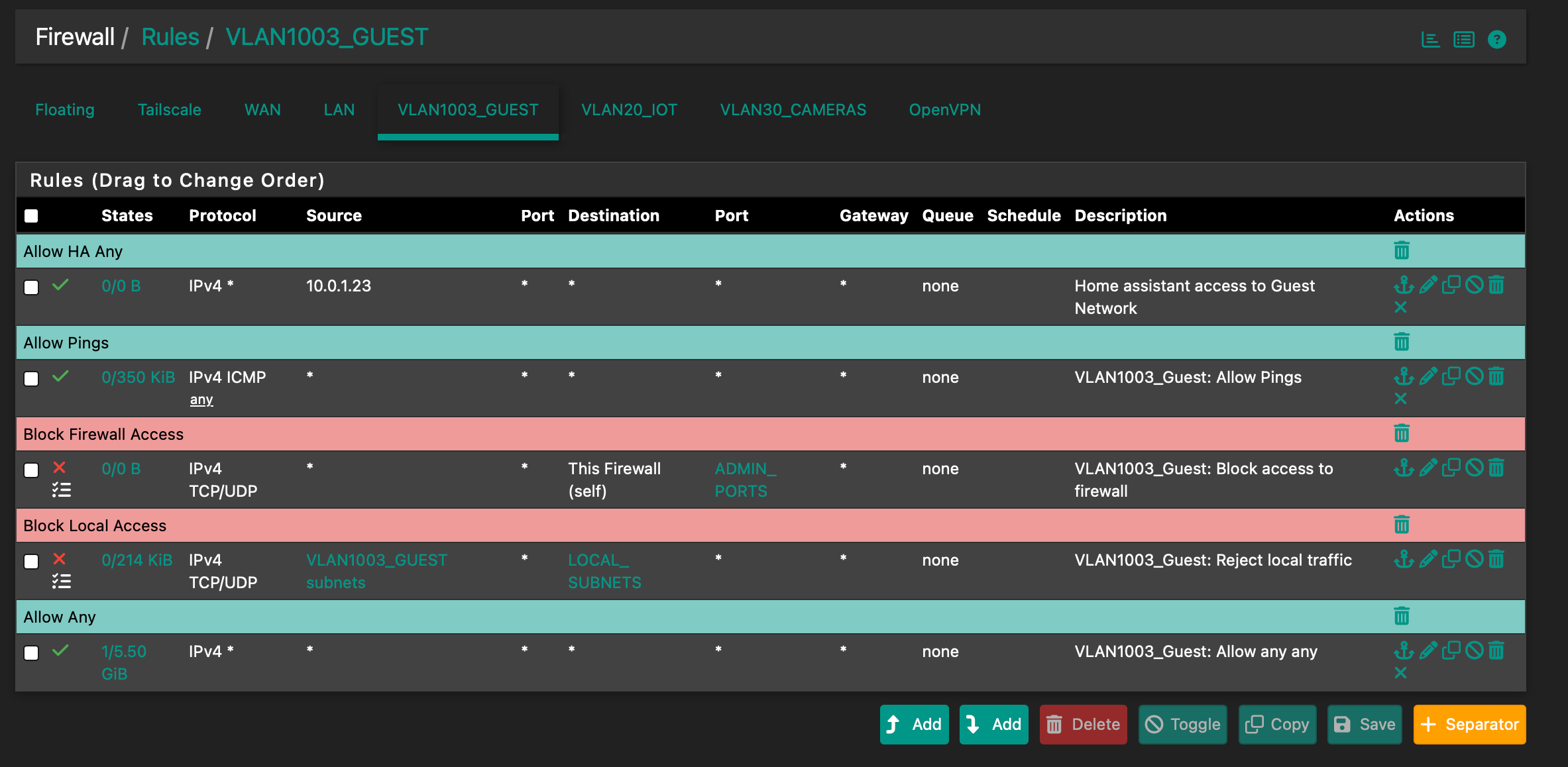
Allow Any Any question regarding guest network
-
Current rules for guest-

I know the Allow Any Any is evaluated last but I don't remember creating it and not sure if it's right. Shouldn't it be a Block Any Any?
-
@wgstarks What are you trying to accomplish/allow/block on this network?
Edit: only LAN has a default allow all rule.
-
I honestly don’t remember creating that rule. I was adding a rule to allow home assistant access to the guest network from its IP on LAN when I noticed the rule in question. I’m really not sure why this rule is needed or if it’s even a good idea?
-
@wgstarks well without it 10.1.0.23 can get to anything (that’s this subnet right?) and things can ping, and nothing else would be allowed.
-
I get that but should the guest network have an allow all rule? This opens the guest network to all traffic from WAN right?
-
@wgstarks Rules apply as traffic enters an interface. Source: VLAN, dest any. Even if it doesn’t say it, traffic only arrives on this VLAN.
-
@SteveITS
Thanks -
@wgstarks said in Allow Any Any question regarding guest network:
I honestly don’t remember creating that rule.
edit the rule, and go to the bottom of the page.

Last decade or so, this info wasn't there.
Is your pfSense that old ?@wgstarks said in Allow Any Any question regarding guest network:
Shouldn't it be a Block Any Any?
Easy to fact check : delete all rules on an interface. All of them.
Now, connect a device and see what you can do - can access out of your own local network : not much. Like : nothing.
One upvote for you if you can tell us what still works without any GUI firewall rules

The thing is : the default behavior of 'pf', that's the firewall used by pfSense, is : "block" so there is no real need to place a block rule at the bottom position in the GUI as the very last 'pf' rule will be 'block all' anyway.
-
@Gertjan
It appears it was created by me a little over 7 years ago. No surprise I don’t remember. Sometimes I have a hard time remembering last week.
I tested connections to other networks last night after reading @SteveITS post. You are both correct that any attempts to connect to other networks are all blocked.
I’m still not sure that the allow any any rule serves a purpose though? Wondering if it should be deleted? If I’m understanding correctly it will allow machines on LAN to connect to machines on the guest network. Wouldn’t it be better to block by default and set specific allow rules for circumstances where connections are needed?
-
@wgstarks said in Allow Any Any question regarding guest network:
I’m still not sure that the allow any any rule serves a purpose though?
Actually, I'm only using the Any rule : see the mast two rules here :
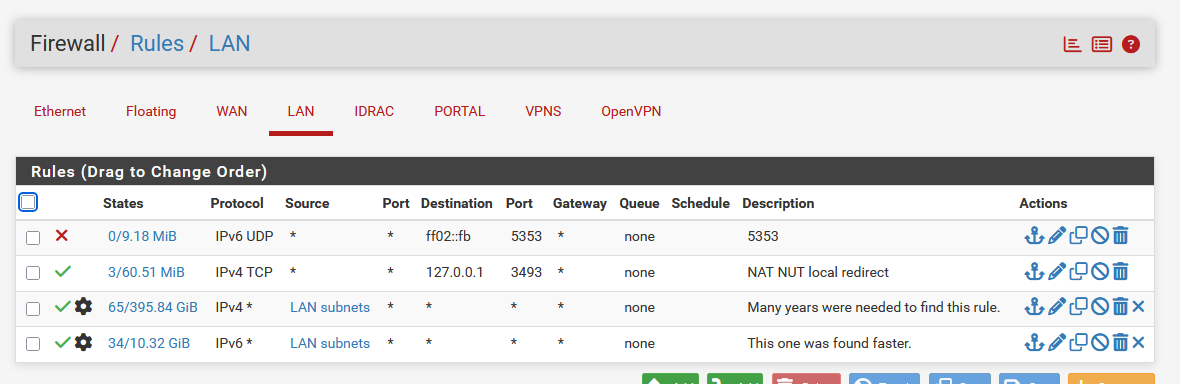
as I'm the one paying for the connection, I'm not going to block myself

The Source will always be a device on that network - and not some other network, so Source is defined, in my case "LAN subnets" and not an 'Any' - it couldn't be Any anyway.
Works fine for me

edit : sure, typical Guest networks should contain some limitations, as
Guests ... tend to go anywhere.
You .... the one paying, can wind up in court as you are responsible for your connection ( which you shouldn't share with non trusted users as this is probably mentioned your ISP usage agreement ). -
@wgstarks said in Allow Any Any question regarding guest network:
Wouldn’t it be better to block by default and set specific allow rules
That is how pfSense and most firewalls work. That's why I asked, "What are you trying to accomplish/allow/block on this network?"
LAN by default allows to any.
All other interfaces in pfSense have only the default deny rule and zero additional rules. So you should ask yourself questions like:
- do these PCs (this network) need DNS from pfSense?
- should these PCs be able to ping pfSense?
- do these PCs need to get to other local networks?
- do these PCs need to get to the Internet?
- etc.
Then create your rules as for what you want them to access.
Since it is labeled as a "guest" network this might be helpful: https://docs.netgate.com/pfsense/en/latest/solutions/netgate-4200/opt-lan.html#isolated
-
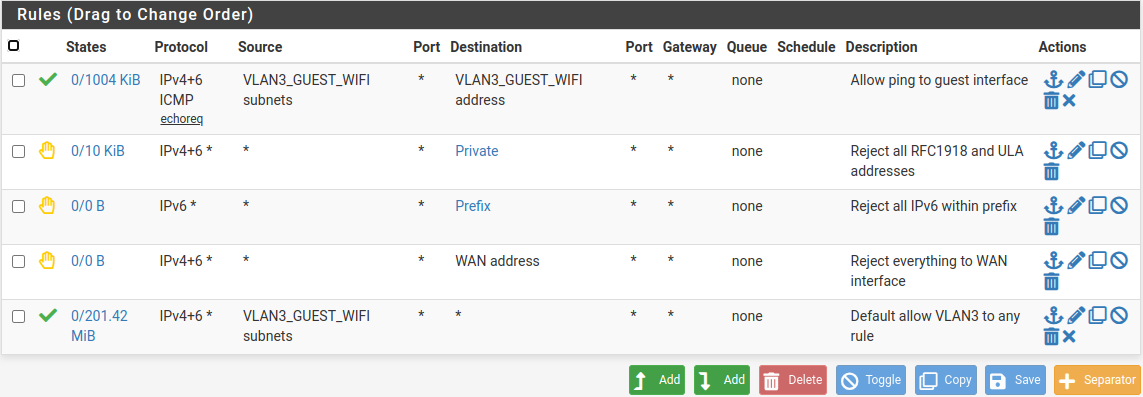
Here are my guest rules:
-
@SteveITS said in Allow Any Any question regarding guest network:
That is how pfSense and most firewalls work. That's why I asked, "What are you trying to accomplish/allow/block on this network?"
LAN by default allows to any.
Thanks ... it came just now to my mind that I misread the initial post/question.
The pfSense LAN is meant to be used for the trusted devices, like the admin access, and so on.
The default LAN rules are pass-all.
All others - let's say less trusted users - should go on another interface.I've such an interface, network : my captive portal used for a hotel :

and I use pfBlockerng to block the most obvious "no-no-don't go" hosts.

and all these :
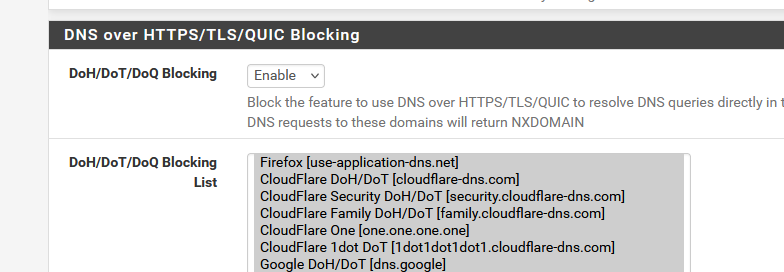
and

Don't ask why I add "Astrology", I'm not sure what it is ^^
The first list, as I'm a hotel, isn't really important

Activating it also demands way more RAM as what my 4100 has. -
This is just a network for visitors to my house and a few IoT devices. They only need access to DHCP, DNS, NTP perhaps (all provided by the firewall) and the internet. Home Assistant needs access to some of the IoT devices so I have created a pass rule from the HA device on LAN to the Guest network. None of the devices on Guest should have access to LAN or any other local networks and I don’t really see a reason to allow access from local networks to the guest network other than the specific instance mentioned. Am I missing something?
-
@wgstarks Ok so:
- block what you want to block
- allow any will let devices on this subnet get to the Internet
Did you ever say what 10.1.0.23 is? If that's not an IP on this guest network the rule is pointless since traffic will never arrive on this interface from an IP that isn't behind this interface. Note it shows 0/0 so has never been triggered/matched.
-
@SteveITS said in [Allow Any Any question regarding guest network]
Did you ever say what 10.1.0.23 is? If that's not an IP on this guest network the rule is pointless since traffic will never arrive on this interface from an IP that isn't behind this interface. Note it shows 0/0 so has never been triggered/matched.
10.0.1.23 is the LAN address for Home Assistant. Obviously I have not set this rule up correctly. How should I setup a rule to allow this LAN address to connect to the Guest network?
-
@wgstarks said in Allow Any Any question regarding guest network:
How should I setup a rule to allow this LAN address to connect to the Guest network?
You would need to create it on LAN.
Though if LAN still has its "allow to any" rule then another one for this IP is not actually necessary.
-
hey there,
I solved this by adding a rule like "reject / guest_network / RFC1918 (alias)".
Followed by "pass guest_network / any / Port collection to allow https, android playstore, mail..." the typical "can I use your internet for a moment?" moments...My IoT stuff has its own subnet, here only home assistant is granted internet access (updates), the rest ("smart TV, IoT devices) are ususally blocked. Once every few months I allow that for updates.
In case you want ALL LAN clients to reach guest...stick with it. Otherwise define your rules more specific. :)
-
I removed the allow any rule from the guest network but now that network no longer has access to WAN. What ALLOW rules do I need to add to give users on this network access to WAN, DHCP, DNS, NTP?
-
@wgstarks So to be clear you want VLAN1003_GUEST to access the WAN network but not the Internet?
I would start by just writing down what you want them to access, and where it is. Then the rules are apparent.
If you are using pfSense for DHCP, pfSense automatically adds rules on an interface so DHCP works, when DHCP server is enabled. So in that one case you don't need a rule.
If you are using pfSense for DNS then you need a rule to allow VLAN1003_GUEST Networks to "VLAN1003_GUEST Address" on pfSense, port 53, TCP/UDP.