Allow Any Any question regarding guest network
-
@SteveITS said in [Allow Any Any question regarding guest network]
Did you ever say what 10.1.0.23 is? If that's not an IP on this guest network the rule is pointless since traffic will never arrive on this interface from an IP that isn't behind this interface. Note it shows 0/0 so has never been triggered/matched.
10.0.1.23 is the LAN address for Home Assistant. Obviously I have not set this rule up correctly. How should I setup a rule to allow this LAN address to connect to the Guest network?
-
@wgstarks said in Allow Any Any question regarding guest network:
How should I setup a rule to allow this LAN address to connect to the Guest network?
You would need to create it on LAN.
Though if LAN still has its "allow to any" rule then another one for this IP is not actually necessary.
-
hey there,
I solved this by adding a rule like "reject / guest_network / RFC1918 (alias)".
Followed by "pass guest_network / any / Port collection to allow https, android playstore, mail..." the typical "can I use your internet for a moment?" moments...My IoT stuff has its own subnet, here only home assistant is granted internet access (updates), the rest ("smart TV, IoT devices) are ususally blocked. Once every few months I allow that for updates.
In case you want ALL LAN clients to reach guest...stick with it. Otherwise define your rules more specific. :)
-
I removed the allow any rule from the guest network but now that network no longer has access to WAN. What ALLOW rules do I need to add to give users on this network access to WAN, DHCP, DNS, NTP?
-
@wgstarks So to be clear you want VLAN1003_GUEST to access the WAN network but not the Internet?
I would start by just writing down what you want them to access, and where it is. Then the rules are apparent.
If you are using pfSense for DHCP, pfSense automatically adds rules on an interface so DHCP works, when DHCP server is enabled. So in that one case you don't need a rule.
If you are using pfSense for DNS then you need a rule to allow VLAN1003_GUEST Networks to "VLAN1003_GUEST Address" on pfSense, port 53, TCP/UDP.
-
I want anyone using the guest network to be able to access the internet. I thought that that would be the same as WAN but allowing access to WAN didn’t work.
Do I also need to create a rule to allow access to NTP provided by pfsense?
-
@wgstarks "WAN network" is the network of the pfSense WAN interface. the /29 or /24 or whatever it is.
Since you don't know what IPs they will access out in the world, it's normal to allow access to "any." So:
- allow what you want to allow (e.g. guest to VLAN1003_GUEST Address for DNS, NTP)
- block what you want to block (e.g. guest to This Firewall, guest to LAN)
- allow to any
The rules are processed in order top down.
-
@SteveITS
Block rules on top right and then the pass rules? -
@wgstarks I don't know, it depends.
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-4200/opt-lan.html#apply-changes
-
@SteveITS
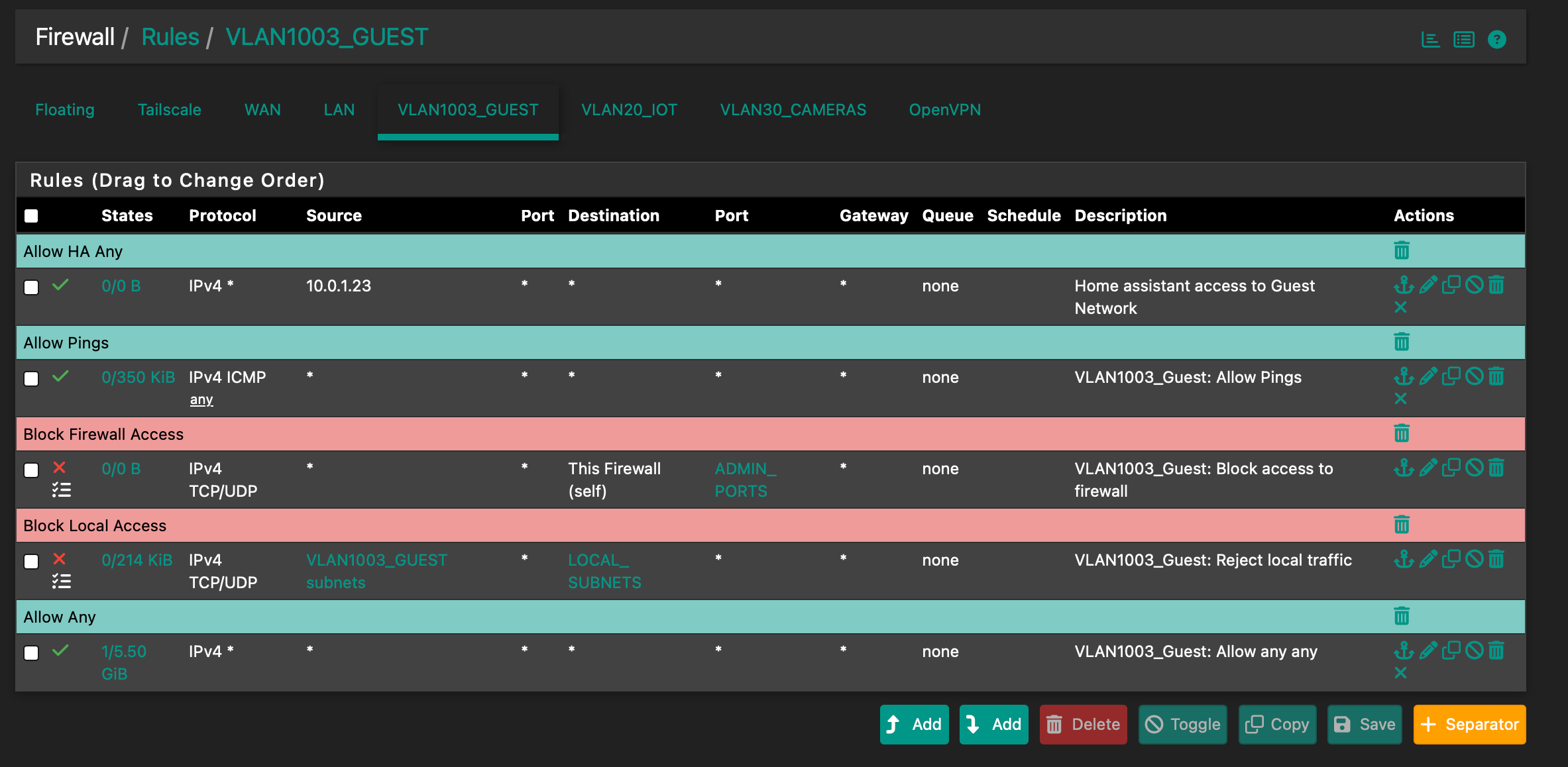
Thanks for all your help. I think I've finally gotten, or at least I'm getting close.Here is the current rules-

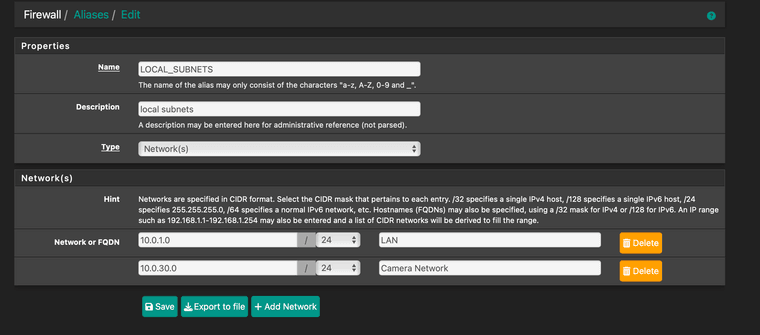
I used the LOCAL_SUBNETS alias because I already had it setup. I think it's the same as RFC 1918-
If you see any problems or anything I've missed please let me know.
-
Suggestion : like your first rule : local (VLAN1003_GUEST) devices are allowed to use the local (pfSense) DNS.
You could add also NTP (port 123 UDP) so devices can use pfSense to sync their time, if they want to. -
@Gertjan
Done thanks.