Sudden appearance of Block IPv4 link-local (1000000101).How to find the cause?
-
Hey guys, can anyone tell me how to find out what happend here? I suddenly see the Block IPv4 link-local. Does that mean a device that is not supposed to be on my network accessed it? I happend when I started my computer but I never saw that event before. Is there a way to identify what device caused it after the fact?
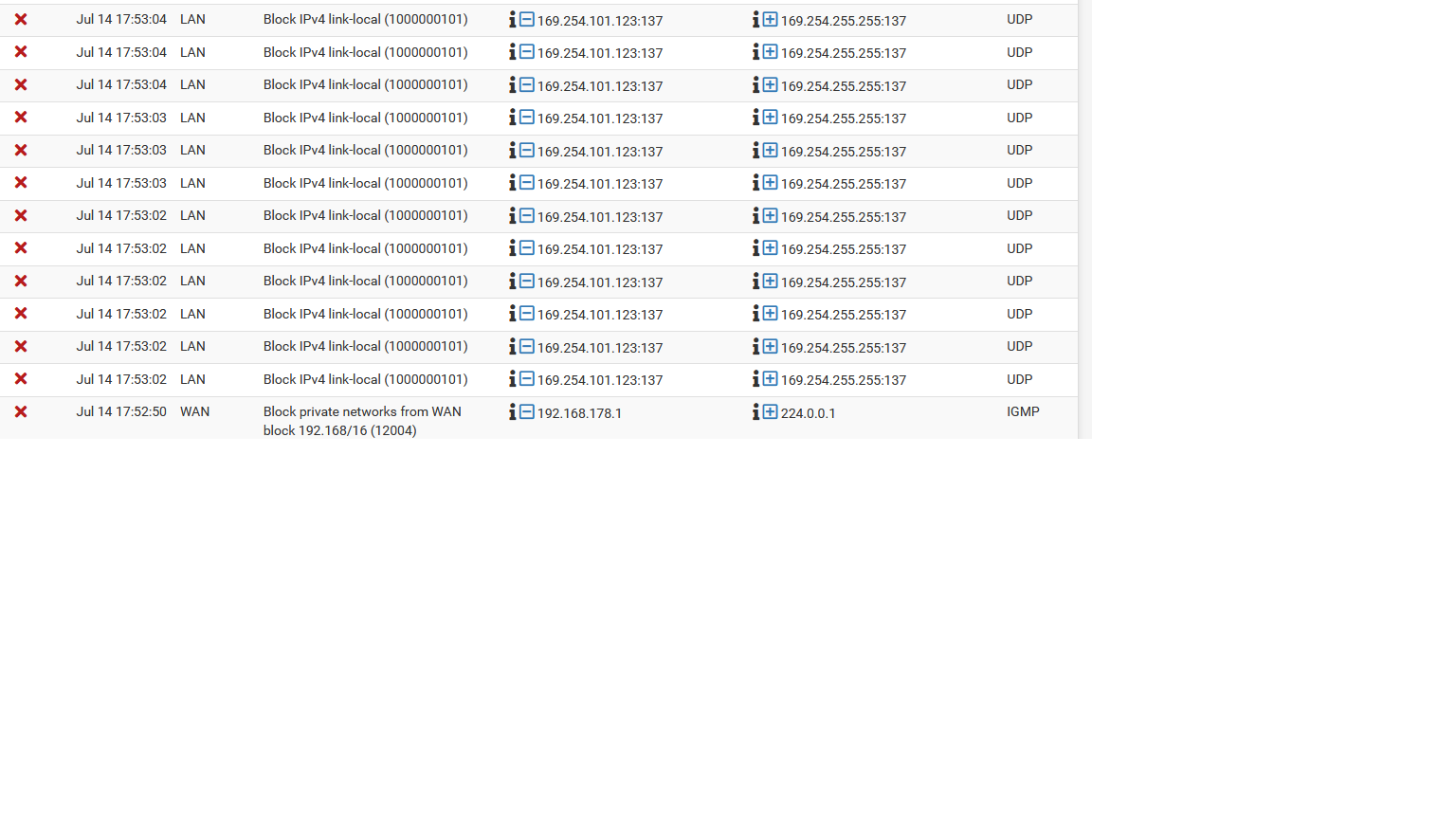
When I ping it inside pfsense I get this. Does this indicate anything?
PING 169.254.101.123 (169.254.101.123): 56 data bytes 92 bytes from 192.168.178.1: Redirect Host(New addr: 169.254.101.123) Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 01e3 0 0000 3f 01 f779 192.168.178.42 169.254.101.123 92 bytes from 192.168.178.1: Redirect Host(New addr: 169.254.101.123) Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 2da5 0 0000 3f 01 cbb7 192.168.178.42 169.254.101.123 92 bytes from 192.168.178.1: Redirect Host(New addr: 169.254.101.123) Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 fad1 0 0000 3f 01 fe8a 192.168.178.42 169.254.101.123 92 bytes from 192.168.178.1: Destination Host Unreachable Vr HL TOS Len ID Flg off TTL Pro cks Src Dst 4 5 00 0054 01e3 0 0000 3f 01 f779 192.168.178.42 169.254.101.123 --- 169.254.101.123 ping statistics --- 3 packets transmitted, 0 packets received, 100.0% packet loss -
@rasputinthegreatest well more than likely what happened is some device, prob the one you turned on didn't get an IP from dhcp so it fell back to APIPA (169.254.x.x address).. And yeah pfsense would block those - you can turn off logging of those if you want.
You can figure out which device it is by doing a packet capture and looking at the mac address of who sent it. Or just look for a device that didn't get an IP from dhcp.
-
@johnpoz I don't see a device missing an IP. So I would just run a packet capture looking for 169.254.101.123 and see if anything shows up?
-
@rasputinthegreatest yeah if your seeing logs still for it - maybe that device got an IP from dhcp and is no longer sending that.. But if your still seeing the logs then simple packet capture will give the mac address and then from that you can track down what device it is.
if your not going to download the packet capture into say wireshark then you prob want to up the output level so it shows mac address.
edit: you going to want full in the capture view options - then you will see output like this
12:23:35.832321 b0:4f:13:0b:fd:16 > 00:08:a2:0c:e6:24, ethertype IPv4 (0x0800), length 141: (tos 0x2,ECT(0), ttl 128, id 19757, offset 0, flags [DF], proto TCP (6), length 127) 192.168.9.100.10510 > 192.168.9.253.8443: Flags [P.], cksum 0x99f6 (correct), seq 3747277868:3747277955, ack 2569268505, win 8212, length 87so this is just normal my pc 192.168.9.100 talking to my pfsense gui at 192.168.9.253.. But you can see my pc mac is that b0:f4 and my pfsense is the 00:08
Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Killer E2600 Gigabit Ethernet Controller Physical Address. . . . . . . . . : B0-4F-13-0B-FD-16 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0igb0: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: LAN options=4e100bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0c:e6:24 inet 192.168.9.253 netmask 0xffffff00 broadcast 192.168.9.255edit: on another note, it could be something just trying to use link-local even if it has normal IPv4.. I have a directv device that does that.. Stupid device ;)
12:35:54.425767 0c:08:b4:48:cc:63 > 01:00:5e:7f:ff:fa, ethertype IPv4 (0x0800), length 335: (tos 0x0, ttl 4, id 12623, offset 0, flags [DF], proto UDP (17), length 321) 169.254.8.104.49152 > 239.255.255.250.1900: [udp sum ok] So see the mac ending in cc:63,12:35:54.426325 0c:08:b4:48:cc:63 > 01:00:5e:7f:ff:fa, ethertype IPv4 (0x0800), length 403: (tos 0x0, ttl 4, id 6600, offset 0, flags [DF], proto UDP (17), length 389) 192.168.7.5.49152 > 239.255.255.250.1900: [udp sum ok]That is my directv box that has a valid IP on the network 192.168.7.0/24 - but it still sends out that 169.254 link local shit..
-
@johnpoz Ok thanks a lot. I will run a capture and see if anything comes up. So far nothing. In my DHCP log it showed this when I started the computer. But the firewall log came shortly after which is a little strange. Like a second device with no IP coming up when I start my computer
Jul 14 17:53:02 kea-dhcp4 41329 INFO [kea-dhcp4.leases.0x29d3ba017400] DHCP4_LEASE_ALLOC [hwtype=1 3c:a1:44:83:13:16], cid=[02:3c:a1:44:83:13:16], tid=0xd2cabdcf: lease 192.168.1.83 has been allocated for 7200 seconds Jul 14 17:53:02 kea-dhcp4 41329 INFO [kea-dhcp4.dhcpsrv.0x29d3ba017400] EVAL_RESULT Expression pool_opt1_0 evaluated to 1 Jul 14 17:53:02 kea-dhcp4 41329 INFO [kea-dhcp4.dhcpsrv.0x29d3ba017400] EVAL_RESULT Expression pool_lan_0 evaluated to 1 Jul 14 17:53:02 kea-dhcp4 41329 INFO [kea-dhcp4.leases.0x29d3ba017400] DHCP4_LEASE_ADVERT [hwtype=1 3c:a1:44:83:13:16], cid=[02:3c:a1:44:83:13:16], tid=0xd2cabdcf: lease 192.168.1.83 will be advertised Jul 14 17:53:02 kea-dhcp4 41329 INFO [kea-dhcp4.dhcpsrv.0x29d3ba017400] EVAL_RESULT Expression pool_opt1_0 evaluated to 1 Jul 14 17:53:02 kea-dhcp4 41329 INFO [kea-dhcp4.dhcpsrv.0x29d3ba017400] EVAL_RESULT Expression pool_lan_0 evaluated to 1 -
@rasputinthegreatest see my edit about devices sending it out even when they have an IP on the network - my directv appliance does that.. But once you have a mac should allow you to track it down. Especially if you have a smart switch and its wired. Where you can look at the mac address table.
If everything is working and you just don't like the noise in the logs, you can turn those off, either in log settings - I believe new 2.8 allows for not logging link local. Or you could setup a rule not to log it.