Pfsense Block access external Public FTP
-
To stay more clear I will connect the ftp out of this pfsense network with filezilla and see the log and post here if you can help me, ok?
thanks
-
yes!!! If you show me the logs from filezilla client - the full detail logs then we can figure out what is going on.
Give me a sec and can give you example of trying to connect to passive from a client and why there can be problems. And how the active works.
So for example here is connection to ftp.redhat.com
Status: Logged in
Status: Retrieving directory listing...
Command: PWD
Response: 257 "/"
Command: TYPE I
Response: 200 Switching to Binary mode.
Command: PORT 64,53,x,x,243,86
Response: 550 Permission denied.
Command: PASV
Response: 227 Entering Passive Mode (209,132,183,61,206,2)
Command: LIST
Response: 150 Here comes the directory listing.
Response: 226 Directory send OK.You can see both active connection and passive connection. I have the client give out my public so that is that 64.43.x.x and then the port would be 243x256 + 86 or port 62294
In the passive server says connect to it at 209.132.186.61 IP port 206x256 + 2 or 52738
If I don't tell my client to use its public IP you get this command.
Command: TYPE I
Response: 200 Switching to Binary mode.
Command: PORT 192,168,9,101,243,123
Response: 550 Permission denied.
Command: PASV
Response: 227 Entering Passive Mode (209,132,183,61,215,34)
Command: LIST
Response: 150 Here comes the directory listing.
Response: 226 Directory send OK.
Status: Directory listing of "/redhat/3scale" successfulSee that port is giving my machines IP 192.168.9.101 - that would never work and the server gave me a 550, so it switched into passive mode and the client switched to passive mode so it could connect to the server on the IP and port given.
-
Hello!
How are youhere is the log connecting ftp out of Pfsense network. I hope can see light to fix the rule.
Thank youStatus: Resolving address of ftp.datasus.gov.br
Status: Connecting to 189.28.143.164:21...
Status: Connection established, waiting for welcome message...
Response: 220 Microsoft FTP Service
Command: USER anonymous
Response: 331 Anonymous access allowed, send identity (e-mail name) as password.
Command: PASS **************
Response: 230 User logged in.
Command: SYST
Response: 215 Windows_NT
Command: FEAT
Response: 211-Extended features supported:
Response: LANG EN*
Response: UTF8
Response: AUTH TLS;TLS-C;SSL;TLS-P;
Response: PBSZ
Response: PROT C;P;
Response: CCC
Response: HOST
Response: SIZE
Response: MDTM
Response: REST STREAM
Response: 211 END
Command: OPTS UTF8 ON
Response: 200 OPTS UTF8 command successful - UTF8 encoding now ON.
Status: Connected
Status: Retrieving directory listing...
Command: PWD
Response: 257 "/" is current directory.
Command: TYPE I
Response: 200 Type set to I.
Command: PASV
Response: 227 Entering Passive Mode (189,28,143,164,21,249).
Command: LIST
Response: 150 Opening BINARY mode data connection.
Response: 226 Transfer complete.
Status: Directory listing successful -
@doguibnu said in Pfsense Block access external Public FTP:
Command: PASV
Response: 227 Entering Passive Mode (189,28,143,164,21,249).
Command: LIST
Response: 150 Opening BINARY mode data connection.
Response: 226 Transfer complete.
Status: Directory listing successfulyour connecting passive all is working fine there
-
Right,
This log is from out Pfsense network
How to configure the rule on PFsense to work inside pfsense?
I did try many times some rules configuration to pass this ftp
I do not know how to fix!Thanks
-
SOLVED
Steps:
Install FTP client proxy package
Go to Service - FTP client proxy
Click to Select Enable the FTP proxy
On Local Interface - Select Lan
Click SaveGo to Firewall-Rules-Wan
New Rule
Action: Pass
Interface: Wan
Protocol: TCPSource: Single host or alias
IP: IP ftp service
Source Port Range
From: 21
To: 249 (on my scenario)Destination: any
Destination Port Range
From: 21
to: 249Click on Save
Why port 249?
The log from filezilla on out Pfsense network show:
Response: 227 Entering Passive Mode (IP ftp service**,21,249**).Now its works fine
Thanks Johnpoz and all for attention and help
Douglas
-
No No No...
None of that has anything to do with any of it..
Talking to a public IP outside pfsense from a client inside pfsense using passive has ZERO need for any port forward or wan rule. While port 21 is the default control port of ftp. how you read passive command is WRONG..
Again I am going to ask have you even bothered to look at the link I provided on how ftp works..
Again your statement is completely wrong with how ftp works..
This statement
Passive Mode (189,28,143,164,21,249).Is telling the client to talk to IP 189.28.143.164 on port (21x256)+249 = port 5625
For a client to talk a ftp server outside pfsense from inside pfsense there is ZERO to do.. Since the client will create the connection to the server and the default rules on lan are any any.. Unless you have modified your lan rules from any any there is nothing to do to talk passive to a ftp server on the public internet from behind pfsense
For client to talk to server in active mode, then you need the ftp proxy package installed an setup. So that it can open the inbound traffic for the data channel to be opened.
-
@johnpoz said in Pfsense Block access external Public FTP:
No No No…
None of that has anything to do with any of it…
Talking to a public IP outside pfsense from a client inside pfsense using passive has ZERO need for any port forward or wan rule. While port 21 is the default control port of ftp. how you read passive command is WRONG…
Again I am going to ask have you even bothered to look at the link I provided on how ftp works…
Again your statement is completely wrong with how ftp works…
This statement
Passive Mode (189,28,143,164,21,249).
Is telling the client to talk to IP 189.28.143.164 on port (21x256)+249 = port 5625
For a client to talk a ftp server outside pfsense from inside pfsense there is ZERO to do… Since the client will create the connection to the server and the default rules on lan are any any… Unless you have modified your lan rules from any any there is nothing to do to talk passive to a ftp server on the public internet from behind pfsense
For client to talk to server in active mode, then you need the ftp proxy package installed an setup. So that it can open the inbound traffic for the data channel to be opened.I am sorry!
I do not what to do more.
Which your suggestion to configure in right mode?Yes I did read your link about the differences active and passive ftp.
I will again and againBut, inside PFsense, how to configure?
I will search more information about
Thanks you
-
there is NOTHING to configure in pfsense for client talking passive.. Nothing unless you modified the default rules to block ports? What are your current lan rules?
Only if your using active to talk to the server do you need the active ftp package helper.. From your log you were using passive and working..
Please post log of your client that is NOT working when behind pfsense and your LAN rules..
-
Hello!
Please, look at this link. He seems was the same difficult that me.https://www.experts-exchange.com/questions/28546035/Trouble-accessing-FTP-sites-via-pfSense.html
I think that I need to do a Lan Rule to pass on ports 20 and 21, right?
Other point:
On my filezilla log inside PFsense network also show me Grey color text (not green) after the wrong wan rule that you show me.
Can be the wayThanks
-
OMG... Dude did you edit the default lan rules away from any any?? If so then yeah your going to have problems. And your going to need more than just 21.. 20 would NEVER be used its a source port in active mode.
But the server in passive is going to give you some random high port to talk to... So post up a screen shot of your LAN rules!!!
I can not help you without some information.. How many times do I have to ask to see your logs? If your LAN rules are not any any then yes you need to show them.. I stated 3 days ago that if you had messed with your lan rules doing any blocking you could have problems with passive. If you would of read the link I gave you goes over what happens in the data channel... So if you are limiting lan to specific ports via rules other than any any then YES you going to have a bad day trying to ftp in passive mode.
That thread is from 2014... Yeah I will admit users have problems with ftp... Ftp should of been killed off 10 years ago.. It is NOT secure, it sucks through NAT, do I need to go on.. sftp is secure, its 1 port so no issues through nat. There are both free clients and servers for every OS.. There is ZERO reason to be still using ftp other than complete lack of caring on the point of the person running the server for security...
-
Hello
Here is my Lan Rules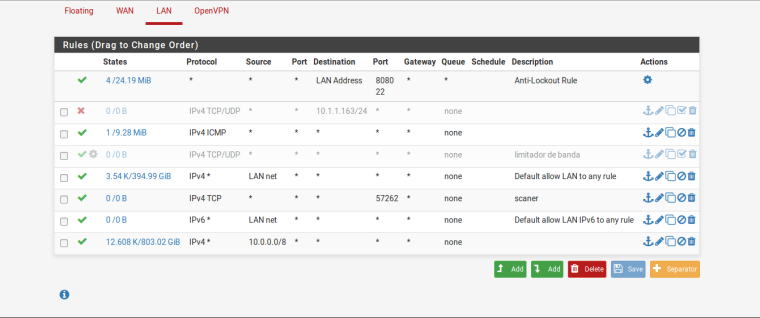
Yes, you right about sftp. I did read about it. But, I need to study how to server config and pfsense config. Then, enable sftp on our network.
But, remember, the Datasus FTP is external service that works with web service database. It is not our ftp server. Then, sad, but I need to do that works fine.I would like to thanks your patience and help until now.
Douglas
-
so you have downstream networks? Why do you have that 10/8 rule? And your icmp rule is any for source network would be pointless unless you have downstream networks.
And really is pointless anyway since you have 10/8 rule - unless you have other networks other than 10/8?
So if your client is on lan net or in 10/8 your rules are any any and should have no issues doing passive ftp to server outside.
Did you mess with outbound nat? Your using lan net as your transit to these downstream networks? Maybe you have a asymmetrical routing problem... Please draw up your network and where are you clients in your network that your trying to ftp with. Do they use pfsense as their gateway?
Your not routing any traffic through a vpn are you?
Do you have any rules in your floating tab?
BTW your scanner rule is pointless unless some downstream client is not in lan net or 10/8
-
@johnpoz said in Pfsense Block access external Public FTP:
hello
so you have downstream networks? Why do you have that 10/8 rule? And your icmp rule is any for source network would be pointless unless you have downstream networks.
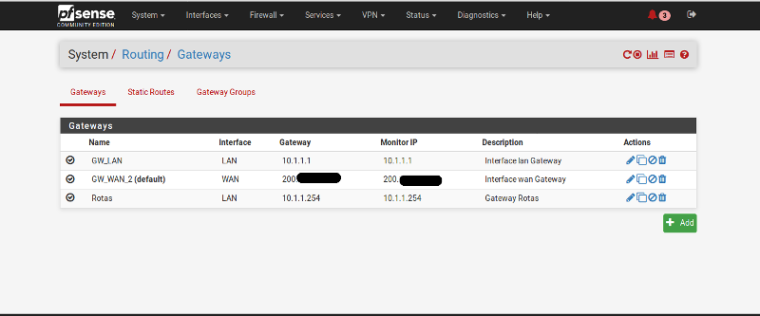
We have 43 networks point route inside pfsense:
For exemple:
10.10.11.254
10.10.34.254
10.10.29.254
10.10.30.254
.......
the internet is provide by:
concentrator Internet MPLS
Dedicated InternetAnd really is pointless anyway since you have 10/8 rule - unless you have other networks other than 10/8?
So if your client is on lan net or in 10/8 your rules are any any and should have no issues doing passive ftp to server outside.
Did you mess with outbound nat? Your using lan net as your transit to these downstream networks?
Yes, we are using lan net to transit on these downstream
Maybe you have a asymmetrical routing problem... Please draw up your network and where are you clients in your network that your trying to ftp with. Do they use pfsense as their gateway?
Yes, they are using pfsense for gateway. Each sector have modem (or circuit point) route to pfsense
Your not routing any traffic through a vpn are you?
We have some users access vpn through our pfsense because we have a NAS.
Do you have any rules in your floating tab?
No, there are not rule floating tab.BTW your scanner rule is pointless unless some downstream client is not in lan net or 10/8
Thanks for now
-
@doguibnu said in Pfsense Block access external Public FTP:
Yes, they are using pfsense for gateway. Each sector have modem (or circuit point) route to pfsense
So there are client in lan net.. Do you have host routing on them, if not then your asymmetrical if they are talking to any downstream network.
So if client in lan wants to talk to 10.x network he sends traffic to his gateway pfsense in the lan net. Pfsense then sends the traffic to some downstream router, the return traffic will not go to pfsense.
Please DRAW your network, and what what is your outbound nat rules. Is lan net also a 10.x address?
And again please post a LOG of filezilla client behind pfsense failing to connect... So we can see what gets sent in the passive command.
-
Hello
@johnpoz said in Pfsense Block access external Public FTP:
So there are client in lan net… Do you have host routing on them, if not then your asymmetrical if they are talking to any downstream network.
So if client in lan wants to talk to 10.x network he sends traffic to his gateway pfsense in the lan net. Pfsense then sends the traffic to some downstream router, the return traffic will not go to pfsense.
Please DRAW your network, and what what is your outbound nat rules. Is lan net also a 10.x address?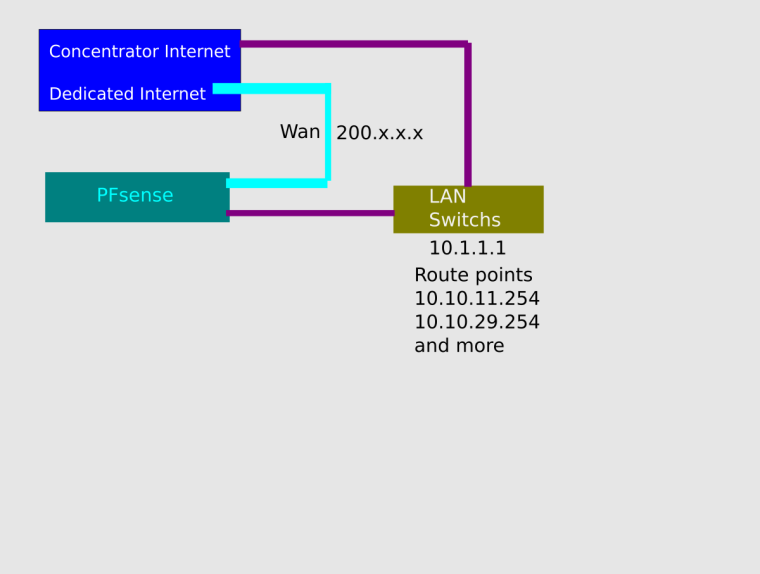
And again please post a LOG of filezilla client behind pfsense failing to connect… So we can see what gets sent in the passive command.
Here log of filezilla. I disabled that wrong wan rule that you tell me, and today now, look: (in grey text color)
Status: Resolving address of ftp.datasus.gov.br
Status: Connecting to 189.28.143.164:21...
Status: Connection established, waiting for welcome message...
Status: Insecure server, it does not support FTP over TLS.
Status: Logged in
Status: Retrieving directory listing...
Status: Directory listing of "/" successful........How today works?............
owwwww!!
Thanks
-
How it works today - because like I said there is NOTHING to do if your doing passive..
And you didn't show the detail log so can not see what the passive command was and or even if your doing active and the ftp helper package is doing the work for you.
So you have downstream networks. Then there should be NOTHING on your lan - it should just be a transit network.
edit: BTW these are normally never good news... What are you alerts/errors - looks like you have 3 of them.