VLAN tagging with untagged parent interface
-
Hi,
Let me start by saying this is the first time I'm configuring a pfsense firewall so please excuse any dumb questions or obvious issues :)
I'm running a pfSense as an edge firewall in a setup something like this:
ix1: INTERNET
ix0: Untagged LAN, currently assigned 10.0.1.1/24The ix0 interface goes to a HP switch with its port currently in access mode in vlan 2.
What I want to do is segment the inside networks into different VLANs whilst keeping the ix0 interface unchanged.
I did the following:
HP Switch: Change the HP switchport to a trunk allowing all VLANs and specifying vlan 2 as the native/un-tagged VLAN.
Pfsense: Add VLANs 10 and 20 , assign them ip addresses and send them out on interface ix0Now the setup looks like this:
ix1: INTERNET, DHCP
ix0: Untagged, 10.0.1.0/24
ix0.10 VLAN 10 tag, 10.0.10.0/24
ix0.20 VLAN 20 tag, 10.0.20.0/24The untagged ix0 is working fine but I cannot get the tagged subinterfaces to work.
I cannot see any MAC addresses in vlan 10 or 20 on the HP switch.I verified that the vlans are trunking from the HP to pfSense. and that the VLANs are created on the HP.
That leaves the pfSense.I keep reading that I have to restart pfsense to make the VLAN tagging work, is that correct?
Many thanks!
-
@b82rez said in VLAN tagging with untagged parent interface:
I keep reading that I have to restart pfsense to make the VLAN tagging work, is that correct?
Not that I know of. Configuring a VLAN is no operation that has to require a reboot to work.
I verified that the vlans are trunking from the HP to pfSense. and that the VLANs are created on the HP.
How did you verify, that the VLANs are trunking from the HP to pfSense? Do you have another client in one of those VLANs that you can test from to reach the VLAN interface on the pfSense side? Did you setup IPs, rules etc. on those new virtual interfaces in pfSense?
Greets
-
If it's been set up as you mention, it shouldn't be a pfSense issue,
To prove it do a packet capture in promiscuous mode on the parent interface, then import the capture into wireshark.
You should see untagged packets and tagged packets, create an extra column with vlan.id as the field.
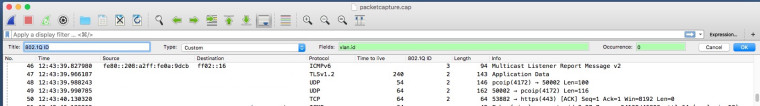
-
Where did you read that you have to reboot to get vlans to work? That is not true.
you can sniff on pfsense with tcpdump directly and the -e to see vlan tags.
-
@johnpoz said in VLAN tagging with untagged parent interface:
you can sniff on pfsense with tcpdump directly and the -e to see vlan tags.
tcpdump -i ix0 -e would do it
So you can :)
-
saves a step if all your doing is validating there is traffic being seen tagged and untagged, etc. ;)
-
Thanks for the fast replies!
Verify trunking on HP:
<sw001>display vlan 10
VLAN ID: 10
VLAN Type: static
Route Interface: not configured
Description: VLAN 0010
Name: VLAN-10
Tagged Ports:
Ten-GigabitEthernet1/0/27 <<--- PFsense
Untagged Ports: noneCaught the "Reboot to get the VLAN tagging to work" from various google searches, perhaps this is referencing an old release.
Just to confirm, it's a supported design to run IP ontop of the parent interface whilst tagging like I've done here?
I'll look at doing the capture also, thanks!
-
If you don't have untagged ports on that vlan, you can't connect dumb clients
-
@b82rez said in VLAN tagging with untagged parent interface:
Just to confirm, it’s a supported design to run IP ontop of the parent interface whilst tagging like I’ve done here?
I'd avoid it in the end to avoid debugging chaos with tagged or untagged traffic on the same interface, but yes it is working and supported. We run it like that at our office location, too. Untagged traffic (vlan1) is the old deprecated server network, all other new networks are using a proper VLAN and are tagged (or using a switch access port in the appropriate VLAN). So yes, that works.
-
@jegr said in VLAN tagging with untagged parent interface:
@b82rez said in VLAN tagging with untagged parent interface:
Just to confirm, it’s a supported design to run IP ontop of the parent interface whilst tagging like I’ve done here?
I'd avoid it in the end to avoid debugging chaos with tagged or untagged traffic on the same interface, but yes it is working and supported. We run it like that at our office location, too. Untagged traffic (vlan1) is the old deprecated server network, all other new networks are using a proper VLAN and are tagged (or using a switch access port in the appropriate VLAN). So yes, that works.
I do it and use it just for my LAN management subnet, switch management addresses, wireless controller & ap YMMV.
-
Yes I run parent native (untagged) with network 192.168.2 and then vlans on top of that parent interface with different networks .3 and .4 with vlan id 3 and 4, etc.
Derelict is sure not a fan of this sort of setup :) But yes it works just fine if you know what your doing and setup your switch ports correctly.
Partly this way because unifi AP until recently had to be untagged. And previous had network is place already that used untagged, and adding the vlans to this was easier than just tagging everything, etc.
I might get around to changing it - but it works no issue, it is a well supported configuration. It allows for being able to connect a device to that port without having to worry about the device support tags, etc.
-
It has its place. Unifi being one of them. It is always sort of a crap shoot how the connected switch will handle it but if it works it works. It has been a while since I saw a switch that didn't like it. I would still absolutely make the untagged VLAN on the switch something other than VLAN 1.
Another nicety is you can directly connect a laptop to the port and get to a network without having to worry about tagging traffic there. Handy for smaller networks.
Another consideration is if you run Diagnostics > Packet Capture on the parent interface, you get all traffic for all VLANs with the dot1q tags present on the tagged VLANs. This might or might not be what you want.
-
I can remember times when it was a no-go to mix tagged and untagged traffic on the same interface. I still cringe when I read about it ... but try to
 at least.
at least. -
@jahonix said in VLAN tagging with untagged parent interface:
I can remember times when it was a no-go to mix tagged and untagged traffic on the same interface. I still cringe when I read about it ... but try to
 at least.
at least.You'll find that's typical when VoIP phones and computers share the same cable. Same with WiF access points and multiple SSIDs.
-
@jknott said in VLAN tagging with untagged parent interface:
@jahonix said in VLAN tagging with untagged parent interface:
I can remember times when it was a no-go to mix tagged and untagged traffic on the same interface. I still cringe when I read about it ... but try to
 at least.
at least.You'll find that's typical when VoIP phones and computers share the same cable. Same with WiF access points and multiple SSIDs.
Exactly. One of the corner cases, where other solutions aren't workable (at least not with a single wire solution) ;)
But even if client ports are configured that way, one is still a bit cleaner in configuring the upstream port to pfsense as trunk with VLANs only. But that's just IMHO :)
-
@jknott said in VLAN tagging with untagged parent interface:
You'll find that's typical when VoIP phones and computers share the same cable.
Do I sound as if I needed this explained?
Being able to remember the distant past but not 5 minutes ago is called Morbus Alzheimer. My mom suffers from it badly.Same with WiF access points and multiple SSIDs.
Buy serious wireless APs with all traffic tagged, not consumer gear on steroids.