IP CAM access
-
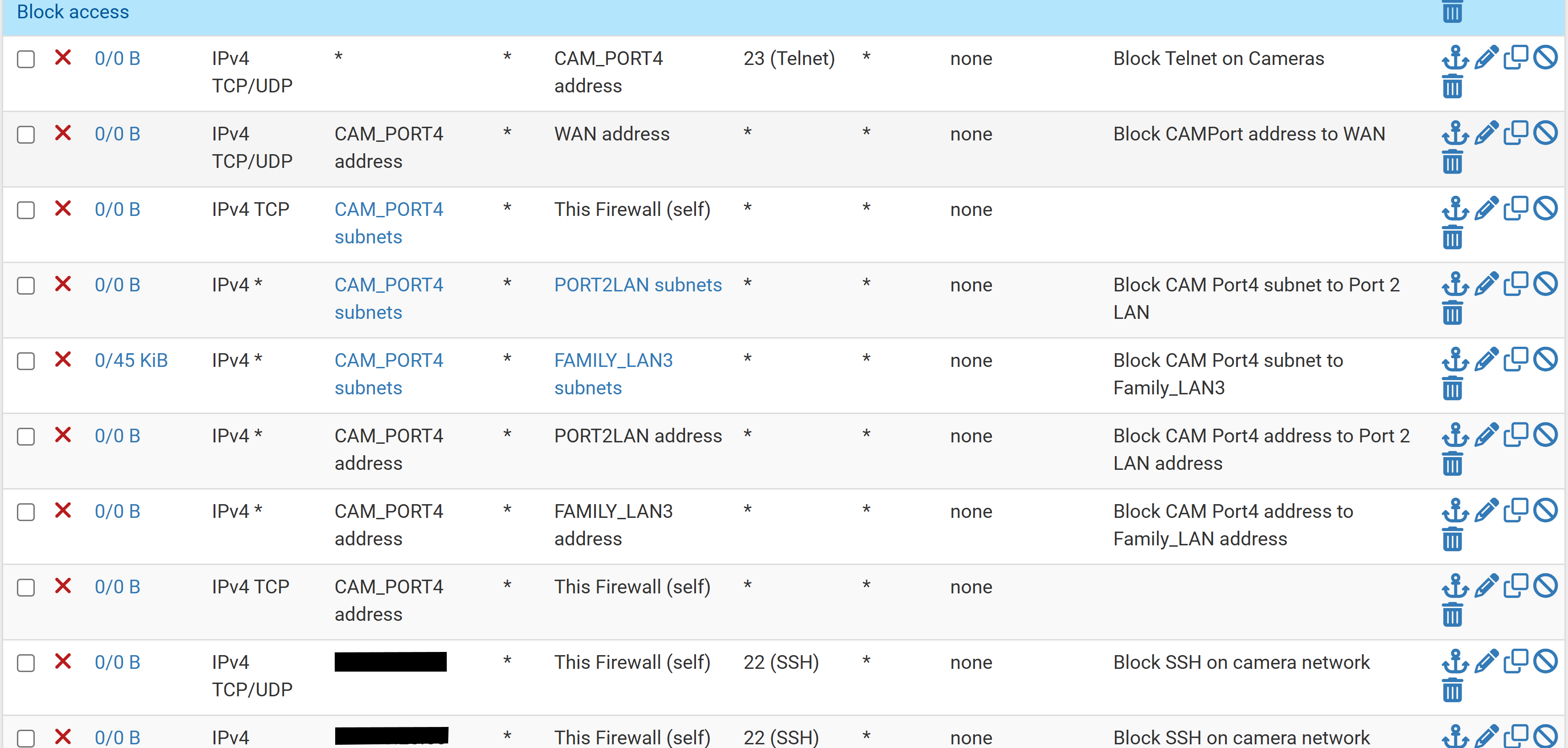
I am new to pfSense. I need some help in configuring my TP-Link IP camera. I am trying to allow them internet access so that i can view cameras when at and not at home. I do not want them to be able to access to my other interfaces. Right now, I am having to manually enter block rules on the TP-Link interface to allow access and see cameras via their app. My rules on the TP-Link interface is large. I do not have any VLAN's setup.
TP-Link camera interface
10.99.x.x is the static IP address
I have block rules to prevent access to firewall, WAN, and my other interfaces.
Manually entering IP address that are getting blocked.
I would greatly appreciate any help.
-
@asyouwish57 Everything going into the interface is blocked by default anyways. You have to have a rule allowing traffic for it to pass.
If you instigate however a connection from one of your other interfaces to the camera where you have allowed it there will be an open state which will let the camera pass traffic back until the state expires..
Your first rule is backwards. though as I pointed out not really needed since it is already blocked by default..
I do not see any kind of rules allowing the camera(s) to access DNS.. by design?
-
I dont know if I can help you , but I will try to get you going in the right direction. I am not familiar with tp-link cameras. I use nest/google so i have a idea.
You certainly have a mess of firewall rules. Does your port 4 subnet have internet access?
I would start with a simple rule set, get everything working. Then add your layers of restrictions.
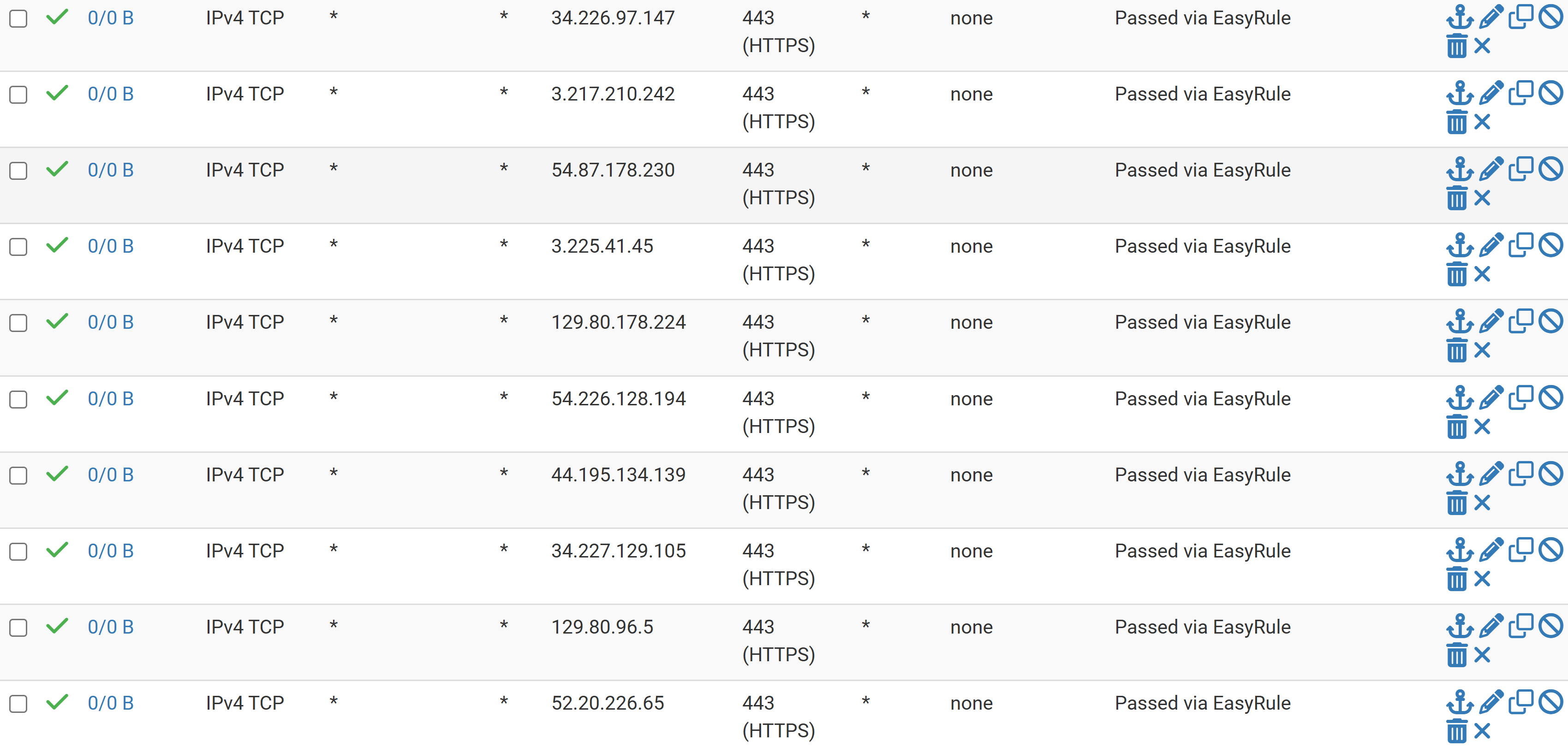
Here are the rules i use for my wired iot devices.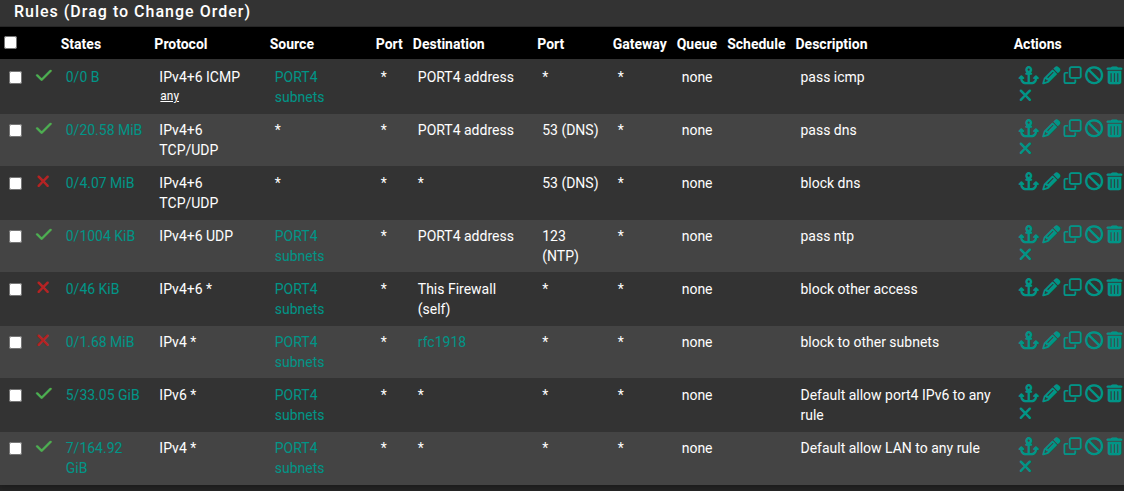
you can use one block rule to other subnets . The netgate docs show how to set it up and use it for the WAN.but, you can also use it to keep every one in there own lane.
https://docs.netgate.com/pfsense/en/latest/recipes/rfc1918-egress.html.I hope this helps you a little bit.
-
Better option is to use a self hosted VPN on pfSense to remotely connect to devices or services on your LAN. That way you are not opening ports on your firewall for miscreants to attack.
Tailscale is what i use.