Is this a suspicious connection? Might be related to Windows Update but not sure
-
@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
fresh Windows installation
And you've forgot to mention the Windows version.
Home or Family ?
Then what you see is totally normal....... : 80
This is somewhat awkward ; port '80' isn't used anymore. It offers you the possibility to packet capture the packets from this PC, and see what is in the data payload.
That said, who is 208.89.74.29 ? tells me that 208.89.74.0/24 isn't Microsoft, neither Microsoft affiliated.
Using a good firewall, or not, you still have to use Ctrl-Alt-Del on your Windows PC, select task Manager and look op every task/process and if it isn't Microsoft signed, ask yourself really if you need, or not.
Better : get Process Explorer v17.06 which is so good that Microsoft finally bought it. -
@Gertjan It is Windows 10 Pro. I see the connections on all my computers that have Windows 10 installed. It only comes up once in a while and not consistently enough to capture it. I mostly see it after the fact. Can I set it up so it automatically gets captured if it shows up?
The task is svchost.exe with a Windows service executing it afaik. I already used TCPView and Process Explorer but it never comes up. I only found it because I have Binisoft Windows Firewall Control installed. Maybe it is a CDN used for Windows Updates being pushed?Because look at this. Unde relations on Virustotal it shows Windows stuff
https://www.virustotal.com/gui/ip-address/208.89.74.27/relations -
@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
Can I set it up so it automatically gets captured if it shows up?
Packet capturing is a diagnostic tools and should be executes under full administrator control.
Capture files can get huge very fast => you pfSense will run out of disk space ....(and implode).@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
I already used TCPView and Process Explorer but it never comes up
Doens't come up ?
"svchost.exe" is a process that have dozens of instances running all the time.
It's a very close to the kernel process.
And it's very "Windows", so it must be ok.@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
Maybe it is a CDN used for Windows Updates being pushed?
For example

You can't be the only one finding these IPs. Somebody else already found what you found.
So Google know about it.
So, it normally should take a couple of seconds before you' know' - and probably also : is it ok ? - or what to do, etc. -
@Gertjan Well I missed it again when it happend. I don't really know how to catch it. I also don't find anyone discussing it online so it remains a mystery. I don't like seeing stuff making outgoing connections that can't be explained. And I am a novice when it comes to packet capturing. I hope it is not a sign of a compromise however.
-
@rasputinthegreatest that company is a CDN network... So its highly likely they are hosting some sort of data for updates..
Traffic to 80 could just be a simple check if you could get there.. As to capturing it - and since its CDN the IP would normally change - what i would do is setup a packet capture under diagnostics - let it run with destination port 80 and their cidr 208.89.72.0/22 or whole asn.., AS999
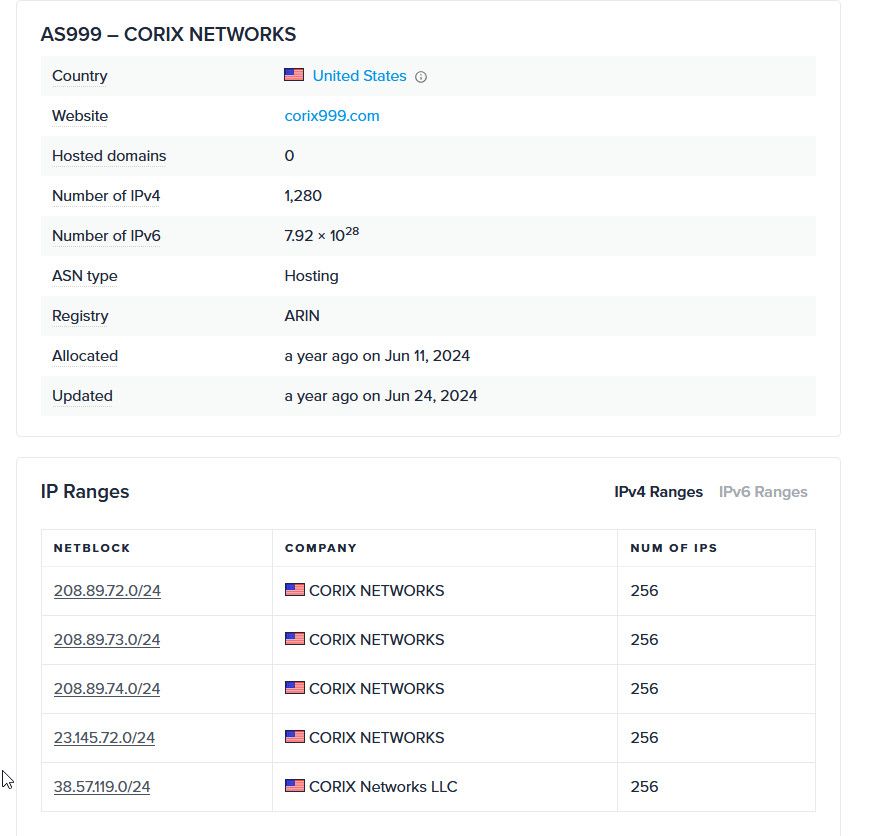
You should prob also log dns traffic.. you can log with unbound,
server: log-queries: yes log-replies: yesIn your unbound advanced option box - then when you log that traffic, might even want to setup a special rule for the cidr/asn that logs that specific traffic. But if you want to know what it is - you should allow it. So you can see what comes back with the http.. Could be something as simple as success, or a redirect maybe, etc.
Then look in your dns log for just before you see the traffic in your firewall for what was queried for, ie the fqdn.
-
@johnpoz said in Is this a suspicious connection? Might be related to Windows Update but not sure:
and since its CDN the IP would normally change
Yeah I sometimes see 208.89.74.17, 208.89.74.27 etc.
@johnpoz said in Is this a suspicious connection? Might be related to Windows Update but not sure:
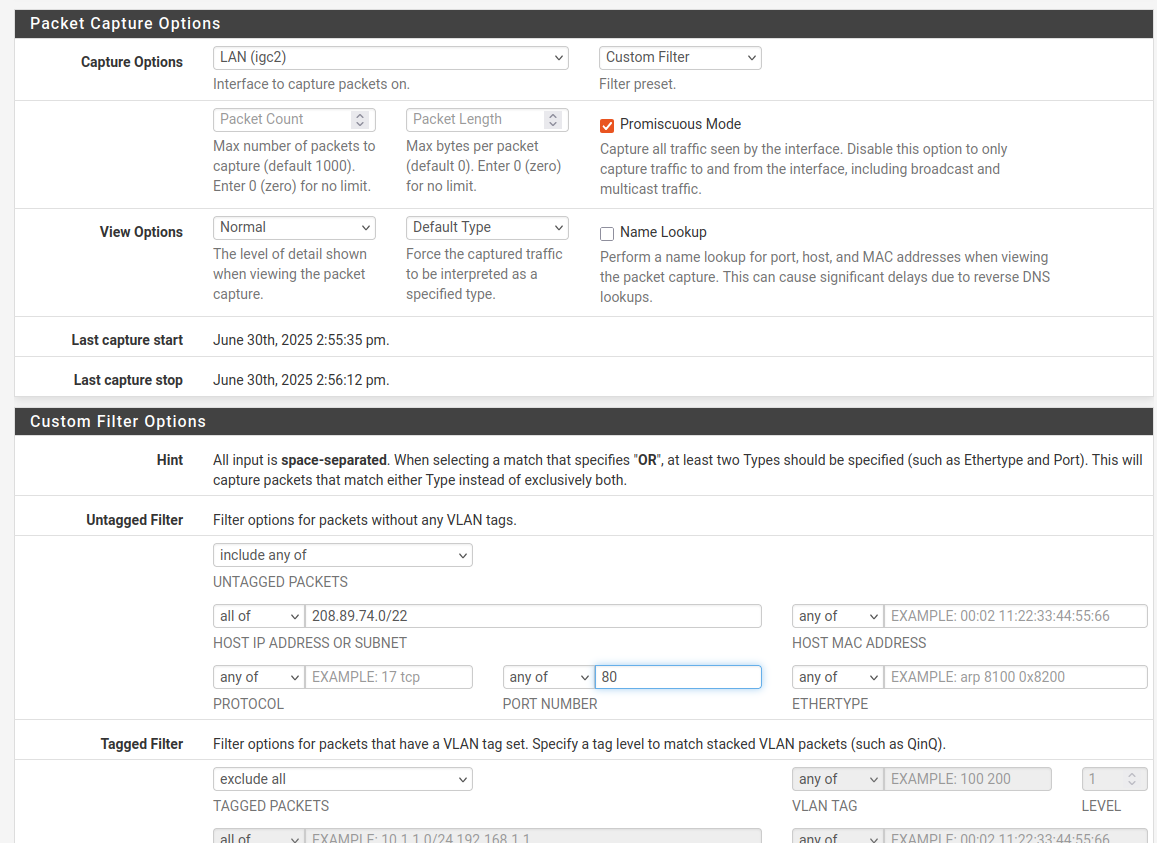
it run with destination port 80 and their cidr 208.89.72.0/22 or whole asn.., AS999
Is this correct? And then I just let it run in the background? Does the capture stop if I leave the webinterface? And how do you capture the whole ASN?
-
@rasputinthegreatest yup that should work.. But you should allow the traffic so you can see an answer - all your going to see is query, but that should include the fqdn your going for in the get. So you prob don't need the dns logging.
But I would be curious what the response is, should give you clue to what its being used for - but I highly doubt its anything nefarious.
I just setup a packet capture myself to see if my windows 10 is talking to that IP range I looked and didn't see anything in the state table, etc.
-
@johnpoz The last few times I saw it was between 2 and 3 pm on my private and work computer. Since the work computer is provided by my firm and runs Sentinel One I doubt it would be a malicious connection.Hopefully it is nothing nefarious.
I just remembered that I had enabled all Snort rules at one point and that an IP from that range got marked for "ET INFO Packed Executable Download". The capture was incomplete since I ran Snort in blocking mode. So I couldn't find out the content or extract if from the pcap
-
@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
So I couldn't find out the content or extract if from the pcap
The packet payload is most probably encrypted (TLS !) so no one (not pfSense) can decode it, so deduct any information from it.
-
@Gertjan It was http which concernes me. I have a snippet from Snort and it was port 80
BTW this site suggests a very high detection rate for malicious files
https://otx.alienvault.com/indicator/ip/208.89.74.27
That is concerning -
@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
https://otx.alienvault.com/indicator/ip/208.89.74.27
Wow.
Do what needs to be done : re install clean.
And with clean I don't mean the factory build in OS partition but a clean, real, official ISO from microsoft.com.
Or have a talk with the 'users' of these PC's. -
@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
https://otx.alienvault.com/indicator/ip/208.89.74.27
both your personal and work computers are going there?
-
@johnpoz Yes thats why I blocked the IPs. My work computer should be totally isolated since it is managed by my firm. I didn't see the IP today.
@Gertjan I already reinstalled these computers so I don't know what else I can do. I used the official ISO from Microsoft with their USB creator on a secure device. Unless my network is compromised on some other end I don't really know what I can do? I don't see any states in the firewall that point to malicious IPs or at least none I look up show as bad except for this one
https://otx.alienvault.com/indicator/ip/150.171.28.10
I also doubt if my PC was compromised my IT department would not have noticed it. I don't see any unusual behaviour on the computers as well.Just for example if I open reddit I connect to this IP but it also shows high AV detection
https://otx.alienvault.com/indicator/ip/151.101.65.140 -
@rasputinthegreatest said in Is this a suspicious connection? Might be related to Windows Update but not sure:
since it is managed by my firm
Hmm, so generally it is not your problem?
My corporation manages my laptop. Every non-corporate network automatically triggers a VPN connection to our corporate network, so the user doesn’t have to do anything to secure the computer.
Of course, this also means that there are many restrictions for the user, since everything—or at least most things—are controlled through policy management settings, ex I can not override this VPN behaviour and other things are also managed by my corporation.
Judging by what you're saying, it's unclear what exactly your firm manages if you're doing everything yourself.
This generally raises concerns about overall security, not just about the specific IP address it’s trying to reach on the network. -
I went through the pfsense logs and under OS Account changes I see this. I didnt install pfsense in 2023. Are those default entries? On 2025-06-17 the power went out and pfsense restarted.
2023-12-06 21:12:27 [root:groupadd] cyrus(60) 2023-12-06 21:12:27 [root:useradd] cyrus(60):cyrus(60):the cyrus mail server:/nonexistent:/usr/sbin/nologin 2023-12-06 21:12:30 [root:groupadd] messagebus(556) 2023-12-06 21:12:30 [root:useradd] messagebus(556):messagebus(556):D-BUS Daemon User:/nonexistent:/usr/sbin/nologin 2023-12-06 21:12:32 [root:groupadd] openvpn(301) 2023-12-06 21:12:32 [root:useradd] openvpn(301):openvpn(301):OpenVPN pseudo-user:/nonexistent:/usr/sbin/nologin 2023-12-06 21:12:32 [root:groupadd] dhcpd(136) 2023-12-06 21:12:32 [root:useradd] dhcpd(136):dhcpd(136):ISC DHCP daemon:/nonexistent:/usr/sbin/nologin 2025-02-15 13:04:29 [unknown:groupadd] all(1998) 2025-02-15 13:04:29 [unknown:usermod] root(0):wheel(0):Charlie &:/root:/bin/sh 2025-02-15 13:04:29 [unknown:useradd] admin(0):wheel(0):System Administrator:/root:/etc/rc.initial 2025-02-15 13:04:29 [unknown:useradd] admin(0) home /root made 2025-02-15 13:04:29 [unknown:groupmod] all(1998) 2025-02-15 13:04:29 [unknown:groupadd] admins(1999) 2025-02-15 12:09:47 [root:usermod] root(0):wheel(0):Charlie &:/root:/bin/sh 2025-02-15 12:09:47 [root:usermod] admin(0):wheel(0):System Administrator:/root:/etc/rc.initial 2025-02-15 12:34:09 [unknown:userdel] admin(0) account removed 2025-02-15 12:34:09 [unknown:groupmod] all(1998) 2025-02-15 12:34:09 [unknown:usermod] root(0):wheel(0):Charlie &:/root:/bin/sh 2025-02-15 12:34:09 [unknown:useradd] admin(0):wheel(0):System Administrator:/root:/etc/rc.initial 2025-02-15 12:34:09 [unknown:useradd] admin(0) home /root made 2025-02-15 12:34:10 [unknown:groupmod] all(1998) 2025-02-15 12:34:10 [unknown:groupmod] admins(1999) 2025-02-19 16:00:52 [unknown:userdel] admin(0) account removed 2025-02-19 16:00:52 [unknown:groupmod] all(1998) 2025-02-19 16:00:52 [unknown:usermod] root(0):wheel(0):Charlie &:/root:/bin/sh 2025-02-19 16:00:52 [unknown:useradd] admin(0):wheel(0):System Administrator:/root:/etc/rc.initial 2025-02-19 16:00:52 [unknown:useradd] admin(0) home /root made 2025-02-19 16:00:52 [unknown:groupmod] all(1998) 2025-02-19 16:00:52 [unknown:groupmod] admins(1999) 2025-04-10 20:59:20 [root:groupadd] ntopng(288) 2025-04-10 20:59:20 [root:useradd] ntopng(288):ntopng(288):ntopng daemon user:/nonexistent:/usr/sbin/nologin 2025-04-10 20:59:20 [root:groupadd] redis(535) 2025-04-10 20:59:20 [root:useradd] redis(535):redis(535):Redis Daemon:/nonexistent:/usr/sbin/nologin 2025-06-17 03:11:44 [unknown:userdel] admin(0) account removed 2025-06-17 03:11:44 [unknown:groupmod] all(1998) 2025-06-17 03:11:44 [unknown:usermod] root(0):wheel(0):Charlie &:/root:/bin/sh 2025-06-17 03:11:44 [unknown:useradd] admin(0):wheel(0):System Administrator:/root:/etc/rc.initial 2025-06-17 03:11:44 [unknown:useradd] admin(0) home /root made 2025-06-17 03:11:44 [unknown:groupmod] all(1998) 2025-06-17 03:11:44 [unknown:groupmod] admins(1999) 2025-06-17 03:14:19 [unknown:userdel] admin(0) account removed 2025-06-17 03:14:19 [unknown:groupmod] all(1998) 2025-06-17 03:14:19 [unknown:usermod] root(0):wheel(0):Charlie &:/root:/bin/sh 2025-06-17 03:14:19 [unknown:useradd] admin(0):wheel(0):System Administrator:/root:/etc/rc.initial 2025-06-17 03:14:19 [unknown:useradd] admin(0) home /root made 2025-06-17 03:14:19 [unknown:groupmod] all(1998) 2025-06-17 03:14:19 [unknown:groupmod] admins(1999) -
@w0w I work from home so my work computer is connected to my personal network. My firm hopefully monitors connections made from that computer and potential tampering with it. I also have no admin rights on that computer so if anything has spread to it I feel like it should have been caught by defender or Sentinel One. I am having the pfsense firewall installed on top because I have an ISP provided router and running a double nat with pfsense behind it. Just to be safe. I also installed it to find out why my network slows down from time to time.
-
@w0w @Gertjan @johnpoz I finally managed to capture the connections. It seems to be Microsoft Edge related from what I can read out of the captures. Like updating blocklists for MS Edge and extensions related.
Connection: Keep-Alive Accept: */* Accept-Encoding: identity If-Unmodified-Since: Fri, 27 Jun 2025 05:10:06 Range: bytes=38496-67887 User-Agent: Microsoft BITS/7.8 Host: msedge.b.tlu.dl.delivery.mp.microsoft.comGET /msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?ebbddd4290c6cf57 HTTP/1.1 Connection: Keep-Alive Accept: */* If-Modified-Since: Fri, 02 Jun 2017 17:39:05 If-None-Match: "82324021e7ddd21:0" User-Agent: Microsoft-CryptoAPI/10.0 Host: ctldl.windowsupdate.com HTTP/1.1 304 Not Modified Connection: keep-alive Cache-Control: public,max-age=900 Last-Modified: Fri, 02 Jun 2017 17:39:05 ETag: "80434021d7dbbb21:0" Ocn-Cache-Status: HIT Ocn-Requestid: . Ocn-Served-By: QLT Server: Qwilt X-OC-Service-Type: lo X-CID: 9 X-CCC: nl -
@rasputinthegreatest well that sure doesn't seem to line up with the nastiness that alienvault is saying.
I never use edge - on work computer yes, but I never see where it goes because its always connected to the work vpn. I am full time work from home.. Its only not connected to vpn when it boots or the vpn times out (which is 5 days). And then I normally reconnect, etc..
-
@johnpoz I guess you only figure this stuff out if you investigate yourself. The information online is very mixed sometimes and puts you in a panic for no reason. I also asked my IT department and they confirmed as well that it is nothing to worry about. Another lesson learned :)
I also don't use Edge. It automatically runs in the background. Thanks Microsoft.
-
@rasputinthegreatest normally hosting stuff on big cdn networks is not cheap - and would assume they do some vetting of what is being hosted/served. Not saying stuff can not be compromised - but seems unlikely some malware people would choose to host their crap there to be honest. While that cdn is not a global player to the likes of aws/azure or clouldflare, etc. They are not a ma and pop vps hoster ;)
Glad you got it figured out - and this thread might be very helpful for the next guy.