No Internet access with VLAN via OPT1
-
@jogovogo is the mask correct on the client/in DHCP settings?
-
@jogovogo said in No Internet access with VLAN via OPT1:
But why do I get an IP address from the dhcp for Opt1?
I'll add that behavior to the "VLAN switch isn't setup correctly" list.
The initial client initiated DHCP traffic is "broadcast" (probably not related).
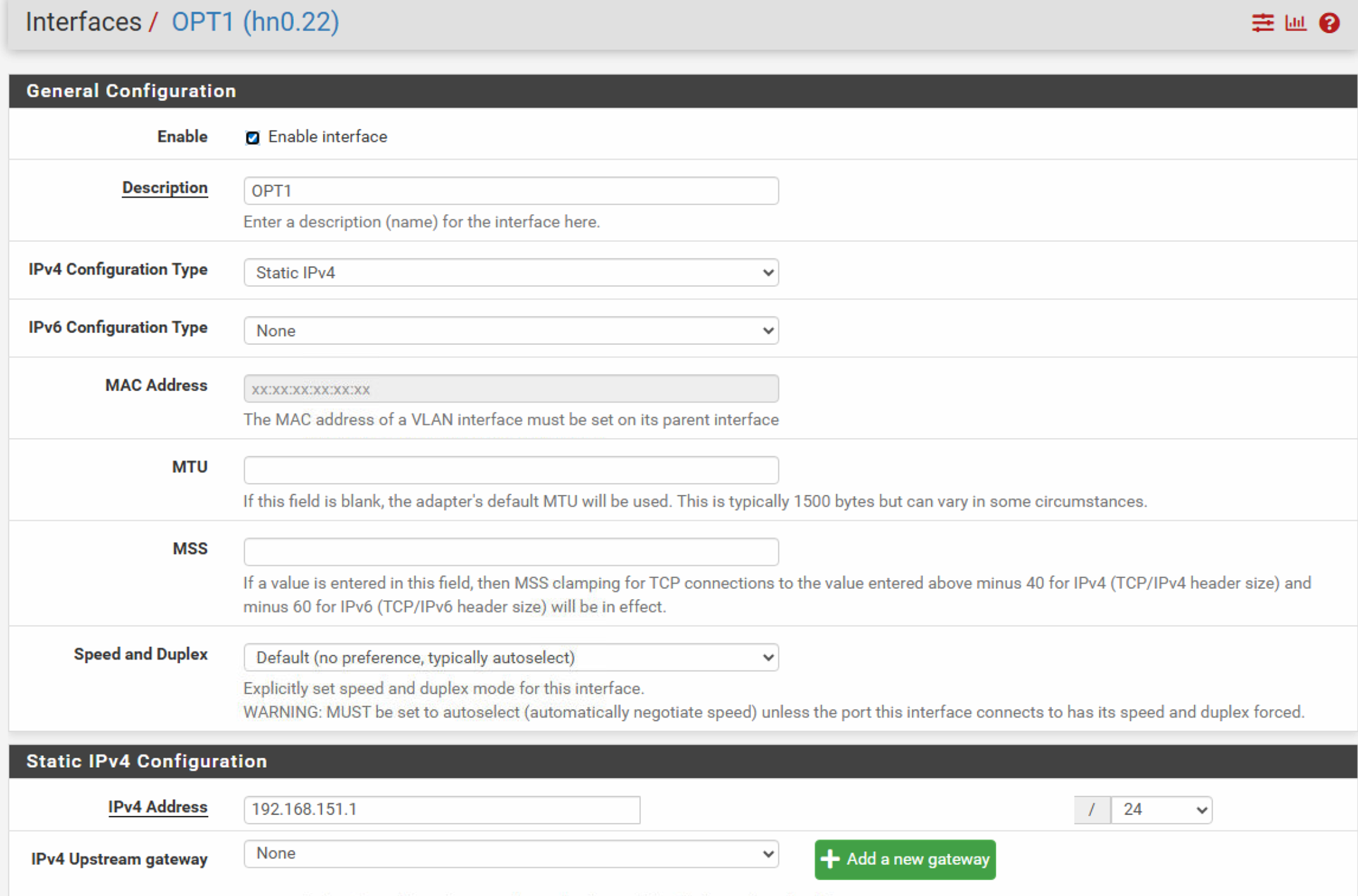
You have activated the DHCP server on OPT1 ?
On the OPT1 connected device shown above, you can
(windows example) :ipconfig /releaseand
ipconfig /renew?
-
Hello, that works automatically. I've already made it so that it receives an address from the DHCP area right away after the release.
This is the case with two different machines.
-
@jogovogo said in No Internet access with VLAN via OPT1:
Hello, that works automatically ....
That's what you want to happen.
Never ever believe the "system". As the network admin, at all times, fact check everything
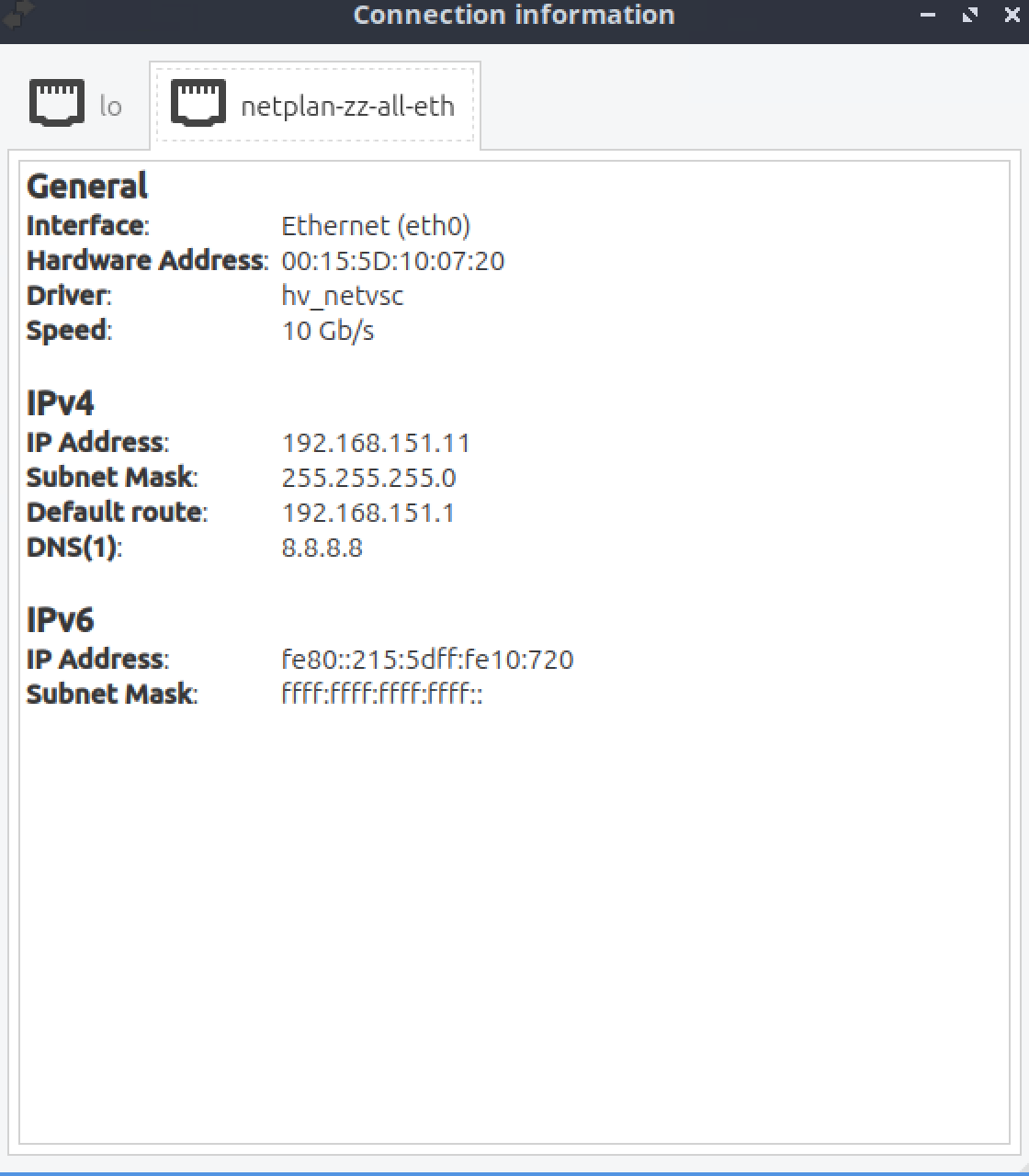
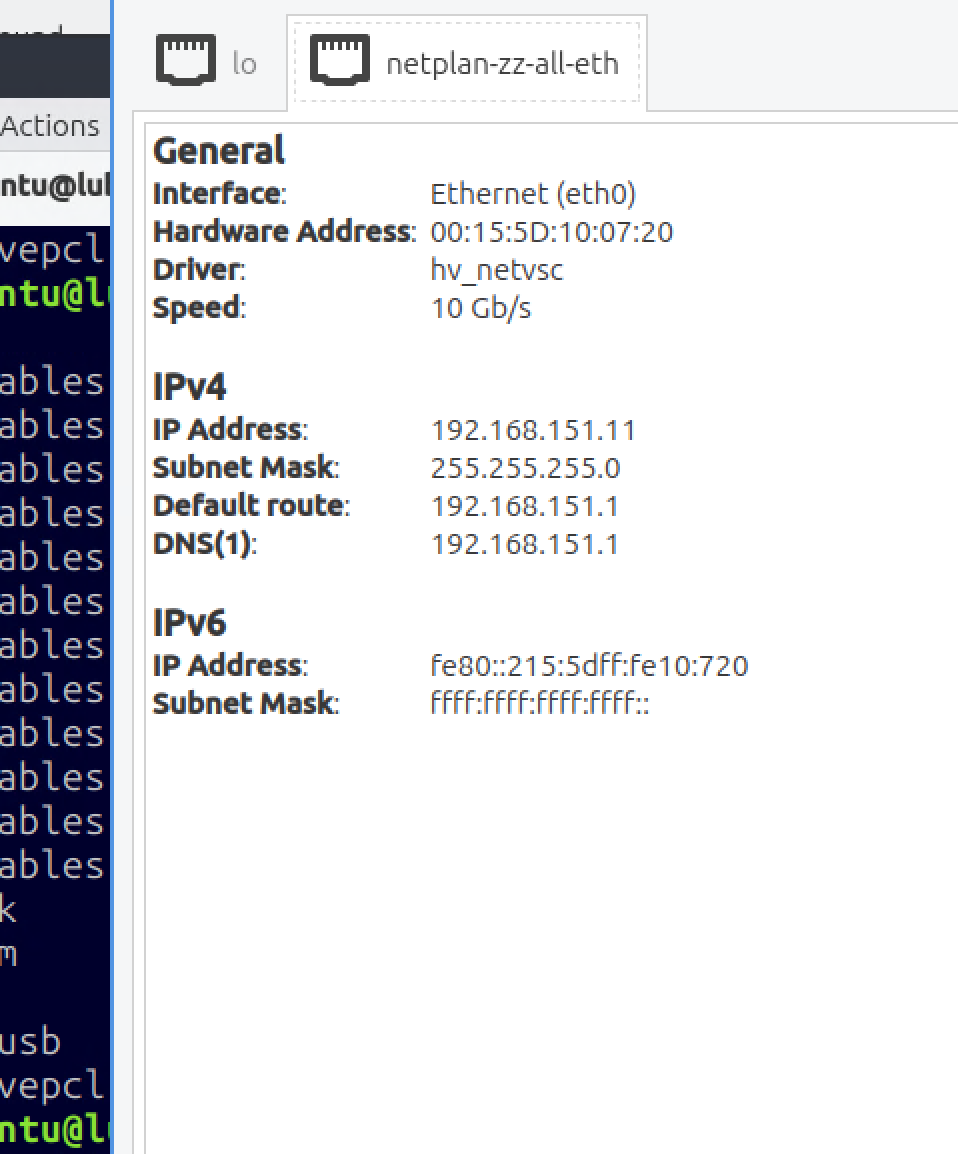
For example, red flags were already shown : The IP (192.168.151.11) looks ok. Mask and gateway also. But the 8.8.8.8 DNS is a fail.
So, my thoughts : some one set them up statically ? Or entered 'strange' settings in the DHCP server ? -
The 8.8.8.8 is only for testing; even if I use the machine to set the IP and as a DNS and gate, the 192.168.151.1 does not work.
-
My first surprise is that I'm now on the firewall, but why?
But still no access to the Internet...
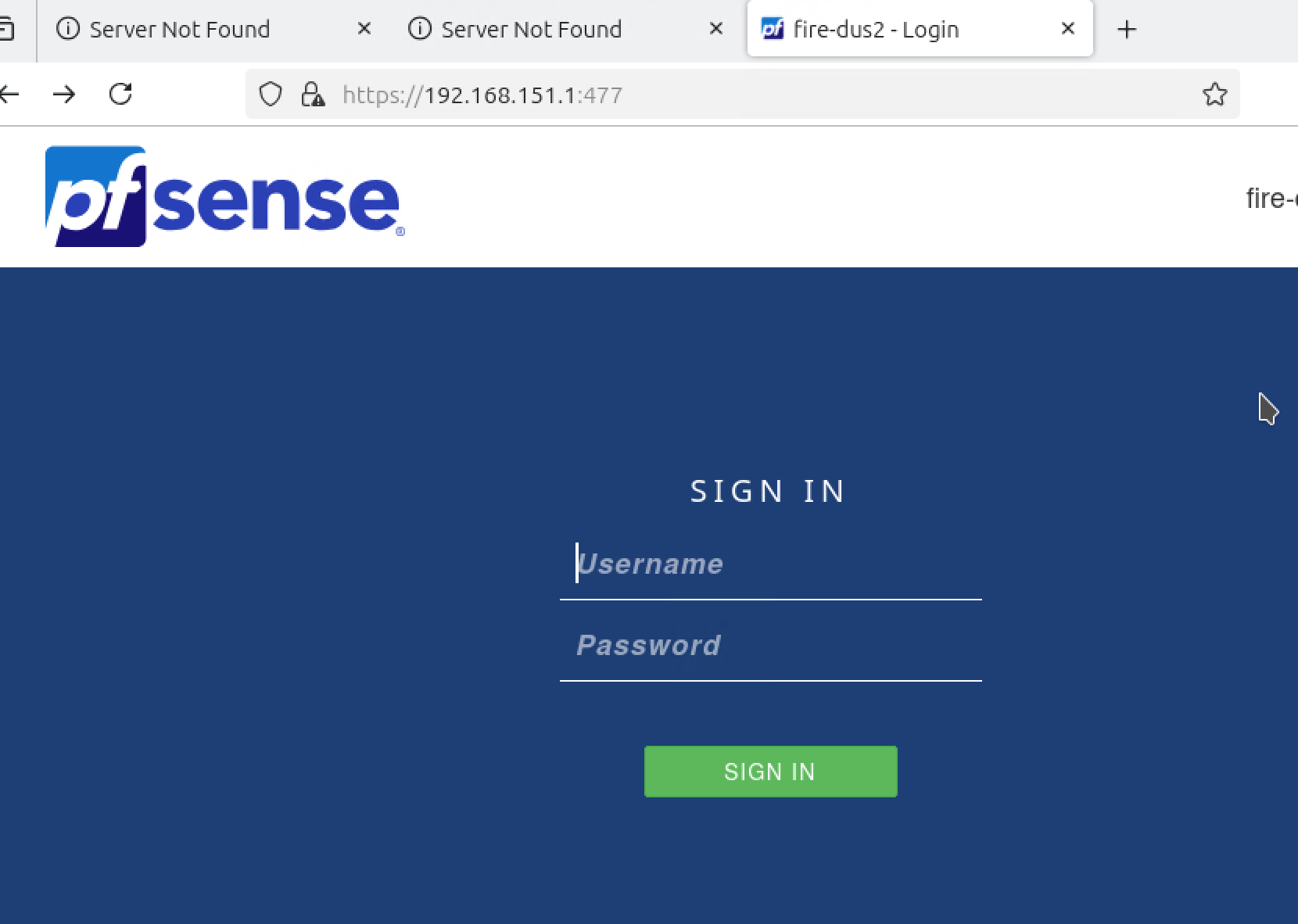
-
Hello again!
The issue has been resolved, simply, by restarting the DNS resolver.
I just had another one, though; perhaps you could also respond to it?
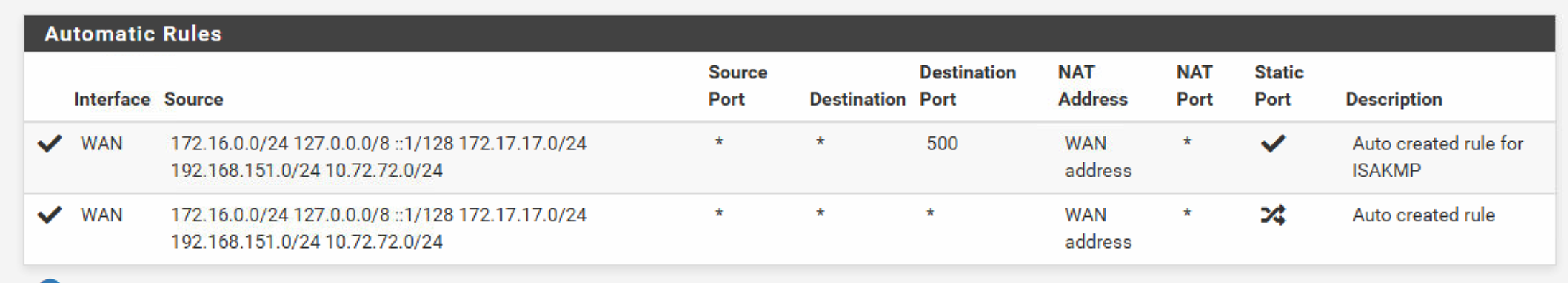
NAT and VLAN
The port 2413 should be seen on 192.168.151.10. The corresponding rule is created automatically. Unfortunately, it does not function.
The "LAN " operates it without any intervention.


-
@jogovogo said in No Internet access with VLAN via OPT1:
restarting the DNS resolver
but:
ping on the address 192.168.151.1 also fails
...is not related to DNS.
In any case restarting DNS is necessary if a new interface has been added, because unbound didn't know about that IP when it started.
re: NAT, often the firewall on the server isn't set to allow traffic from any IP, only the local subnet or RFC1918.
https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat-port-forwards.html may help. -
Hello, many thanks for your prompt response!
Indeed, ping has nothing to do with DNS.
I didn't notice it because I didn't even attempt it on one machine.This is working now as well. We used pfBlockerNG, and the opt1 still needed to be defined in the Outbound Firewall Rules. Then once update via cron and now it works!
cheers
ron -
@jogovogo said in No Internet access with VLAN via OPT1:
My first surprise is that I'm now on the firewall, but why?
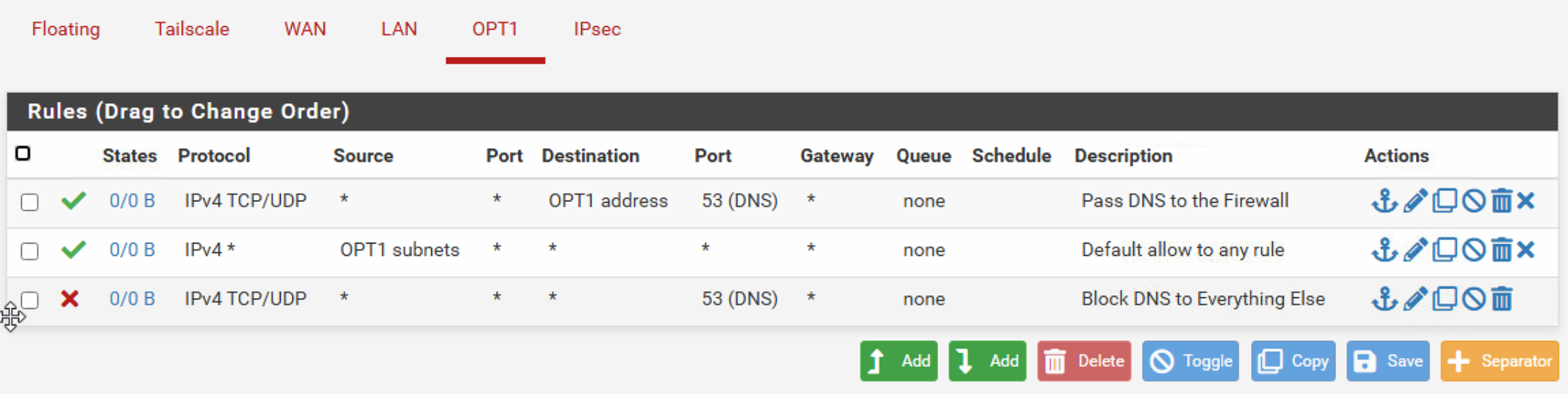
The web server that serves the pfSense GUI runs on all assigned interfaces.
When you installed pfSense, there was a pass rule for incoming traffic on the initial LAN interface : it accepts all traffic.
When you add more LAN type interfaces, the ones called OPTx, there will be no inital rules, so you can't access anything.
DHCP will work as pfSense will add hidden DHCP (UDP port 67 and 68) rules, but nothing else (no http https dns icmp etc etc etc etc).
When you add a pas rules for TCP, UDP, etc, things "start to work".When you use addresses like this :
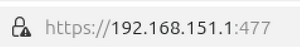
you use IP addresses.
So, even is DNS is not working, then that won't be an issue.
Your browser doesn't need to use use DNS (for translating host names to IP addresses) as you already gave an IP. It can contact the device 192.168.151.1 right away.
You've allowed TCP IPv4 traffic to port 477, which is apparently your changed your pfSense https web GUI interface port.@jogovogo said in No Internet access with VLAN via OPT1:
The issue has been resolved, simply, by restarting the DNS resolver.
Euh ......
As you've changed lost of things at the same moment, it's hard to tell why dns (== the resolver) didn't work initially.
Normally, when you add an new interface like your OPT1 interface, system processes like DNS (the resolver) gets restarted.
The resolver will listen to All Interfaces :
by default so it would work right away on the new OPT interface.
Again, you still have to add a firewall rule to allow DNS traffic to reach the pfSense DNS port 53 of course.