Blocking URL's in Pfsense firewall for specifi range of IP
-
Thinking about it, that may not work for me, not sure. The reason I say that is because I currently have "kids" systems reserved in DHCP, their lease gives them a different DNS server "1.1.1.3", all other systems default to PfSense IP which forwards to "1.1.1.1". the .3 is the adult filter from Cloudflare.
I made an attempt using the below set of rules, but it does not seem effective, i.e. the target PC can still access youtube.com. Should the below type of setup be possible, can I effectively block just a few urls for a handful of devices this way. Again I am looking for a simple effective means to manage a url block list for handful of devices on my network. I feel like this should be easy to do in pfSense and if not perhaps a new feature.
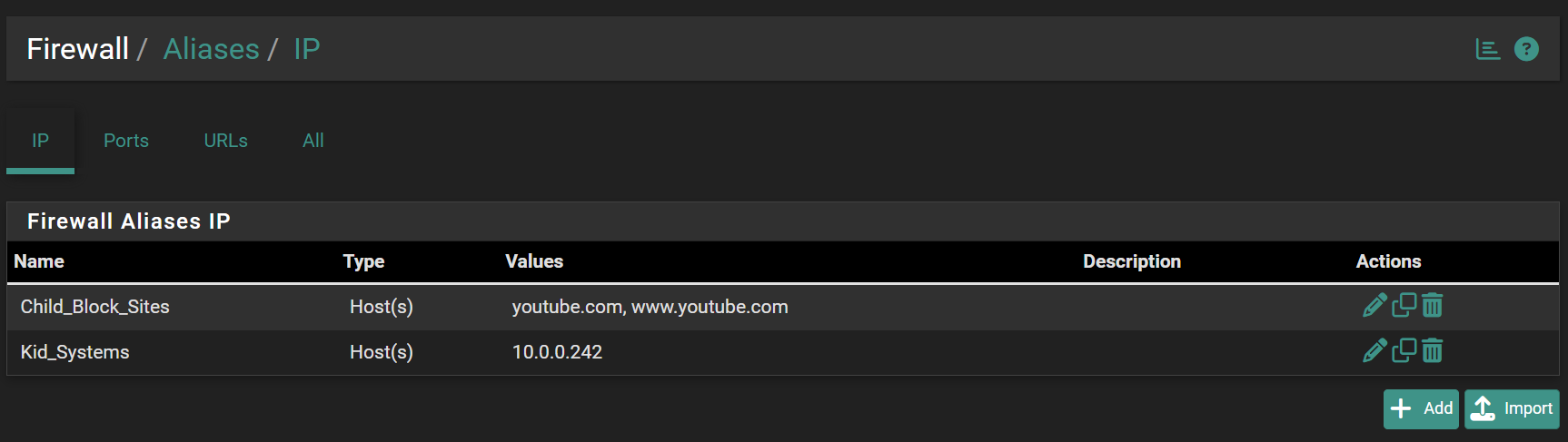
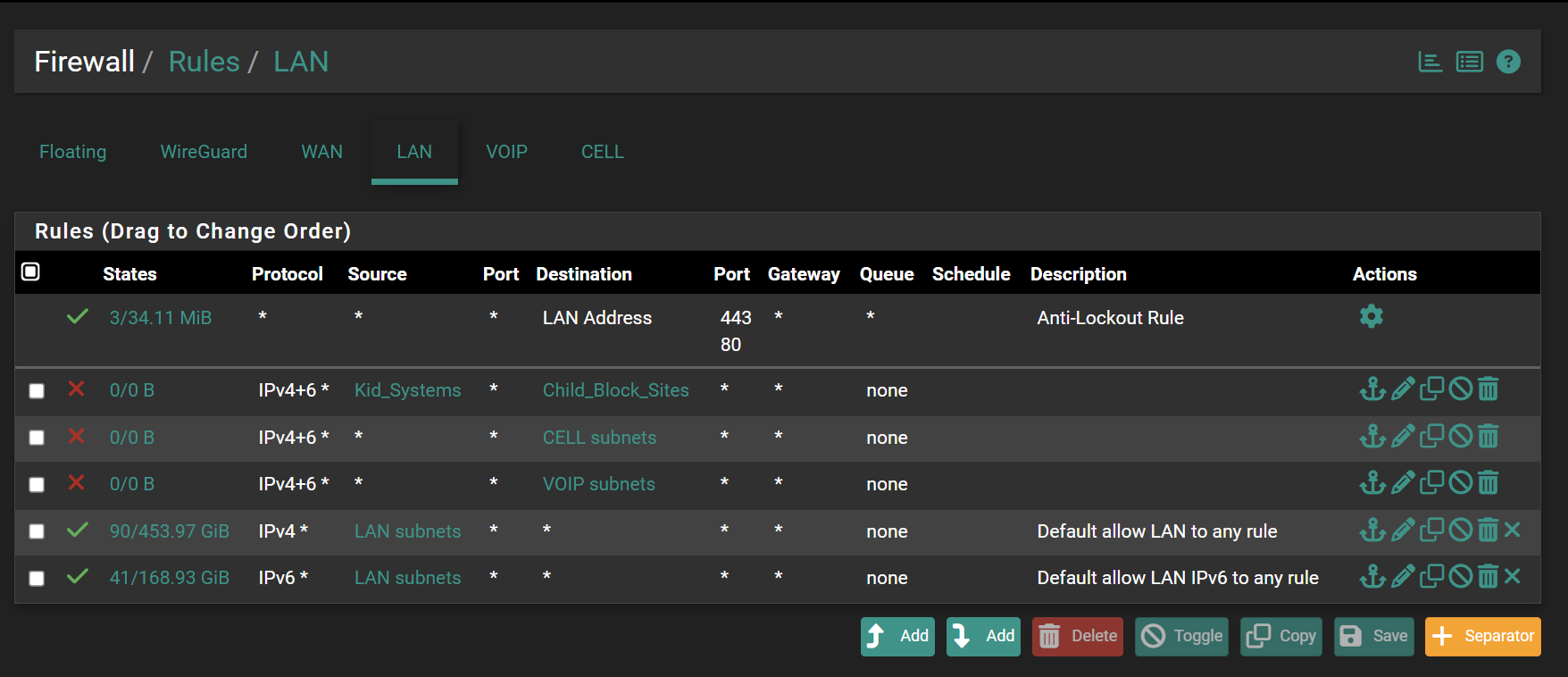
-
Yup, you can't block with rules like that. The alias will be resolved to an IP or set of IPs when the ruleset is generated but that will only be a tiny fraction of the potential IPs used by youtube.
You can block by ASN but that will impact far more than just youtube. You pretty much need to filter using DNS to get the sort of functionality you're looking for.
-
Is there any solution leveraging DNS where I can achieve the desired outcome described.
i.e.
By default clients receive pfSense IP (10.X.X.X) as their DNS Server, no other filtering or blocking, PF forwards to 1.1.1.1. (Cloudflare). (Current Setup and Working)
Select clients (KIDS Systems) receive / have their DNS requests sent to 1.1.1.3. (Working Today via DHCP Reservation)
Net-New-Addon - Same Select "KIDS Systems" are blocked from youtube.com but again has to continue leveraging 1.1.1.3 as their DNS server so that Adult content is effectively blocked. (Solution Not Found Yet)
Thanks.
-
You could switch that around so that most systems use 1.1.1.1 directly but kids systems use Unbound in pfSense and are forwarded to 1.1.1.3. Then you can add filtering to unbound for some domains.
Or you could pass kids systems to an external DNS service that allows adding domains to block.
-
Not really crazy about that idea, i have DNS over TLS configured and other local hosts id like to be able to address by hostname easily.
Perhaps there is a plugin solution ??
-
I also found the custom view option you were referencing, which I really like. This would be almost perfect if all clients where using the pfsense box for DNS. I don't suppose there is a way to create a view so that certain clients have their requests forwarded to 1.1.1.1 and others to 1.1.1.3 ? Outside of my current method which is via DHCP. If this does not exist, could this be a potential future product enhancement.
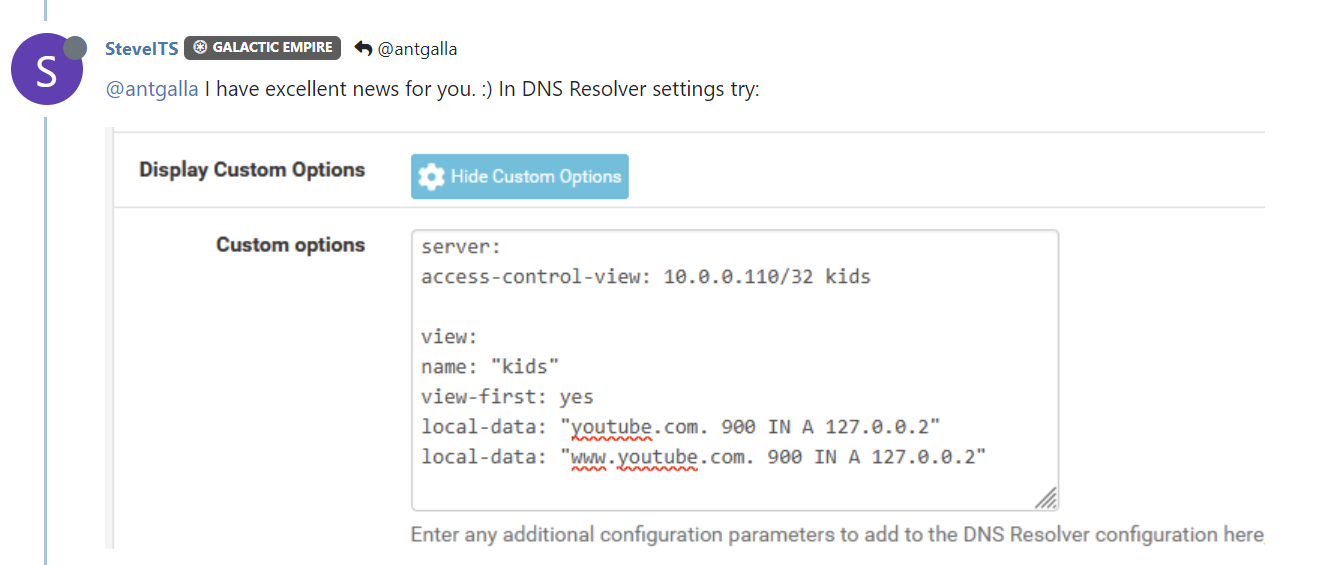
-
I haven't tried that but I believe could. You should be able to set any number of parameters for he client view.
An alternative here might be to also run the DNS forwarder. You have to run it on a different port to avoid a conflict but you can forward requests to that port.
-
Is there any documentation of what parameters exist for DNS Resolver and / or would you be able to hook me up with the syntax for the above scenario.
Thank you so much.
-
I'm not sure what it would be for that off-hand. But you should be able to enter config for anything that the resolver (Unbound) can do so:
https://man.freebsd.org/cgi/man.cgi?query=unbound.confA lot!
-
How does this look, I would like to backup / edit the unbound config via SSH, where does one find that config file.
view:
name: "client_110"
view-first: yes
client-subnet: 1.0.0.110/32forward-zone:
name: "."
forward-addr: 1.1.1.3 -
The unbound conf file is generated automatically from the pfSense config when the service is started and anytime a change is made. Editing the config directly is only useful as a test. But it's in /var/unbound/unbound.conf.
-
-
Well like I said I've tried to do that so.... I'm not sure.

Does it work? I'd expect to see a load of errors when it creates the test config of there's a problem.