GeoIP Blocking with pfBlockerNG
-
Hi,
I've been using pfSense for about 10 years with mostly no trouble. I'd like to block traffic from many countries outside the U.S. to our web site to handle the insane amount of traffic we've been getting from bot nets all over the world.
I installed pfBlockerNG and got a MaxMind License key. If I go the the Firewall > pfBlockerNG > GeoIP tab, I selected some countries in the "Top 20" category and then choose "Deny Inbound" as the "List action". We're getting a lot of bot traffic from other countries not on the Top 20 list, so I did the same thing for the other continent lists that include those countries (Africa, Asia, etc.).
After the cron did its update, I see six new rules at the top of my Firewall Rules page, each one corresponding to one of the lists of countries (see image).
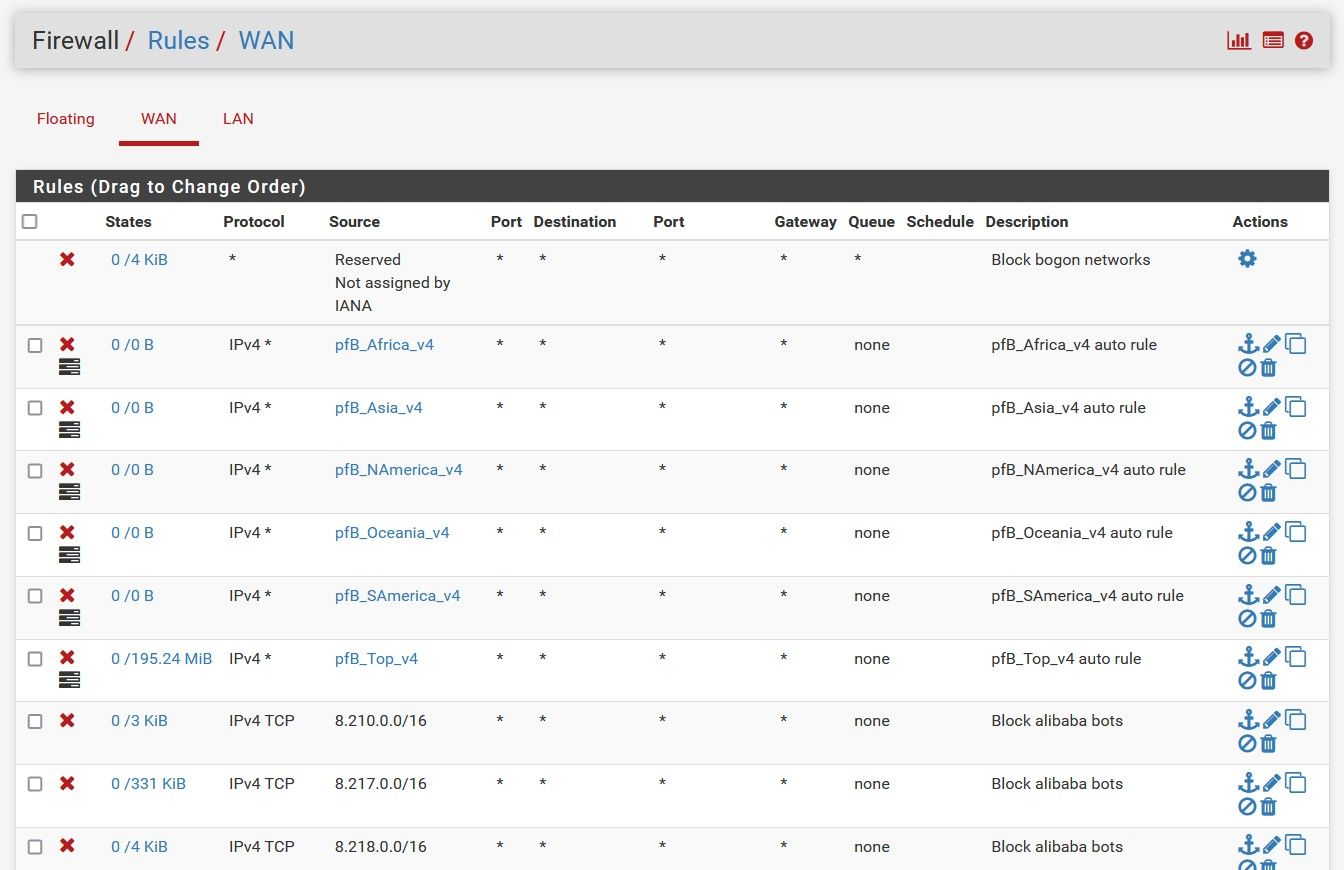
If I drag my mouse over the name of the list (in the "Source" column), I can see the lists of IP network addresses for each list. If I look at the firewall logs, I can see that the pfB_Top_v4 list is working: hundreds of connections from IPs on that list are being blocked every second.
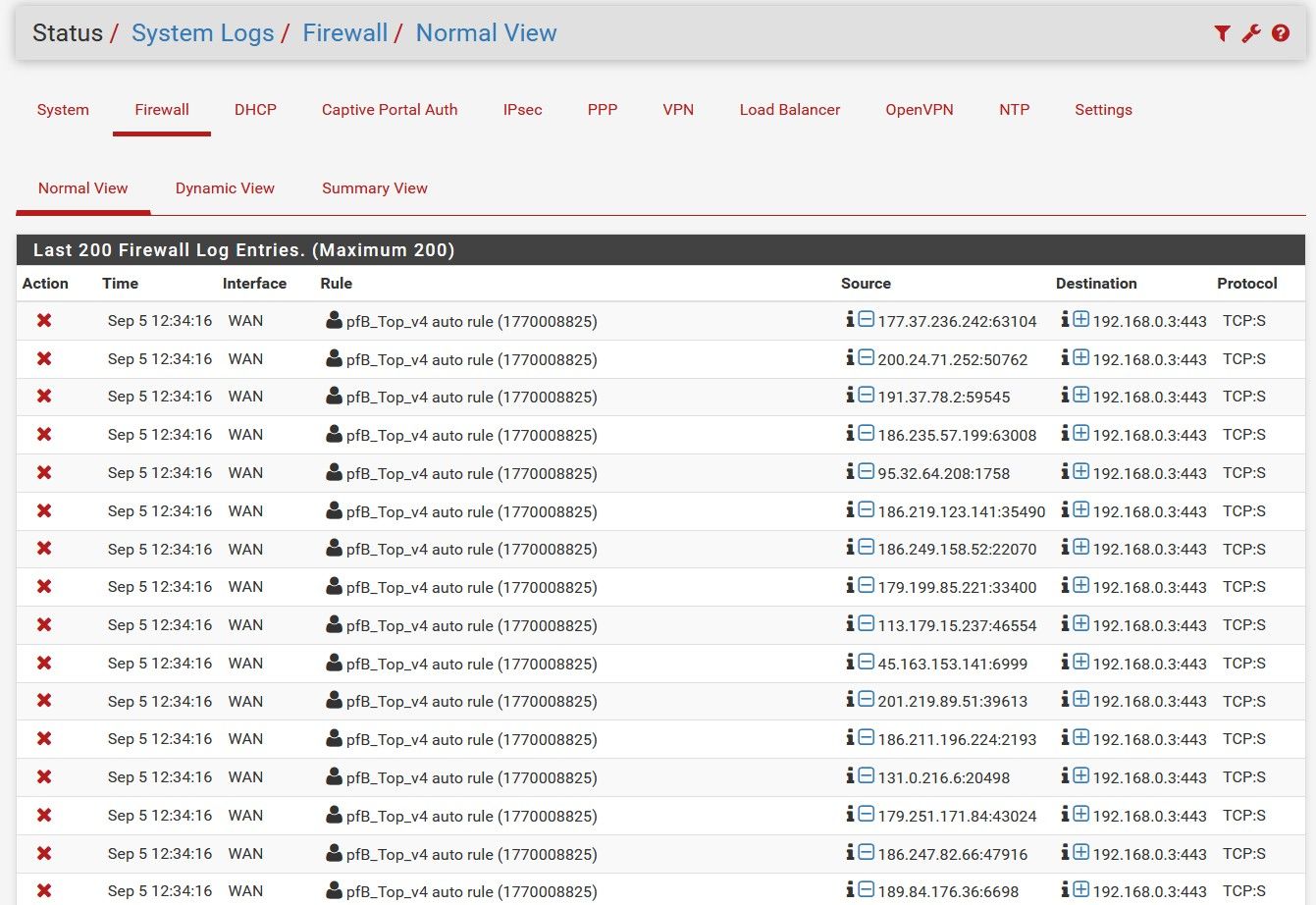
However, traffic from the other five continents is not being blocked. It looks like the configurations for all six GeoIP lists are the same, but only the "Top 20" list is actually working.I would like to get all six block lists working. Any insight as to what I should do would be appreciated. Thank you for reading this.
Theodric Young
System: Netgate SG-4860
Version: 2.4.5-RELEASE-p1 (amd64) -
@theodric Everything is fine with your rules.
I suspect there isn't much traffic matcing.
If yoou are interested in just two or three countires maybe its better to allow just those
But also do take care other needed traffic too.Denying access to the world isn't a good idea in practice, however if you know what you are doing its an option.
-
@netblues Hi, thanks for your reply. Actually there is a huge amount of traffic that is getting through that matches the IP networks in the other lists (Africa, Asia, SAmerica, etc.). I can see traffic from those IP networks in the web server logs.
Thanks again for your comment.
Theodric
-
@theodric Hmm, the rules look correct. Are you saying you can identify IP adresses in your webserver logs that you can also find within the ranges in the source blocklists (verified - not guessing)?
I’d say you are just not seeing traffic that matches or there is something in the pfBlocker IP lists you are fetching that causes them to be defective.
-
those other rules are not triggering - the 0/0 shows nothing matched on those rules.
Did your ruleset fully load? You start creating lots of lists, you could be run into tables memory issue, and some off the rules might not even load.
Do you have anything in floating that could be allowing it?
I am with @netblues trying to block the world is normally a bad idea - vs trying to block all the bad guys its easier to just allow the guys you want.
I have rule that allows only US based IPs, and belgium - because users of my services I have opened would all be in the US, and some family members currently in belgium.. There is little point to creating block lists for all the other continents. Since if they are not listed in my allow then they wouldn't get in.
-
@theodric agree just allow your country.
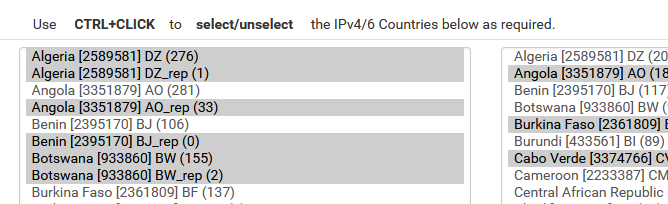
One pitfall for the continent blocks is you still need to select the countries on the page, otherwise the generated aliases are empty.
-
-
@SteveITS that is a great point - yeah I think those lists are empty until you pick what you want in them..
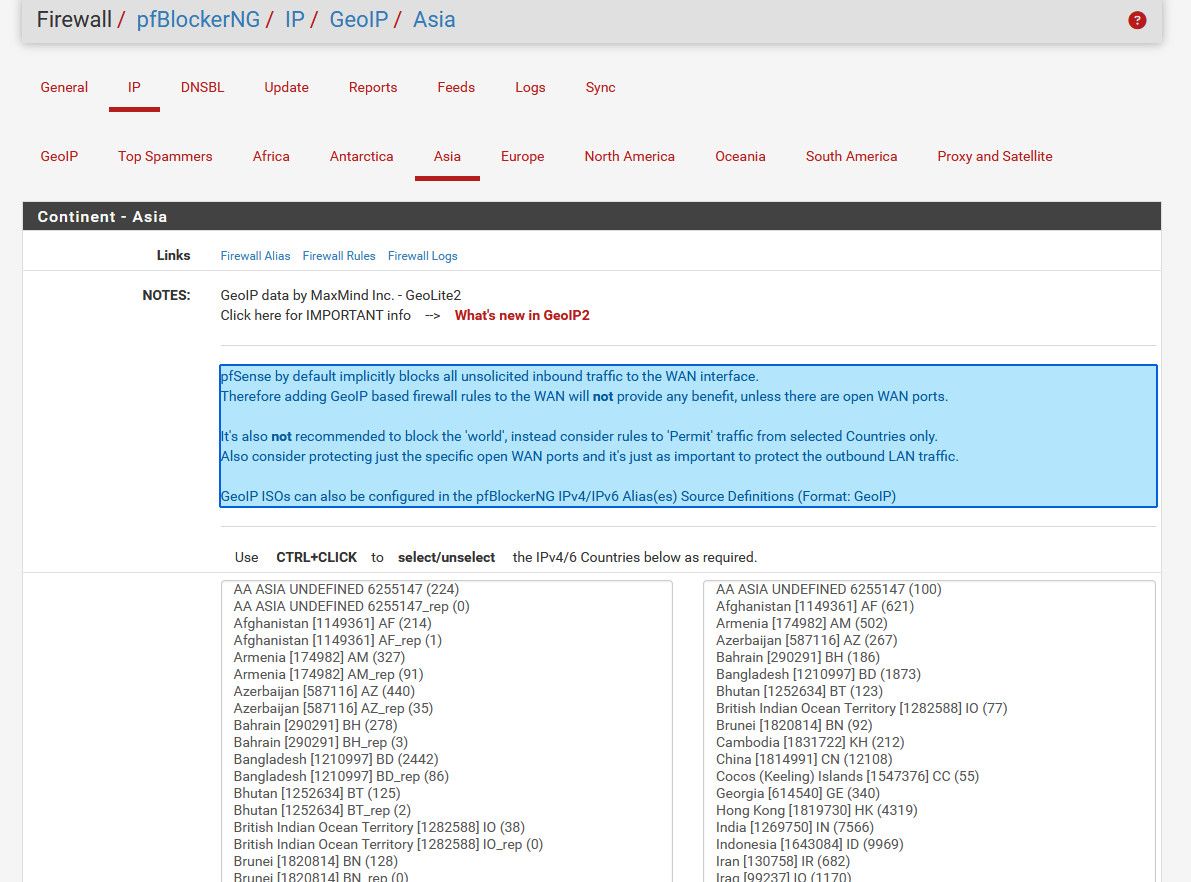
I just took a look at them and nothing is selected in any of them.
-
@theodric said in GeoIP Blocking with pfBlockerNG:
Theodric Young
System: Netgate SG-4860
Version: 2.4.5-RELEASE-p1 (amd64)And while we are at it, how about upgrading to a recent version?
Teaching an old dog new (pfblockerng) trcks won't cut it.I'm not saying this is the issue though too.
With the seer amount of "generated" traffic perhaps opting for a two server setup is the option.
Fairs better than a server farm with a load balancer and lots of instances. (unless of course money is not an issue and you are facebook, or maybe tesla)Setup a web front for the country traffic that interests you, and send all other traffic to another instance
If you are using haproxy, you will need to handle this there, with the additional benefit of rate limiting bulk traffic.
If you are doing nat, then this can be done at the nat port forward level, where you can specify pfblocker generated source ip lists. Send a few countries to the premium web server and the rest to another instance, and let it "burn".
Augment list with a block list at the wan level for the known "abuse" countries (like china , pakistan, brazil and india) and you will be good to go. -
@netblues good catch - I didn't even notice that... Yeah that is quite an old version.. 2020..
Looks like 6 major versions behind.. That is crazy..
-
…and for a couple years, give or take, MaxMind has required the additional field/info to update so the geoIP data probably isn’t updating.