Having trouble accessing NAS through VPN server
-
Here is a packet capture of a successful connection when the iPad is on the home network.
4 3.716247 10.10.250.243 192.168.200.4 TCP 78 55639 → 445 [SYN] Seq=0 Win=65535 Len=0 MSS=1460 WS=32 TSval=143854129 TSecr=0 SACK_PERM 5 3.733679 10.10.250.243 192.168.200.4 TCP 66 55639 → 445 [ACK] Seq=1 Ack=1 Win=131744 Len=0 TSval=143854153 TSecr=1190980799 6 3.733776 10.10.250.243 192.168.200.4 SMB 139 Session message; Negotiate Protocol 7 3.747014 10.10.250.243 192.168.200.4 TCP 66 55639 → 445 [ACK] Seq=74 Ack=207 Win=131552 Len=0 TSval=143854166 TSecr=1190980827 8 3.747738 10.10.250.243 192.168.200.4 SMB2 178 Negotiate Protocol Request 9 3.752455 10.10.250.243 192.168.200.4 TCP 66 55639 → 445 [ACK] Seq=186 Ack=413 Win=131328 Len=0 TSval=143854172 TSecr=1190980831iPad IP is 10.10.250.243
From my limited understanding of how this works, it appears that the iPad is not receiving the SYN-ACK from the NAS when I tunnel through the VPN..
-
Anyone have a suggestion for troubleshooting?
So when I try to ping the NAS from my iPhone while using the VPN tunnel, I see the traffic pass the firewall but the ping fails. Not sure what to try next...
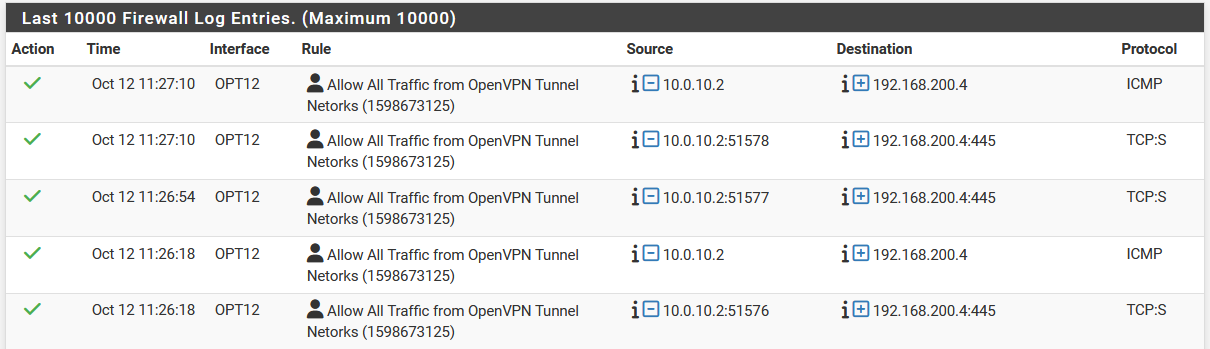
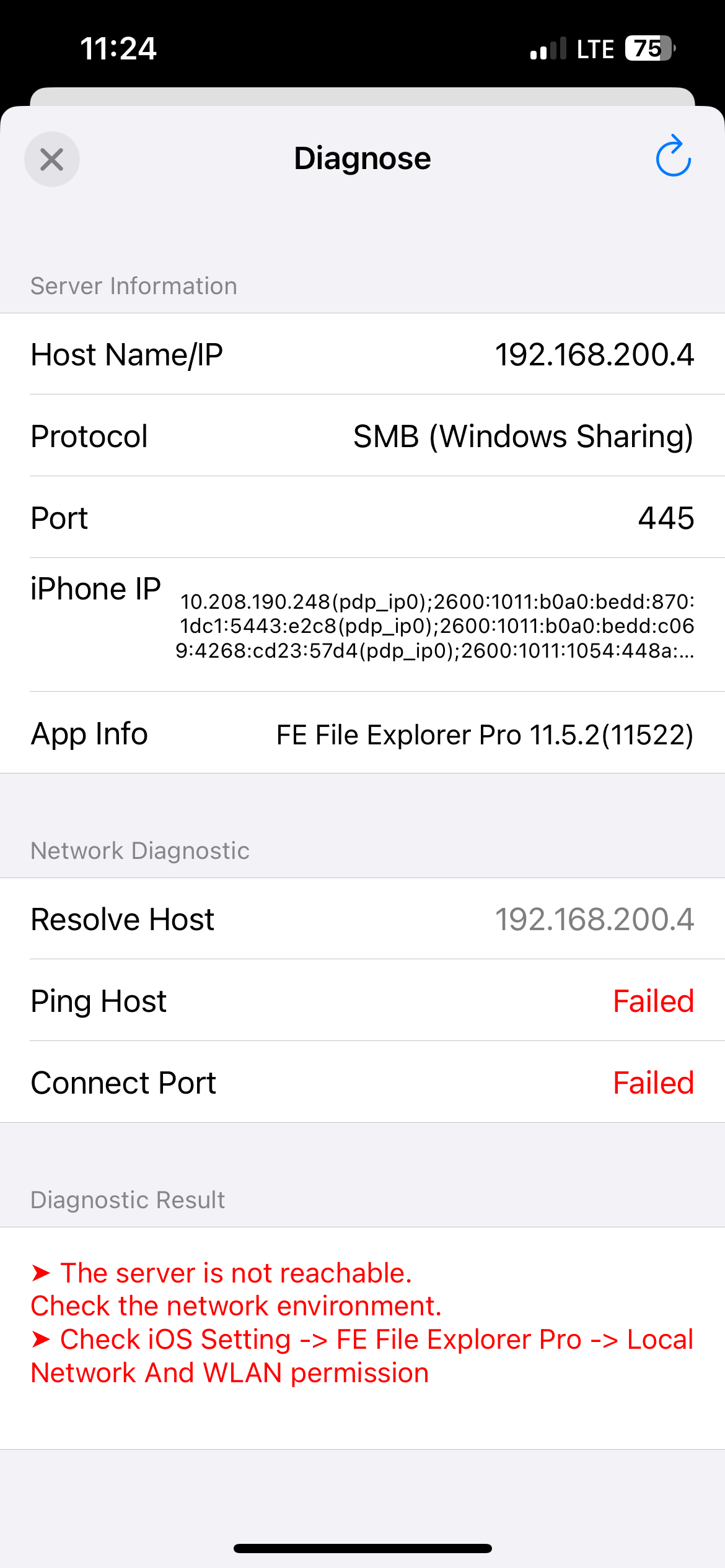
I have two VPN servers. OPT11 uses TCP and assigns local devices an address in the 10.0.20.0/24 network space. OPT12 is UDP and uses 10.0.10.0/24. THe iPhone in this attempt was 10.0.10.2.
-
@azdeltawye dies the firewall on the NAS allow connections from the VPN device IP?
-
@SteveITS
Thanks for the reply. I disabled the firewall on the NAS and still get the same result. -
@azdeltawye hey there,
please post a screenshot of your firewall rule for your openVPN interface in use (rules > Interface), not just the log entry.
What kind of internet access do you have (dual stack, dual stack lite / cgnat, IPv4 / 6 only)?don't know about iphones...so, just heard that they offer all kinds of stuff androids don't regarding network configs. Might want to take a look there as well (or try, if possible) with an android / linux / windows client).
Can you ping your public IP (from outside your LAN)? Or better yet your DynDNS address? Does that work at all (first step)? -
Does the NAS have a route back through the VPN ? If it's default route is PfSense, then it should work ?
Had something similar a while back on our work lab VPN. Some LAN devices would respond ok, but others needed a static route added to enable remote access via the VPN. Never figured out why, but the extra route solved it.
-
@the-other
I’m on travel for the week so I’ll post the firewall rules when I get home.As for my internet, I have Comcast Xfinity with a publicly routeable address. Comcast offers ipv6 support but I only have ipv4 enabled. I use a DDNS service for remote access because my IP changes from time to time..
I cannot ping my IP when I am remote. I don’t recall if I have a ICMP block rule on my WAN. I’ll check that as well when I get home.Thanks for the suggestions.
-
@pwood999
No static routes are in place, just the default settings in pfsense. -
@azdeltawye yeah, but can you ping your dyndns address? That should also give you your actual public IP...can you ping that one?
-
@the-other
No, I cannot ping my ddns url. It resolves my WAN IP but times out on the ping attempt. -
@azdeltawye do you have a firewall rule on WAN allowing ICMP?
-
@SteveITS
I do not have a rule to pass ICMP traffic in the WAN interface.I’ll have to wait until I get home before I add a rule. Editing firewall rules via remote iPhone connection is sketchy at best…
-
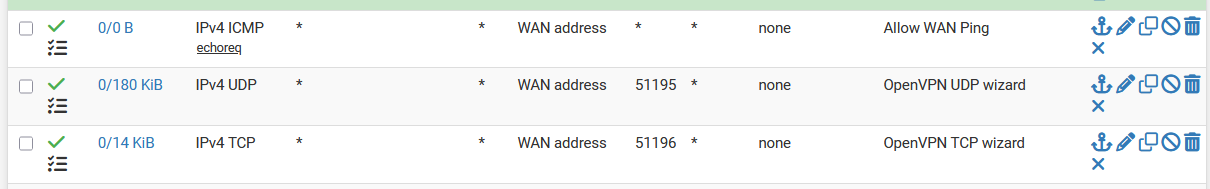
@SteveITS
OK, added an Echo Request rule on the WAN to allow ICMP traffic. I can now ping my IP directly and the DDNS URL. However, I still cannot access the NAS with File Explorer.Here are my WAN pass rules:
-
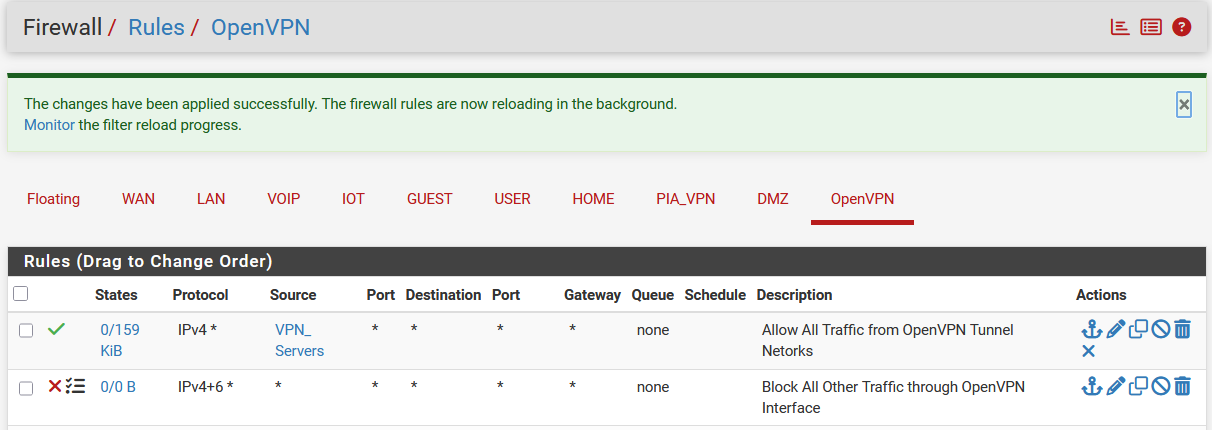
@the-other
Here are all the active OpenVPN interface rules:
The VPN Servers Alias is this:

-
What is your pfSense LAN IP, and network ?
Like 192.168.1.1 and 255.255.255.0 or /24 ?Your NAS IP, network, gateway and DNS ?
Like 192.168.1.x, 255.255.255.0/24 or /24, 192.168.1.1 (gateway !) and 192.168.1.1 (DNS) ? -
@Gertjan
My pfSense IP is 192.168.125.1 on a /24 network
My NAS IP is 192.168.200.4 on a /24 network, the GW and DNS are 192.168.200.1
My OpenVPN server tunnel networks are 10.0.10.0/24 & 10.0.20.0/24Like I mentioned in the first post in this thread, this used to work. I think it was around 2 years ago, I could access my NAS via the File Explorer app on my iPhone while logged into my OpenVPN server over a remote connection. So I'm not sure exactly when it broke. Since then, there have been several iOS updates, FE app updates, DSM updates and OpenVPN updates. My pfSense configuration, for the most part, has not changed.
BTW, I disabled the allow ping rule on my WAN after getting spammed by ping bots...
-
Your NAS will send reply traffic to its gateway : 192.168.200.1
Or, it local network segment gataway is 192.168.125.1/24
Afaik, this can't work.See it like this : traffic arrives from the "10.0.10.0/24 or 10.0.20.0/24" network and s to go the the 192.168.125.1/24 network to reach the NAS.
Only 192.168.200.0/24 is known to pfSense .... that's like the post office receiving a letter mentioning a road that doesn't exist in its city. -
@Gertjan
I hear what you're saying but I don't think that is correct in this situation. I thought PfSense automatically adds VLAN subnets to its routing table when the VLANs are created. And since I have the 'allow all' rule on my VPN server interface, I can ping and access all my VLAN gateways, including the 200 VLAN gateway which is where the NAS lives, when I tunnel into my VPN server.Anecdotally, I have a security camera NVR on my 175 VLAN (192.168.175.0/24) which I have no problem accessing when I tunnel into my VPN server from a remote location. No special entries in the routing table to allow this connection, it just works.
And like I mentioned before, this did actually work some years ago. I was able to access the NAS with the FE application from my iOS device over the VPN. Something changed, other than my pfSense configuration that is preventing access now...
-
@azdeltawye said in Having trouble accessing NAS through VPN server:
I thought PfSense automatically adds VLAN subnets
Where did VLANs come from ?
So you do have a 192.168.200.1/24 interface ? (LAN, or VLAN doesn't matter, as long as it is set up correctly).VLAN need a setup on the pfSense side, and on the smart 'VLAN capable side' switch side.
-
@Gertjan said in Having trouble accessing NAS through VPN server:
Where did VLANs come from ?
huh??
I configured them when I designed the network years ago... You can see the different interfaces of my network from the screenshot on post #16. Here is a summary of how the network segments are defined: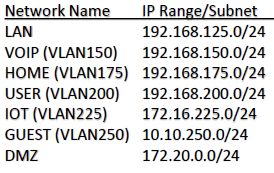
Yes, all the layer 2 switches and APs are capable of VLAN tagging...
So when I log into my VPN server with my iPhone from a remote location, I am able to ping random devices on every VLAN listed above in my network. However, I cannot ping the Synology NAS (192.168.200.4). But, I am able to ping my backup 'NAS' (192.168.200.5). My backup 'NAS' is just an old Asus RT-AC86 router with a Samba SSD plugged into the USB port. I cannot access either NAS from the File Explorer app on my iphone.
Now when I am at home and my iPhone is on the 200 VLAN network, I can ping and access both NAS devices with the File Explorer app.