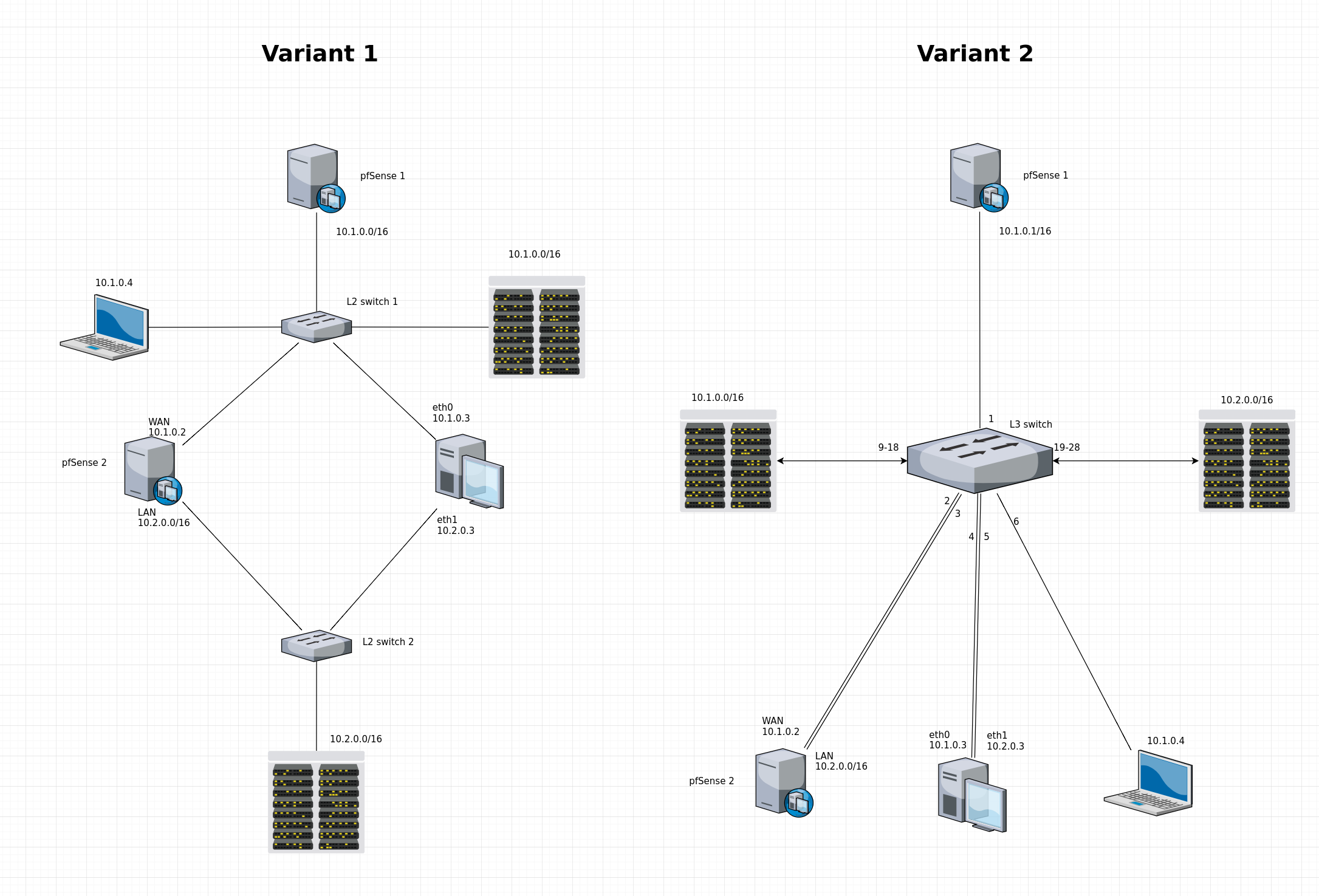
VLAN setup
-
I need some guidance regarding my very first VLAN setup. Please take a look at both variants on the diagram. What I want:
- my laptop obtains IP from pfSense 1 (company pfSense)
- my workstation obtains IP on eth0 from pfSense 1
- some servers obtain IPs from pfSense 1 so that they can be shared with other coworkers (10.1.0.0/16)
- the WAN interface on pfSense 2 (my personal pfSense) obtains IP from pfSense 1
- my workstation obtains IP on eth1 from pfSense 2
- another group of servers for personal use obtain IPs from pfSense 2 (10.2.0.0/16)
- all my VPN connections/clients are running on pfSense 2 so that they can be used from my Workstation (through eth1) and also from my personal servers in 10.2.0.0/16)
I have no problem setting this up with two dummy switches as shown in variant 1. But I have one Cisco SG300-28 that sits unused and this is the perfect opportunity to learn something new. I want to go with variant 2. Could you please explain me how should I configure all the ports on the switch? I am reading about tagged/untagged/trunk/access port modes and I am trying to make sense out of it but I am afraid I still don't fully understand it. Also what the pfSense configuration should look like? Any gotchas?
Thanks!
Switch ports:
1 - from pfSense 1 (company pfsense)
2 - WAN on pfSense 2
3 - LAN on pfSense 2
4 - eth0 on my workstation
5 - eth1 on my workstation
6 - laptop
9-18 - shared servers
19-28 - personal servers
-
The purpose of a VLAN is to logically separate networks. Those networks would be on different subnets. However, unless I'm missing something, all your addresses are in the same subnet. This means using VLANs won't get you much. While desktop computers and servers can usually be configured to access VLANs directly, don't be surprised if your notebook doesn't. This means you'll need a managed switch to assign individual ports to the various VLANs. That Cisco switch would be fine for that. You'd then have to configure a VLAN interface on pfSense, for every VLAN you want, in addition to the native interface. Each of these interfaces must be on it's own range of network addresses, such as 10.1.0.0, 10.1.1.0, etc..
-
No, I have two subnets: 10.1.0.0/16 (the company subnet) and 10.2.0.0/16 which would be my personal subnet. There must be a way to separate them because there are two DHCP servers connected to the same switch. The way I see it I need a VLAN for 10.2.0.0/16. But I am not sure if I need a second VLAN for ports 2, 4, 6 and 9-18. I think port 1 should be trunk.
-
@pvn said in VLAN setup:
No, I have two subnets: 10.1.0.0/16 (the company subnet) and 10.2.0.0/16 which would be my personal subnet. There must be a way to separate them because there are two DHCP servers connected to the same switch. The way I see it I need a VLAN for 10.2.0.0/16. But I am not sure if I need a second VLAN for ports 2, 4, 6 and 9-18. I think port 1 should be trunk.
Sorry, I missed the 10.2. You configure pfSense for whatever LAN/VLANs you need. You might have native LAN and a VLAN. Then configure the switch to pass the LAN/VLANs as appropriate, with the port connected to pfSense set up as a trunk.
-
I think I figured it out. I configured all ports on the switch in Access mode. Then I assigned VLAN 1 to the ports where I want direct communication with the company's pfsense and VLAN 10 to the ports where I want communication with my personal pfsense. I don't know if this is the best way to do it but it works. And I don't have any VLAN interfaces on my pfsense. I guess I don't need it.
-
So you have this pfsense 2 downstream of pfsense 1 with pfsense2 wan in 10.1 and is lan in 10.2?
Why do you have 1 machine with legs in both?
-
@johnpoz said in VLAN setup:
So you have this pfsense 2 downstream of pfsense 1 with pfsense2 wan in 10.1 and is lan in 10.2?
Correct.
@johnpoz said in VLAN setup:
Why do you have 1 machine with legs in both?
Yes, my workstation will have eth0 in 10.1 (corporate network) and eth1 in 10.2 (my private network). The reasons for this are:
- I will have direct access to the servers in both networks and my personal servers in 10.2 will be invisible from the corporate network
- I will have all my VPN connections on pfSense 2 instead of on my workstation. That way everything in 10.2 will be able to use them. I will have to add the appropriate routing on my workstation in order to route the networks behind the VPNs via eth1.
- It is fun
If you have any better idea how to accomplish all this please do let me know.
-
@pvn said in VLAN setup:
my workstation will have eth0 in 10.1 (corporate network) and eth1 in 10.2 (my private network)
You better be careful with that. You might wind up bypassing the corporate network security.