Port 0 and IPv4 Great... but hey what about IPv6 or inet6?
-
if you noticed you have an auto added pfsense plus auto created rule
block quick inet proto { tcp, udp } from any port = 0 to anyThis is ipv4 only.... if you use a ipv6 tunnel broker you will never see an ipv6 rule and guess what the GUI does not allow you to create a floating rule with port zero.
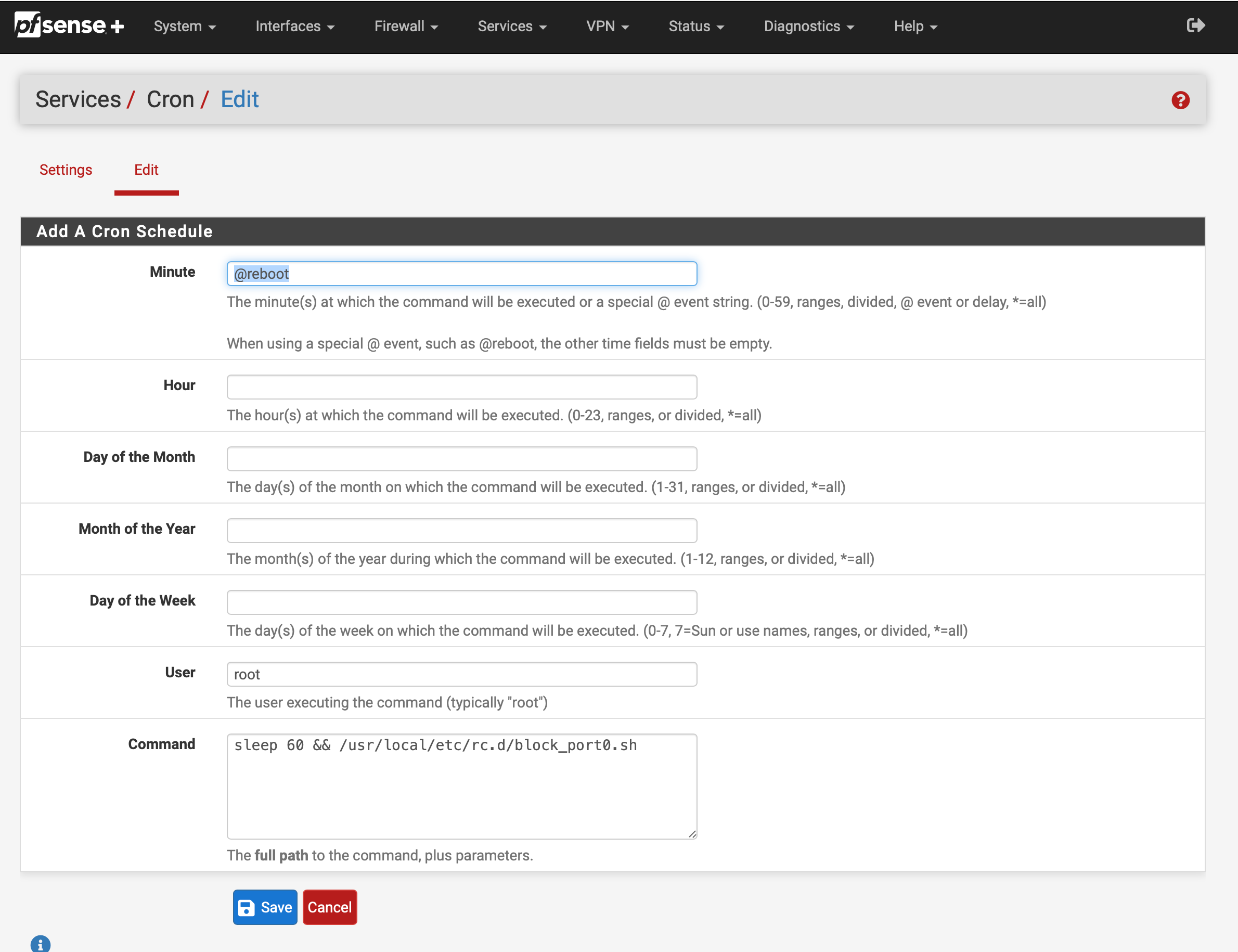
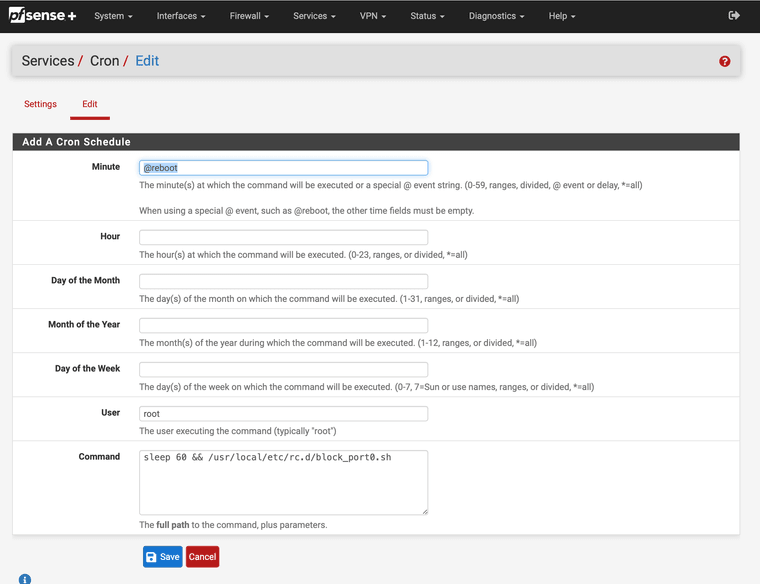
Work around create a script so you get the rules like this
block drop quick inet proto tcp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000114 block drop quick inet proto udp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000114 block drop quick inet proto tcp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000115 block drop quick inet proto udp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000115 block drop quick inet6 proto tcp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000116 block drop quick inet6 proto udp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000116 block drop quick inet6 proto tcp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000117 block drop quick inet6 proto udp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000117/usr/local/etc/rc.d/block_port0.sh
#!/bin/sh /sbin/pfctl -a "custom/block_port0" -v -f - <<EOF block drop quick inet proto { tcp udp } from any port = 0 to any label "Block from port 0 IPv4" block drop quick inet proto { tcp udp } from any to any port = 0 label "Block to port 0 IPv4" block drop quick inet6 proto { tcp udp } from any port = 0 to any label "Block from port 0 IPv6" block drop quick inet6 proto { tcp udp } from any to any port = 0 label "Block to port 0 IPv6" EOFmake it executable.
chmod +x /usr/local/etc/rc.d/block_port0.shAdd a cron job
Bingo run
pfctl -srand now you have that block rule for ipv6 also it should show inet6.
or a better script to include bogons
#!/bin/sh /sbin/pfctl -a "custom/block_port0" -v -f - <<EOF # Block TCP/UDP packets with source or destination port 0 (IPv4) block drop quick inet proto { tcp udp } from any port = 0 to any label "Block from port 0 IPv4" block drop quick inet proto { tcp udp } from any to any port = 0 label "Block to port 0 IPv4" # Block TCP/UDP packets with source or destination port 0 (IPv6) block drop quick inet6 proto { tcp udp } from any port = 0 to any label "Block from port 0 IPv6" block drop quick inet6 proto { tcp udp } from any to any port = 0 label "Block to port 0 IPv6" # Block some spoofed IPv4 addresses block drop quick inet from 127.0.0.0/8 to any label "Block IPv4 loopback source" block drop quick inet from 0.0.0.0/8 to any label "Block IPv4 zero network" block drop quick inet from 169.254.0.0/16 to any label "Block IPv4 link-local source" block drop quick inet from 224.0.0.0/4 to any label "Block IPv4 multicast source" block drop quick inet from 240.0.0.0/5 to any label "Block IPv4 reserved source" # Block some spoofed IPv6 addresses block drop quick inet6 from ::1 to any label "Block IPv6 loopback source" block drop quick inet6 from ::/128 to any label "Block IPv6 unspecified source" block drop quick inet6 from fe80::/10 to any label "Block IPv6 link-local source" block drop quick inet6 from ff00::/8 to any label "Block IPv6 multicast source" EOF -
pfctl -s rulesshould show the rules loaded
-
Shell Output - pfctl -vvsr | grep "port = 0" @12 block drop quick inet proto tcp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000107 @13 block drop quick inet proto udp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000107 @14 block drop quick inet proto tcp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000108 @15 block drop quick inet proto udp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000108Shell Output - pfctl -vvsr -a custom/block_port0 | grep "port = 0" @0 block drop quick inet proto tcp from any port = 0 to any label "Block from port 0 IPv4" @1 block drop quick inet proto udp from any port = 0 to any label "Block from port 0 IPv4" @2 block drop quick inet proto tcp from any to any port = 0 label "Block to port 0 IPv4" @3 block drop quick inet proto udp from any to any port = 0 label "Block to port 0 IPv4" @4 block drop quick inet6 proto tcp from any port = 0 to any label "Block from port 0 IPv6" @5 block drop quick inet6 proto udp from any port = 0 to any label "Block from port 0 IPv6" @6 block drop quick inet6 proto tcp from any to any port = 0 label "Block to port 0 IPv6" @7 block drop quick inet6 proto udp from any to any port = 0 label "Block to port 0 IPv6" -
@JonathanLee said in Port 0 and IPv4 Great... but hey what about IPv6 or inet6?:
pfctl -s rules
something is not right because it should show also with pfctl -sr and it is not
pfctl -sr -a custom/block_port0 # DOES show them
-
-
pfctl -sr -a custom/block_port0So it works but they are not part of the main ruleset they are loaded and working
-
@JonathanLee said in Port 0 and IPv4 Great... but hey what about IPv6 or inet6?:
This is ipv4 only.... if you use a ipv6 tunnel broker you will never see an ipv6 rule and guess what the GUI does not allow you to create a floating rule with port zero.
huh.. the rules are there for both IPv4 and v6
cat /tmp/rules.debug
# We use the mighty pf, we cannot be fooled. block quick inet proto { tcp, udp } from any port = 0 to any ridentifier 1000000114 label "Block traffic from port 0" block quick inet proto { tcp, udp } from any to any port = 0 ridentifier 1000000115 label "Block traffic to port 0" block quick inet6 proto { tcp, udp } from any port = 0 to any ridentifier 1000000116 label "Block traffic from port 0" block quick inet6 proto { tcp, udp } from any to any port = 0 ridentifier 1000000117 label "Block traffic to port 0" -
@johnpoz I noticed that my setup was missing part of the IPv6 rule, even though IPv6 is enabled. I'm not sure if it's due to the older version I'm using. Thanks for taking a look!
-
@JonathanLee what version are you running?
-
@johnpoz 25.03.01
-
@JonathanLee so some old beta snapshot? Why?
-
@johnpoz it is the last one where Squid status page works, I am using it to attempt to figure out why in the new versions the status page does not work correctly. Plus it is my everything works version. Just every thing works how I wanted in this version, I feel very strongly about this version. I would love to update but the Squid status page is not working for me in the new versions.
-
@JonathanLee is there a thread where you give details of this status page not working? Is there a current redmine on it?
Using some old "beta" version is not proper way to go about getting something not working fixed.
-
@johnpoz There is a redmine open on it yes.
This is it
https://redmine.pfsense.org/issues/15410
except it is now Squid 7.1 that is stable and has the issue
-
@johnpoz This even does this with the newest CE edition inside of UTM virtualized environment outside of the 2100s
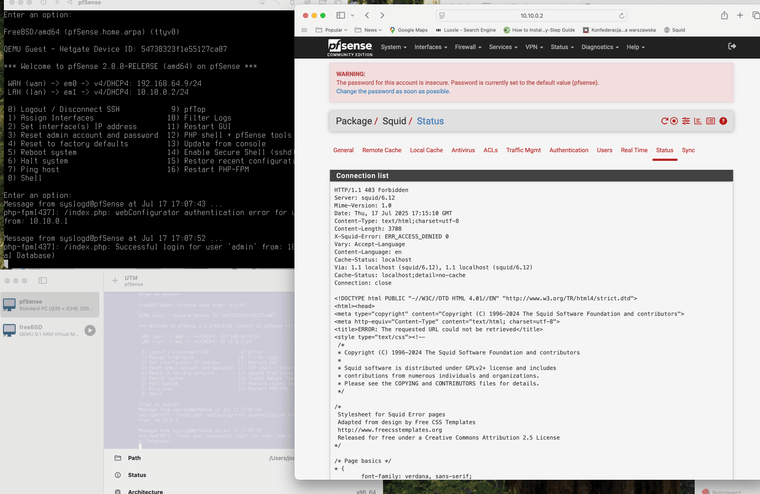
It is not just the 2100s this is set up for standard stuff everything else works with it just the status page