New Tunable: kern.crypto.iimb.enable_aescbc on fresh install
-
@tedquade Guess when 25.07 officially releases I'll factory erase and check again.
-
SG-4100, 24.11, set to 0 here.
Weird, this is explicit set in my config file:<sysctl> <item> <tunable>kern.crypto.iimb.enable_aescbc</tunable> <value>0</value> </item> </sysctl>Edit:
If you enable IPsec-MB, it will set kern.crypto.iimb.enable_aescbc to 0.
Since I`m running Wireguard only, that is what I want, in my SG-4100.
Just a FYI only, QAT is enabled but not in use. -
@luckman212 said in New Tunable: kern.crypto.iimb.enable_aescbc on fresh install:
Noticed a new tunable that I haven't seen before
kern.crypto.iimb.enable_aescbc
On a stock 6100 25.07 RC install, this is being set to 0Any more info on this?
See documentation on Crypto here.
-
@dennypage Yes thanks I saw that, so I assume that for the 6100 (which does have QAT) that
0is the preferred value here? Or does it not even really matter much? -
@luckman212 No idea, just spitballing, but is it dependent on the type of VPN you choose? I use OpenVPN, not IPSec.
-
kern.crypto.iimb.enable_aescbc Enables handling of AES-CBC. IIMB can be slower than QAT for CBC so this is a toggle to disable handling for AES-CBC while accelerating other algorithms so IPsec-MB and QAT can coexist in such environments. Supported on x86-64 only. Default is enabled (1). To disable, set a value of 0.So I read that as 'set zero' when using both IPsec-MB and QAT. Well, that is what I have set it to on my Xeon system.
 ️
️ -
@luckman212 said in New Tunable: kern.crypto.iimb.enable_aescbc on fresh install:
Yes thanks I saw that, so I assume that for the 6100 (which does have QAT) that 0 is the preferred value here? Or does it not even really matter much?
Mine shows as 1 in System / Advanced / System Tunables, however I do not see it actually being used by the kernel:
[25.07-RC][root@fw]/root: sysctl kern.crypto.iimb.enable_aescbc sysctl: unknown oid 'kern.crypto.iimb.enable_aescbc' [25.07-RC][root@fw]/root:kldstat on my 6100 shows that iimb.ko isn't loaded, so this makes sense. Looking at /etc/inc/pfsense-utils.inc, the loading of iimb.ko is controlled by system/ipsec_mb.
Looking at /etc/inc/config.console.inc, it appears that system/ipsec_mb is set to true on the 6100, but only on initial install. This explicit setting of ipsec_mb on the 6100 appears to be new. Ditto for kern.crypto.iimb.enable_aescbc, which is now set to 0, but only on initial install. So now, you get the option of using iimb on the 6100.
Again looking /etc/inc/config.console.inc, on the 6100 system/crypto_hardware will be set to qat during install, so iimb may be an option, but qat is still the default.
So in summary, to answer your question, I don't think it matters at all.

[Edit: it does indeed matter -- see below]
-
@dennypage said in New Tunable: kern.crypto.iimb.enable_aescbc on fresh install:
So in summary, to answer your question, I don't think it matters at all.

Well, according to the documentation, ChaCha20-Poly1305 is accelerated by iimb, so if you are running only wireguard, you would benefit by enabling it.
If that is the case, kern.crypto.iimb.enable_aescbc will be 0.Not sure if QAT enabled or disabled, will influence in that value.
-
@mcury so...
I do use WireGuard, and I DON'T use IPsec. I DO have
kern.crypto.iimb.enable_aescbc=0set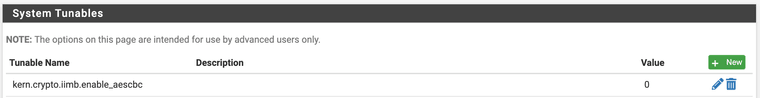
And it seems
iimb.kois loaded...[25.07-RC][root@r1.lan]/root: kldstat Id Refs Address Size Name 1 74 0xffffffff80200000 2dcd238 kernel 2 1 0xffffffff82fcf000 60b278 zfs.ko 3 1 0xffffffff835db000 1e2a8 opensolaris.ko 4 3 0xffffffff83e20000 6780 gpiobus.ko 5 1 0xffffffff83e27000 2140 gpioled.ko 6 1 0xffffffff83e2a000 22a0 cordbuc.ko 7 1 0xffffffff83e2d000 5a80 udf.ko 8 1 0xffffffff83e33000 23a0 cpuctl.ko 9 1 0xffffffff83e36000 4250 ichsmb.ko 10 1 0xffffffff83e3b000 2178 smbus.ko 11 1 0xffffffff83e3e000 4390 qat.ko 12 6 0xffffffff83e43000 14dd0 qat_hw.ko 13 9 0xffffffff83e58000 2ffe0 qat_common.ko 14 8 0xffffffff83e88000 68cd8 qat_api.ko 15 1 0xffffffff83ef1000 122c20 qat_c3xxx_fw.ko 16 1 0xffffffff84200000 5d67c8 iimb.ko 17 1 0xffffffff84014000 11258 qat_c2xxx.ko 19 1 0xffffffff84056000 20f0 coretemp.ko 20 1 0xffffffff84026000 2f5e0 if_wg.ko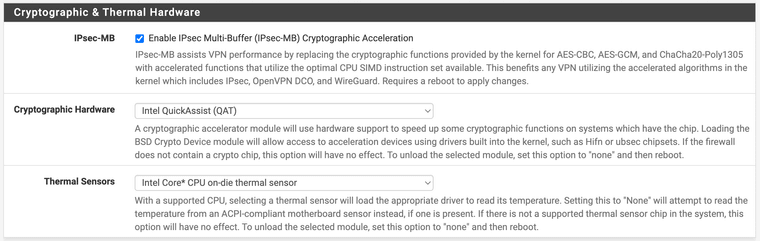
I did a fresh USB wipe and reinstall to get here, so these are "default" settings I think...
-
@luckman212 said in New Tunable: kern.crypto.iimb.enable_aescbc on fresh install:
I did a fresh USB wipe and reinstall to get here, so these are "default" settings I think...
You should be good now, for wireguard.

-
I enabled my iimb by hand. Seems to work fine on my 6100.
FWIW, the current documentation indicates that the default value of kern.crypto.iimb.enable_aescbc is 1 (enabled), although it has a warning that iimb can be slower than qat for cbc. I don't use cbc, so it doesn't matter in my case.
I think the documentation is incorrect or outdated (at least for the 6100), as the code in /etc/inc/config.console.inc explicitly sets kern.crypto.iimb.enable_aescbc to 0.
FWIW, there is also an interesting note on the qat/iimb trade-off earlier here. YMMV
-
Out of curiosity are you getting any hits for qat in vmstat? I'm configured in a nearly identical way and it must be that I must either not be using the right ciphers or IPsec-MB is so efficient it absolutely makes QAT useless.