Difference Between Assigning an IP Address to a Firewall Interface vs. Assigning It to a Bridge Interface?
-
Hello Professionals,
My PFSense Plus firewall has two interfaces:
- LAN
- Server
This firewall is positioned between two switches — one connected to the LAN interface and the other to the Server interface — and is used to control traffic between these two internal network segments. In other words, it functions as an internal firewall.
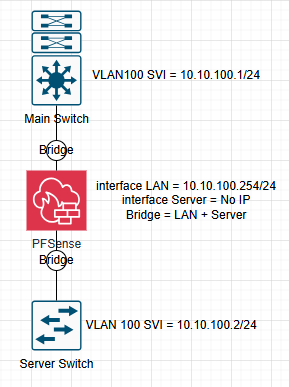
When I initially configured the device, I set it up without much trouble by creating a bridge.
I assigned an IP address to the LAN interface, enabled the Server interface without assigning it an IP address, and then bridged the two. This setup worked as intended.Now, I’m planning to add another internal firewall and configure High Availability (HA) using CARP. This raises a few questions.
If I had assigned the IP address to the bridge interface itself rather than to the LAN interface, how would the behavior have changed compared to my current setup? If the two configurations function the same, are there any special considerations I should keep in mind when setting up CARP?

This questioning came up when I started wondering: when setting up a CARP VIP, which interface should it be assigned to — the LAN interface or the bridge interface?
Thank you for your time.
-
@eeebbune
If you pull the network cable the system disables the IP configuration of the respective interface (because of missing carrier). If it is a bridge member and has the IP defined on, this tears down the other bridge members as well.
If the IP definition is on the bridge this has no impact on the other members. -
Thank you for your reply.
In that case, would you change assigning IP from LAN interface to Bridge interface? Changing configuration is better in terms of managing network?
-
@eeebbune
Yes, it's recommended to assign the IP to the bridge. And in case, that any member interface is hardware base, I'd change this.
If all interfaces are virtualized, I think, it makes no big difference. -
Could you see my testing lab please? there are actually more complex configurations.
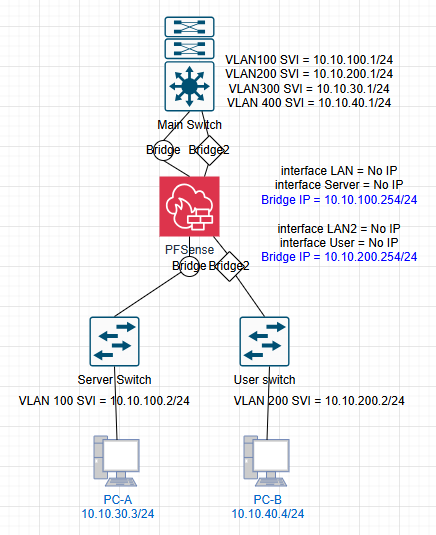
As you can see, there are two different bridge connections on the firewall.
Unlike switch interfaces (VLAN100, VLAN200), actual edge devices has different subnet addresses.My theory was:
- Providing IP address/gateway to Bridge interface rather giving physical interface port for each bridge.(LAN1, LAN2 -> BRG1, BRG2)
*BRG1 = 10.10.100.254 / gateway: 10.10.100.1
*BRG2 = 10.10.200.254 / gateway: 10.10.200.1 - PC-A and PC-B are able to communicate when I allow rule to each bridges. (Alloy any to any)
Cause, firewall system tunables has 'pfil.bridge =1 && pfil.member=0'.
However, after I gave IP address to bridge, seems like firewall discarding packets from PC-A/PC-B.
Both can't reach to their gateway. (10.10.30.1 for PC-A, 10.10.40.1 for PC-B).Looks like my idea has serious defect, and I couldn't figure out which part.
Thank you very much.
- Providing IP address/gateway to Bridge interface rather giving physical interface port for each bridge.(LAN1, LAN2 -> BRG1, BRG2)
-
@eeebbune said in Difference Between Assigning an IP Address to a Firewall Interface vs. Assigning It to a Bridge Interface?:
However, after I gave IP address to bridge, seems like firewall discarding packets from PC-A/PC-B.
Assigning IPs to the bridges shouldn't have an impact on the communication normally. It's even not required in your setup to assign IPs to both. You only need one IP on pfSense for management purposes.
Both can't reach to their gateway. (10.10.30.1 for PC-A, 10.10.40.1 for PC-B).
Even if you have pass any-to-any rules on the bridges and on the member interfaces?
-
@viragomann Yes, actually, I made Allow any to any rules for all interface including bridge interfaces for testing. I wanted to see traffics going right direction and compare what I expected.
However, after I provides IP address to bridge, I'm getting less information from firewall.From the firewall state, (PC-B to PC-A)
[Any 10.10.40.4 -> 10.10.30.3 SYN_SENT:ESTABLISH]
BRG2 10.10.40.4 -> 10.10.30.3 SYN_SENT:ESTABLISH
BRG1 10.10.40.4 -> 10.10.30.3 SYN_SENT:ESTABLISHHowever, I found two solutions.
- Creating rules in floating tab with enabling quick
- Make BRG1, BRG2 as a one interface group and creating rule.
I have no idea why those can be the solutions but seems like there's something related rule priority.
Thank you for taking care of my issue.