set up pfSense as additional gateway into VPNs
-
@sgw
The idea of configuring the LAN as DHCP client was to get maximum flexibility. The device doesn't need a static IP for what you're aiming and if the remote sites admin want to assign it a certain IP for whatever reason he could do this by a static mapping.
But for sure you can also go with a static IP. -
@viragomann I agree. Tested with static IP on LAN also, looks good.
The test box is on the way to the customer, for the next stages of testing.
Thanks again. -
Unfortunately I have issues with testing this.
The box is connected at the home of their coder.
The box gets DHCP-IP, connects to OpenVPN, everything up ...
I search for around 3 hrs now:
He adds a route on his windows PC, and tries to ping a server at the server site.
I packet capture on both pfsenses:the openvpn server side and the openvpn client side
The ICMP request gets to the target server, I see the reply packet on the LAN interface of the OpenVPN server pfSense ... but NOT on the tunnel interface.
The reply gets routed to the internet and NOT into the tunnel (on the ovpn-server-machine, to be redundant).
The routing table looks correct to me.
I can replicate that with MTR. And I don't know the reason.
I can add the subnets etc if helpful
-
more details, sorry for flooding:
openvpn-client-side: LAN-IP: 192.168.8.57
the client gets access to this server-LAN via CSC: 192.168.1.0/24
I see routes created on the server:
192.168.8.0/24 via ovpnc1 ..
There is no 2nd subnet like this at other ovpn-clients, I double-checked that.
Route on the ovpn-client-pfSense:
192.168.1.0/24 via ovpnc ... ok as well
I can ping the LAN-IP of the ovpn-client-pfsense from the ovpn-server. But NOT from LAN.
firewall rules checked, windows-firewall (the server machine to be reached is MS Windows Server) disabled for debugging
This is quite confusing right now
-
I installed mtr on the ovpn-server.
A ping to the LAN-IP of the ovpn-client should go through the tunnel, I also see according rules in the ovpn-routing-table. But not in the general routing table ... I assume that's correct this way, it looks similar for the ~20 other ovpn-clients.
The mtr run shows that the ICMP-packet is routed to the default gateway instead.
That's wrong. -
@sgw
On the OpenVPN server you have to specify the remote networks correctly to get the routes set.
And also you need to create a client specific override for the client and as well specify the remote networks there.Are you missing these settings?
-
@viragomann thanks
no, I have these ... see the CSC:
in IPv4 Tunnel Network I set a specific Tunnel IP for that client: 172.31.0.121/23
in IPv4 Local Networks I add the server side LAN to be reached: 192.168.1.0/24
in IPv4 Remote Networks I have the client side LAN subnet: 192.168.8.0/24That's all. I do it like this all the time for ~20 clients ...
This client is only different in using only LAN.
On the client I see a route to the server LAN in Diagnostics/Routes.
On the server the routes to the ovpn-client-LANs are not there, but visible in Status / OpenVPN / Routing TableAnd they look similar for a working and that non-working client:
sg1100_19 88.xxx:30322 172.31.0.78 2025-04-11 12:36:43 sg1100_19 88.xxx:30322 192.168.118.0/24 2025-04-10 13:03:28 sg1100_21 185.yyy:23417 192.168.8.0/24 2025-04-11 12:30:27 sg1100_21 185.yyy:23417 172.31.0.121 2025-04-11 12:36:43That's the strange thing: it looks correct.
-
@viragomann said in set up pfSense as additional gateway into VPNs:
On the OpenVPN server you have to specify the remote networks correctly to get the routes set.
I define that in the CSCs for the clients. The OpenVPN-server itself doesn't have to be adjusted when adding clients, at least as far as I know. I only edit that in the CSCs. Right?
-
What I see and what looks suspicious:
the Default Gateway IPv4 on the ovpn-server-side points to a specific gateway and is not set to "Automatic".
For all the other clients it works but the routing for this one client is wrong:
when I mtr from the server to the client side the packets are sent to def gw and not into the ovpn-tunnel
-
@sgw
As mentioned, client sites networks have to be specified once in the server settings at "remote networks" and again in the CSO.If they are missed in the server settins pfSense doesn't add routes.
-
I don't see where to add that, and I didn't do that for the other clients.
VPN/ Server/ OpenVPN/ Servers/ Edit ?
used Search in Browser, not found ;-)
-
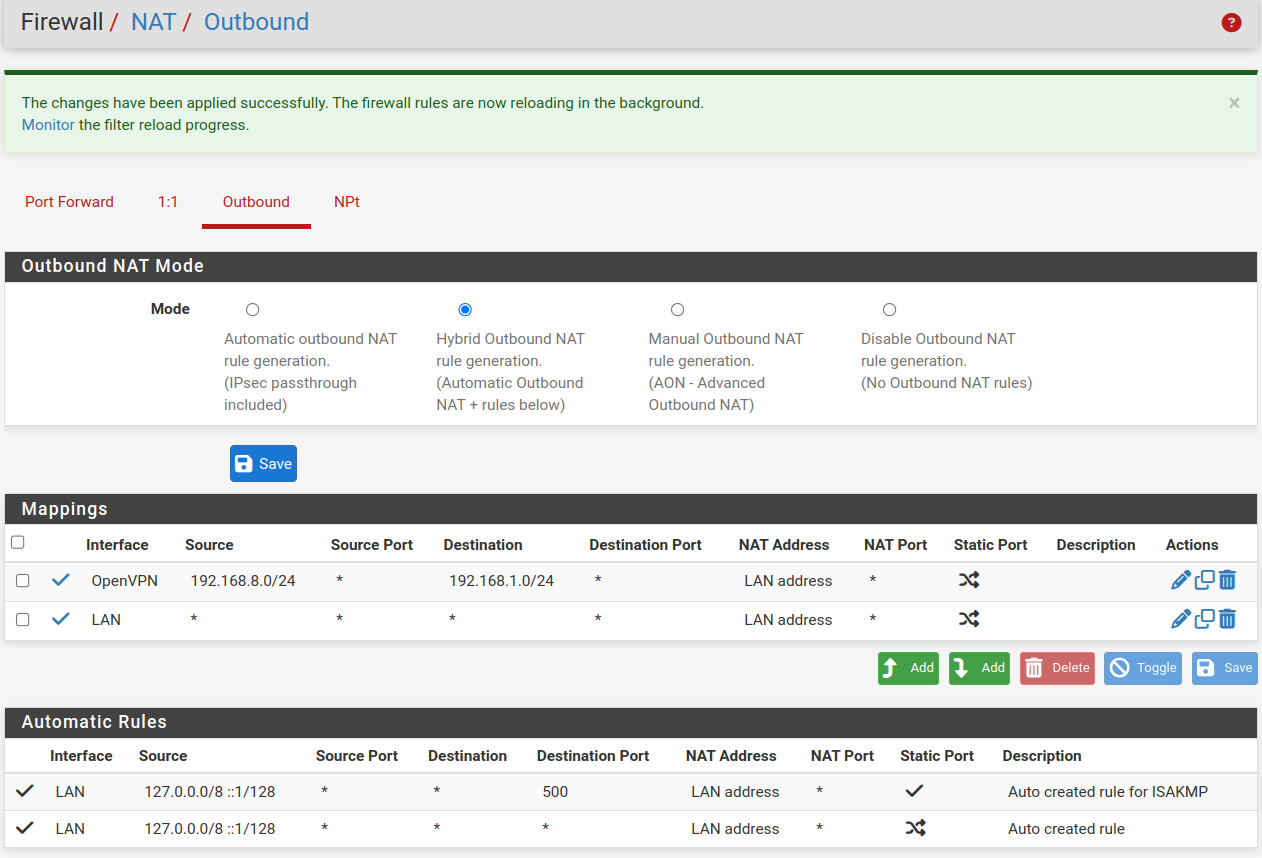
currently it seems to work after adding a NAT outbound rule on the client
OpenVPN 192.168.8.0/24 * 192.168.1.0/24
we test now
-
That outbound rule editing changed something, as if there was something changed under the hood.
Right now the admin there is able to access systems on the other side of the tunnel, as intended.
Nothing changed on the OpenVPN server, btw.
That NATing isn't fully correct still
What I'd like to have:
- server side IP should be able to ping a PC on the client side
- server side VM should be able to access a system on the client side, with a mapped IP in the client LAN
currently I have this, and rebooted for a check, the admin is able to access a server VM via RDP: GREAT, but not 100% yet ;-)
THANKS so far, I think I need some time afk now soon
-
@sgw
Yeah, outbound NAT rules (masquerading) can be used to circumvent missing routes.
I'd rather set the routes properly, but depends on the use-case. -
@viragomann I agree but I repeat: where to set these routes? See question above. Thanks.
-
@sgw
The "Remote networks" field is only available in peer to peer server mode. But this is, what you should set up for your use case. -
@viragomann Ah, that explains why it feels like barking up the wrong tree ;-)
I hope I can run that in parallel to the other openvpn-server? (separate port, sure).
Thanks so far, have a nice weekend!
-
@sgw
Yes, of course you can run multiple OpenVPN servers for different purposes. -
I set that up on the server site pfSense.
For the peer to peer VPN there is no Client Export, so I assume I have to set up a Server on the other site as well, also in Peer2Peer-Mode? For sure I browse the docs in a minute.
looking forward to solve this ;-)
EDIT: I see, seems I can follow this for example. So not a 2nd server but a specific client config. Will try monday or so.
-
I have it working mostly.
One more question: I found out that CSCs won't work for peer-to-peer-OpenVPN?
What is the way to limit access then?
If I have multiple vpn-users connecting to one ovpn-server I could only set fw-rules on the client-side of the vpn-tunnel, right?
thanks for additional insights here, I am right before setting up the 2nd client to test things in parallel (for sure with a 2nd user etc ;-) )
EDIT: CSC seems to work .. dunno where their admin had that info. Still testing things, good progress.