Having trouble accessing NAS through VPN server
-
What is your pfSense LAN IP, and network ?
Like 192.168.1.1 and 255.255.255.0 or /24 ?Your NAS IP, network, gateway and DNS ?
Like 192.168.1.x, 255.255.255.0/24 or /24, 192.168.1.1 (gateway !) and 192.168.1.1 (DNS) ? -
@Gertjan
My pfSense IP is 192.168.125.1 on a /24 network
My NAS IP is 192.168.200.4 on a /24 network, the GW and DNS are 192.168.200.1
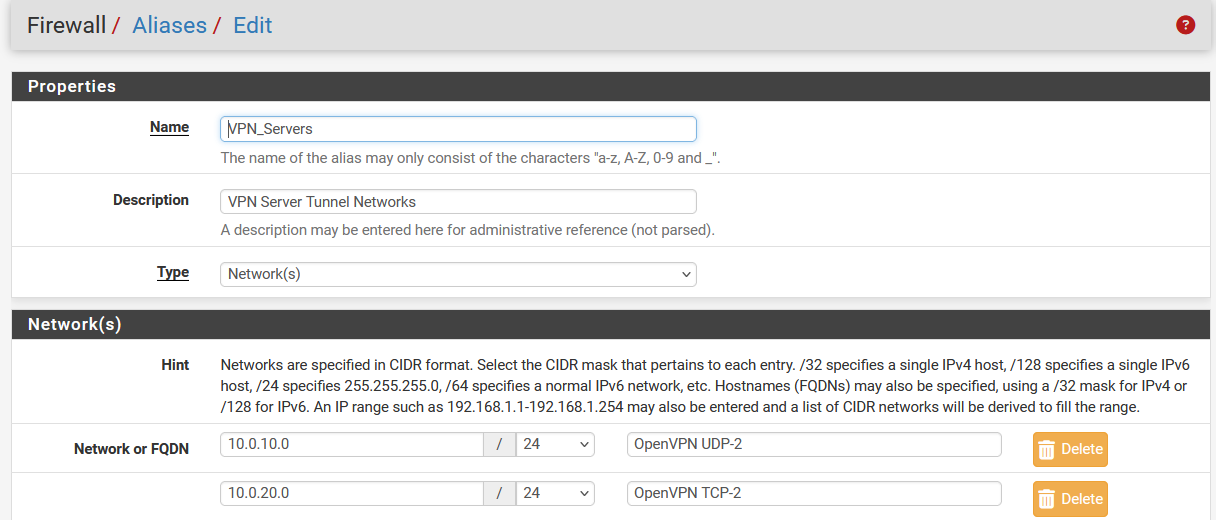
My OpenVPN server tunnel networks are 10.0.10.0/24 & 10.0.20.0/24Like I mentioned in the first post in this thread, this used to work. I think it was around 2 years ago, I could access my NAS via the File Explorer app on my iPhone while logged into my OpenVPN server over a remote connection. So I'm not sure exactly when it broke. Since then, there have been several iOS updates, FE app updates, DSM updates and OpenVPN updates. My pfSense configuration, for the most part, has not changed.
BTW, I disabled the allow ping rule on my WAN after getting spammed by ping bots...
-
Your NAS will send reply traffic to its gateway : 192.168.200.1
Or, it local network segment gataway is 192.168.125.1/24
Afaik, this can't work.See it like this : traffic arrives from the "10.0.10.0/24 or 10.0.20.0/24" network and s to go the the 192.168.125.1/24 network to reach the NAS.
Only 192.168.200.0/24 is known to pfSense .... that's like the post office receiving a letter mentioning a road that doesn't exist in its city. -
@Gertjan
I hear what you're saying but I don't think that is correct in this situation. I thought PfSense automatically adds VLAN subnets to its routing table when the VLANs are created. And since I have the 'allow all' rule on my VPN server interface, I can ping and access all my VLAN gateways, including the 200 VLAN gateway which is where the NAS lives, when I tunnel into my VPN server.Anecdotally, I have a security camera NVR on my 175 VLAN (192.168.175.0/24) which I have no problem accessing when I tunnel into my VPN server from a remote location. No special entries in the routing table to allow this connection, it just works.
And like I mentioned before, this did actually work some years ago. I was able to access the NAS with the FE application from my iOS device over the VPN. Something changed, other than my pfSense configuration that is preventing access now...
-
@azdeltawye said in Having trouble accessing NAS through VPN server:
I thought PfSense automatically adds VLAN subnets
Where did VLANs come from ?
So you do have a 192.168.200.1/24 interface ? (LAN, or VLAN doesn't matter, as long as it is set up correctly).VLAN need a setup on the pfSense side, and on the smart 'VLAN capable side' switch side.
-
@Gertjan said in Having trouble accessing NAS through VPN server:
Where did VLANs come from ?
huh??
I configured them when I designed the network years ago... You can see the different interfaces of my network from the screenshot on post #16. Here is a summary of how the network segments are defined: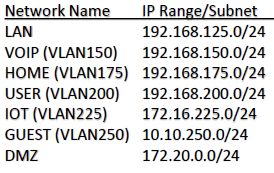
Yes, all the layer 2 switches and APs are capable of VLAN tagging...
So when I log into my VPN server with my iPhone from a remote location, I am able to ping random devices on every VLAN listed above in my network. However, I cannot ping the Synology NAS (192.168.200.4). But, I am able to ping my backup 'NAS' (192.168.200.5). My backup 'NAS' is just an old Asus RT-AC86 router with a Samba SSD plugged into the USB port. I cannot access either NAS from the File Explorer app on my iphone.
Now when I am at home and my iPhone is on the 200 VLAN network, I can ping and access both NAS devices with the File Explorer app.
-
@azdeltawye said in Having trouble accessing NAS through VPN server:
huh??
Don't worry. I thought you had a single pfSense LAN, 192.168.125.0/24 and a NAS using 192.168.200.4 on that LAN.
That will fail of course.
But solved now : you have more then one LAN ^^ Your NAS lives on the LAN called 'HOME' :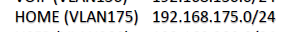
Check that :
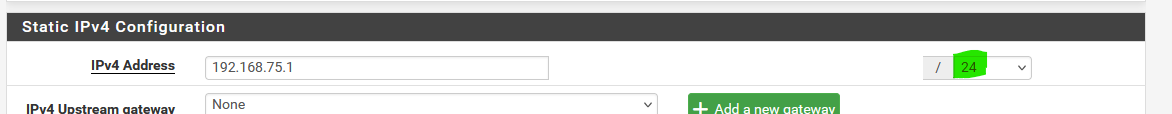
has been set to /24.
Check that your OpenVPN interface firewall says :
Btw : You've two of them : 10.0.20.0/24 and 10.0.10.0/24.
About :
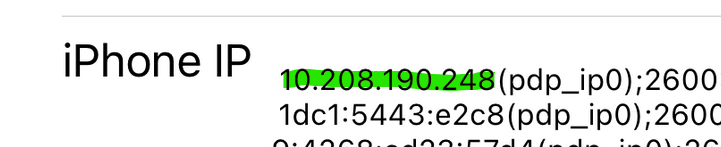
I would presume that your iPad would have a 10.0.10.0/24 or 10.0.20.0/24 IP when connected to the VPN, not this 10.208.190.248 IP (where did that came from ?)
-
@Gertjan
Actually, the NAS's live on the USER .200 network.
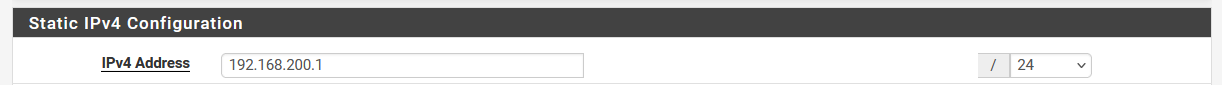
Yes, it is a /24.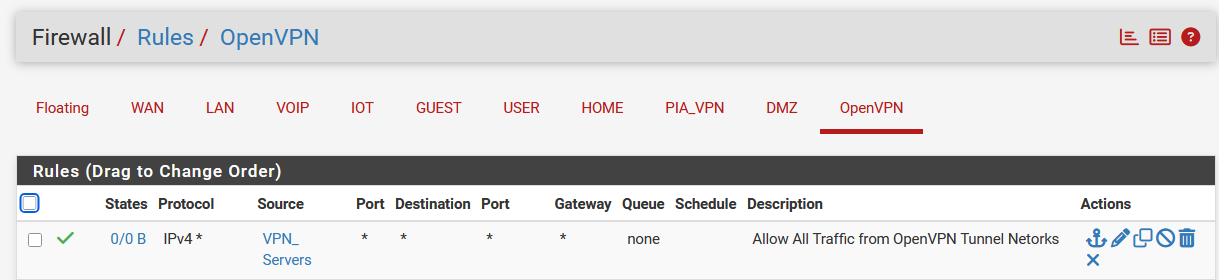
Yeah, I have the OpenVPN server subnets rule to allow all traffic.What advanced settings do you have in your VPN interface rule? I see a gear symbol next to the pass check mark. Is that something that may help?
That private address assigned to my iPhone (10.208.190.248) is puzzling. It appears to be a Verizon thing. If I go to Starbucks and jump on their WiFi, or work, it shows the same address.. Just for kicks, I put that IP in the VPN interface rule shown above but that had no effect. My iPad does not have any of that since it has no SIM card.
-
@azdeltawye said in Having trouble accessing NAS through VPN server:
What advanced settings do you have in your VPN interface rule?
Just the "Allow IP options" set :
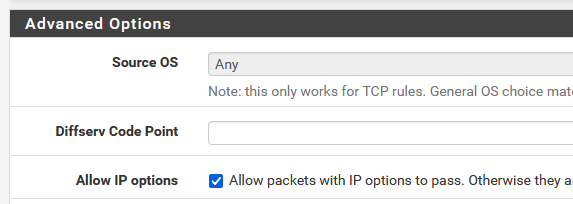
Probably not needed.
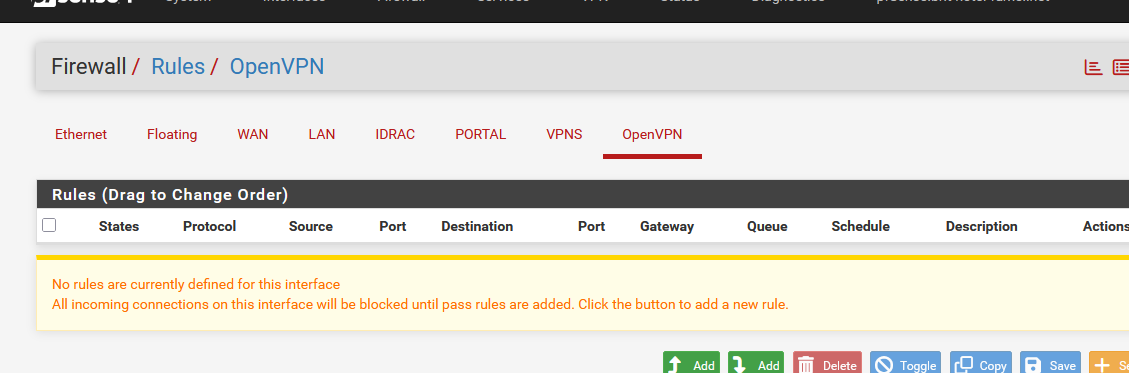
Btw : my OpenVPN interface firewall rule set is empty :
as I've created an "VPNS" for my OpenVPN server :
so it's has it's own dedicated interface with rule set :
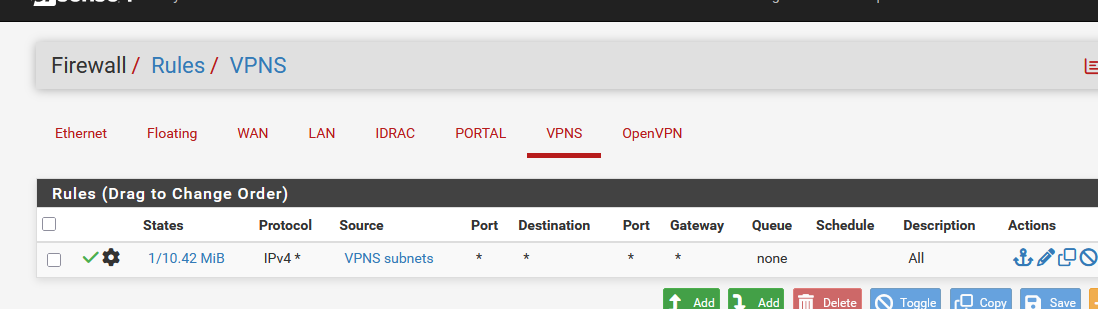
This is also most probably a way of doing things, and not important.
-
hey there,
so:
everything is reachable via VPN except your syno NAS? Correct?
I'd say: are you sure you disabled your NAS firewall? please check again.Just for the fun of it:
set a allow rule on your openVPN Interface to ecplictly allow (for test, change later) ANY to NAS IP for TCP/UDP. (I know, your rule should include that...as mentioned: for the fun of it).Does your iphone get an IP from the right defined range? Do you have random MAC active?
-
@the-other
Yes the Synology firewall is disabled.
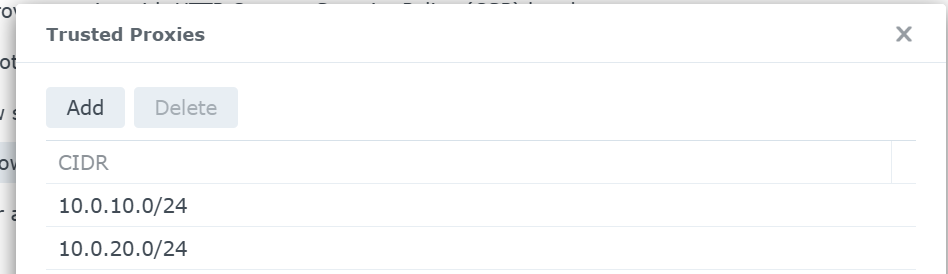
Additionally, I have the VPN subnets listed as 'trusted proxies'
The Asus 'NAS' does not have the firewall enabled since it is in AP mode...
I also verified that the iPhone and iPad get IPs in the expected VPN subnets, I checked for both VPN servers.
Here is something in the Synology that may need tweaking. This is the General>Advanced Settings tab:
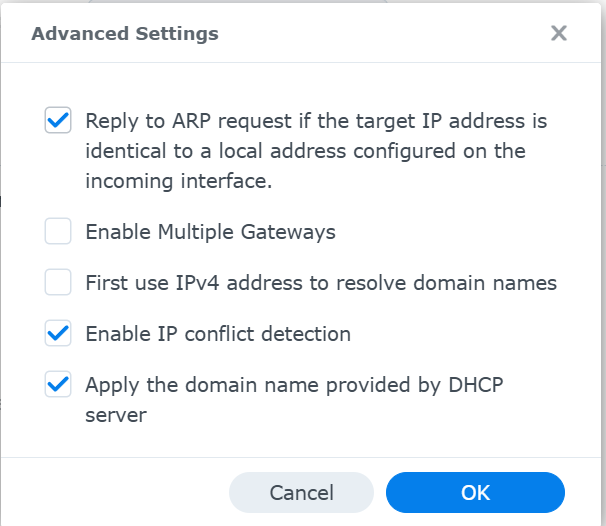
-
@azdeltawye well, I have some stuff set differently:
- your 2nd screenshot (advanced settings) are the very same here (plus activated "first use IPv4...").
- I have nothing under "trusted proxies"
With firewall (on NAS) set I have no trouble accessing my NAS via openVPN.
Have you tried to set an (for the fun of it) rule like
allow any to NAS IP? Yeah, I know...your rule any any allow should cover that...
I still think that something NAS related is the problem, since you can access everything else via vpn just fine...
Sorry for asking again: can you ping your NAS IP thru your VPN tunnel? -
@the-other
Ok, I made a specific rule in the OpenVPN interface to allow any to both NAS servers.
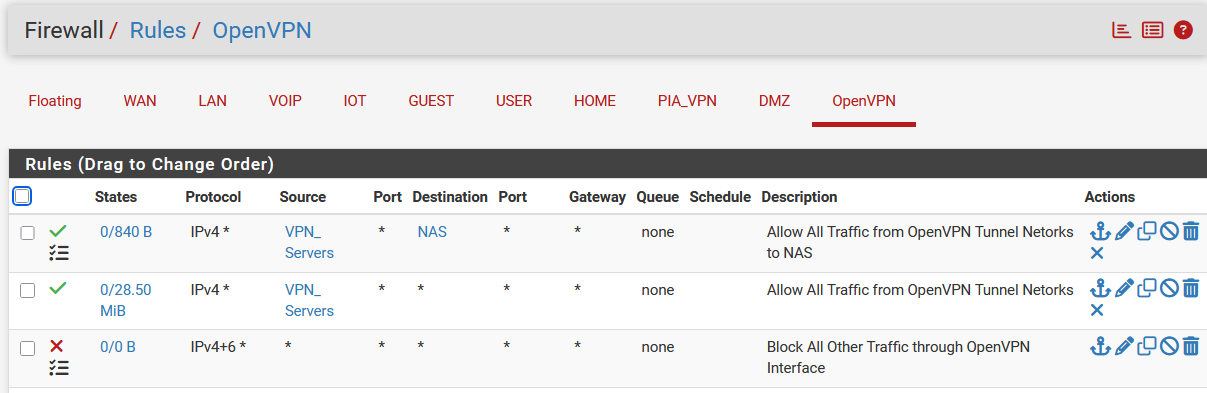
Here you can see me connecting to the VPN server with my iPhone and attempting to ping both the NAS servers. The traffic passes through the firewall but the ping fails to the Synology (200.4).

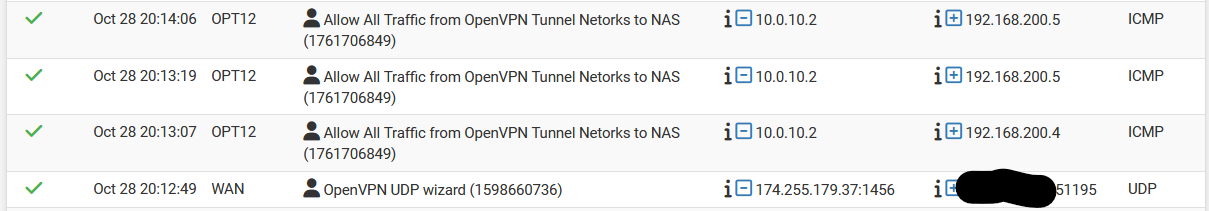
I can, however, successfully ping the backup NAS (200.5) but I cannot connect to that one either with the File Explorer app.BTW, the backup NAS is an old Asus AC-RT86 router in AP mode with WiFi disabled and a SAMBA SSD in the USB port.