Scheduled blocks won't work without manual states reset
-
I can confirm:
/sbin/pfctl -F state works sometimes (cron task)
pfctl -F state works sometimes (cron task)/sbin/pfctl -k >IP on the block list<works sometimes="" (cron="" task)<br="">pfctl -k >IP on the block list <works sometimes="" (cron="" task)<br="">Both also seem to work in the Diagnostics/Command Prompt however, nothing reliably clears established UDP states.
After the PASS schedule expires, all states are cleared and then a few (Steam and Teamspeak in my case) immediately re-establish.</works></works>
-
Thanks to alot of my own trial and error I have figured out why it doesn't work for me and how I can make it work.
If I have the schedule block at 10pm at night and schedule the cron job to clear a specific IP states at 10:01pm it doesn't work.
If I change the cron job to run at 1 minute past the hour for every hour, it works!
To confirm the obvious, yes my computer time and pfsense times are correct and i've run the test several times. I've run now at 4pm scheduled block with cron to block at 1 minute past every hour and it worked immediately. I had it try before at 3pm scheduled block with 3:01pm run same cron job. It doesn't work.
So for some reason, cron doesn't recognize the specific hour! It's in 24 hour clock military time. I haven't checked if I can do 12 hour clock time if it's possible. But I obviously have the Cron job programmed correctly and everything else correct as the only difference that makes it work is specify to run the job every hour at 1 minute past the hour, rather than at the specific time. This is not a good solution as it can cause interrupts every hour.
I expect to be the first person to find the solution to this as no one has an answer anywhere I could find. Please prove me wrong and beat me to it.
-
I managed to get cron to work without saying * for the hour. I found out that although the schedule runs at 1800 hours (6pm) I have to schedule Cron to run at 2201 hours for it to think it is 1 minute past the hour. It then successfully runs the cron job 1 minute after the scheduled job and clears the state table. So for Cron to run the job 1 minute after the scheduled rule, I have to actually program Cron to run 4 hours and 1 minute after the scheduled rule.
My question now is why does Cron think it is 2200 hours when it is 1800 hours? In other words, why does Cron think the time is 4 hours ahead of what the schedule does?
-
I managed to get cron to work without saying * for the hour. I found out that although the schedule runs at 1800 hours (6pm) I have to schedule Cron to run at 2201 hours for it to think it is 1 minute past the hour. It then successfully runs the cron job 1 minute after the scheduled job and clears the state table. So for Cron to run the job 1 minute after the scheduled rule, I have to actually program Cron to run 4 hours and 1 minute after the scheduled rule.
My question now is why does Cron think it is 2200 hours when it is 1800 hours? In other words, why does Cron think the time is 4 hours ahead of what the schedule does?
Have you set the timezone correctly? - System/General Setup.
-
I managed to get cron to work without saying * for the hour. I found out that although the schedule runs at 1800 hours (6pm) I have to schedule Cron to run at 2201 hours for it to think it is 1 minute past the hour. It then successfully runs the cron job 1 minute after the scheduled job and clears the state table. So for Cron to run the job 1 minute after the scheduled rule, I have to actually program Cron to run 4 hours and 1 minute after the scheduled rule.
My question now is why does Cron think it is 2200 hours when it is 1800 hours? In other words, why does Cron think the time is 4 hours ahead of what the schedule does?
Have you set the timezone correctly? - System/General Setup.
Yes, the time zone is correct in General setup.
-
I saw another discussion someone wrote to use the following code but it doesn't work for me.
pfctl -k x.x.x.x/24 ; pfctl -k 0.0.0.0/0 -k x.x.x.x/24
I assume if my pfsense box is 192.168.1.1 that the x.x.x.x should be that IP address? Or is there something else I should be doing? That threat is closed to comments or I'd ask there.
-
Since killing the state table by IP, even manually pressing the button, is unreliable and the only method is resetting the entire firewall state table manually, I've set a scheduled reboot using Cron which works perfectly. I know it's not the idea solution rebooting the server every night, but I need results and this is the only reliable method.
/sbin/shutdown -r nowI hope pfsense will have a patch to fix clearing the state tables by ip address.
-
Since killing the state table by IP, even manually pressing the button, is unreliable and the only method is resetting the entire firewall state table manually, I've set a scheduled reboot using Cron which works perfectly. I know it's not the idea solution rebooting the server every night, but I need results and this is the only reliable method.
/sbin/shutdown -r nowI hope pfsense will have a patch to fix clearing the state tables by ip address.
I can't believe we are the only people who want this 'feature', I would expect pfsense to be capable of what the $100 routers seem to do quite well.
-
You are not alone and this is a very old problem on pfsense… only this thread is 3 years old.
In time what you can't fix you learn to live with that or if you can't, then you will try to find a solution that work to your needs.This is how it finally work for my kids, see the attachment:
- allow DHCP only to this VLAN/firewall.
- allow DNS & NTP only to this firewall.
- deny access to this firewall for all client except admin IP...
legend:
inet lucia = Mon-Sun 12:00-12:30 / Mon-Fri 19:00-20:30 / Mon-Sun 14:30-17:00 ( school )
vacanta = every day 06-23 ( no school )
zilnic = every day 06-22:15p.s.
extra cron script to kill states,
don't forget to make the script x
...
15-30 22 * * * root /usr/local/bin/pf_stop_tablete_copii.sh#!/bin/sh /sbin/pfctl -K 192.168.101.111 /sbin/pfctl -K 192.168.101.112
-
@ecfx:
You are not alone and this is a very old problem on pfsense… only this thread is 3 years old.
In time what you can't fix you learn to live with that or if you can't, then you will try to find a solution that work to your needs.This is how it finally work for my kids, see the attachment:
- allow DHCP only to this VLAN/firewall.
- allow DNS & NTP only to this firewall.
- deny access to this firewall for all client except admin IP...
legend:
inet lucia = Mon-Sun 12:00-12:30 / Mon-Fri 19:00-20:30 / Mon-Sun 14:30-17:00 ( school )
vacanta = every day 06-23 ( no school )
zilnic = every day 06-22:15p.s.
extra cron script to kill states,
don't forget to make the script x
...
15-30 22 * * * root /usr/local/bin/pf_stop_tablete_copii.sh#!/bin/sh /sbin/pfctl -K 192.168.101.111 /sbin/pfctl -K 192.168.101.112Thanks, I'm not sure this all makes sense to me but it looks like an uppercase K where I was using a lowercase k?
Also, to specify allowe DHCP, DNS, NTP only to this firewall, i'm not sure where to set those rules? -
see the attachment.
I have also a DNS server in another lan 192.168.22.16 for kids that filter dns with pihole and forward requests to opendns ( family shield… adult content... ) so I had to allow also open DNS directly just in case my server is offline.
Local DNS/NTP is your LAN interface IP and 127.0.0.1
-
Odd thing, my router didn't reboot tonight at 10:05pm as scheduled (which I put 2:05am because it was working 4 hours in ahead previously). I tried setting the correct time and now it works. It seems to have fixed itself. Very weird but thought I'd share that problem is solved.
Just need to test more with rules to avoid rebooting. -
Have you tried Opnsense? It has the latest BSD.
-
Have you tried Opnsense? It has the latest BSD.
I haven't tried Opnsense, but honestly I just setup pfsense and want to give it a fair shot. I switched from ipfire which was having more problems. pfsense seems much better than ipFire so far, although it has the same challenges with removing states after scheduled blocks without rebooting. The good news is with pfsense I can at least schedule a reboot where ipfire I couldn't do that.
With more time I'll learn more tricks I can share. :)
-
Have you tried Opnsense? It has the latest BSD.
With more time I'll learn more tricks I can share. :)
Looking forward to it as I am almost out of hair! ;)
-
Have you tried Opnsense? It has the latest BSD.
I haven't tried Opnsense, but honestly I just setup pfsense and want to give it a fair shot. I switched from ipfire which was having more problems. pfsense seems much better than ipFire so far, although it has the same challenges with removing states after scheduled blocks without rebooting. The good news is with pfsense I can at least schedule a reboot where ipfire I couldn't do that.
With more time I'll learn more tricks I can share. :)
Anything new?
-
I tried everything in this thread.
This is still not fixed.
-
I have a combo solution which works well (so far). Set your schedules for allowing instead of blocking with scheduled cron jobs (example: /usr/bin/nice -n20 /sbin/pfctl -k 192.168.1.10) for flushing states, say in every 60min, followed by a blocking rule.
this is how my rules look like on the LAN interface
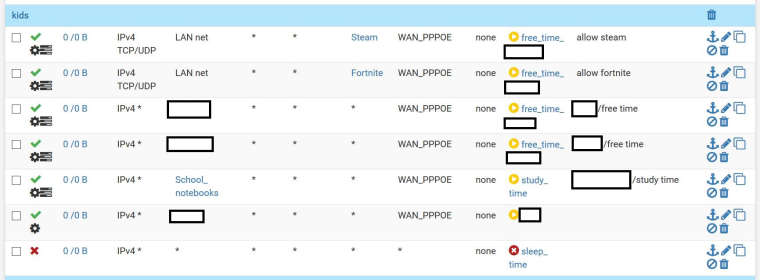
-
Wow this new forums software is horrible. Doesn't work right with noscript at all, and i had to switch to chrome (Spew)....
that said, i have stumbled upon this "bug" and am obviously trying to do the same thing as you all. I noticed that my schedule was applying, and new connections are being filtered, but if a user has a voice channel open (Discord i think), then the connection is not terminated till i do a full state reset.
Sorry that i dont have anything new to add except that pfsense should fix this OBVIOUS BUG....
-
and still current on 2.4.4-RELEASE (amd64)