WebConfigurator default certificate expired yesterday
-
Or, even better : update - don't stay on old versions.
And then …. you have access to a package called 'acme' that can install a new, real - your browser will be so happy - certificate. And it will not expire ;) (well, it does, but it will get renewed before, you doing nothing to make this happen)Btw : but upgrade, otherwise you'll be having very soon a boatload of exceptions to remember.
-
Or he can just have his browser just the CA of pfsense that created the cert.. Then his browser will be happy, and he can use any fqdn he want does not have to be public domain, and can use rfc1918 in his san on his cert as well.. And can set the cert to be good for 10 years..
His browser will be very happy then ;)
-
Or he can just have his browser just the CA of pfsense that created the cert.. Then his browser will be happy, and he can use any fqdn he want does not have to be public domain, and can use rfc1918 in his san on his cert as well.. And can set the cert to be good for 10 years..
His browser will be very happy then ;)
Ok, I agree, you win :)
I have to add that a domaine name is needed, well spotted. The "acme solution" is like using a missile from a nuclear sub-marine to wipe out an ant.
But it works sooooo good. -
Not sure I would call it that drastic of a solution ;) And for many it is a very valid solution.. But I don't use public domains locally.. I use local.lan for my local domain. So that rules out acme, and I also like to be able to access devices via their rfc1918 address and still get happy green icon for the cert.. So again rules out acme..
This also allows you to easy create certs for other sort of device that uses https to access.. my unifi controller for example, or the web gui on my switches, etc. Just trust the CA and now you can use those certs you create pretty much anything you have locally that has a webgui and allows you to install certs.
-
I'd use that for a public website, but thats about it. Those silly warnings on my browser are no annoyance after the first time I use it on pfsense.
-
an expired certificate in firefox seems to re-present the untrusted website alert. I had obviously whitelisted the self signed cert in the browser years ago. It just expired, thus creating another warning evidently.
Or, even better : update - don't stay on old versions.
There is no upgrade path for i386 smarty pants, so i have to create a brand new x64 install and then hope the config imports (read as takes time to do, time i dont have right now) (aint broke = dont fix, other fires burning IRL, a million better things to do, etc..). The new pfsense version was just released 2 months ago!, and it already has a few point releases so i know its not super duper stable for everyone yet. Who knows, some developer might have assumed that everyone unnecessarily turns off their serial ports… or like that time upgrading from 1.2.3 to 2.x required me to purchase all new hardware (fun times!).
So theres a boatload of not upgrading right now reasons, take your pick.
-
There is no upgrade path for i386 smarty pants, so i have to create a brand new x64 install and then hope the config imports (read as takes time to do, time i dont have right now) (aint broke = dont fix, other fires burning IRL, a million better things to do, etc..).
Installing 2.4.2 with a config recovery takes less than 10 minutes, and even if you don't want to go to 2.4 the 2.3 branch is at 2.3.5p1 now so your 2.3.4p1 is outdated on all fronts.
-
"aint broke = dont fix"
Keeping your firewall/security device current doesn't fall to that sort of thinking…
Big difference in hey the TV still gets a picture sort of no reason to upgrade it mentality... And hey my firewall is running old code..
I can understand dealing with change control - or yeah other things going on where you push it off.. But that old adage does not apply when it comes to keeping software updated and current.. Look at all the companies that got bit by wannacry because ah will get to that patch in a few months, next year - why fix what not broke ;)
-
I'd also update the TV (-:
I'd religiously update anything with a web connection.
-
hehehe - TV doesn't have smart apps, no network connection… should of been more clear in my example ;)
Like when you were a kid and you had to use pair of pliers to change the channel on the old knob tv... Dad would say not broken, why fix it - yes we have a remote.. He would just tell you to change the channel so why get a new fancy tv ;) hehehe
I completely agree.. Anything that talks on the network should be patched.. There is something said about jumping the guy and rolling out a patch to 1,000 computers without any testing 1 hour after code is released... Then there is still running windows 7 non sp1 on your network and complaining that you got hit with wannacry ;) 2.3.5 came out over 2 months ago... If your stuck on 32bit code..
-
The new pfsense version was just released 2 months ago!, and it already has a few point releases so i know its not super duper stable for everyone yet.
That logic fails since everything that went into 2.3.5 and 2.3.5_1 was to correct defects in 2.3.4_1.
The easiest way to refresh the webgui certificate is to go to the menu, open option 12, then type playback generateguicert then type exit. That will generate the webgui certificate using current best practices.
Enter an option: 12
Starting the pfSense developer shell….
Welcome to the pfSense developer shell
Type "help" to show common usage scenarios.
Available playback commands:
changepassword disablecarp disablecarpmaint disabledhcpd disablereferercheck enableallowallwan enablecarp enablecarpmaint enablesshd externalconfiglocator gatewaystatus generateguicert gitsync installpkg listpkg pfanchordrill pftabledrill removepkgconfig removeshaper resetwebgui restartdhcpd restartipsec svc uninstallpkgpfSense shell: playback generateguicert
Playback of file generateguicert started.
Generating a new self-signed SSL certificate for the GUI...Done.
Restarting webConfigurator...Done.
pfSense shell: -
My 32 bit D2700 is immune to spectre by the way… Funny. So is my old AMD x2.
Saved by old junk!
-
@johnpoz I assume you mean "just use the CA". Would you please post how this can be accomplished when it is impossible to log into the GUI?
-
-
That's exactly what I ended up doing -- I used kde konqueror.
I had tried console/ pfsense-shell / generateguicert but it didn't do anything, didn't generate any output and offered no help with '--help'. -
Derelict gave you how you could redo the self signed via console.. Or as it seems you did used a browser that allows you to make exception for old certs.
As to how to create your own signed cert via pfsense CA... Have been over this many many times already..
Here is latest version - previous versions lost their images when forum was updated
https://forum.netgate.com/post/831783 -
@johnpoz As I've said too many times, the gui was unreachable and once I used a less secure browser, I was able to fix it. I truly don't need instructions for how to use a gui I couldn't reach and which I successfully used with the less secure browser. generateguicert did nothing as I've said a couple of times.
-
Well NO SHIT its not going to do anything if you don't use the playback command as instructed
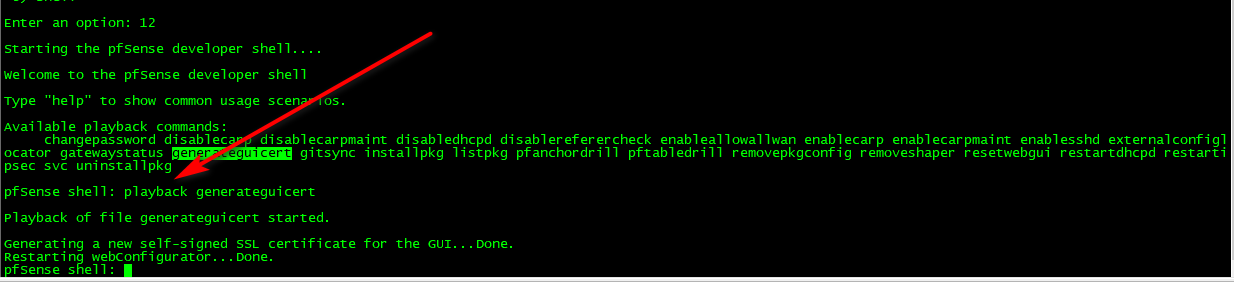
Clearly it generates new cert.. And sets the gui to use it..
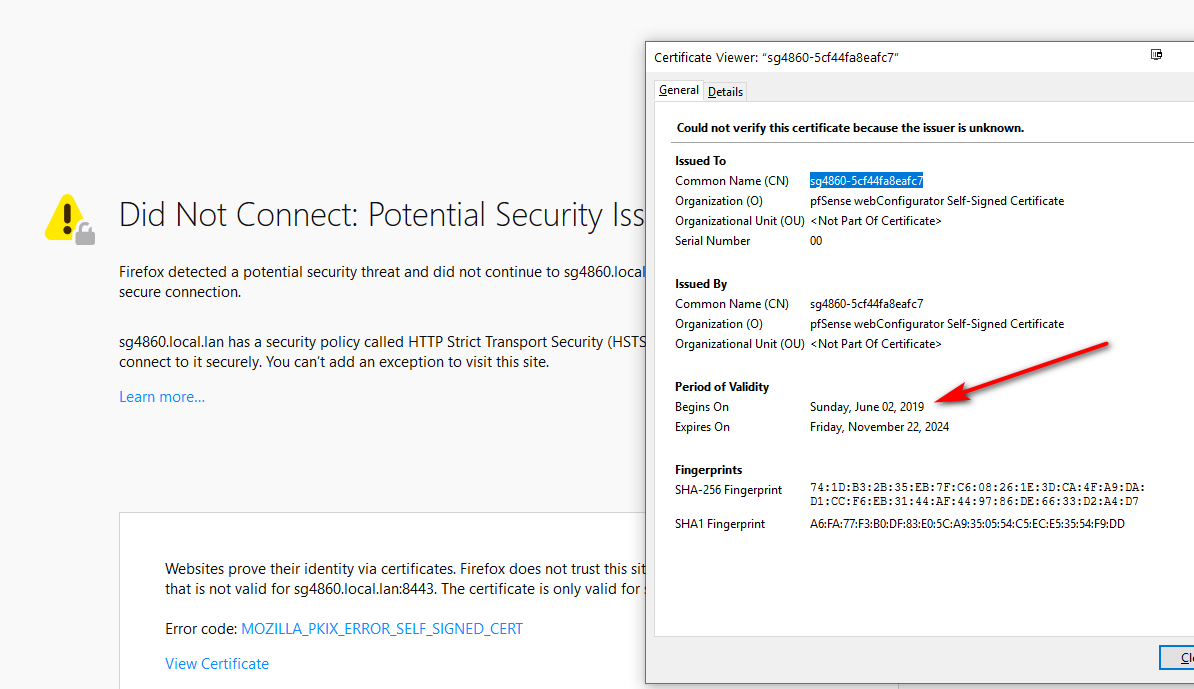
My point was since you already stated your in - is NOW do it with your own CA and set it for like 10 years so you don't have to worry about it expiring again.
-
@adamf663 said in WebConfigurator default certificate expired yesterday:
generateguicert did nothing as I've said a couple of times.
It generates and puts in place a new cert with valid date boundaries.
Still, the new cert it signed by an authority that your browser doesn't trust.
That can be circumvented by importing the cert details into the 'database' of your system or browser. A working GUI is of course needed to do so.
Not the GUI, but the console access can stop https access to the GUI, if needed. Many forum posts explain what to do.I've just used t to generate a new cert, my Fifefox was still complaining of course, had to use the IPv4 of my pfSense, and got in after telling Firefox to allow an exception. So, the instructions work.
I was using the console access.The fact that browsers become more more picky every day is known.
Up to you to disable the https access to the GUI, or use really trusted certificates out of the box (brower's box).edit @johnpoz went down the same way, posted faster.
-
@Gertjan My ca goes out 10 years. The problem was with the server cert and generateguicert did nothing and didn't write any information.