Crazy, Can't Firewall Interfaces From Each Other
-
This is just kinda weird.
I've been using M0n0wall for years, and I'd like to think I know my way around the firewall rules, but this one is got me stumped.
I'm running 3 interfaces, Wan (public IP) Lan (192.168.100.x) and Opt 1 (10.12.45.x). The WAN is running on the onboard NIC, and the other two interfaces are running on an Intel Dual NIC.
I have firewall rules on both the Lan and Opt 1 interfaces specifically disallowing traffic to one another. I have that rule at the very top for both interfaces, yet they both pass traffic to one another.
I'm running version 1.2 beta 1 on a 1 GHz Celeron with 512 MB ram, and the only package I'm running is Squid.
Am I crazy, or just stupid? Any ideas?
-M@
-
Please post your rules from both the LAN and OPT1 side so we can see if there is an issue in the way you set the rules up.
-
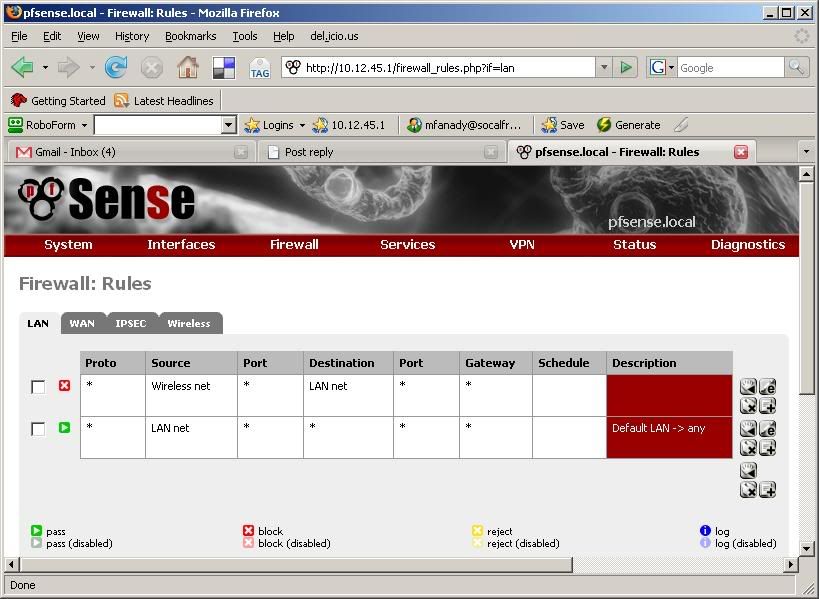
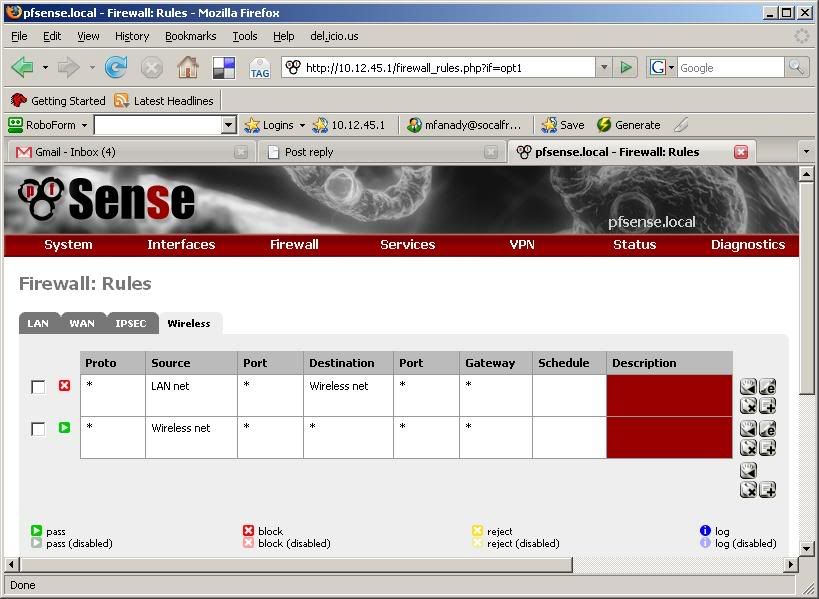
Not sure if it would be better to just post the firewall portion of the xml file, or screen shot, so for clarity's sake, I'll just post screen shots.
These are just the latest variations I've tried. I was under the impression that unless explicitly allowed, the firewall will block all incoming connections to an interface. The only other experience I have in this regard is running m0n0wall on multi NIC Soekris boxes, where this is the case.
In this scenario however, I have my craptop on the wireless, which obtained a lease of 192.168.100.199, and can both ping computers on the lan (in the 10.12.45.x subnet) and access system resources. I have also refreshed the firewall states.
My only thought is there is a hardware problem, maybe it doesn't like the old Intel dual NIC I'm running? To muddy the water even further, when I first set this up a few days ago, I tested it, and the two networks were segregated, next thing I knew they were not. This is only for my home setup (which is why I'm taking a chance on old hardware and beta versions of software) but I'm quite perplexed none-the-less.
edit the only other thing besides squid I have going on are two IPsec tunnels, one to the 10.11.0.x/24 subnet, and another to the 10.11.1.x/24 subnet. Fortunately, those subnets CANNOT be accessed from the wireless subent (I share my internet with my neighbors over the wireless)
-
You got the flow of traffic wrong.
On Lan ( block any lan traffic to wireless )
Source = Lan net
Destination = Wirelessetc…..
-
Well, on the plus side, I guess my hardware is fine, but unfortunately, I guess I am just retarded. Thanks Razor.
-M@
-
It's exactly as Perry points out. Just remember that the LAN interface can't control traffic starting from the Wireless network or vice-versa. Nice to see that it's working and that there are no hardware problems either. :)