Managing Wired + Wireless IP Cameras (blocking access explicitly?)
-
Thanks Derelict for the comprehensive response. I can support multiple SSID's but I recently retired my old DDWRT powered AP's in favor of some D-Link DAP-1650 which have "Guest SSIDs" but not just raw control over SSID creation/managment or VLAN tagging for them. I may opt to simply add an OPT1 and have that be the "CAM" network.
I currently do not allow any outside access to any of the cams, nor do I allow VPNing to the network as one of the cam's is a baby monitor. I may relent and allow a VPN of some sort into the network so I can check in while traveling. I am very rusty on OPEN VPN options but I think that appears to still be the best option and it has viable options for Android and Windows clients.
Thank you again, the overview is much appreciated and allows me to say I'm OK going forward with the cameras in my main network and using VPN For remote access as needed. I will look to eventually put cam's on their own segment via an OPT interface or VLAN's and add some additional controls that way.
-
Wow didn't take much to get OpenVPN going with Cert + Login authentication. The client export package makes getting it going on Android and Windows a breeze. I remember distinctly paying Chris to walk me through step by step connecting a site to site open VPN a few years ago and thinking it seemed more complex than it needed to be. Sure is slick now with the wizard.
-
Yup. EZPZ. And pretty secure with SSL/TLS + User Auth with TLS authentication enabled. You pretty much only have to worry about the key getting compromised. Lots of luck to anyone without it.
-
Yup. EZPZ. And pretty secure with SSL/TLS + User Auth with TLS authentication enabled. You pretty much only have to worry about the key getting compromised. Lots of luck to anyone without it.
Yea, I went with SSL/TLS + USER and it was a breeze. Sure makes me feel better vs poking holes. Now to get some sort of Dynamic DNS setup since my cable company decided to start moving IP's on me after 10 years of the same IP.
-
Sorry for the noob here, but I see traffic going from Cams to WAN. This is apparently a known "Feature" of some of the cameras I have. Will this firewall rule (assuming IP_CAMS is an alias of cameras) block any access from the cameras to the outside world:
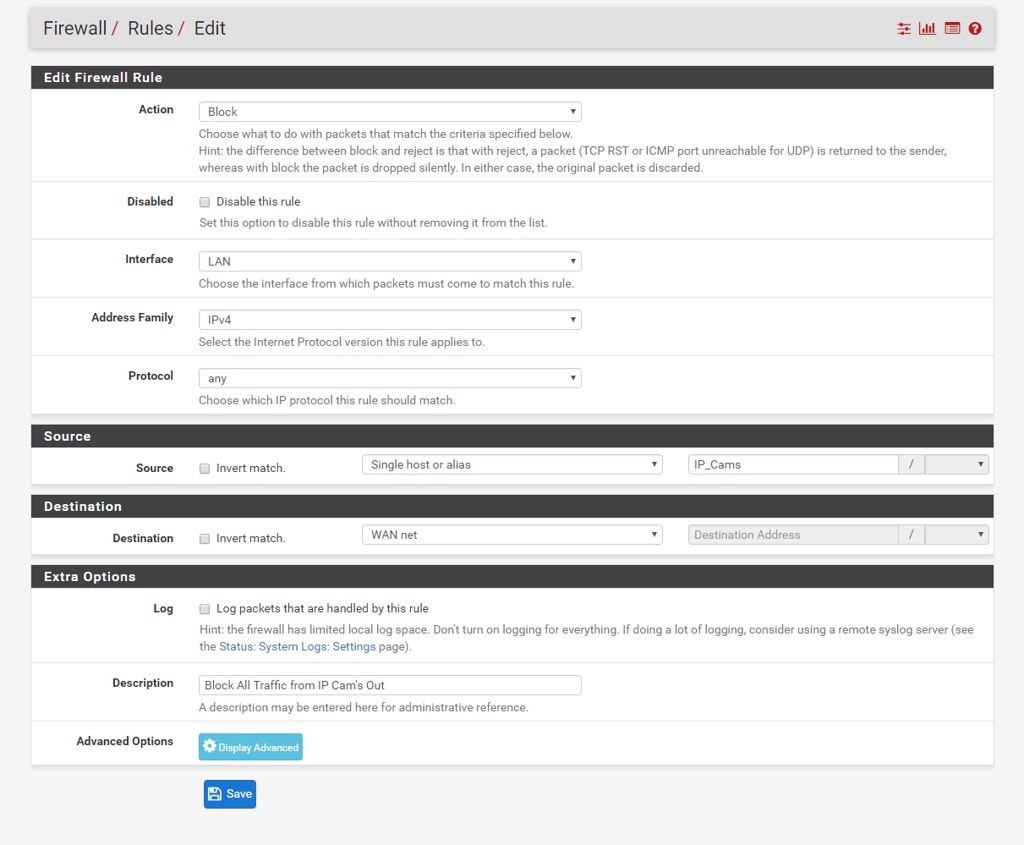
?
I am always on the LAN network when connecting to the cameras thanks to the VPN set up above.
-
Change the Destination from WAN Net to Any. WAN Net is not "The Internet", it's just the actual network your WAN IP is part of.
-
@KOM:
Change the Destination from WAN Net to Any. WAN Net is not "The Internet", it's just the actual network your WAN IP is part of.
That won't block traffic to LAN? This is why I ask I guess.
-
Of course it won't, this iscontrolling traffic coming FROM the LAN going anywhere else (thus the any) thanks for the patience ;)
-
this iscontrolling traffic coming FROM the LAN going anywhere else
Now you're getting it. Rules apply to traffic entering an interface and control where that traffic is allowed to go to.
-
@KOM:
this iscontrolling traffic coming FROM the LAN going anywhere else
Now you're getting it. Rules apply to traffic entering an interface and control where that traffic is allowed to go to.
I was CISCO CCNA Certified 14 years ago, you'd think this wouldn't be this foreign to me but that's what you get when you become a middle-manager stooge. Thank you again for your patience and answers this community has always been so helpful.