Dual-WAN access configuration
-
OVPN newbie here. I'm trying to configure my dual-WAN Netgate 3100 for access from outside on both WANs.
Using the wizard, I've successfully configured one service connection on WAN. But I can't get the second service to work on OPT1.
The docs say:
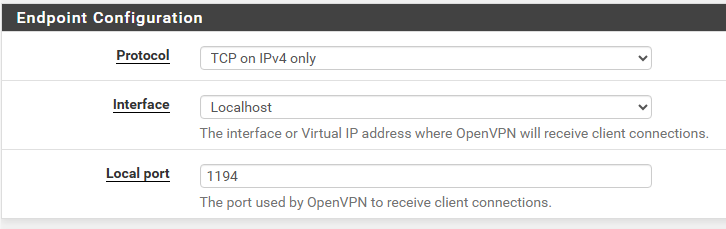
"Local port
The port number upon which OpenVPN will listen for incoming connections from peers. Firewall rules must allow traffic to this port and this port must be specified in the client configuration.The port for each server must be unique for each interface when using a standard UDP or TCP Protocol choice and must be globally unique if using a multihome Protocol."
My working OVPN server on WAN is using port 1194. Since the docs say "the port for each server must be unique" I've set the OPT1 server to use port 1195.
Per the docs I'm trying to set a firewall rule to allow traffic on port 1195. However, the firewall rule dropdown menu doesn't present a choice for port 1195 - only 1194.
Is there some place where I am supposed to configure port 1195 to be available in the dropdown? Or is there something I misunderstand in the configuration?
Thanks in advance!
-
@chitchat
My two cents:Configure openvpn to tisten on localhost.
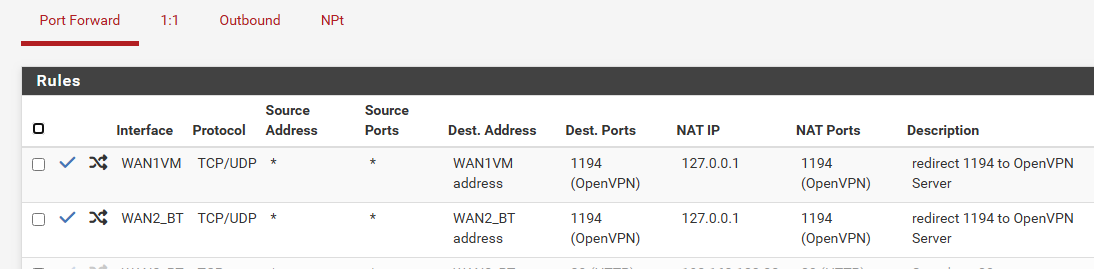
Create a portforward in both WANs, from the Internet (any), to 127.0.0.1 port 1194 UDP.
Use DDNS or configure two remote entries in the .ovpn, with a timeout of 2 seconds. -
Other. 1195.. however if this is for failover when you should use 1194 on that interface as well..
The solution provided above seems interesting..
If you are truly looking for multiple VPN instances then yes you do need to use a different port.
-
I configured both servers to listen on 1194 - that worked!
My newbie skills do not understand how that should work. I would have thought that the two servers would trip over themselves trying to listen to the same port.
Here's a related question - I'm trying to troubleshoot why I can't sucessfully connect via OpenVPN connect with my mobile phone over a certain cellular carrier. One carrier works, another doesn't.
A suggestion was made that one carrier might be blocking UDP, so to set the OVPN server to use TCP instead (I know this is frowned upon for performance reasons).
Can I set one OVPN server to use UDP and another OVPN server to use TCP, both listening on port 1194? Is that viable?
Right now I'm remote, and the only access I have to the Netgate router is via the current OVPN setup. I'm afraid of borking things up and getting myself locked out by doing seemingly screwy like the above.
Thanks.
-
@chitchat said in Dual-WAN access configuration:
Can I set one OVPN server to use UDP and another OVPN server to use TCP, both listening on port 1194? Is that viable
Yes, of course.
-
The suggestion above by @mcury is the easiest method. It also means routes configured for VPN clients still apply regardless of which WAN they connect via.
In the .ovpn client file, you simply have two remote entries:
remote [WAN-1 Public IP Address] 1194 udp4
remote [WAN-2 Public IP Address] 1194 udp4Pete
-
@pwood999 As I said, I'm a newbie with OVPN, and I'm too sqeamish to try the @mcury solution without understanding what I'm doing, and GUI screenshots. Especially while I'm remote and could screw something up and get myself locked out.
As to your suggestion, first, thanks for that! But as I described it, one of the OVPN servers will be configured as accepting TCP and one UDP. So in the lines you were suggesting for the .ovpn file, shouldn't one of those servers show "TCP" (or is it "TCP4"?).
So more like:
remote [WAN-1 Public IP Address] 1194 tcp4
remote [WAN-2 Public IP Address] 1194 udp4Do the above entries work even if I'm not doing the @mcury thing? Right now, I have two different .ovpn client files - that's how the GUI menu does it - one for each WAN, depending upon which one I try to attach to.
Thanks.
-
@chitchat
It is tcp4 and udp4Works for any configuration too
-
@chitchat Assuming the two VPN servers use all the same certs then it should be ok.
In my case the single VPN server listens on Localhost. Then there's two port-forwards (one for each WAN) to the same VPN server.