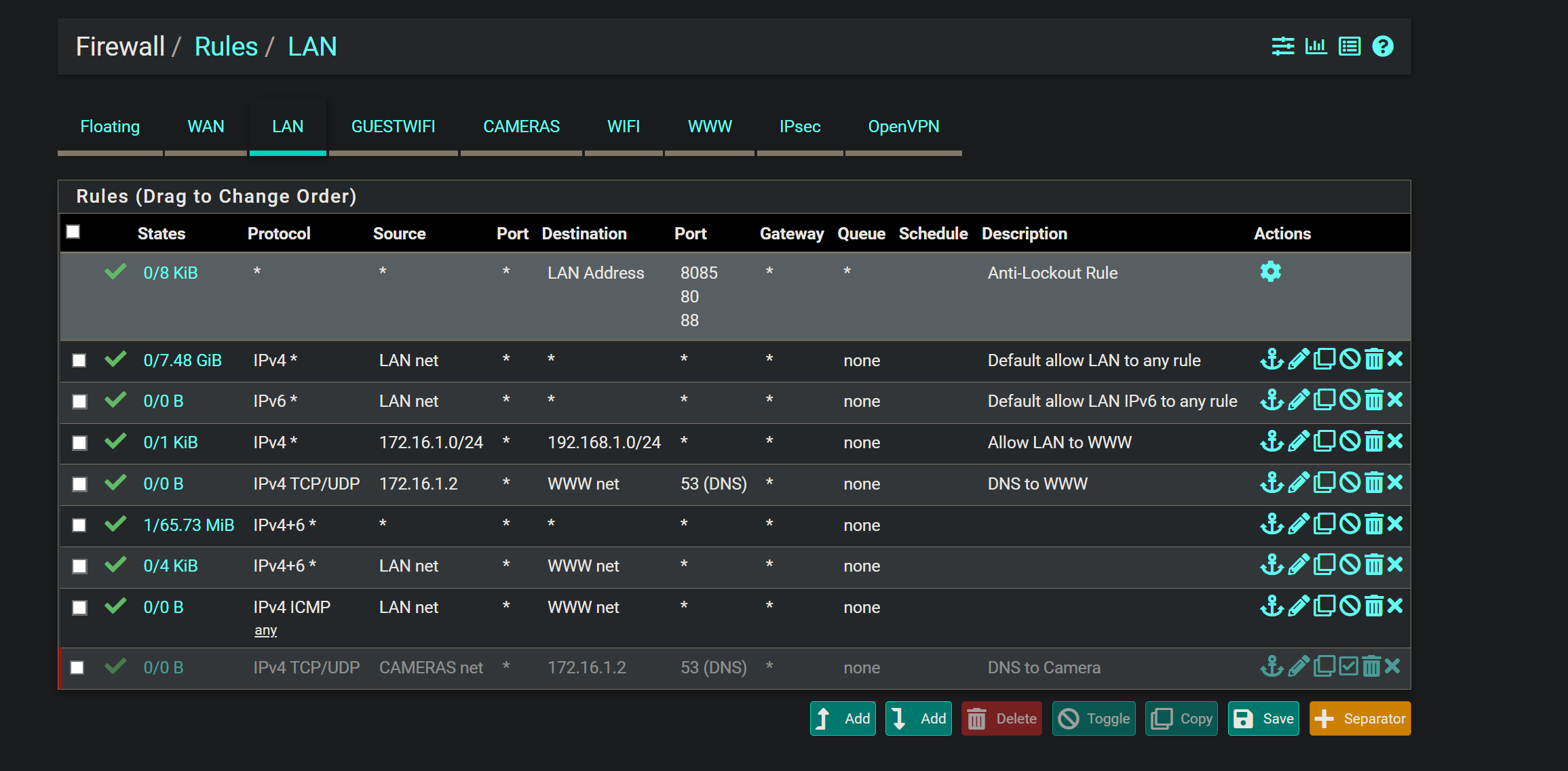
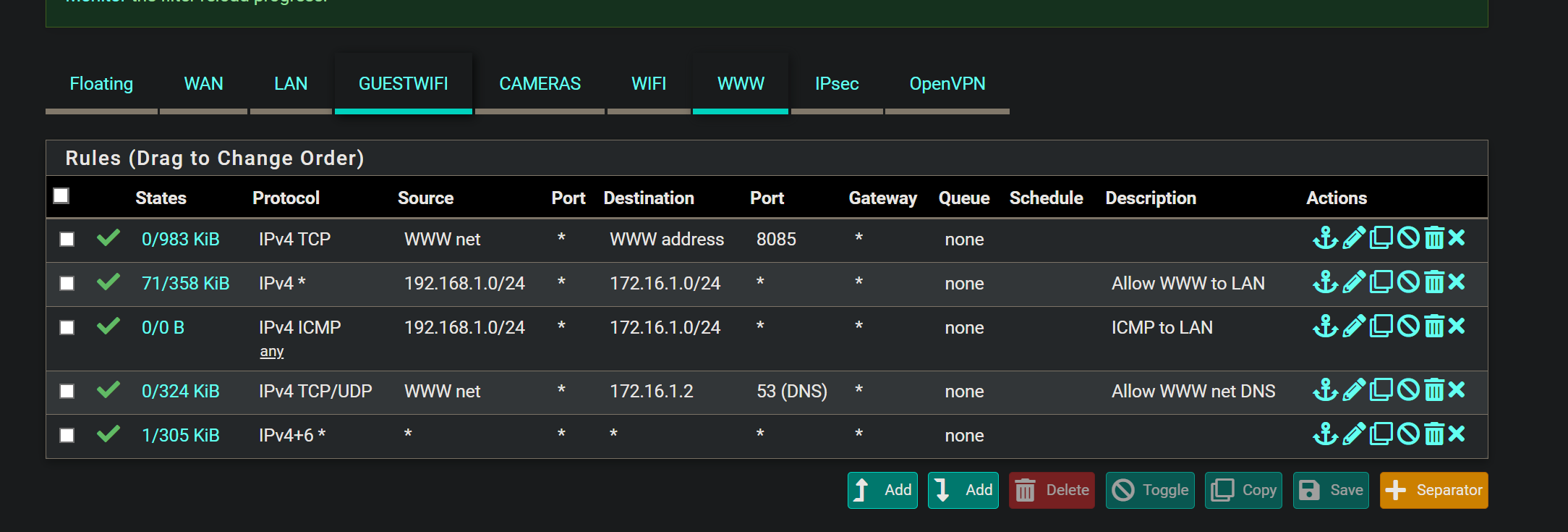
Inter VLAN Access
-
I have read many articles, followed AI-generated steps, and used pfSense for a few years (with one subnet), but I am having issues getting access between the LAN subnet and the VLANS. I have managed to get PING to ping the 'gateway' for each VLAN from the LAN, but not the other way around. I think once I get the method down, that works, I should have it, or I am missing something important somewhere else.
I have Windows servers on the LAN subnet (172.16.1.2, 172.16.1.3, 172.16.1.4) that feed DNS, and 172.16.1.2 that feeds DHCP.
I want to get DNS from the LAN servers and send it to the VLANS.
I want to be able to PING from the LAN to all the VLANS and vice versa.I have tried several rules on the LAN side, the VLAN side, and back, but none seem to work. I can add a rule to hit the WebGUI, and it works. So, I believe the rules are working, but I am just stuck.
I would appreciate some ideas on resolving this.
Here are just some things I have tried:
Thanks!
-
@Overcon All rules on any interface are only inbound. That means you can only control IPs connected to that interface, what they allowed to reach and what not. If you want some device on VLANx to connect to some other device on LAN, you have to do that on VLANx, not on the LAN.
Also top to bottom, first match wins. Your screenshots show that you didn't do it right, yet. -
Inter VLAN Access
When you initially installed pfSense, you found on the on LAN interface these two rules :
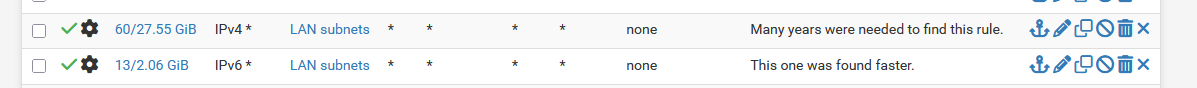
Then you created 'more' LANs (VLAN, whatever, its all the same at this point).
Use the copy icon on the IPv4 rule on the LAN interface, and assign it to a new other LAN(VLAN) ....
and - wait for it .... => change "LAN subnets" source to name of of that interface, like your "GUESTWIFI subnet".
Save.
Do the same thing for the IPv6 rule.Repeat all this for your other new LANs(VLANs).
Now Apply all.
Done.All LANs(VLANs) can now communicate with each other.
The idea is : every interface needs rules so traffic can enter that interface.
Btw : you use VLAN, not normal LAN - possible stress, pain and a steep learning process is still ahead.
AI should have told you not to use VLANs, but classic LANs as way easier to set up and maintain.
There only one physical part to admin LAN : slide in a NIC in on both side and plug the RJ45 cable. Done. No mouse, no strange interfaces, no hassle. Easy to rebuild when thing go wrong
VLANs can be useful of course, for example when you have a shared SSID AP.
-
@Gertjan @Bob-Dig
Thanks, guys. I have tried copying the default allow rules from LAN, but I am still getting blocked by a Default Deny. I have even tried accessing via creating an EasyRule, but still no luck.
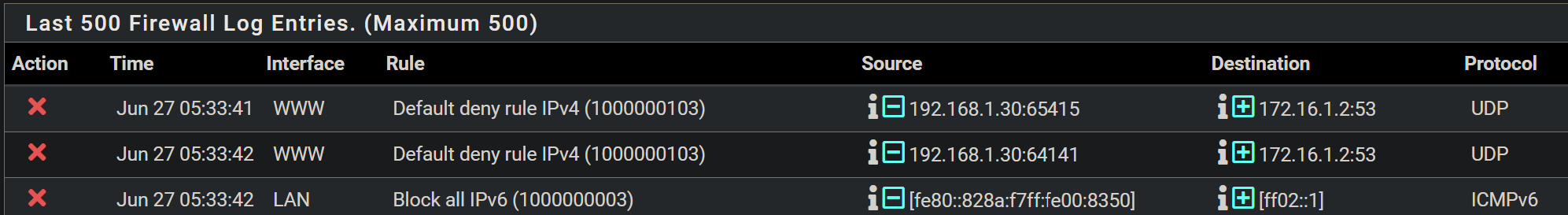
-
@Overcon said in Inter VLAN Access:
but I am still getting blocked by a Default Deny
You should use the (default) rules proposed by Netgate. You can trust these guys, they created pfSense, and know about firewalls.
These two :
can happen anymore as you've added :
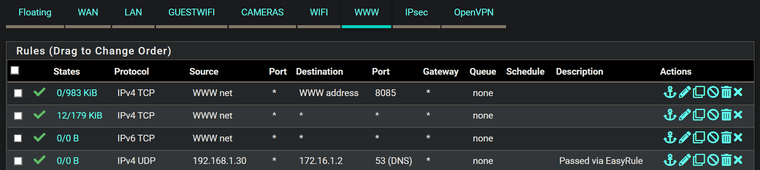
although your WWW firewall rule set is already problamatic.
The first 3 rules are TCP only, that ... can be done, but is already fishy - not a real live scenario.
Rule 2 and 3 are doubles, one is useless.
Limitations of rule 1 are overridden by rule 2 (and 3).Get the default rules back in place, and use Diagnostics > Packet Capture and scan your traffic for a while.
You'll be seeing https, DNS, NTP, and many many others.
Then make your own list with what you allow, and what not.
Then you build your rules upon your choices.
And then you test and see what's broken ... and you redo the process.And after a while, and this can take weeks, you get back to the original Netgate's proposition :
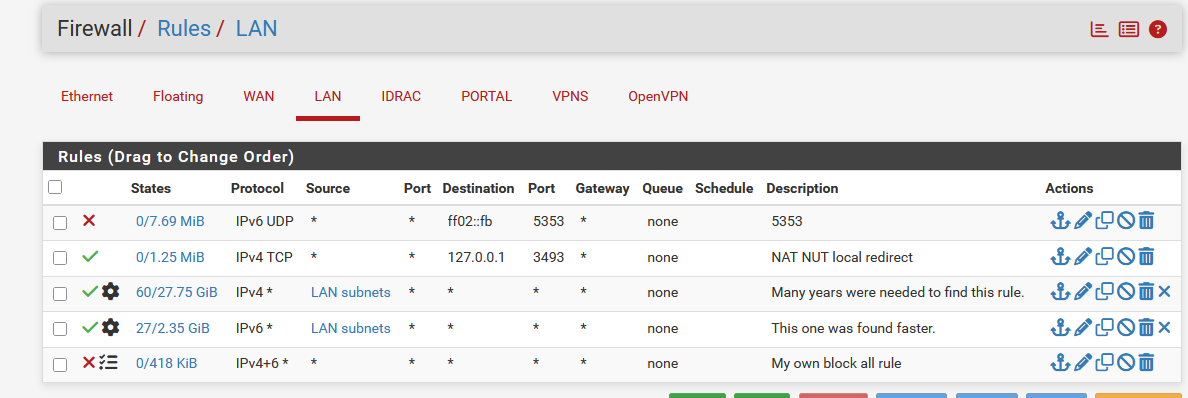
(rule 3 and 4).and live will be good.
That said, you have a firewall, as we all have. Even the basic ISP router or the most stupid TP-Link from Walmart uses a firewall.
You still have to check all your devices (on your LANs) and see what they do, what traffic kind of traffic they generate, what you will accept, what you don't accept, etc. You should do this even before opting for a firewall with more bells and whisles like pfSense.
True, with pfSense you can packet capture to see what goes down the LAN(s). -
I figured it out. It was my old IPSEC tunnel. It was capturing the traffic, so the rules never really impacted the traffic. Once I removed the IPSEC tunnel, the rules started working, as mentioned.