HAProxy Port Redirect Internal
-
-
So I turned off SSL offloading. Since the acme/letsencrypt cert I made earlier is now being used by webConfiguator. I figured the two acme/letsencrypt and self signed certs may be clashing???
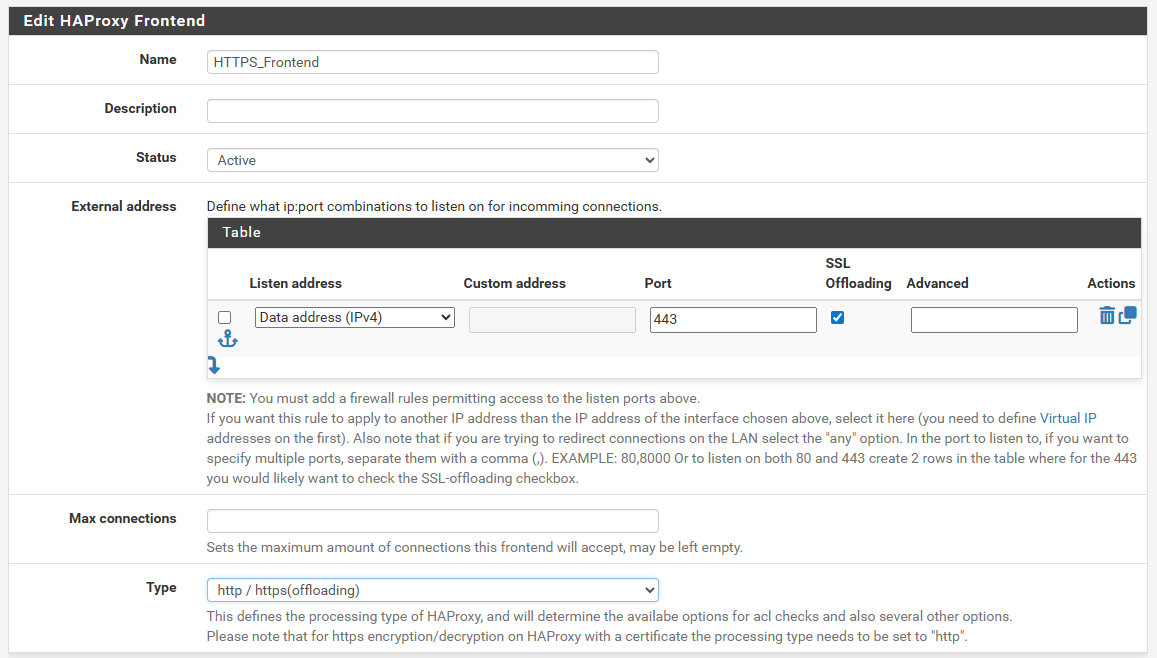
Basically I am now just trying to use HAproxy as a port redirect. Again my webConfiguator is set to listen on port 443 and backend on 10443. I thought this was baked into the whole front end listening on 443 and the backend set for 10443.
This is being done entirely inside of my own LAN. Later I want to try SSL offload and front end listen on 443 then backend on 80 for my blueiris security cam web server that can not do SSL.
-
@spiker said in HAProxy Port Redirect Internal:
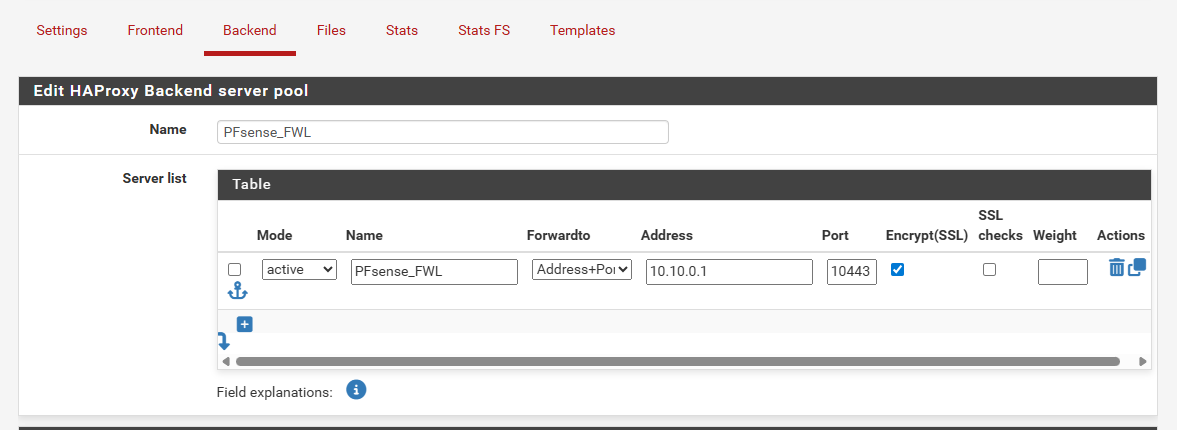
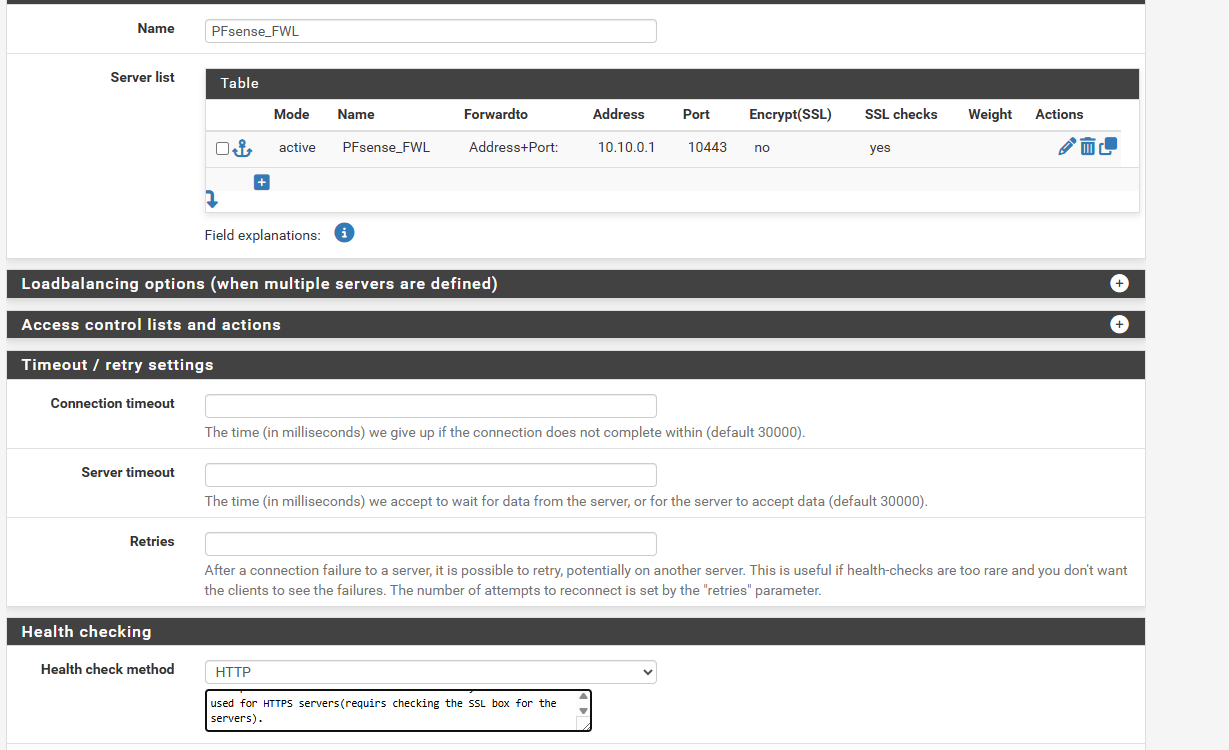
I have the acme certs working just fine through HAProxy but I have to manually put in the destination port, in my case 10443. I have the front end set up to listen on the network in question and on port 443, and the backend set for 10443.
What do you get exactly if you access port 443?
-
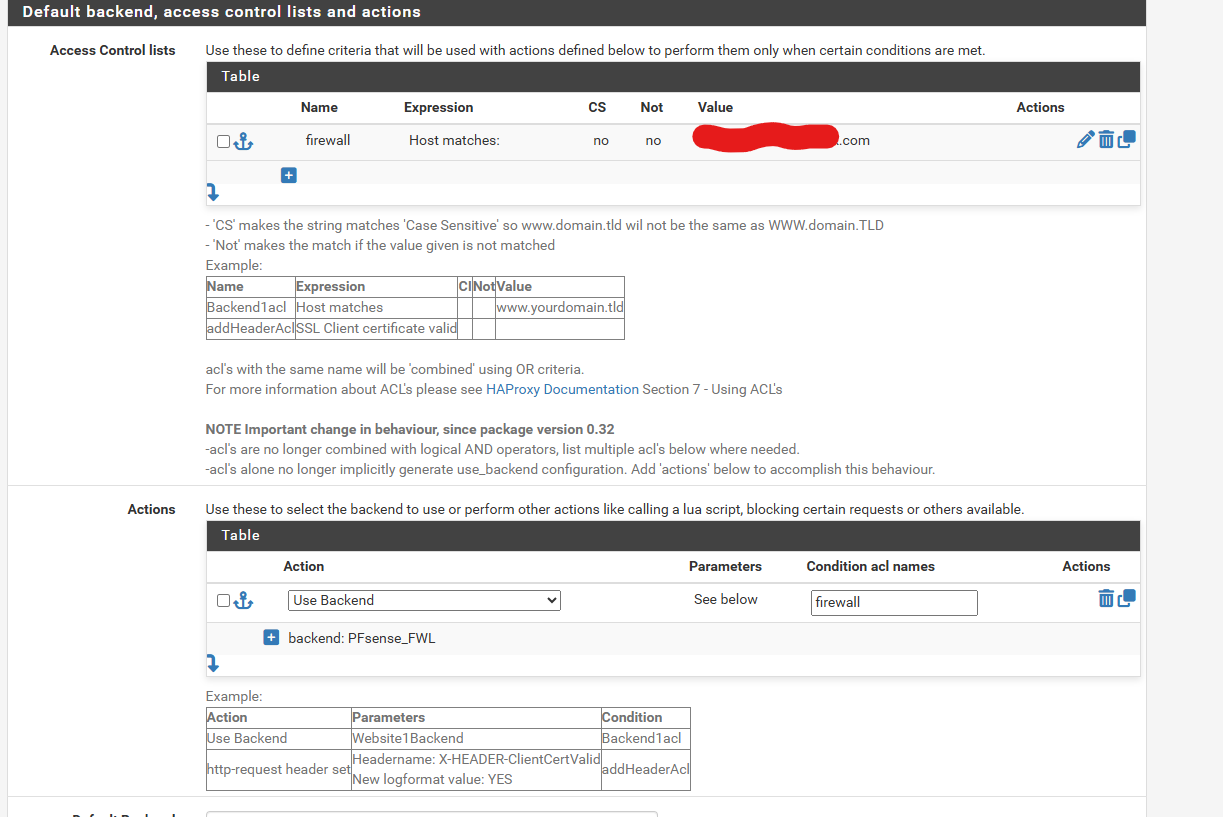
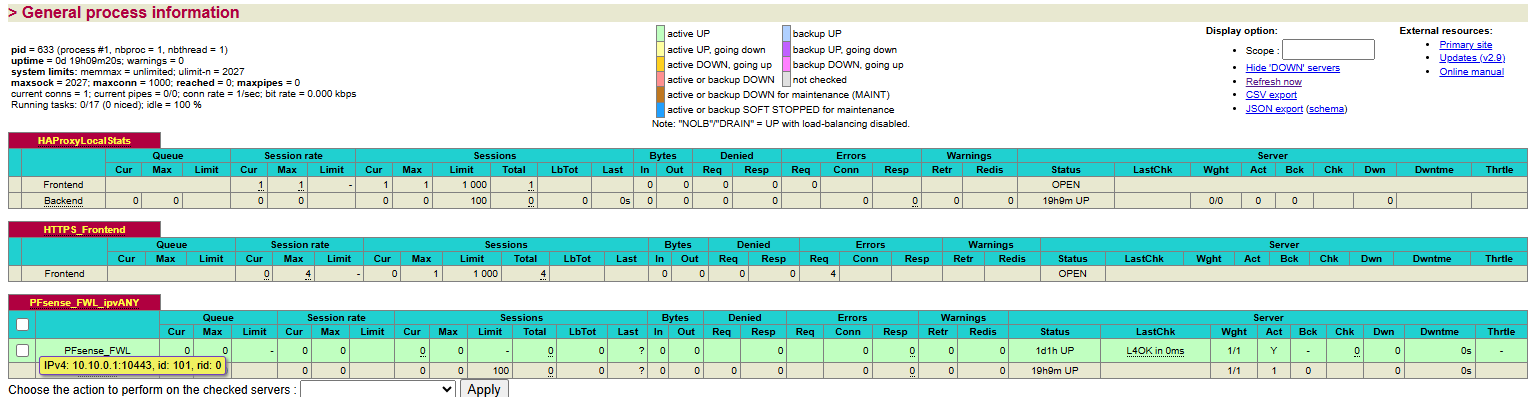
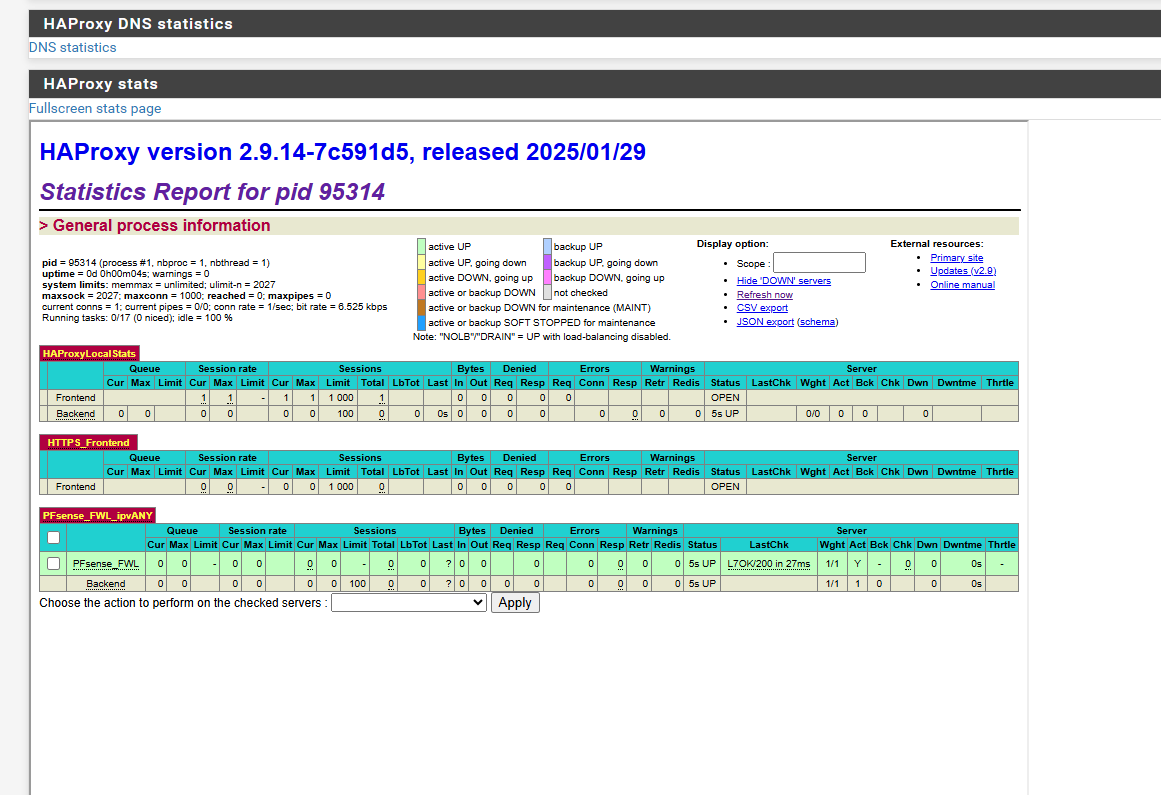
@viragomann What does the HAProxy Stats page show for the PFsense_FWL backend? It will show if the backend is up or down, and what the error is. Hover your mouse cursor over the backend and confirm that it shows
10.10.0.1:10443. -
Another test you can do is create a new frontend on a different listening port, set no ACL or actions, and then set the Default backend to PFsense_FWL. Then try accessing the new frontend. This will rule out any issues with your ACL matching.
-
-
-
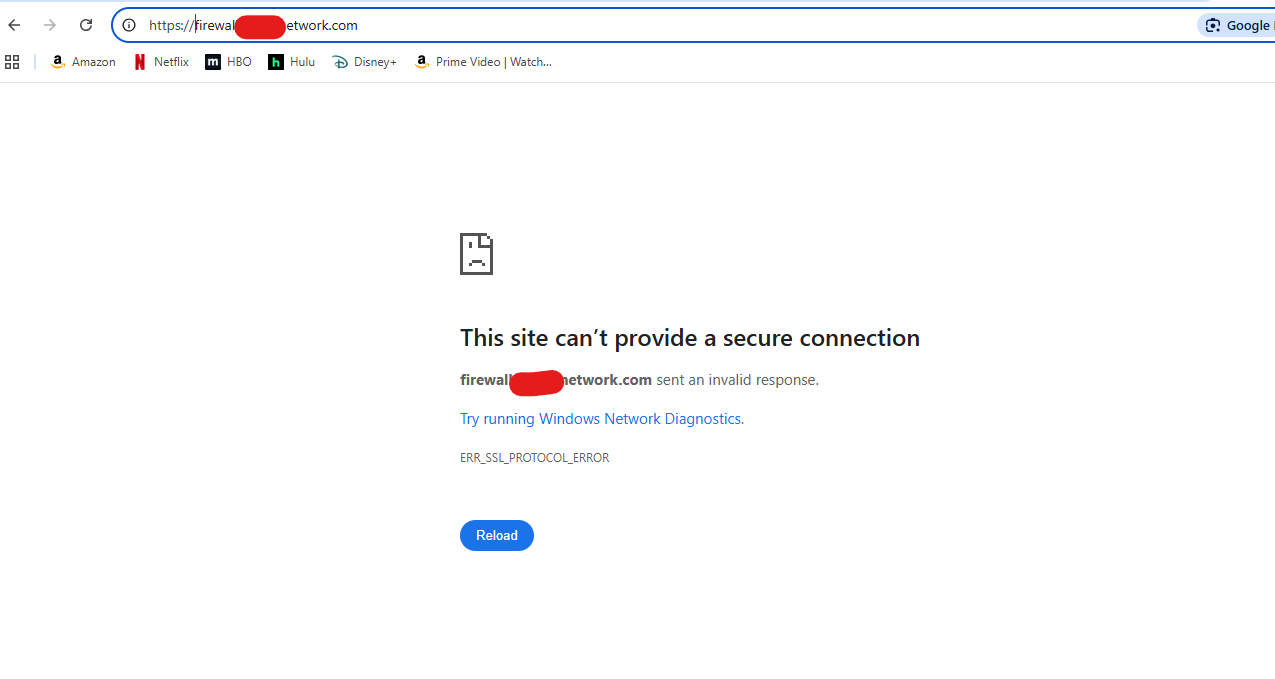
The SSL cert works fine when I navigate directly to the web interface on the configured port 10443.
-
@spiker Can you access your firewall by going directly to https://10.10.0.1:10433 ?
If you change the health check for the backend to HTTP, does it still show as UP?Also, try adding
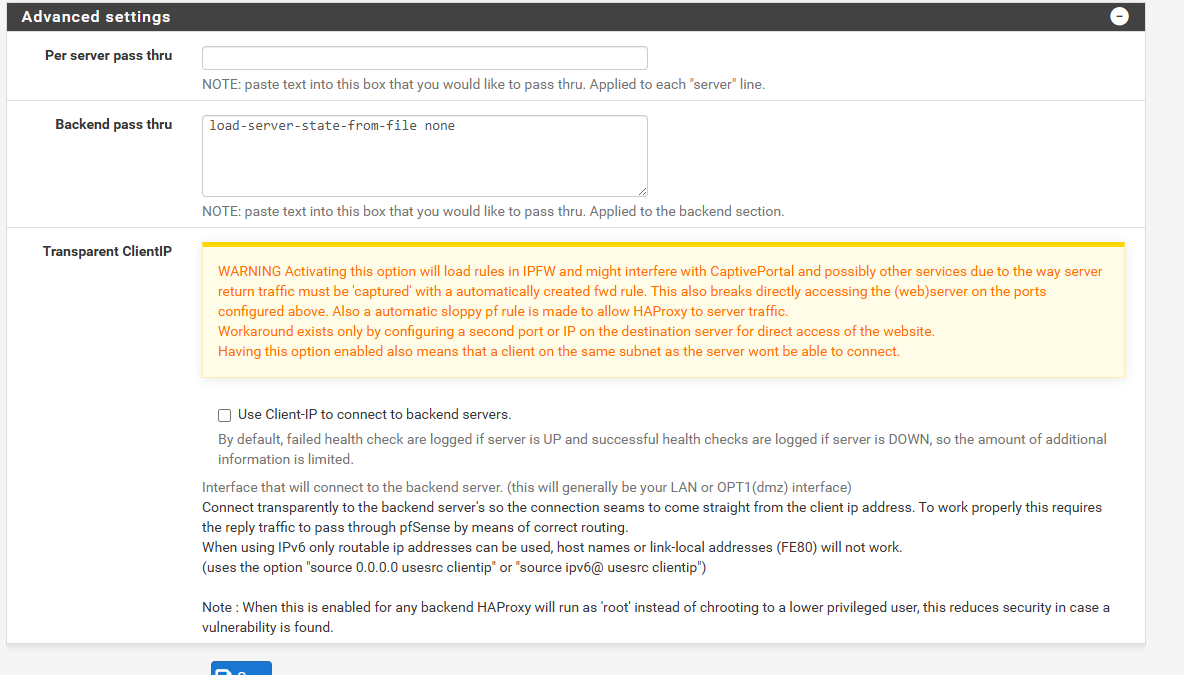
load-server-state-from-file noneto the Advanced Settings > Backend pass thru section of each backend, as by default HAProxy will save the backend server state, and any changes will not take effect. -
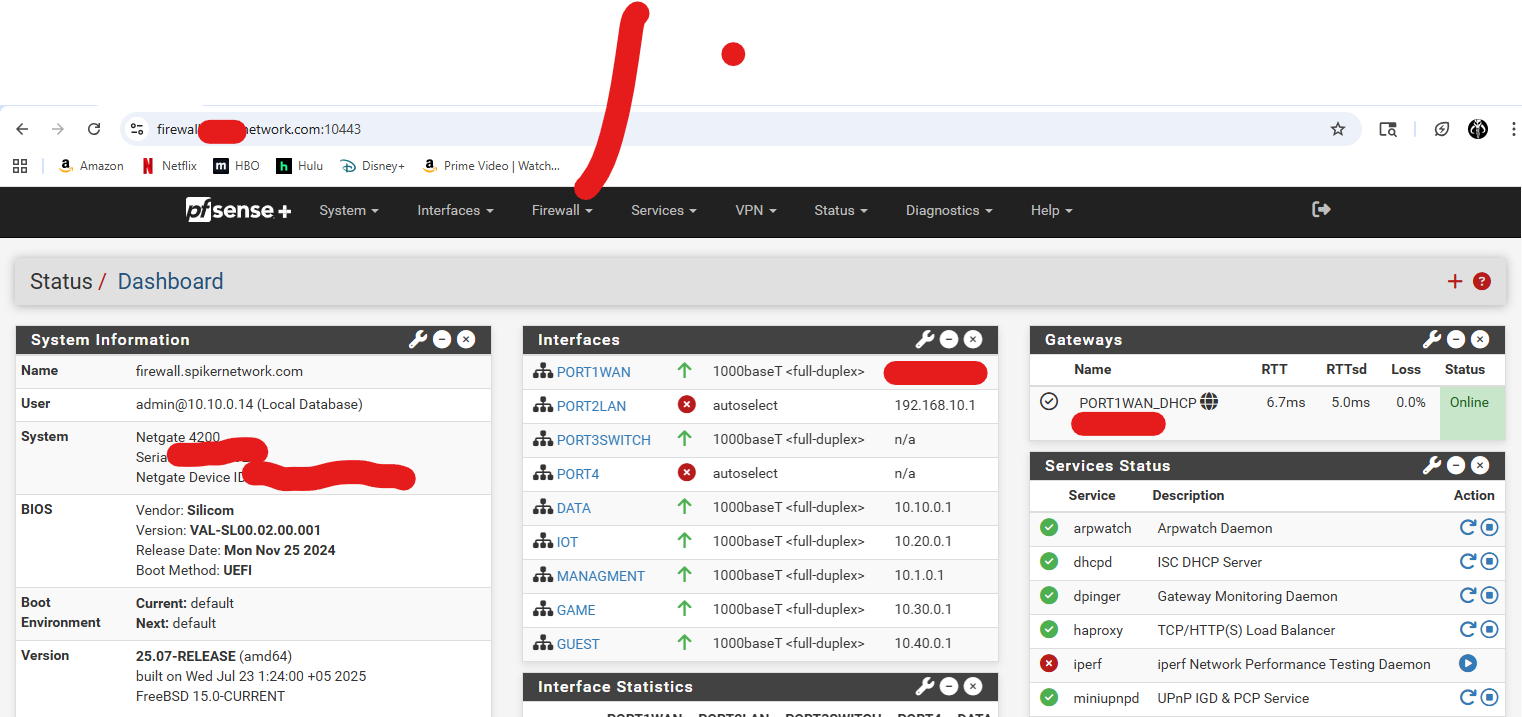
I can directly access the FWL from https://10.10.0.1:10443
let me change the health check and take a look.
-
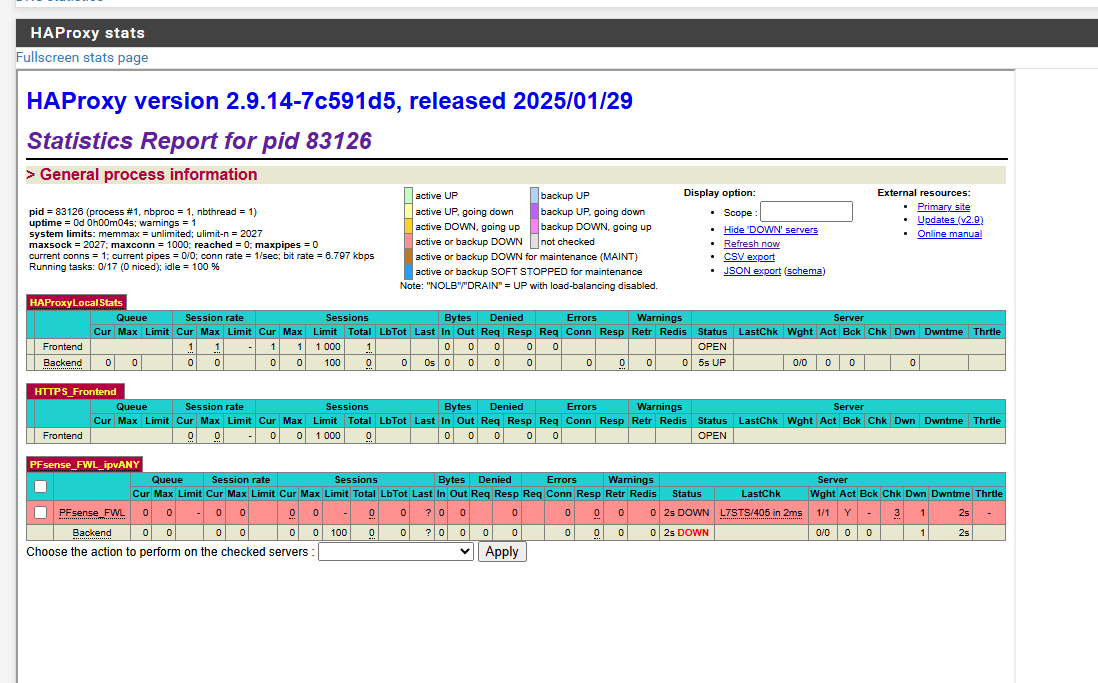
Ok change the backend health check from Basic to HTTP and also checked SSL checks per the notes in the health check method field. It looks down now
-
@spiker
Did you even add the proper certificate to the frontend? -
So I turned off SSL Offloading, but yes I have a proper cert on the front end.
Really I an misusing haproxy here by just trying to get it to port redirect for one of my networks from 443 to 10443.
-
@spiker
If you turn off SSL offloading, you cannot access HAproxy using https. So the error in the browser, you shown above is plausible. -
@spiker Mouse over L7STS/405 and see what it says.
I am doing the same thing that you are trying, and it works for me.
I do see that myHttp check methodis set to GET instead of OPTIONS, so try that and see if that fixes the health check status. -
Ok turned SSL offloading back on, and selected the valid cert I set up with Acme/letsencrypt.
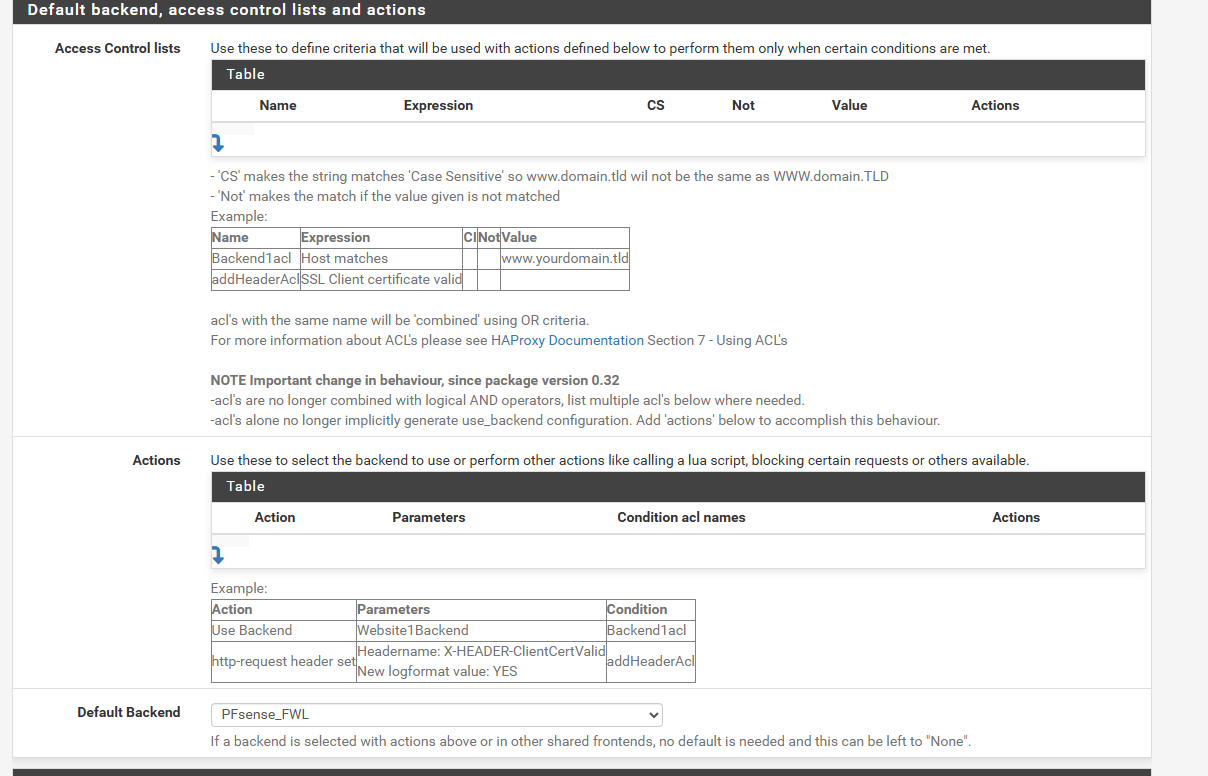
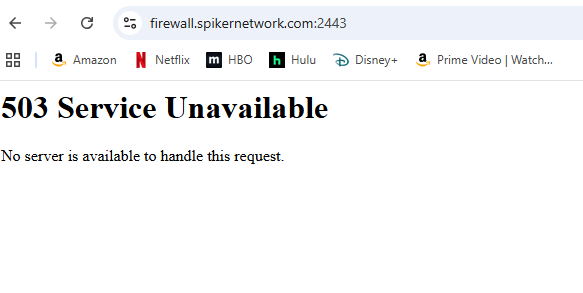
I set the new front end to listen on 2443 and killed all the ACL's and set the default backend to PFsense_FWL
did not blur out my domain but I do not plan on opening any services from WAN anyway.
-
"I am doing the same thing that you are trying, and it works for me.
I do see that my Http check method is set to GET instead of OPTIONS, so try that and see if that fixes the health check status."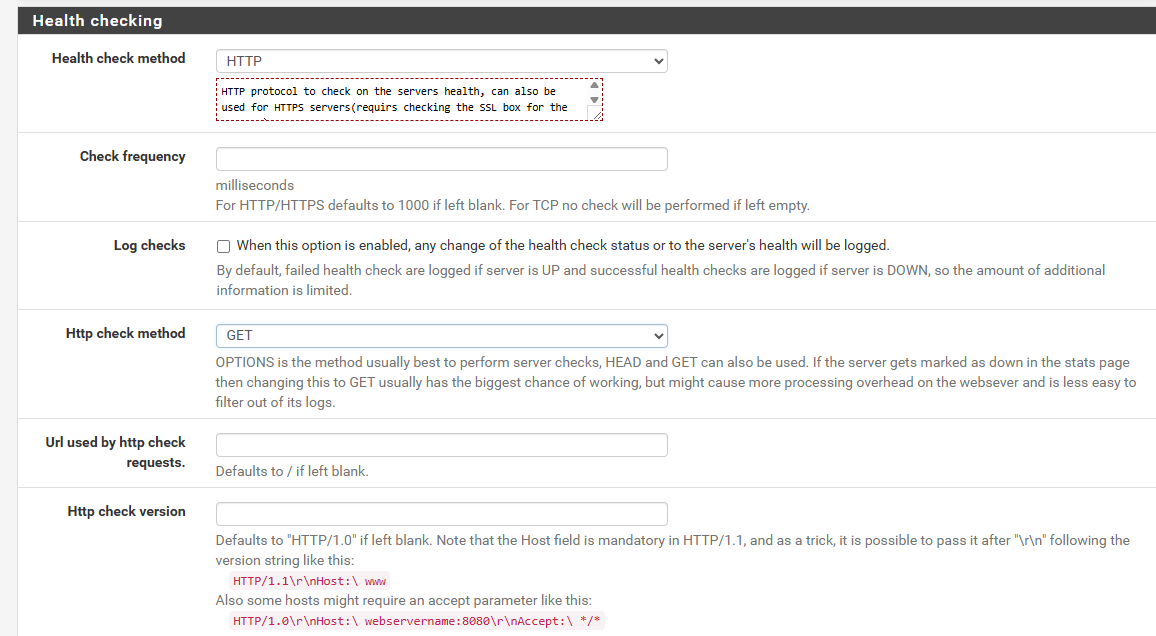
-
@spiker
This is the web UI directly accessed.What do you get without the port stated?
Edit:
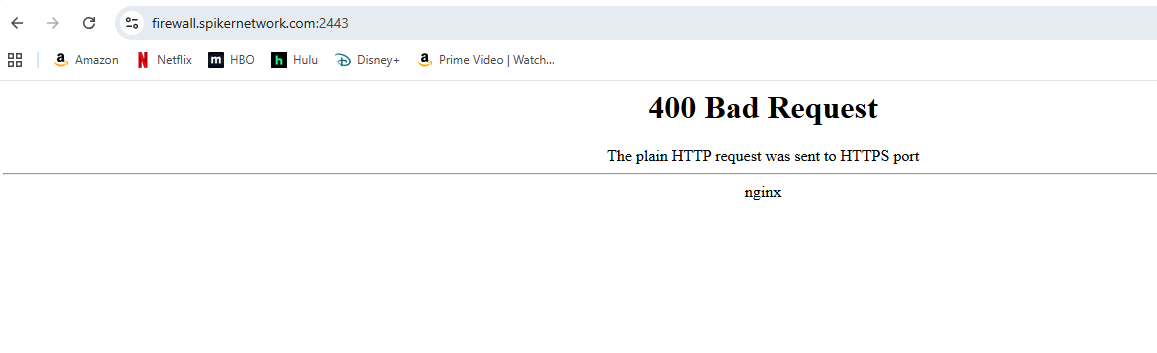
Oh well, your frontend ist listening on port 2443 now. -
As the error message indicates, your web UI is forced to use https, but HAproxy uses http for accessing it.
-
Yeah directly accessed would be on port 10443, and that works just fine, cert and all.
I do have a rule on all other interfaces/networks to block port 10443, but I am on the network that is stated in the front end and that interface has no rule to block 10443 to the FWL address.