 that's set in traefik yaml config
also are u saying due to my pihole being on my isp lan it wont connect to my traefik ip on the pfsense lan?
-
@patient0 r u there?