Squid make sure to set “email_err_data off”
-
Just learned about this bug there is a patch and there is a work around.
This was sent out from Amos Jeffries on the Squid email system. If you are not part of it here it is.
Credits:
This vulnerability was discovered by Leonardo Giovannini of
Doyensec.Fixed by Amos Jeffries of Treehouse Networks Ltd.
Squid Proxy Cache Security Update Advisory SQUID-2025:2
Advisory ID: | SQUID-2025:2
Date: | Oct 15, 2025
Summary: | Information Disclosure in Error handling.
Affected versions: | Squid 3.x -> 3.5.28
| Squid 4.x -> 4.17
| Squid 5.x -> 5.9
| Squid 6.x -> 6.14
| Squid 7.x -> 7.1
Fixed in version: | Squid 7.2
Problem Description:
Due to a failure to redact HTTP Authentication credentials
Squid is vulnerable to an Information Disclosure attack.
Severity:
This problem allows a script to bypass Browser security
protections and learn the credentials a trusted client uses to
authenticate.This problem potentially allows a remote client to identify
security tokens or credentials used internally by a web
application using Squid for backend load balancing.These attacks do not require Squid to be configured with HTTP
Authentication.
Updated Packages:
This bug is fixed by Squid version 7.2.
In addition, patches addressing this problem for the stable
releases can be found in our patch archives:Squid 7:
https://github.com/squid-cache/squid/commit/0951a0681011dfca3d78c84fd7f1e19c78a4443fIf you are using a prepackaged version of Squid then please
refer to the package vendor for availability information on
updated packages.
Determining if your version is vulnerable:
The following test can be used to determine if your Squid has
a vulnerable configuration:squid -k parse 2>&1 | grep "email_err_data"
All Squid with
email_err_data offare not vulnerable.All Squid up to and including 7.1 with
email_err_data on
are vulnerable.All Squid up to and including 7.1 without
email_err_data
are vulnerable.
Workaround:
Disable debug information in administrator mailto links
generated by Squid. By configuring squid.conf with:email_err_data off
Contact details for the Squid project:
-
Set this inside of custom options like
Example:
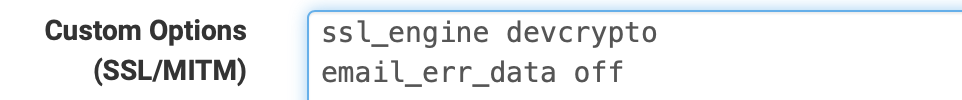
(ignore ssl_engine)After run Squid -k parse and you should see this within the tests if you have no errors and it moves to the next time you have the work around.
2025/10/17 07:02:07| Processing: ssl_engine devcrypto 2025/10/17 07:02:07| Processing: email_err_data off -
 G Gertjan referenced this topic
G Gertjan referenced this topic