Blocked internet but it's still "Kind of" working
-
@SteveITS
The rule that I used to test this on is for one of my laptop that my son uses. I have 2 other rules that are aliases base that is setup identical to this.I also have ipV6 completely disabled in pfSense and all devices IP addresses are using DHCP reservation.
In addition, I'm using Home Assistant to disable/enable the rules which is confirmed to work.
This rule is at the very top of the list just below the Anti-Lockout Rule.
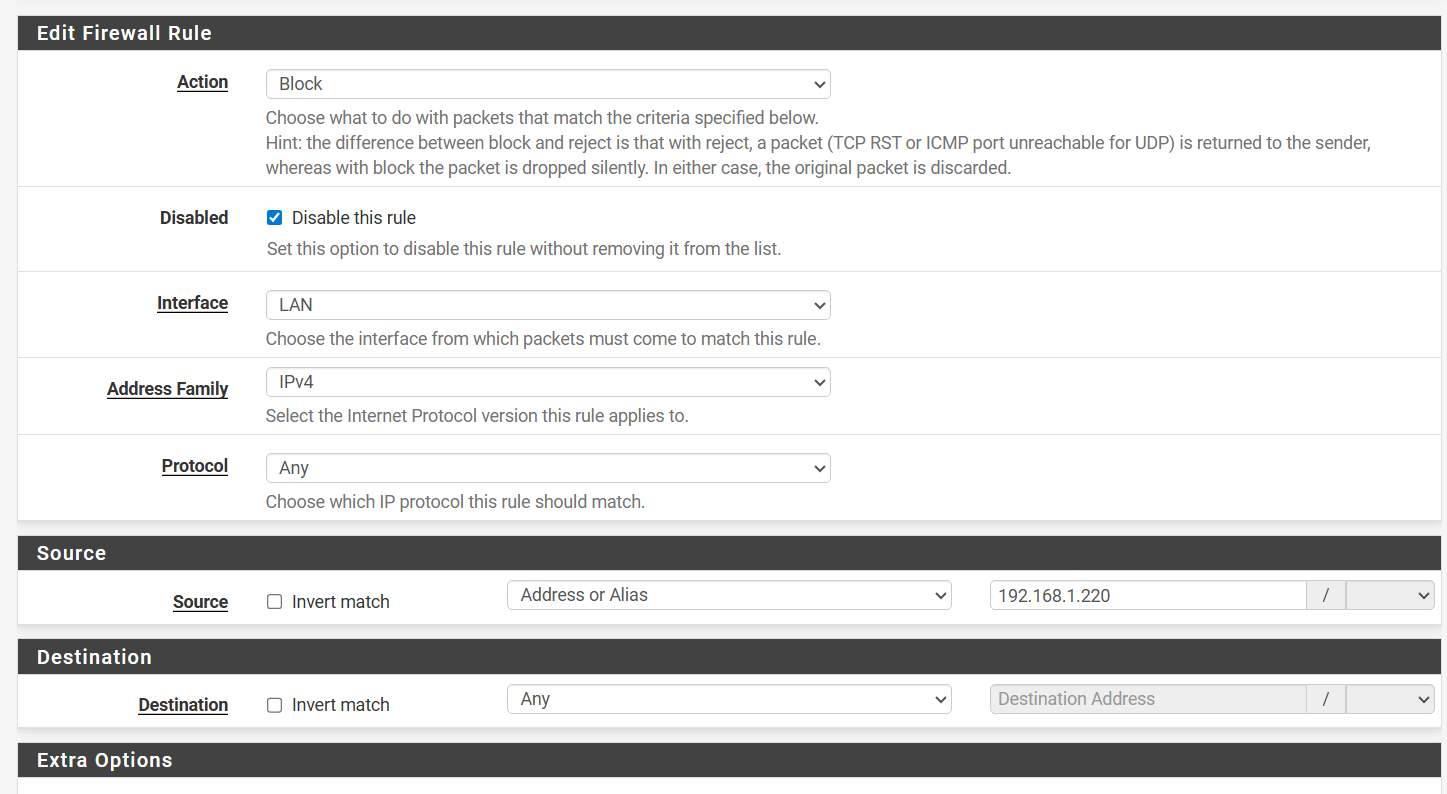
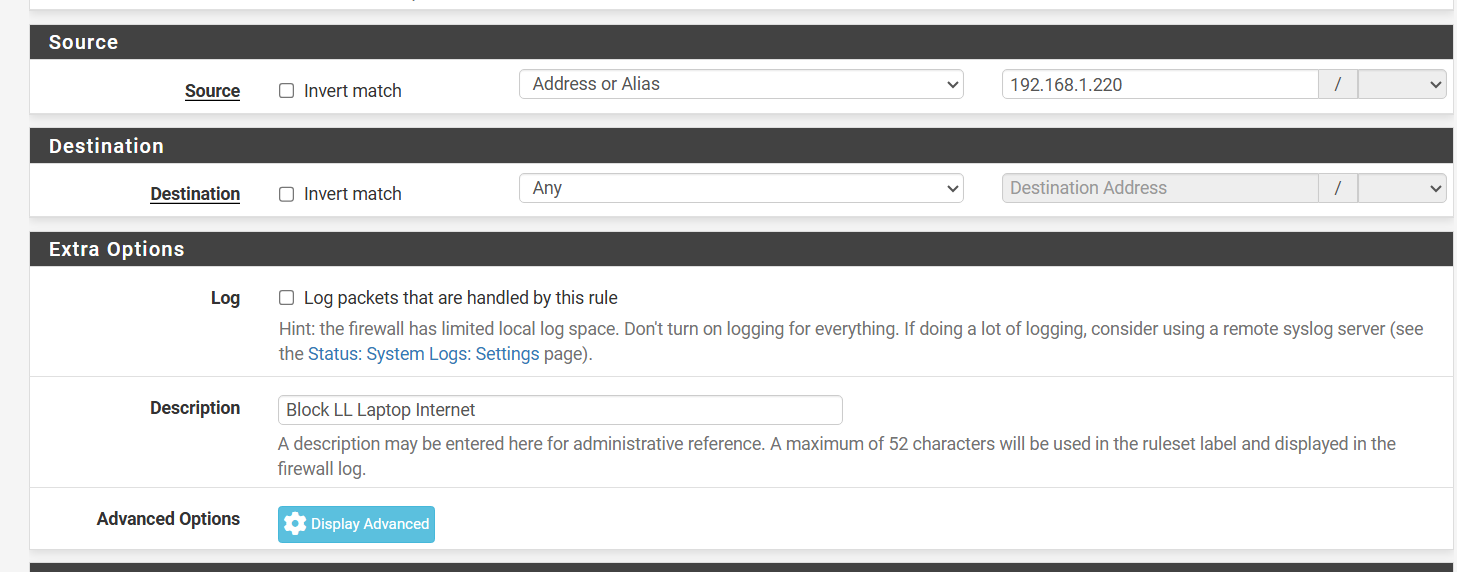
-
@cheapie408 and did you validate your states are flushed.. If you go to google.com, and then block internet - there is still a state to google.com - where yeah you can search on google. But any results you try to go to would be blocked - because that would be a new state.
When you create a new block rule - you have to either kill any existing states, or wait for them to time out on their own, etc.
It is gone over in the link @SteveITS provided.
States are evaluated before rules.. if there is an existing state to xyz.. Doesn't matter if you have a rule that would prevent future states to xyz.. Until you kill that state to xyz, or it times out on its own - yeah still going to be able to go to xyz.
-
@johnpoz, I did go into Diagnostics - States and reset states, if that's what you're asking.
-
@cheapie408
Remember that adding / enabling a block rule does not delete existing states.
So probably there was an existing connection for Google and you could reuse it.If you intend to provide scheduled access to the internet, use a pass rule for this. Only a pass rule can remove the belonging states at the time it expires.
-
@cheapie408 if you killed all the states, and you can still go somewhere - then your rules are not blocking what you want to block. You sure the states were killed off?
Look in the state table - if there is a state, then your rule didn't block it, or it wasn't killed when you thought you reset it.,
-
In fact, I do intend on having rules that are scheduled base as well. The idea is to implement a parental control using a combination of Home Assistant and PFSense. I know that I can enable/disable rules in Pfsense from home assistant so to simplify it, I can just create a regular non scheduled rules inside of pfsense and use Home Assistant automation to enable/disable the rules.
HA also gives me the ability to control the rules on the fly.Your thoughts?
As you're saying, if only a pass rule can remove the states, using a block rule as I'm using it now will not work if I'm enabling and disabling the rule on a dialy basis?
So for my purpose, what might the pass rule look like? I played with it a little this morning and couldn't quite figure it out.
-
@cheapie408 you would put your pass rule on a schedule..
https://docs.netgate.com/pfsense/en/latest/firewall/time-based-rules.html
-
@cheapie408
And followed by a block rule for the same source, so that following pass rules don't take effect. -
So this is what I got,
Created alias for RFC1918 with 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16
created a pass rule for the (single host) and block rule as shown. The passrule should remain active and when I want to turn on/off internet, I'd enable/disable the block rule?
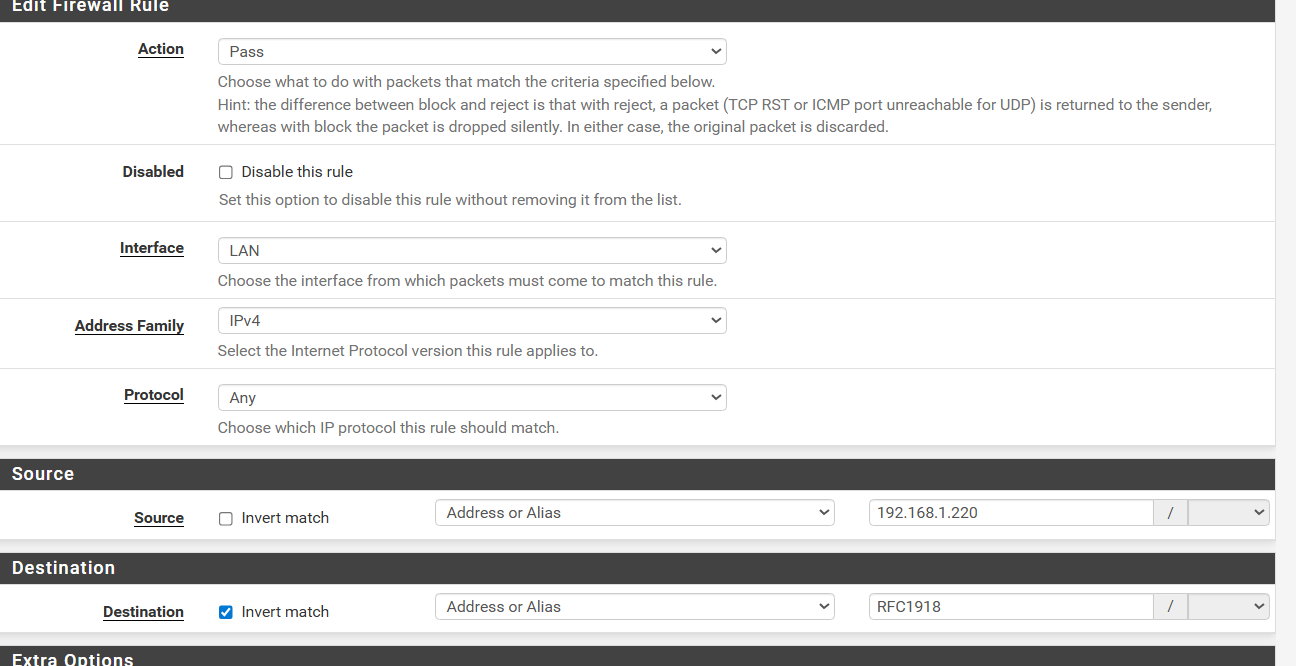
-
@cheapie408 You can also create a schedule, and add an entry to the schedule each time you want to grant extra access. Something like:
Mon - Fri / 6:00-7:00 / Weekday mornings
Wed / 7:00-7:15 / Late start day
Mon - Fri / 15:00-18:45 / Weekday evenings
Sat - Sun / 13:00-16:00 / Weekends
August 7 / 0:00-20:59 / (added extra time today)The block rule needs to always be enabled, so 2 rules:
- allow LL laptop during schedule
- block LL laptop
as noted in
https://docs.netgate.com/pfsense/en/latest/firewall/time-based-rules.html
Or you can just enable/disable the allow rule.
-
@cheapie408 background to was @SteveITS mentioned: the first firewall rule that matches will be used:
"Rulesets on the Interface tabs are evaluated on a first match basis. This means that reading the ruleset for an interface from top to bottom, the first rule that matches will be the one used by the firewall."
https://docs.netgate.com/pfsense/en/latest/firewall/fundamentals.html
-
@patient0 exactly and if the allow is on a schedule when time hits that the rule is not enabled, ie say after 10pm every night then any states created by that allow rule would be removed. If they try and go back they hit the block rule (which you currently have disabled) and the firewall would not allow, and no state created.
-
@SteveITS
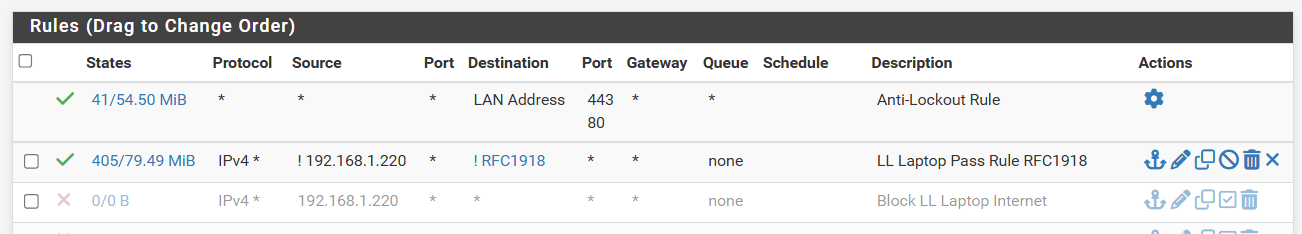
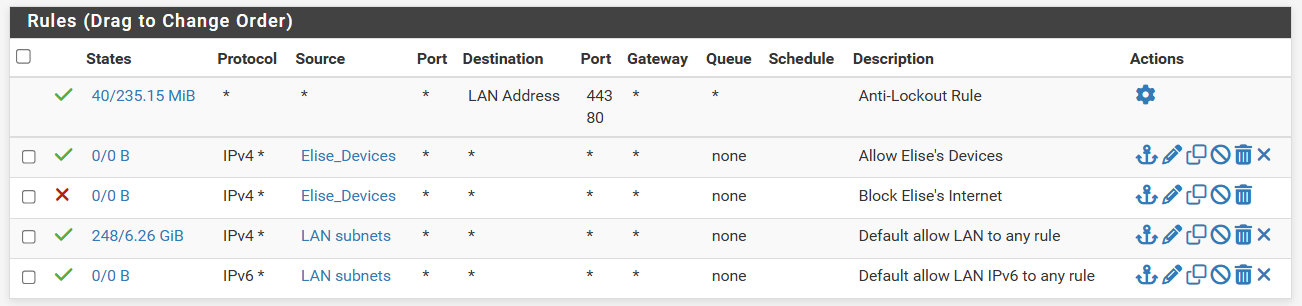
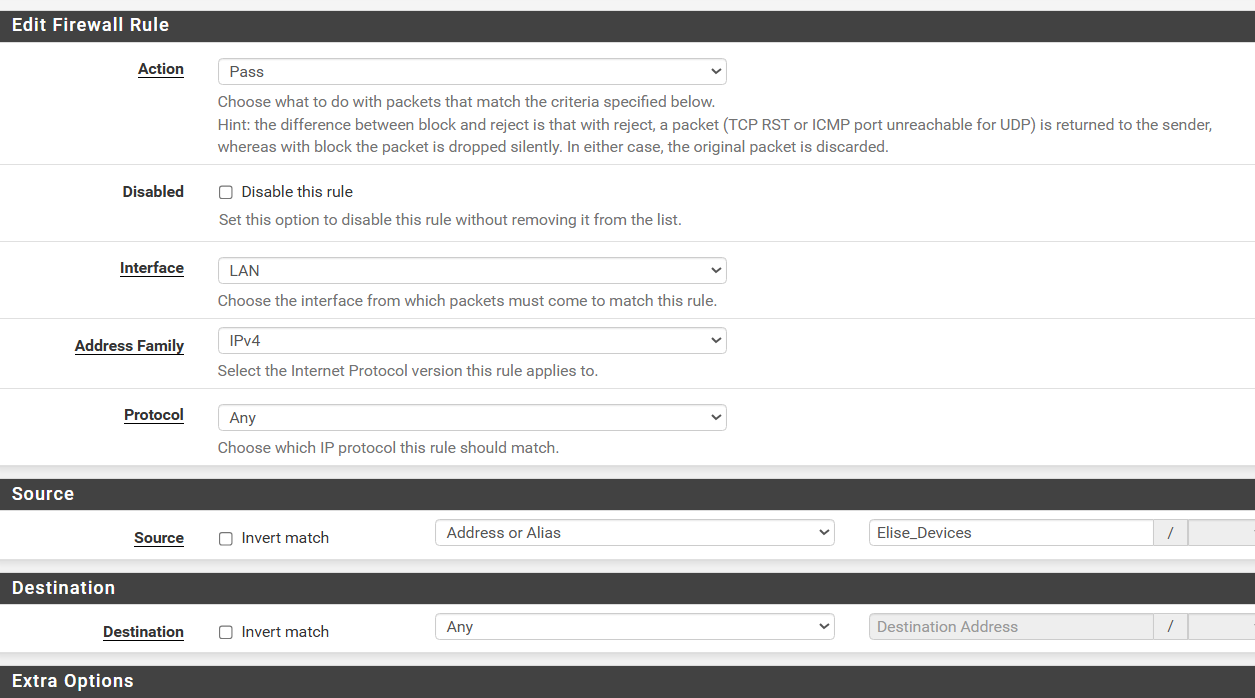
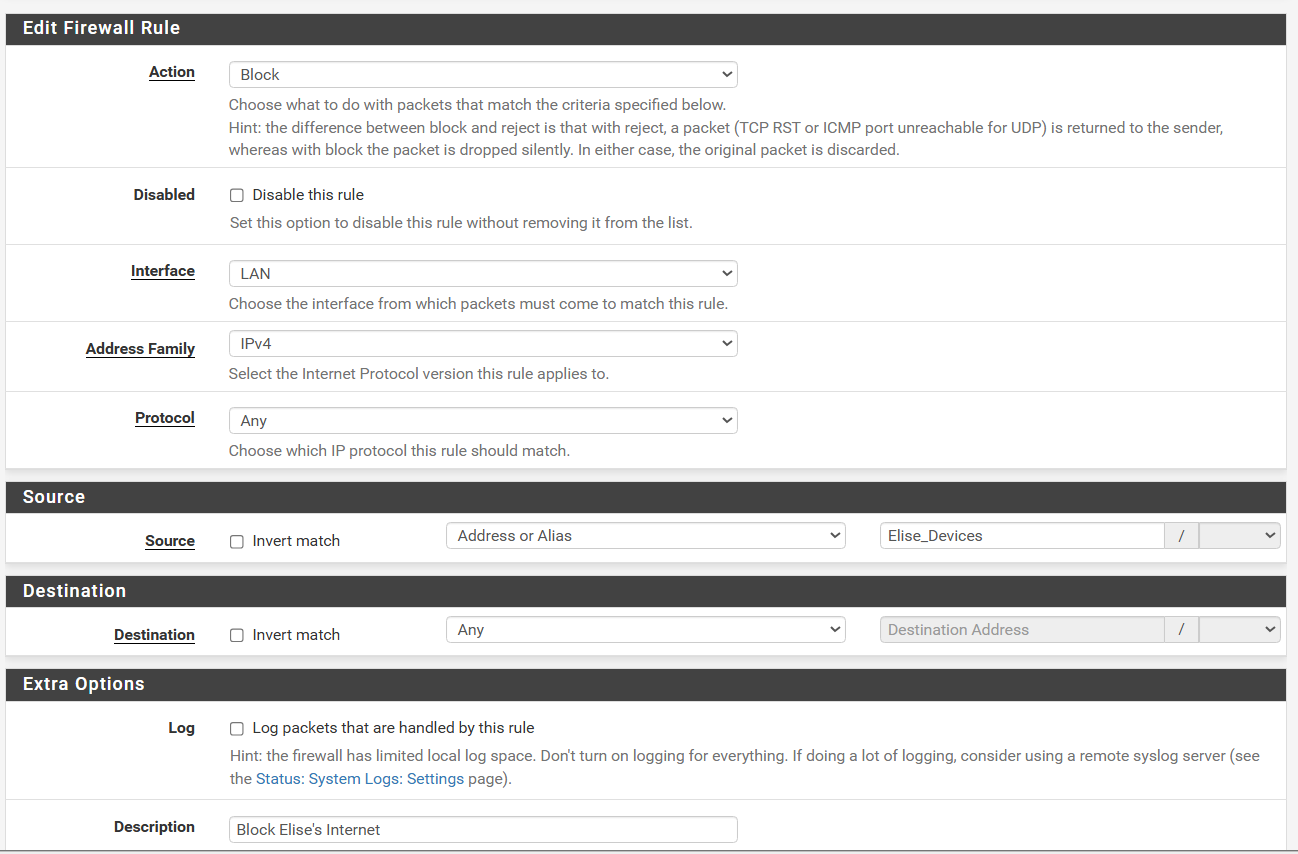
So to make this less complicated and take scheduling out of the equation of pfsense. Say I wanted to rely on Home Assistant to enable the block rule, so in PFSense there should only be one rule that I toggle.Based on what everyone is suggesting, this is what my setting looks like. I deleted all my previous and starting from scratch. These are mainly tablets and streaming device and they do not need local access when internet is off. When it's down time it's lights out.
The pass rule is above the block rule for Elise's devices. The block rule remains enabled at all time and because the pass rule is above the block rule, when it is enabled, it will ignore the block rule and allow traffic through. So when I want to turn on/off internet, the pass rule is what I'll be toggling. Sounds about right?
-
@cheapie408 said in Blocked internet but it's still "Kind of" working:
So when I want to turn on/off internet, the pass rule is what I'll be toggling. Sounds about right?
Kind of, yes. It's the same as a scheduled rule but you're manually turning it on and off. Which is why we all digressed, I guess. :)
I am however unclear on whether any open states will be killed once the rule is disabled. I suspect they are not, and it is the schedule that handles that.
There's a discussion and a few possible options on this Reddit thread, found in a quick search.
-
@SteveITS not sure why something like this couldn't be simplier in pfsense, the logic is simple. I guess the claim of "enterprise level" adds some weirdness to it.
I tested this just now on my own laptop just replacing elise's device with my own IP.
This is what I observed, when pass rule is disabled, it takes maybe 30 2nd before pinging starts to fail. If I have a youtube video playing, the entire video will complete but will fail on the following video.
Google search no shows no internet and browsing to website also no longer works.
I'm reading up on the link you provided now. Kids are smart these days, they figure out how to bypass the block anyway they can so we gotta be ahead of them. LOL
-
@cheapie408 said in Blocked internet but it's still "Kind of" working:
takes maybe 30 2nd before pinging starts to fail
Yeah that's the open state ending. Also the video, because the connection is not yet closed. It might stop if you pause playback long enough, not sure. IOW new connections are blocked.
Since we have no admin access to our son's school Chromebook and I wanted to leave IPv6 active, we use the pfSense Plus feature to block its MAC address. I did create my wife a pfSense login to access only (IIRC) the firewall schedules, though she mostly just asks me to edit them. So I can add an entry for "today," default start time "12 am" (who cares) and I set an end time.
Windows/iPhone/iPad are different but at least there we have the MS/Apple parental controls.
-
In my case the "kids" are all grown up & moved out, but few years back I went through all this pain. For many years I simply showed them the firerwall logs & used "embarassed teenager" mode to get them to self limit.
Full blocks frequently caused moans of "can't I just have 10 more minutes", etc.
The best solution was speed limiting their laptop, phones & game consoles to about 50kbps (or less). They couldn't complain "the internet" wasn't working because searches still worked, but most things became unusable !! Then an hour later full block.
-
I will keep this advise in my parenting note pad and apply it in a couple years. I like it!