pfBlockerNG not logging anything by default?
-
@Gertjan said in pfBlockerNG not logging anything by default?:
Is "192.168.51.5" a typo ? It doesn't show up in any logs .
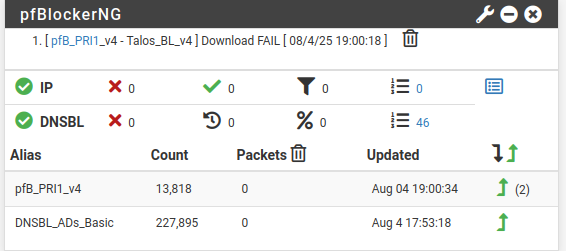
DNS-reply,Aug 5 10:39:03,local,PTR,PTR,Unk,5.51.168.192.in-addr.arpa,192.168.1.86,NXDOMAIN,unkIt does but with reverse DNS
This all seems to happen since changing to Unbound Python mode. Or has a Hacker created a subnet? I can't see anything in pfsense related to that subnet or those domains being looked up. I also see for the first time in my firewall logs the information next to WAN saying "Direction is out". Never saw this before. I feel like something opened up since installing pfblockerNG .
I am the only one using the devices behind pfsense. Its just a work computer and a laptop. Both create these weird DNS requests to hometheater-%RANDOMSTRING%.local for example. But its mostly my work computer doing these lookups@Gertjan said in pfBlockerNG not logging anything by default?:
What is your pfSense domain set to ?
mypfsense.arpa not even .local. But I see these logged by pfblockerNG with "local.home.arpa"
AAAA,AAAA,Unk,hometheater-wadq2.local.home.arpa,127.0.0.1,ServFail,unkI just don't understand all these domains and they sound sus if you take a look:
devmachine-FKcElwG.local mypc-DogOjT5.local desktop-ZmWfGXFW.local desktop-A5k217Qu.local hometheater-WADQ2.local hometheater-tQNIYv.local hometheater-ejsl1t.local surveillance-GanzOF.local fileshare-7JksiB.local mediacenter-VAY4Bk.localCan this just be randomly generated with no purpose? I tried packet captures of DNS traffic and these things dont show up there since they often orginate from 127.0.0.1
Or could it come from the ISP router in front of my pfsense? But it should block mDNS already afaik and even after blocking port 5353 I still see these .local things.
EDIT: Found something by @johnpoz here
https://forum.netgate.com/topic/146509/strange-dns-queries-from-pfsense/11
But the strings are much more random and less concrete in his example with gibberish.local.lan -
So something showed up again and the Unbound log shows nothing useful. No IP or who requested it. I guess the log level is not enough?
Aug 6 11:40:26 mypfsense unbound[24282]: [24282:0] debug: worker request: max UDP reply size modified (1472 to max-udp-size) Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: validator[module 1] operate: extstate:module_state_initial event:module_event_pass Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validator operate: query networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: iterator[module 2] operate: extstate:module_state_initial event:module_event_pass Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: resolving networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: finishing processing for networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: validator[module 1] operate: extstate:module_wait_module event:module_event_moddone Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validator operate: query networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validate(nxdomain): sec_status_secure Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validation success networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: cache memory msg=124942 rrset=239262 infra=87934 val=85965 Aug 6 11:40:58 mypfsense unbound[24282]: [24282:1] debug: validator[module 1] operate: extstate:module_state_initial event:module_event_passNow i saw this with log level 2. Very little information still. I don't know what is being resolved here and why.
Aug 6 12:48:34 mypfsense unbound[35444]: [35444:3] info: resolving desktop-Am6uk.local. A IN Aug 6 12:48:34 mypfsense unbound[35444]: [35444:3] info: validate(nxdomain): sec_status_secure Aug 6 12:48:34 mypfsense unbound[35444]: [35444:3] info: validation success desktop-Am6uk.local. A IN -
Now i saw this with log level 2. Very little information still. I don't know what is being resolved here and why. I have found a correlation with my firewall in that moment. I see port 5353 being blocked by my user rule but also see port 5335 being blocked by a default rule
Aug 6 12:48:34 mypfsense unbound[35444]: [35444:3] info: resolving desktop-Am6uk.local. A IN Aug 6 12:48:34 mypfsense unbound[35444]: [35444:3] info: validate(nxdomain): sec_status_secure Aug 6 12:48:34 mypfsense unbound[35444]: [35444:3] info: validation success desktop-Am6uk.local. A IN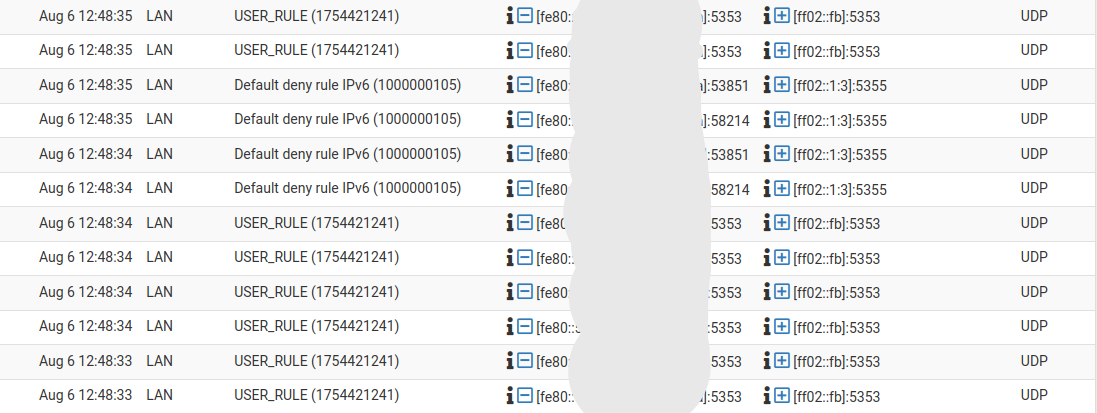
Is Unbound using port 5335? Would this be helpful to dig deeper?
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
It does but with reverse DNS
No.
It's :@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
192.168.1.86
asking for the reverse (see the "PTR,PTR" indication) of
5.51.168.192.in-addr
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
This all seems to happen since changing to Unbound Python mode
Unbound didn't change.
When you activate 'python mode' - see the config file /var/unbound/unbound.conf, last 3 lines - you tell unbound that it should activate the Python extension of unbound. "Python" is what unbound uses to communicate with external modules (also called addons, or extensions etc). pfb_unbound.py is such an extension, and is present with pfBlockerng for faster integration.
This "pfb_unbound.py" is used by pfBockerng so it can sneak peak what DNS requests are handled for stats purposs, what to block, etc.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
devmachine-FKcElwG.local
mypc-DogOjT5.local
desktop-ZmWfGXFW.local
desktop-A5k217Qu.local
hometheater-WADQ2.local
hometheater-tQNIYv.local
hometheater-ejsl1t.local
surveillance-GanzOF.local
fileshare-7JksiB.local
mediacenter-VAY4Bk.localI think (
 ) that these have to do with Avahi. And you use (you know why ?) Avahi on your Ubuntu .... I could be wrong of course.
) that these have to do with Avahi. And you use (you know why ?) Avahi on your Ubuntu .... I could be wrong of course.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
Or could it come from the ISP router in front of my pfsense?
No.
Look at your WAN firewall rule. Normally, there are .... none !
So, the default firewall behavior applies : No traffic initiated on the pfSense WAN side can enter.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
Now i saw this with log level 2
That's why I proposed '3'.
Don't forget to revert it.And keep in mind : pfSense => Unbound (and thus pfBlockerng) only see DNS traffic that is received by unbound.
Devices on LAN(s) that ask DNS info from other DNS servers like 8.8.8.8 - their requests will never show up under unbound/pfBlockerng. -
@Gertjan said in pfBlockerNG not logging anything by default?:
I think (
 ) that these have to do with Avahi. And you use (you know why ?) Avahi on your Ubuntu .... I could be wrong of course.
) that these have to do with Avahi. And you use (you know why ?) Avahi on your Ubuntu .... I could be wrong of course.I dont think so.It happens from my Windows 10 computer. It orginates from the IP 192.168.1.86
@Gertjan said in pfBlockerNG not logging anything by default?:
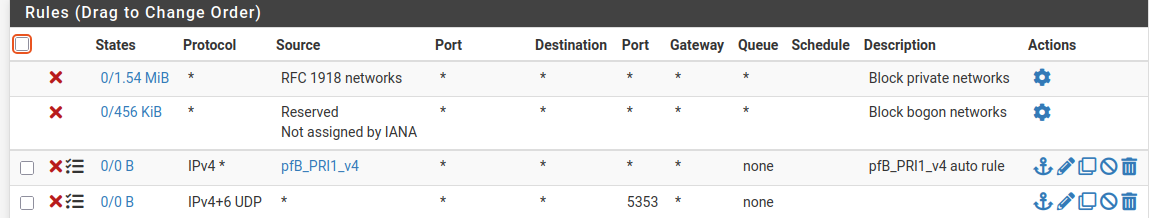
Look at your WAN firewall rule. Normally, there are .... none !
These are my WAN rules
@Gertjan said in pfBlockerNG not logging anything by default?:
That's why I proposed '3'.
What I posted was log level 3. Doesn't give any information. It just appears
Aug 6 11:40:26 mypfsense unbound[24282]: [24282:0] debug: worker request: max UDP reply size modified (1472 to max-udp-size) Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: validator[module 1] operate: extstate:module_state_initial event:module_event_pass Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validator operate: query networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: iterator[module 2] operate: extstate:module_state_initial event:module_event_pass Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: resolving networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: finishing processing for networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: validator[module 1] operate: extstate:module_wait_module event:module_event_moddone Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validator operate: query networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validate(nxdomain): sec_status_secure Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] info: validation success networkhub-Hfl1Jc.local. A IN Aug 6 11:40:28 mypfsense unbound[24282]: [24282:0] debug: cache memory msg=124942 rrset=239262 infra=87934 val=85965 Aug 6 11:40:58 mypfsense unbound[24282]: [24282:1] debug: validator[module 1] operate: extstate:module_state_initial event:module_event_passBut do you understand why I see port 5353 and port 5355 in my firewall log?
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
But do you understand why I see port 5353 and port 5355 in my firewall log?
Check : port 5353
so what is mDNS ? => More fact checking : Avahi (software) and now you reached the point why I was thinking about Avahi (Bonjour etc).
Normally, there would be pass rules, for example if you have NAT rules.
Blocking stuff that will get blocked anyway : ok, but not needed.
So KIS wins : don't even bother to blocking what will get blocked anyway.The counters show :
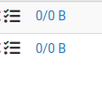
these two rules didn't capture any traffic.
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
It just appears
So shown is all the DNS traffic and other internal stages) that unbound received from 11:40:26 to 11:40:58, about 30 seconds.
That's close to 'nothing'. -
@Gertjan said in pfBlockerNG not logging anything by default?:
The counters show :
Yeah it didn't happen on WAN. And on LAN the counter also shows nothing for the 5353 rule I setup despite it being blocked in the firewall log. I guess it was redundant.
@Gertjan said in pfBlockerNG not logging anything by default?:
so what is mDNS ? => More fact checking : Avahi (software) and now you reached the point why I was thinking about Avahi (Bonjour etc).
I read about this as well and often people say it relates to Apple devices but my Apple devices are in front of pfsense and not behind the firewall. And the DNS queries still sound fishy to me especially coming from my work computer. I asked my IT if these domains sound familiar to them but obviously not so it must be inside my LAN. I did Wireshark captures but nothing shows up or is encrypted.
I know you say it's nothing but why am I even seeing this in the first place? It makes me feel uneasy and still would like to know if this is just random or something nefarious. My Windows desktop is using FortiClient and MS Sharepoint and I have read about a lot of attacks on both of these lately.
I don't know why the names would be so specific like "surveillance", "desktop", "hometheater","networkhub", "fileshare" and "devmachine". There is nothing on my network that ever used any of these terms.
It seems a little like wildcard poking I see by bots if you own your own website on Cloudflare. They try out all sorts of names to see if anything is there. -
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
I know you say it's nothing but why am I even seeing this in the first place?
Test this :
Install a pfSense with its WAN into an existing network. Default, the pfSense WAN uses DHCP, so it's "plug and play".
Hook up a switch to LAN - don'(t sue any other of the switch port. Leave them empty.
Use the pfSense console access to analyze logs.
Make sure that .... there are very few or no DNS look ups.
May one ne in a while, asking for abcd.netgate.com or some other pfsense.org domain as pfSense tests ones in a while if upgrades are avaible.
If you have set up a time service, you'll see that a time server is contacted.
And that's it.Now, populate your LAN.
All kind of traffics starts to show up. These come from your LAN devices.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
if you own your own website on Cloudflare. They try out all sorts of names to see if anything is there.
"Cloudflare" lives on the WAN side, also known as the Internet.
Nothing that lives out there can come into the WAN - not one bit. Ever.
( well, admins can do strange things, true, so lets presume a default pfSense install )
So, what can these bots do ? They can't use your resolver (unbound) to resolve stuff. They can't access your pfSense unbound from the outside.Bots that live on devices on your LAN : that's another story. All your other LAN devices are exposed now and pfSense can't do anything about it. That's why most devices have their own firewall.
-
@Gertjan said in pfBlockerNG not logging anything by default?:
Install a pfSense with its WAN into an existing network. Default, the pfSense WAN uses DHCP, so it's "plug and play".
So you mean build a new computer with pfsense again? My pfsense is already part of an existing network since I run double-nat. I have only my ISP network to test from. Could a managed switch be the culprit somehow?
@Gertjan said in pfBlockerNG not logging anything by default?:
Use the pfSense console access to analyze logs.
Don't I have to connect a device to access pfsense or how would I do that?
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
So you mean build a new computer ...
I prefer you see things with your own eyes.
Or just believe my words : hook up a clean non tampered pfSense (you are allowed to change the password, nothing more - no packages) it will work.
With very few to no DNS requests to handle.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
Could a managed switch be the culprit somehow?
Why ? Smart switches don't generate DNS requests.
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
Don't I have to connect a device to access pfsense or how would I do that?
?
The most important interface on pfSense is the "console" connection
It always work.
NICs can be down. -
@Gertjan said in pfBlockerNG not logging anything by default?:
prefer you see things with your own eyes.
Or just believe my words : hook up a clean non tampered pfSense (you are allowed to change the password, nothing more - no packages) it will work.
With very few to no DNS requests to handle.I am on it. But verifying it has not been tampered with is impossible even on a clean installation if it's embedded in firmware for example.
Also don't I need to increase log levels or at least install pfblockerNG to even see any of these DNS queries? I only found them through pfblockerNG in the first place. In default logs it would not show up.@Gertjan said in pfBlockerNG not logging anything by default?:
Why ? Smart switches don't generate DNS requests.
My QNAP switch has a section for IGMP snooping and LLDP. Maybe it has some stuff in it's "memory" that it is broadcasting? Sorry I have no idea.
@Gertjan said in pfBlockerNG not logging anything by default?:
The most important interface on pfSense is the "console" connection

It always work.
NICs can be down.What does that look like? Do I need a special hardware for that or does it work another way? I can only have a screen and keyboard plugged into the firewall. Does it offer a GUI/shell or direct input through that? Otherwise I am out of luck here. I only have IPMI on the board but that would need a connection to a different device as well so it's not ideal.
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
is impossible even on a clean installation if it's embedded in firmware for example.
Because "you don't want to". (no time, other interest, etc) Remember : pfSense is 'open source' **. So, here it is - to be seen by everybody who takes the effort to understand what it all means.
** granted : the FreeBSD kernel has its own github source tree, and can be found else where.
Maybe there are a process or two (binaries) that are owned by Netgate without freely accessible source but these can be reverse engineered (tools exist) if you really want to know what happens in there.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
In default logs it would not show up.
And that's a good thing.
Just know that you can see them if you need to.
pfBlockerng makes already nice stats for you.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
What does that look like?
On this kind of devices : My 4100 : there is no VGA or HDMI connector. So, when the system boots, you can't see the BIOS, you 'see' nothing untill the web GUI engine starts. For that to work, a LAN interface needs to be up. For an interface to be up, the system had to boot to the end without errors.
So, these devices have a "serial port". That port is sued to spit out the BIOS and boot process. Hook up a serial 'USB' connector, and use a terminal emulator.If you use a "PC" as a pfSense device then you have a video card, and USB mouse, keyboard etc so that will be your 'console' access. Hook up a screen and you see the boot process etc.
Another example : your smart switch , How do you access the GUI ? => with a web browser. You can't attach a VGA screen to it neither. What happens when the firmware update fails ? You have to use the console access - if one exist. If it doesn't : you waste bin the device as no access anymore.
Neither your APs, Printers, coffee machine, airco; whatever. Most have a 'hidden' serial connection for low 'console' level access. Always 'command line based' of course. -
@Gertjan said in pfBlockerNG not logging anything by default?:
Because "you don't want to". (no time, other interest, etc
What do you mean? I am unfortunately not a software engineer nor a hardware specialist. It would probably take me years to figure any of this stuff out. Definitely no time for that. My switch has a console port but I never used it thus far.
@Gertjan said in pfBlockerNG not logging anything by default?:
And that's a good thing.
Just know that you can see them if you need to.
pfBlockerng makes already nice stats for you.So on that clean machine with a fresh install you recommend installing pfblockerNG? But how is it a good thing if I don't see what is going on? I need some sort of log that would show these weird domains to me in case they happen there as well on a separat network. If I hadn't installed pfblockerNG I would not even have seen whats going on. I consider that a bad thing. Or one could say ignorance is bliss?

BTW: I haven't seen any new entries since my work computer is off. Yesterday it happend after it was off but I think only because I tried to ping it from my laptop and through pfsense. So I feel like my work computer is the culprit which is not great either...
-
This post is deleted! -
Is it possible to set a *.local and *.arpa domain override here to get rid of all these entries?
-
Wild cards like *.something are not allowed.
Domain Overrides is meant to be used for something completely different.
Be sure to rename your :
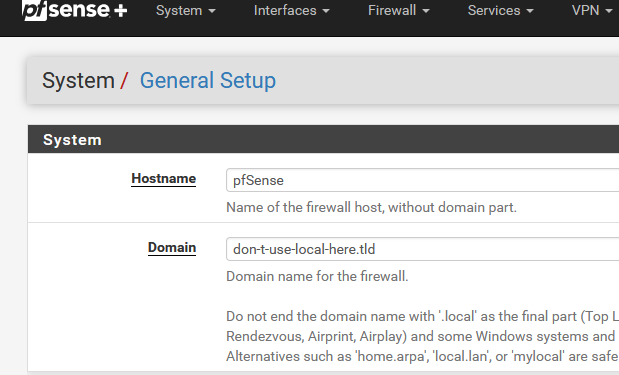
then, if you have to, locate the device that sends these DNS requests. Shut it down or find the process sends these requests, and kill it.
-
@Gertjan Whenever it is a full hour I see stuff like this in my logs:
https://otx.alienvault.com/indicator/ip/94.16.122.152
It seems to be time servers but it's a TOR node and some private person hosting traefik? I feel like this should not show up? It originates from my ASUS access point. But it is also related to when the emerging threats get updated. All happens at the full hour mark. I don't know why some random private persons ntp server gets queried. -
This post is deleted! -
So today I had just my work computer running behind pfsense as an experiment and I am still seeing these weird DNS queries. Now for the weekend I will only use my laptop and see what happens. If I am still seeing these queries there must be something up with pfsense.
-
Why would pfSense generate random host names / URLs ?
If it (unbound) has to resolve "otx.alienvault.com" then that was because it was asked to do so. The request came in by LAN, and was handled. And logged.
Shut down all LAN devices, and "DNS requests" will stop.
The ones still there will be 'Netgate' or 'time server' based.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
https://otx.alienvault.com/indicator/ip/94.16.122.152
Where - what log - did you find that URL (DNS only deals with host names) ?