Please help to configure HAProxy to serve certifficate on internal LAN too
-
-
@ha11oga11o you can uncheck that - but you would then loose ability to resolve any resources internally unless you create host overrides for them.
Or set reservations for them and register those.
See my edit of previous post - not a fan of using the same domain public and internal if you are going to have stuff on that domain that resolves on the public side - I would suggest you just use say home.arpa as your internal name - then you would never run into such an issue.
-
Mine goal is only to be able to use nextcloud.mydomain.xx both outside and inside LAN.
Outside all works fine. As i understand if im at local LAN with phone we will not be able to resolve nextcloud.mydomain.xx. It will be not reachable?
That is different issue with same outcome then.
We are in need to be able to use it out and in house without VPN fiddling.I did create host override. You can see on posts above. I did place bunch of pictures. Is that what you are talking about?
Thanks!
-
oh yeah, 192.168.1.214 is static bounded with its MAC address.
I untick both DHCP Registration and Static DHCP registration and now dig returns only 192.168.1.1 but i cant access it from LAN anymore. I do have Host override as posted in pics above. But we cannot resolve it anymore.
Is there anything else i need to do so we gain access to nextcloud.mydomain.xx within local LAN?Guys, thank you in advance.
-
@ha11oga11o if you resolve nextcloud.mydomain.xx to your external IP, ie the same one public people do then it would be handled by your haproxy.
Example I have ssl offloading for external users for the public fqdn something.mydomain.tld - this resolves externally to my public IP that hits pfsense wan, this also resolves to my public IP when on my local network, so again haproxy handles the ssl, etc.
But if I wanted or needed to access that directly on my local lan then I use its name.home.arpa:port that the service is on that doesn't do ssl, etc.
What is the point of using the same fqdn internally and externally? What do you think that gets you other than issues?
-
@johnpoz said in Please help to configure HAProxy to serve certifficate on internal LAN too:
@ha11oga11o if you resolve nextcloud.mydomain.xx to your external IP, ie the same one public people do then it would be handled by your haproxy.
Example I have ssl offloading for external users for the public fqdn something.mydomain.tld - this resolves externally to my public IP that hits pfsense wan, this also resolves to my public IP when on my local network, so again haproxy handles the ssl, etc.
But if I wanted or needed to access that directly on my local lan then I use its name.home.arpa:port that the service is on that doesn't do ssl, etc.
What is the point of using the same fqdn internally and externally? What do you think that gets you other than issues?
On this case problem is that phone nextcloud client hangs when switching out and in. Simply cannot be used when inside LAN. Well, it can be used either out or in. But to switch it it needs to be totally reset and sync.
It remember which connection is allowed, at which cert. And sticks on that. Basically its useless until i sort this out to behave exactly same out and in.I cant believe no one had similar issue at home lab self hosted?? Im sure someone had need to do things like this?
Thank you again.
-
@ha11oga11o and again - not an issue if you don't try and use the same domain internally as you do externally.
Haproxy doesn't care from what direction you are coming from, wan or lan makes no difference.
It remember which connection is allowed, at which cert
if you always hit haproxy via the pfsense wan IP - it would always be the same cert.. Not from outside public cert, and internally selfsigned cert.
you list a rfc1918 address on pfsense wan, or are you trying to hit your lan address 192.168.1.1 ? If you hit that and your on the 192.168.1 network you going to run into an asymmetrical problem where sure haproxy will send to your .214 address but when your service answers to a 192.168.1.x address to the client that would be coming from a different host than who it talked to.. Your fqdn you want to use should hit the wan IP of pfsense.
-
@johnpoz said in Please help to configure HAProxy to serve certifficate on internal LAN too:
@ha11oga11o and again - not an issue if you don't try and use the same domain internally as you do externally.
Haproxy doesn't care from what direction you are coming from, wan or lan makes no difference.
It remember which connection is allowed, at which cert
if you always hit haproxy via the pfsense wan IP - it would always be the same cert.. Not from outside public cert, and internally selfsigned cert.
you list a rfc1918 address on pfsense wan, or are you trying to hit your lan address 192.168.1.1 ? If you hit that and your on the 192.168.1 network you going to run into an asymmetrical problem where sure haproxy will send to your .214 address but when your service answers to a 192.168.1.x address to the client that would be coming from a different host than who it talked to.. Your fqdn you want to use should hit the wan IP of pfsense.
Must admit that i really dont understand these things. I dont have knowledge to figure it out. I know that i have ticked
Block private networks and loopback addresses
and
Block bogon networksat WAN general configuration interface. I really dont know can that be issue?
If there is any chance to make it to just work with same domain name in and out, and to serve proper certificate will you please tell me what exactly to do.
If its to much to ask is totally fine. Many thnx for hints and tips, i will try to do it with hit and run approach hoping not to destroy everything in process.
Cheers :)
-
@ha11oga11o said in Please help to configure HAProxy to serve certifficate on internal LAN too:
Block private networks and loopback addresses
on your LAN?
If there is any chance to make it to just work with same domain name in and out
Already went over this - have your fqdn you want to use resolve to your wan address of pfsense.. But then you will be unable to resolve any of your other local resources via dhcp registration. This only complicates the setup, but yeah you can do it.
blocking rfc and bogon on your wan interface has nothing to do with hitting your wan IP from the lan side, those go through your lan interface rules, not your wan rules.
edit: here maybe this will help?
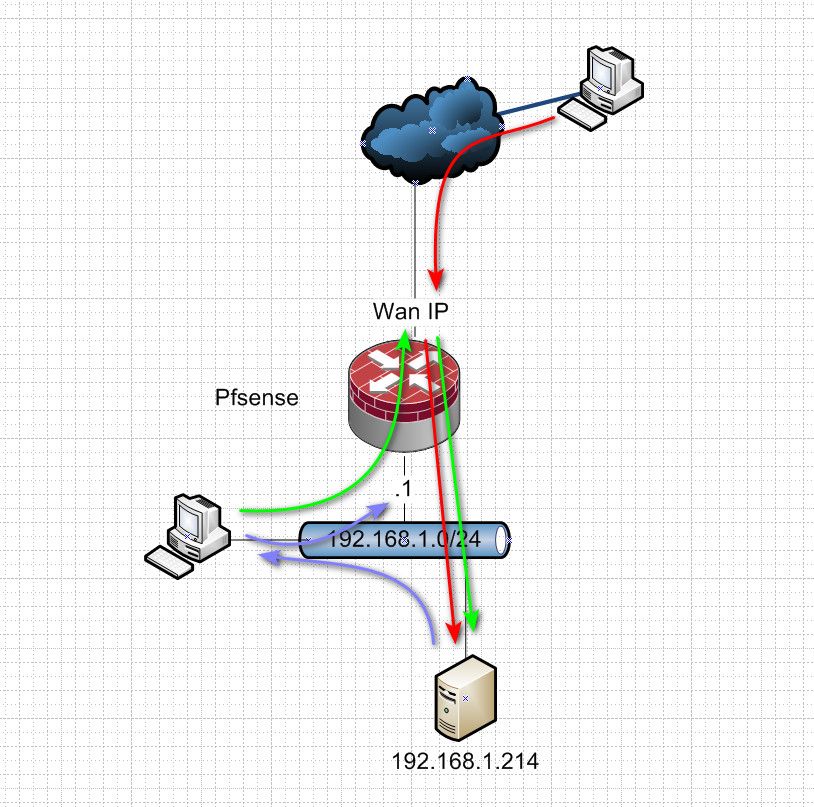
If you hit your wan IP from wan (red) haproxy sends it on to your device serving your service..
If you hit your wan IP from lan (green) haproxy sends it on to your device serving your service.
If you hit your lan IP (purple) from your lan, haproxy sends it on to your device serving the service. But the response now comes from the device itself vs the haproxy. This is asymmetrical.. And your client could say what the hell I didn't talk to 192.168.1.214, I talked to wanIP of pfsense.
If you always hit your pfsense wan IP be it from wan or lan - the cert served will always be the cert you setup in haproxy.
-
I had it working fine before with free dynamic dns. BUT only nextcloud with opened 443 and 80 to outside. It was with self signed certificate.
Now i need it working with proper certificate and possibly to have other fqdn to be usable using haproxy. To play and learn a bit.
It seems theres no proper/easy way to do what i want to be done then?All that works fine for hosting actually, im just trying to do some weird non standard stuff.
Seems self hosting is not appealing as i though to.
Guys, many thnx for your nerves and time for me. If you have any other suggestions, and will to deal with me, im opened for suggestion.
Cheers!
-
@ha11oga11o said in Please help to configure HAProxy to serve certifficate on internal LAN too:
It seems theres no proper/easy way to do what i want to be done then?
What? I have gone over exactly how to set this up... You can use whatever fqdn you want on the public side.. That end up on your pfsense wan IP, and haproxy can send that anywhere you want using whatever certs you want for the offloading.
Your problem is you are trying to use the same domain name internally and externally - this leads to complications in what resolves to what..
All your problems go away if you would just use a different internal domain name to resolve your internal resources. home.arpa is the approved domain for this use.. Now when you hit publicdomain.tld it hits your haproxy on your wan IP. If you use otherpublicdomain.tld - again also hits your wan IP.. Doesn't matter where you resolve this from - out on the internet or from some phone on your local wifi network.
And when you do want to access a local resource with its local IP then use something.home.arpa.. So you can access all your devices via the dhcp registration of their names.
-
@johnpoz said in Please help to configure HAProxy to serve certifficate on internal LAN too:
All your problems go away if you would just use a different internal domain name to resolve your internal resources. home.arpa is the approved domain for this use.. Now when you hit publicdomain.tld it hits your haproxy on your wan IP. If you use otherpublicdomain.tld - again also hits your wan IP.. Doesn't matter where you resolve this from - out on the internet or from some phone on your local wifi network.
Im so sorry. I did not seen that pictogram initially. Thank you.
To be honest, i dont know how to set up what you just told me. Kill me, but i dont have that much knowledge in my head. Im trying.Just to add again, that blo***dy nextcloud app has to be on same domain name connection and same cert. Otherwise it just hangs in some kind timeout with error 1000 or 1001. And when that happens what it had to sync simply forget and never got synced again. So basically its not copied to cloud.
If you are saying to use nextcloud.mydomain.xx outside, and when at local LAN to use nextcloud.home.arpa that will not work. I dont know is it app limitation, protocol limitation or something third.
Please dont roast me, im really grateful for help, bit strugling with languages and terminology.
-
@ha11oga11o said in Please help to configure HAProxy to serve certifficate on internal LAN too:
Just to add again, that blo***dy nextcloud app has to be on same domain name connection and same cert.
Yeah - what part do you not understand if you always resolve nextcloud.domain.tld so that it hits your haproxy on your pfsense wan IP are you not getting?
You have 2 options - use a different domain internally and always go to nextcloud.publicdomain.tld, or use the same domain internally as external and run into the problem of what IP it resolves to..
Change your local domain to say home.arpa or .internal or atleast something different than the public domain your using to point to pfsense wan IP on the public internet.
You are shooting yourself in the foot trying to use the same domain externally as internally. There are ways around it, but they complicate the setup. For example you might be able to use views in unbound as one way to work around the problem. You could use only host entries for all your resources. But then again you run into a problem of using the fqdn for this service, now always pointing to your wan IP.. And that is great when you want to access the service haproxy is doing - but if you want to access that resource on some other service that haproxy doesn't handle - like say simple file sharing.. You are going to have problems.
Since you clearly do not understand how any of this works - the simple solution is change the local domain you are using so it is not the same as the public domain you want to use to get to your nextcloud.
-
@johnpoz said in Please help to configure HAProxy to serve certifficate on internal LAN too:
@ha11oga11o said in Please help to configure HAProxy to serve certifficate on internal LAN too:
Just to add again, that blo***dy nextcloud app has to be on same domain name connection and same cert.
Yeah - what part do you not understand if you always resolve nextcloud.domain.tld so that it hits your haproxy on your pfsense wan IP are you not getting?
You have 2 options - use a different domain internally and always go to nextcloud.publicdomain.tld, or use the same domain internally as external and run into the problem of what IP it resolves to..
Change your local domain to say home.arpa or .internal or atleast something different than the public domain your using to point to pfsense wan IP on the public internet.
You are shooting yourself in the foot trying to use the same domain externally as internally. There are ways around it, but they complicate the setup. For example you might be able to use views in unbound as one way to work around the problem. You could use only host entries for all your resources. But then again you run into a problem of using the fqdn for this service, now always pointing to your wan IP.. And that is great when you want to access the service haproxy is doing - but if you want to access that resource on some other service that haproxy doesn't handle - like say simple file sharing.. You are going to have problems.
Since you clearly do not understand how any of this works - the simple solution is change the local domain you are using so it is not the same as the public domain you want to use to get to your nextcloud.
OK, thank you.
-
@johnpoz said in Please help to configure HAProxy to serve certifficate on internal LAN too:
Yeah - what part do you not understand if you always resolve nextcloud.domain.tld so that it hits your haproxy on your pfsense wan IP are you not getting?
You have 2 options - use a different domain internally and always go to nextcloud.publicdomain.tld, or use the same domain internally as external and run into the problem of what IP it resolves to..
Change your local domain to say home.arpa or .internal or atleast something different than the public domain your using to point to pfsense wan IP on the public internet.
You are shooting yourself in the foot trying to use the same domain externally as internally. There are ways around it, but they complicate the setup. For example you might be able to use views in unbound as one way to work around the problem. You could use only host entries for all your resources. But then again you run into a problem of using the fqdn for this service, now always pointing to your wan IP.. And that is great when you want to access the service haproxy is doing - but if you want to access that resource on some other service that haproxy doesn't handle - like say simple file sharing.. You are going to have problems.
Since you clearly do not understand how any of this works - the simple solution is change the local domain you are using so it is not the same as the public domain you want to use to get to your nextcloud.
This tone is outrageous directed at somebody who acknowledged right off the rip that English is not their first language. How many languages do you speak, John? And safely assuming it's only one—English of course—take it from a fellow English native that you'd do well to say more with less words.
You otherwise were directing OP in the right direction in my opinion.