pfBlockerNG not logging anything by default?
-
@Gertjan said in pfBlockerNG not logging anything by default?:
Because "you don't want to". (no time, other interest, etc
What do you mean? I am unfortunately not a software engineer nor a hardware specialist. It would probably take me years to figure any of this stuff out. Definitely no time for that. My switch has a console port but I never used it thus far.
@Gertjan said in pfBlockerNG not logging anything by default?:
And that's a good thing.
Just know that you can see them if you need to.
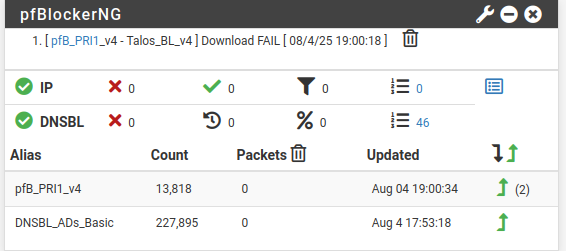
pfBlockerng makes already nice stats for you.So on that clean machine with a fresh install you recommend installing pfblockerNG? But how is it a good thing if I don't see what is going on? I need some sort of log that would show these weird domains to me in case they happen there as well on a separat network. If I hadn't installed pfblockerNG I would not even have seen whats going on. I consider that a bad thing. Or one could say ignorance is bliss?

BTW: I haven't seen any new entries since my work computer is off. Yesterday it happend after it was off but I think only because I tried to ping it from my laptop and through pfsense. So I feel like my work computer is the culprit which is not great either...
-
This post is deleted! -
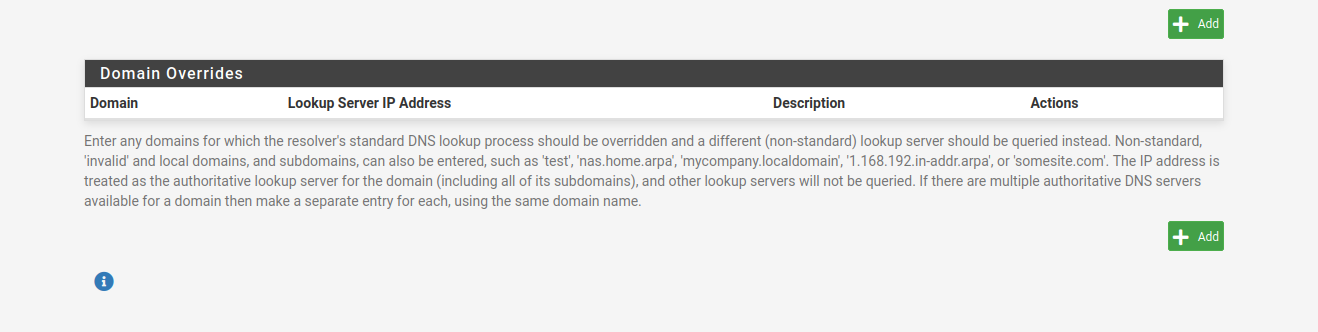
Is it possible to set a *.local and *.arpa domain override here to get rid of all these entries?
-
Wild cards like *.something are not allowed.
Domain Overrides is meant to be used for something completely different.
Be sure to rename your :
then, if you have to, locate the device that sends these DNS requests. Shut it down or find the process sends these requests, and kill it.
-
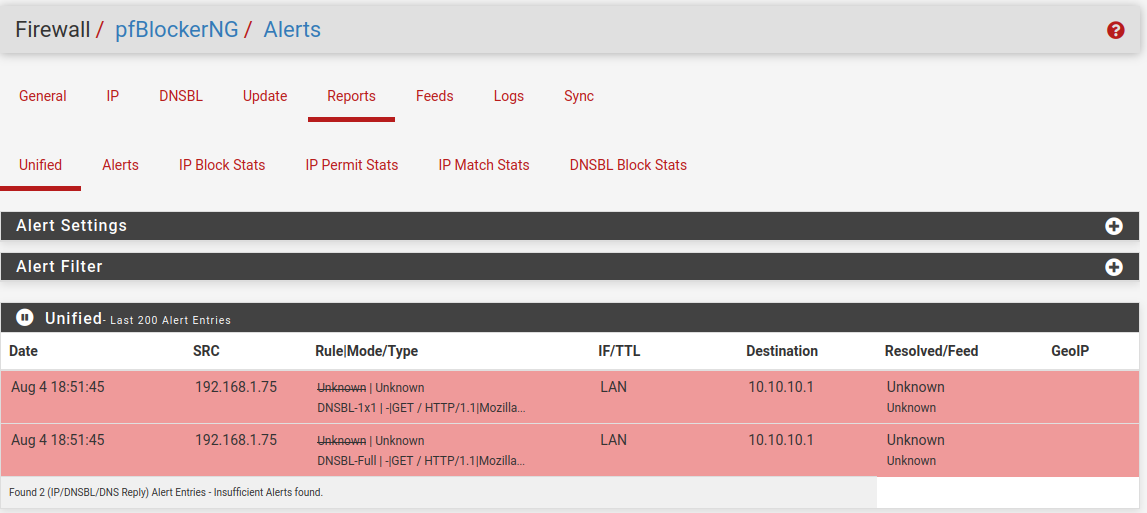
@Gertjan Whenever it is a full hour I see stuff like this in my logs:
https://otx.alienvault.com/indicator/ip/94.16.122.152
It seems to be time servers but it's a TOR node and some private person hosting traefik? I feel like this should not show up? It originates from my ASUS access point. But it is also related to when the emerging threats get updated. All happens at the full hour mark. I don't know why some random private persons ntp server gets queried. -
This post is deleted! -
So today I had just my work computer running behind pfsense as an experiment and I am still seeing these weird DNS queries. Now for the weekend I will only use my laptop and see what happens. If I am still seeing these queries there must be something up with pfsense.
-
Why would pfSense generate random host names / URLs ?
If it (unbound) has to resolve "otx.alienvault.com" then that was because it was asked to do so. The request came in by LAN, and was handled. And logged.
Shut down all LAN devices, and "DNS requests" will stop.
The ones still there will be 'Netgate' or 'time server' based.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
https://otx.alienvault.com/indicator/ip/94.16.122.152
Where - what log - did you find that URL (DNS only deals with host names) ?
-
@Gertjan s7.vonderste.in resolves to 94.16.122.152. I just saw a dns request for that. In the whitelist on OTX Alienvault there is a timeserver: 3.de.pool.ntp.org
I just don't know why a timeserver runs on a TOR node and seems to be hosted by a private person.
Maybe pfblocker resolves it incorrectly becaues the time server is hosted on the same IP?
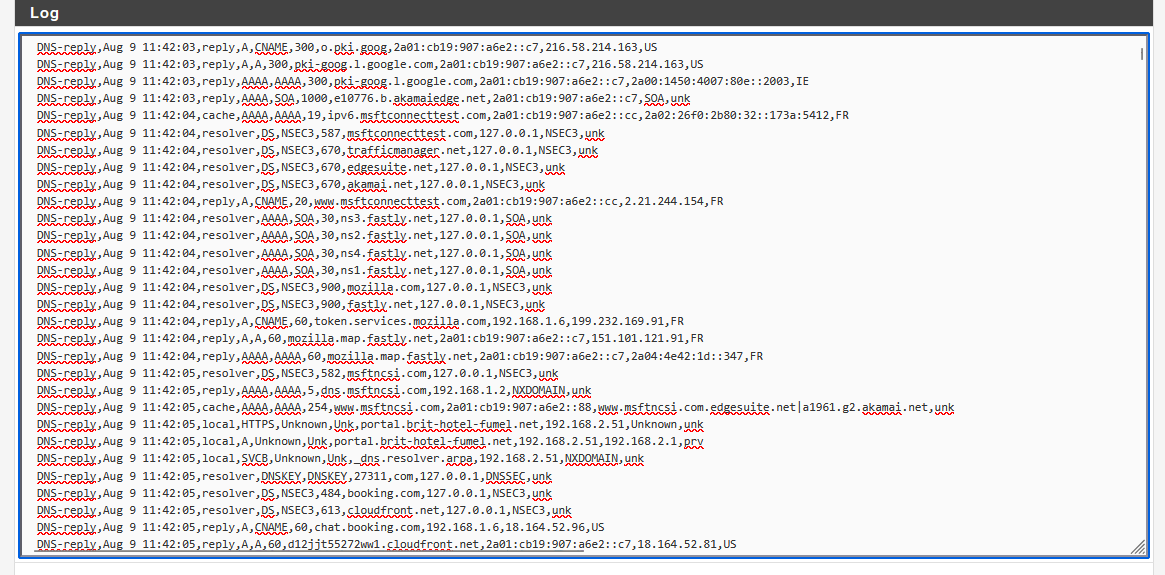
Anyway I see this coming from my ASUS router which is in Access Point mode. These weird domains always come up every hour and I think they are related to ntp on that ASUS router. Since I disconnected it it has stopped. Here is an example of what I see. Scanning these IPs shows nothing malicious but who knows.93.122.215.85.in-addr.arpa,192.168.1.8,sonne.floppy.org,unk 94.244.38.46.in-addr.arpa,192.168.1.8,basilisk.mybb.deWhat didn't stop was on my work computer these weird replies as mentioned above.
reply,A,NSEC,1081,domaincontroller-gPHvwjYS.local,192.168.1.86,NXDOMAIN,unkBut it only happend once today instead of multiple times like the days before.
@Gertjan said in pfBlockerNG not logging anything by default?:
Where - what log - did you find that URL (DNS only deals with host names) ?
I find them in pfblockerNG dns_reply log under Logs
EDIT: I just realized that it is kind of in the name pool.ntp.org
its made up of multiple sources so it does make sense that it resolves some of these weird private hosts? -
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
its made up of multiple sources so it does make sense that it resolves some of these weird private hosts
An public NTP pool like pool.ntp.org would not list host names with weird random paddings that reference local devices.
"domaincontroller-gPHvwjYS.local,192.168.1.86" is a reverse PTR, and is requested by one of your local
devices.
Why , I don't know.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
I find them in pfblockerNG dns_reply log under Logs
No URLs there, only host names.
-
@Gertjan said in pfBlockerNG not logging anything by default?:
"domaincontroller-gPHvwjYS.local,192.168.1.86" is a reverse PTR, and is requested by one of your local
Yes these local domains are requested by my work computer. They are unrelated to NTP. I was talking about these entries every hour:
93.122.215.85.in-addr.arpa,192.168.1.8,sonne.floppy.org,unk 94.244.38.46.in-addr.arpa,192.168.1.8,basilisk.mybb.deAre you using pool.ntp.org? If so what does it show at the full hour for you? Like 12am, 1pm etc?
I read that it's made up of a pool of timeservers that are closest to you to get the most accurate time. That's why they get queried. -
I finally got around installing a new pfsense firewall and the first connections I am seeing right of the bat are lets say strange. I don't know what they are:
https://otx.alienvault.com/indicator/ip/178.250.1.11
https://www.abuseipdb.com/check/178.250.1.11
https://www.virustotal.com/gui/ip-address/178.250.1.11/community
https://viz.greynoise.io/ip/178.250.1.11Aug 10 11:07:09 WAN Default deny rule IPv4 (1000000103) 178.250.1.11:443 192.168.178.21:18414 TCP:PAIts incoming from WAN trying to get to the firewall. Very mixed results here.
Never heard of criteo and it is flagged by some people despite being whitelisted on otx alienvault. I remember seeing the same the first time I installed pfsense on my other machine I think. Any idea what it could be?
I also did a packetcapture and there are losts of ACKed Unseen segments. Does this indicate anything?
On my other firewall I don't see anything coming from WAN to LAN but on the new one there is so much IPs. What can it be?