pfb_filter and pfb_dnsbl services are not running Pfsense 25.07.1
-
@nanda said in pfb_filter and pfb_dnsbl services are not running Pfsense 25.07.1:
PfblockerNG-dev log contains sanity check failure,
This won't be stopping it - also there is "fix" for the miscount in the forum.
This thread discusses the line that needs to be changeddid you do a force reload ?
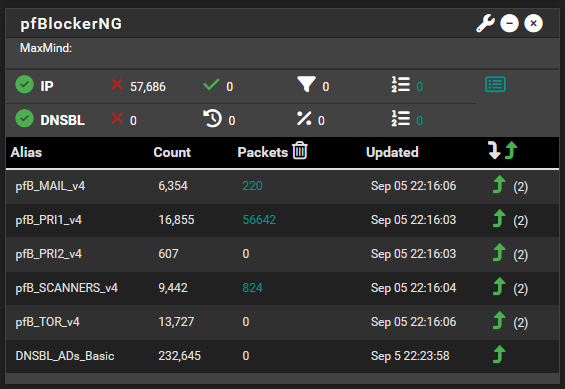
what does the pfblocker dashboard widget show ? -
This won't be stopping it - also there is "fix" for the miscount in the forum.
This thread discusses the line that needs to be changedThe specified line is changed and the same thread is also referred in given the question.
did you do a force reload ?
Yes, force reload performed after file change.
what does the pfblocker dashboard widget show ?
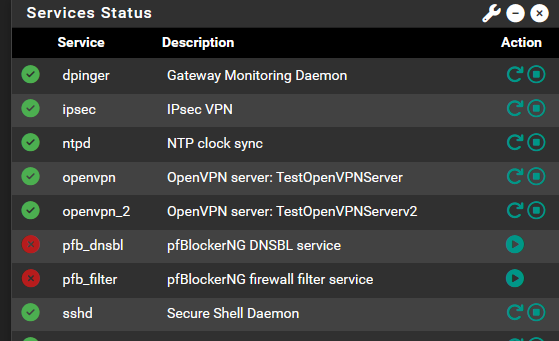
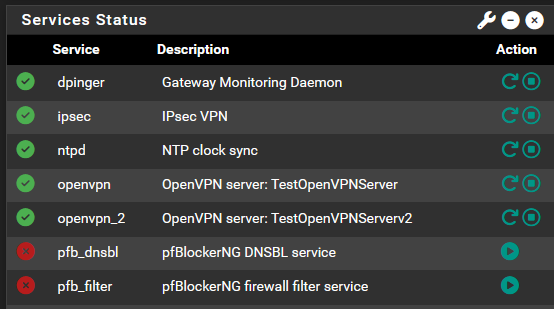
Same result (please see the 1st image)
-
@nanda said in pfb_filter and pfb_dnsbl services are not running Pfsense 25.07.1:
Same result (please see the 1st image)
That's the services widget on the dashboard - not the pfblocker widget what does it show ?
-
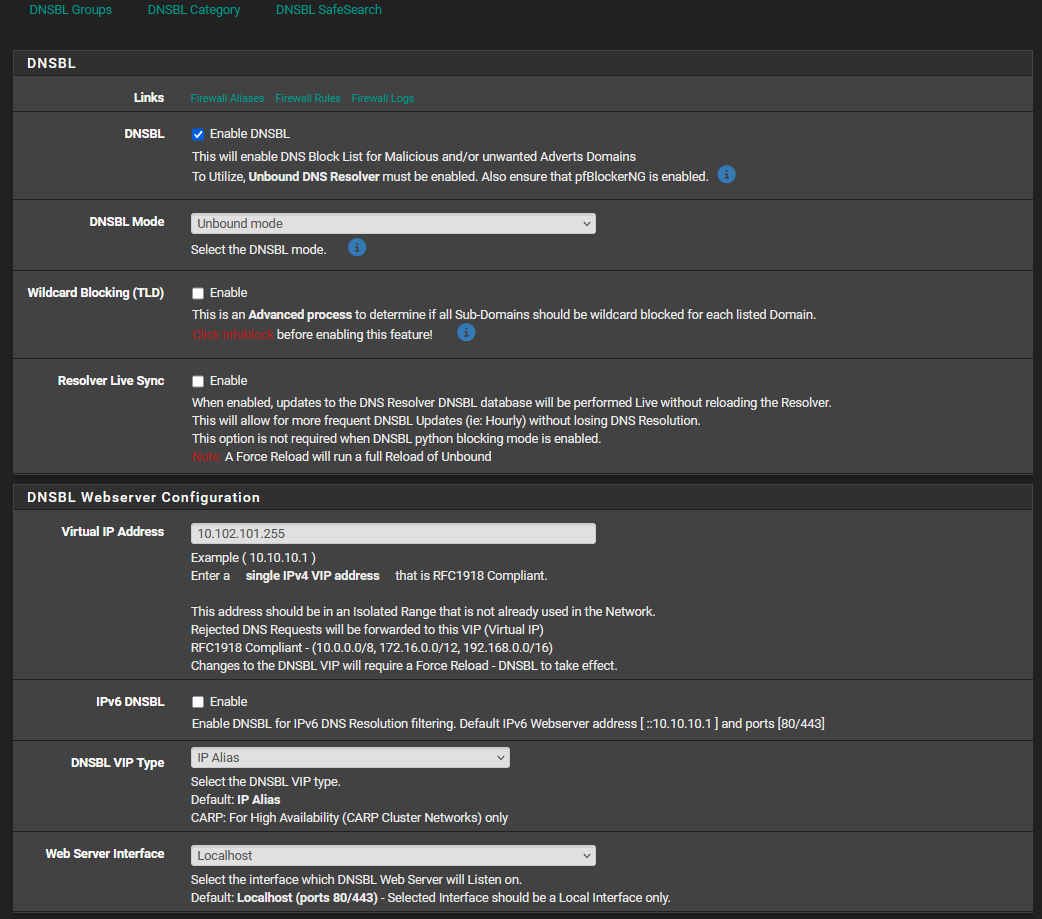
can you show us the dnsbl setup page python mode? and any other settings you may have - image of the settings page would be helpful
The certificate error you are showing is likely the show stopper.
what blocking mode are you using ? DNSBL Web/VIP? Null block no logging? or null block (logging) ?
the certificate error might suggest you are using. DNSBL Web/VIP but let's confirm -
Have you got any packages installed that include openssl ?
what version is installed ?
openssl version -
That's the services widget on the dashboard - not the pfblocker widget what does it show ?
can you show us the dnsbl setup page python mode? and any other settings you may have - image of the settings page would be helpful
Please see the screenshots below:
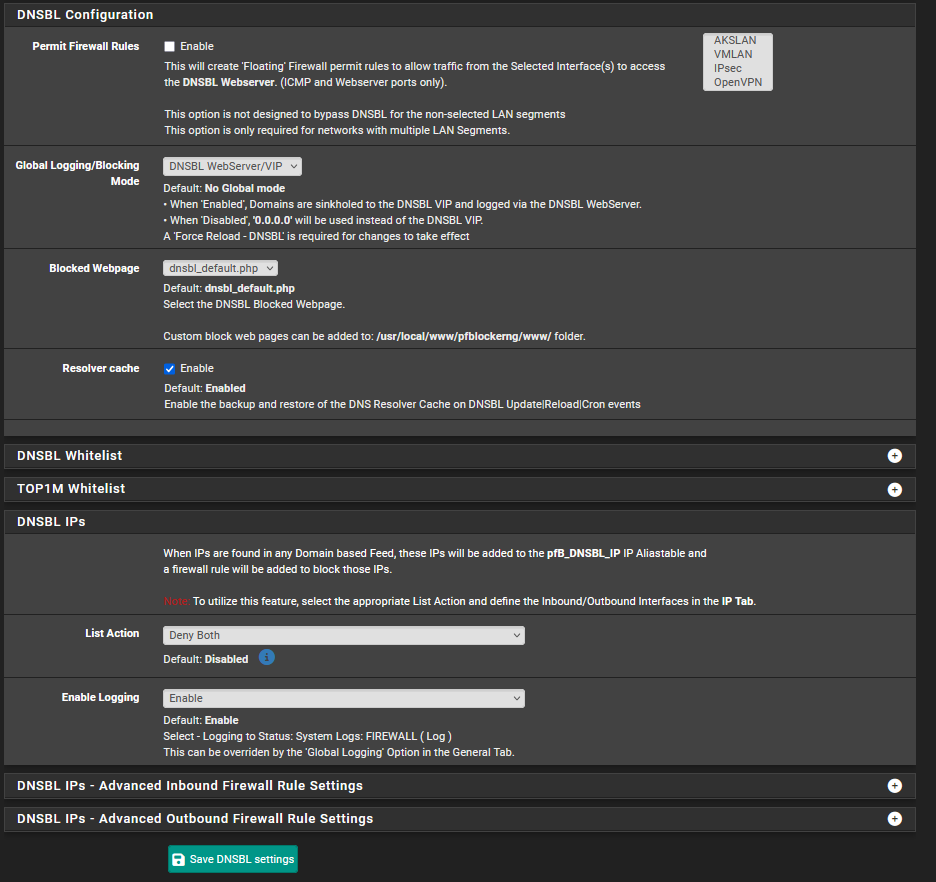
The certificate error you are showing is likely the show stopper.
If this might be the case, how it will affect pfb_filter daemon service? pfb_dnsbl did require certificate whereas pfb_filter did not.
what blocking mode are you using ? DNSBL Web/VIP? Null block no logging? or null block (logging) ?
DNSBL Web/VIP
Have you got any packages installed that include openssl ?
I do not see any installed packages, from given information, that include openssl. I think openssl is a necessity for pfsense functions, for example, certificate generation, and it will be a part of pfsense image.
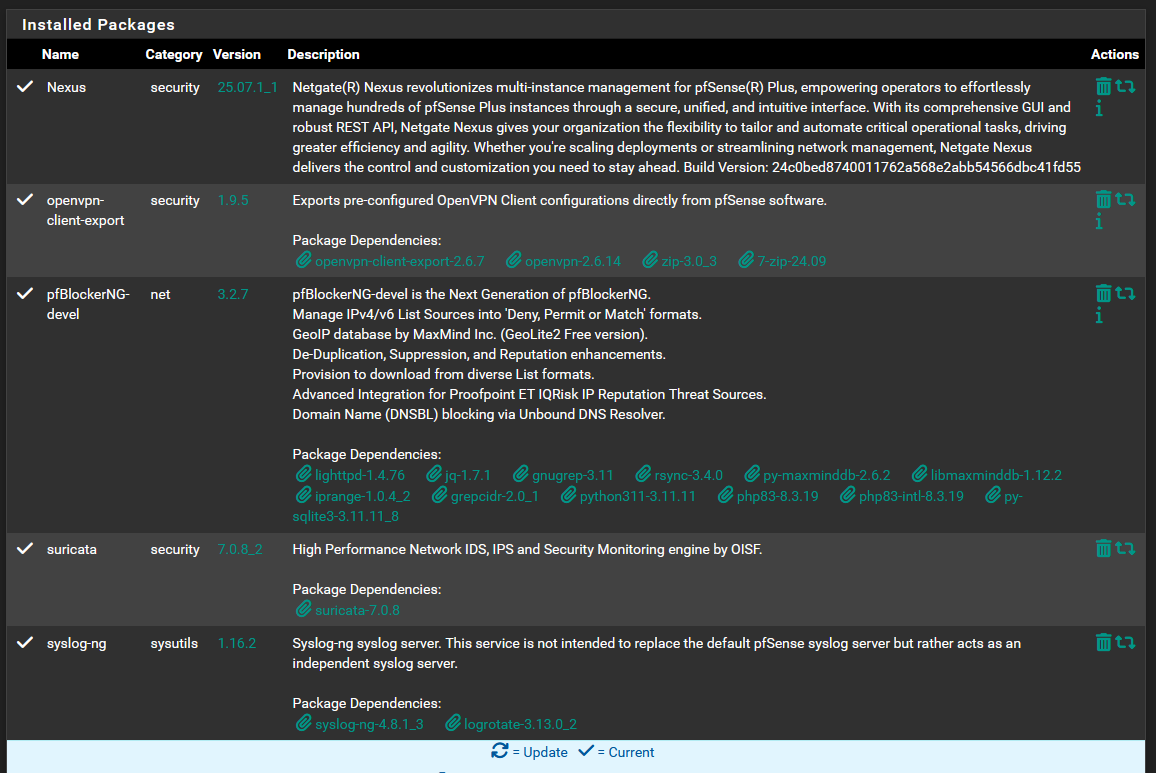
what version is installed ?
[25.07.1-RELEASE][suser@...]/: openssl version OpenSSL 3.0.16 11 Feb 2025 (Library: OpenSSL 3.0.16 11 Feb 2025) -
Let me take a look -- just recovering from a 3 hour power outage, which caught an 18TB raid in the middle of a rebuild after a failed drive was hot swapped earlier this morning -- might be a bit before I can spin up my test systems -- Fun Friday.
Not that it should matter here - but any reason you don't use unbound python mode ?
Uses Less Memory (what are you running on for RAM)
you mentioned it was a clean install.new install - are clients using this as the DNS now?
that dashboard widget sort of says it is running (hasn't done anything (0 count) and are the services still down at that point ? usually when the services are down the check mark is what you see.
the Virtual IP address that end in .255 seems like a strange choice unless you have a very specific setup - is there a reason you picked that instead of the default ?
I'd be curious if you willing to try - if you turned off the DNSBL Webservice/VIP and used say Null Blocking (logging) - then see if the services start and stay running ?
Actually in my setup I have the "no global logging" option selected on that screen and then set Null Blocking (logging) on the individual selections -
-
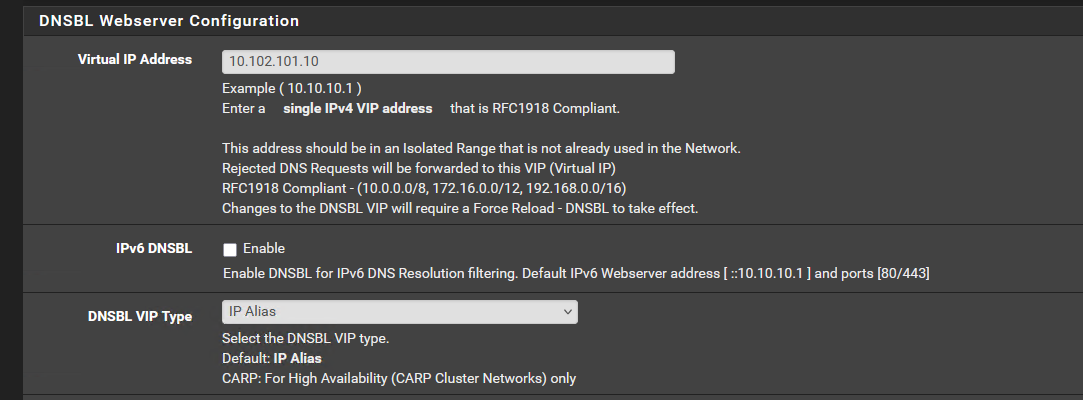
The usage of specific IP address has no special reason. It is for convenience.
The configuration is changed as recommended.DNSBL mode => unbound python mode
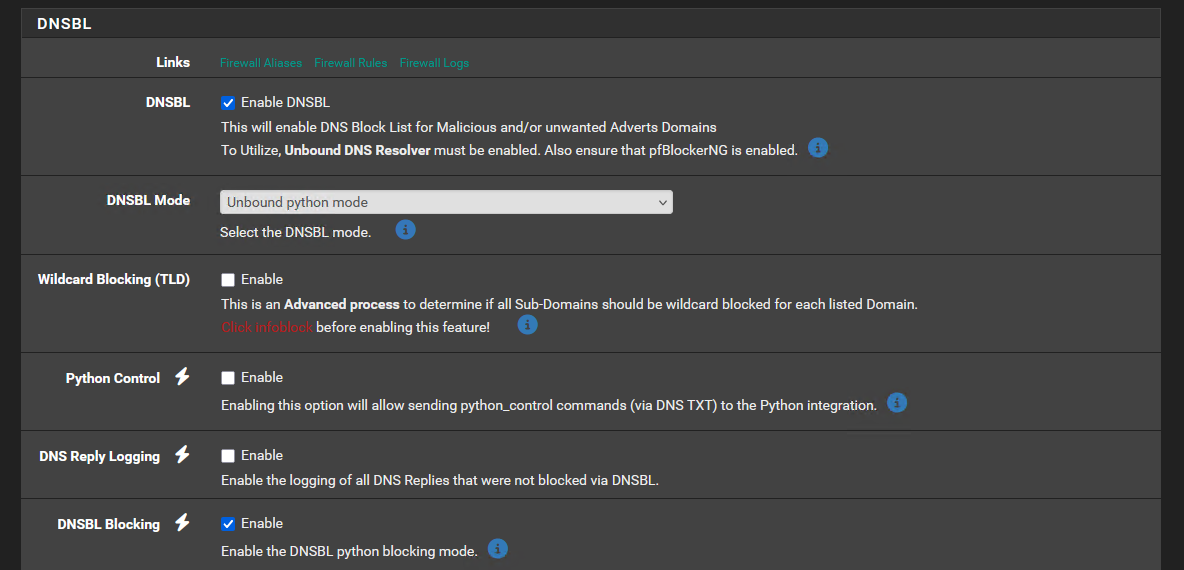
Virtual ip address => 10.102.101.10
Global logging => Null blocking (logging)
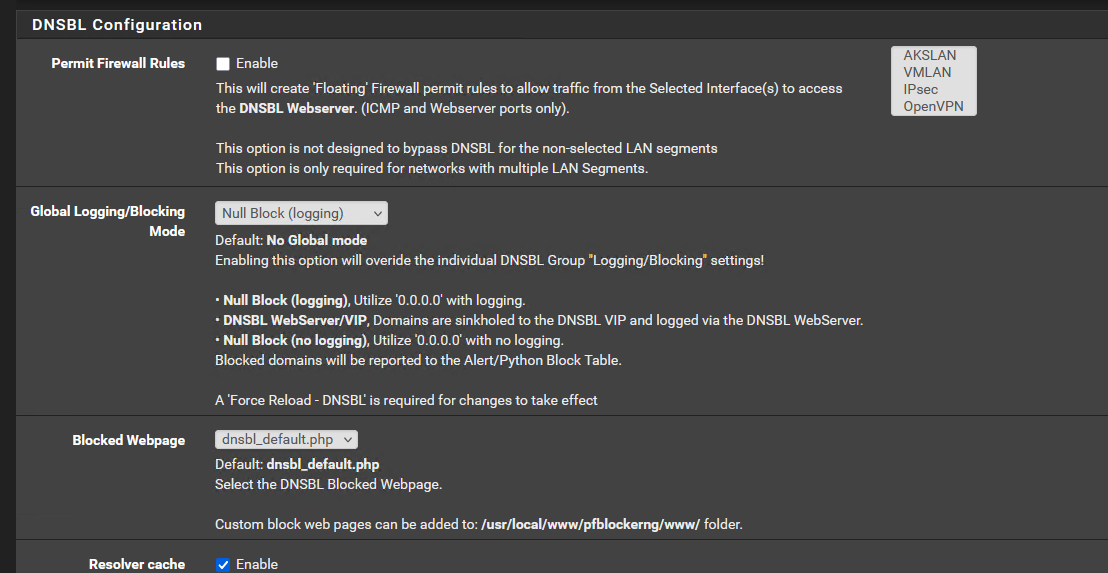
Services are not starting.
When I checked the status of the service, the firewall returned, "does not exist". I tried to find the executable in the directory, but I couldn't except sh file. Manual execution of sh files did neither produce executable nor start the service.
[25.07.1-RELEASE][suser@...]/root: service pfb_filter status pfb_filter does not exist in /etc/rc.d or the local startup directories (/usr/local/etc/rc.d), or is not executable [25.07.1-RELEASE][suser@...]/root: ls /usr/local/etc/rc.d/ choparp dnsmasq isc-dhcrelay6 nginx php_fpm sshguard unbound dbus expiretable kea openvpn radvd strongswan uuidd dhcp6c igmpproxy lighttpd pcscd rrdcached suricata waagent dhcp6relay isc-dhcpd microcode_update pfb_dnsbl.sh rsyncd suricata.sh waagent.sh dhcp6s isc-dhcpd6 miniupnpd pfb_filter.sh scponlyc syslog-ng wireguardd dhcpcd isc-dhcrelay mpd5 pfnet-controller smartd syslog-ng.sh xinetd -
@nanda said in pfb_filter and pfb_dnsbl services are not running Pfsense 25.07.1:
When I checked the status of the service, the firewall returned, "does not exist".
as in on the Status -> Services page? or where specifically ?
and yet it shows on the dashboard services widget..And you said this was a fresh install so ...
are there any errors in pfblockerNG 's error.log, dnsbl_parsed_error or py_error
(Firewall -> pfBlockerNG -> Logson the pfblockerNG -> General.
make sure the Keep Settings option is enabled
then head over to packages and try to reinstall the package (you may remove and install or just reinstall)
see if you spot any install errors during the installthen when complete
you will need to change the masterfile / mastercat line againand then check the update page at
Firewall -> pfBlockerNG -> Updateshould have a status showing the next scheduled cron event (if that is within a few minutes just wait for it to run). if it is more than say 20 minutes away or says not scheduled (or similar) then on the same update screen force Cron hit run.
when that is complete
check the status
then reboot
check the status -
@jrey said
When I checked the status of the service, the firewall returned, "does not exist".
as in on the Status -> Services page? or where specifically ?
and yet it shows on the dashboard services widget..Please see below. I can see .sh files but not executables (suricata & syslog-ng have both).
[25.07.1-RELEASE][suser@...]/root: ls /usr/local/etc/rc.d/ choparp dnsmasq isc-dhcrelay6 nginx php_fpm sshguard unbound dbus expiretable kea openvpn radvd strongswan uuidd dhcp6c igmpproxy lighttpd pcscd rrdcached suricata waagent dhcp6relay isc-dhcpd microcode_update pfb_dnsbl.sh rsyncd suricata.sh waagent.sh dhcp6s isc-dhcpd6 miniupnpd pfb_filter.sh scponlyc syslog-ng wireguardd dhcpcd isc-dhcrelay mpd5 pfnet-controller smartd syslog-ng.sh xinetdare there any errors in pfblockerNG 's error.log, dnsbl_parsed_error or py_error
(Firewall -> pfBlockerNG -> Logserror.log contains a few lines on feeds failed to fetch entires
py_error is empty
dnsbl_parsed_error (see below) did not have any errors that prevent service execution... 19:00:44,StevenBlack_ADs,ip6-loopback,::1 ip6-loopback ... 19:14:40,StevenBlack_ADs,ip6-loopback,::1 ip6-loopback ... 19:14:46,EasyList,admi2fib4exit,||admi2fib4exit^ ... 00:01:20,EasyList,admi2fib4exit,||admi2fib4exit^ ... 00:01:09,EasyList,admi2fib4exit,||admi2fib4exit^ ... 16:50:29,UT1_adult,xxx,xxxKeep settings is enabled, package uninstalled and reinstalled, code changed, feed updated and finally system rebooted. No change in the service status in dashboard's service widget.
I found that except log (e.g., block, permit), the other functions are working. So, I will stop digging further on this regard and hope that future firewall upgrade will solve it. I need to identify, segregate and transfer logs to SIEM, which won't be a hassle.
Thank you very much for your assistance.
With appreciation
Nanda, D.Sc. (Tech.) -
@nanda said in pfb_filter and pfb_dnsbl services are not running Pfsense 25.07.1:
I can see .sh files but not executables
those pfb_*.sh files are the executables
looking at the errors (suggests some of the lists you are using) you might want to look for these lines in the pfblockerng.log especially if you are on smaller hardware (like an 1100) you may just have to be more selective on your list selection (smaller lists)
pfSense Table Stats ------------------- table-entries hard limit 600000 Table Usage Count 161557You likely have the default values set, (which might be too small)
then the idea here is to have the Total Usage Count < (Hard Limit / 2)If you need adjustment will find the setting for the hard limit on
System -> Advanced / Firewall & NAT -> (in the section Packet Processing) (on 25.07.1)the comment there reads:
Maximum number of table entries for systems such as aliases, sshguard, snort, etc, combined. Note: Leave this blank for the default. -
those pfb_*.sh files are the executables
Thanks for clarifying the executables.
I do not think that the hardware and table entry size won't be problem as the current configuration provides sufficient computation and memory for its operations. Pfsense is running in different hardware, e.g., Intel Xenon Platinum 8272CL processor and maximum table entries is set to 10 times than the default.
pfSense Table Stats ------------------- table-entries hard limit 4000000 Table Usage Count 465931