Bug: Problem with schedules that go over to the next day
-
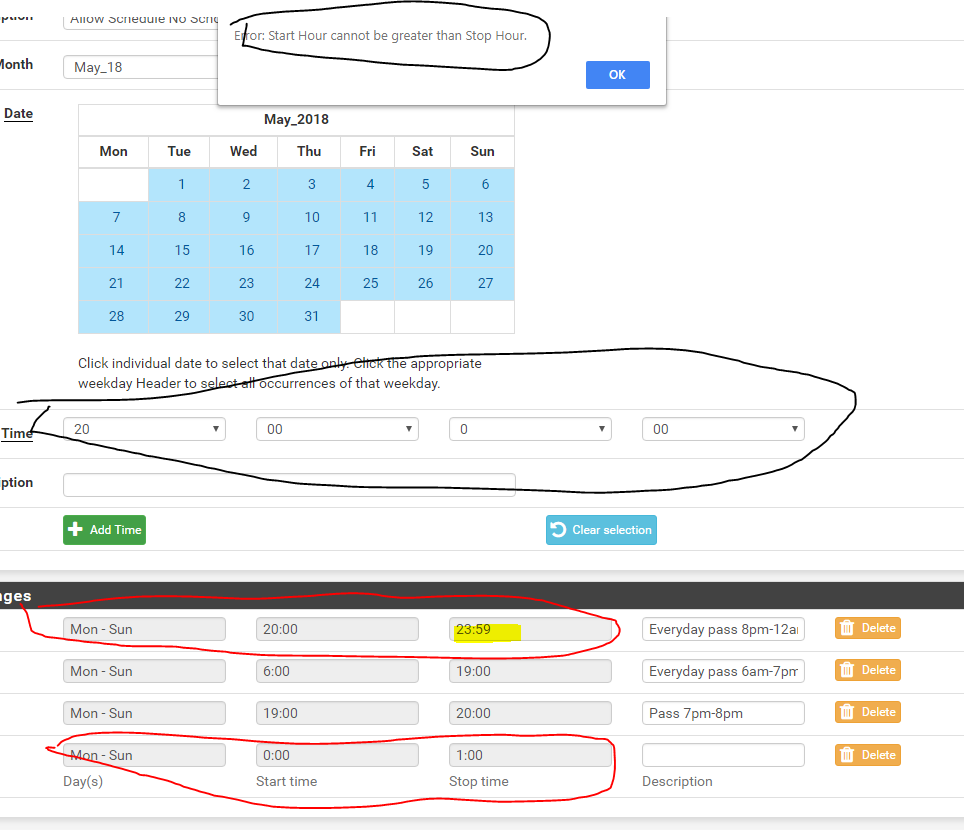
Hi all, i have a schedule setup for my kids xbox. It all works but there is a problem when the schedule runs into the next day there is a 1min period where you cannot have an allow schedule.
for example from 8pm to 1am i want them to have internet access but because of the Bug "Error:Start Hour cannot be grater than Stop Hour" i cant create a scheduled from
20:00 - 1:00
20:00 - 0:00it forces me to schedule 20:00-23:59 then have to schedule 0:00 - 1:00 but there leaves a 1min period where it will drop traffic.
I'm open to suggestions. thanks for your time.
-
Block from 1am til 8pm instead.
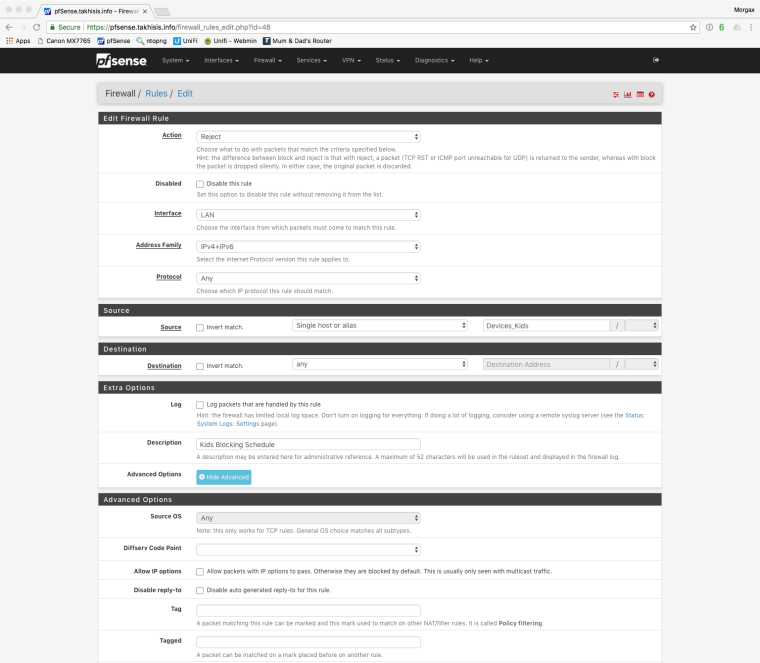
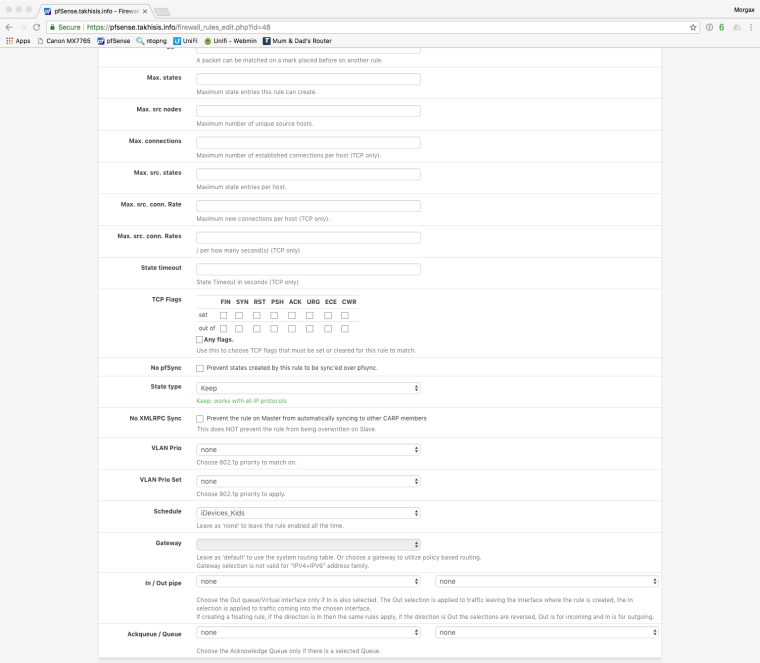
Here is how I do my schedule, with a blocking firewall rule on LAN. So they only have access 8am till 9:30pm school nights, 8am till 10:30pm weekends.
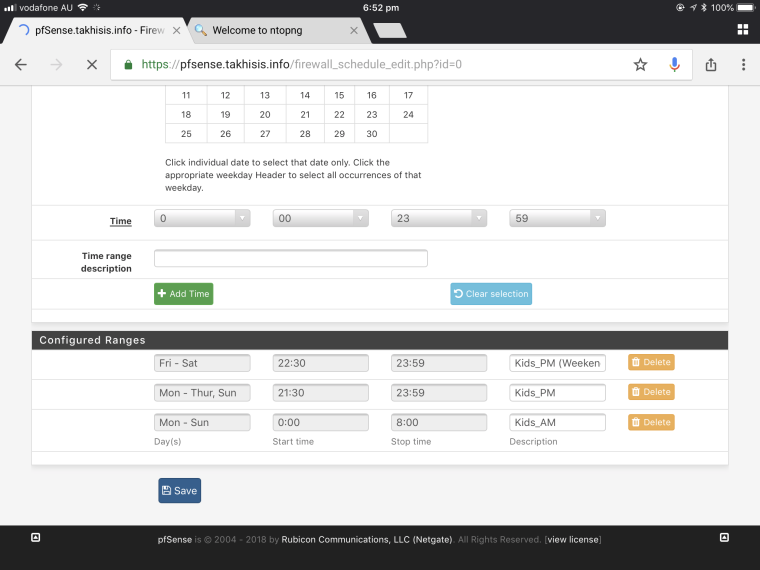
-
Can you post a screenshot of your LAN rules for this schedule? I'm trying to restrict my kids access in a similar way but I think my rules are the problem.
Thanks much
pp -
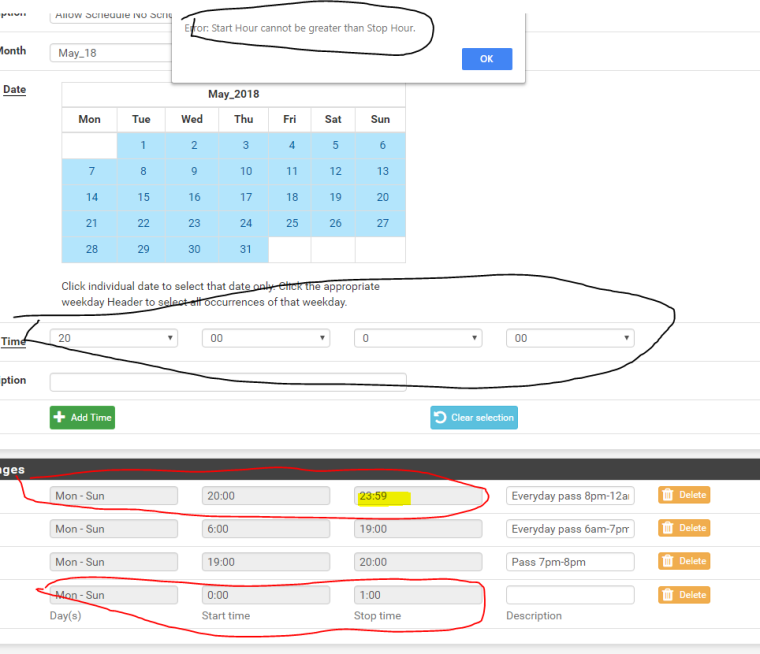
Rules cannot span midnight. It is not a bug.
Make a rule that stops at 23:59 and another from 00:00 to 01:00
-
-
@derelict said in Bug: Problem with schedules that go over to the next day:
Rules cannot span midnight. It is not a bug.
Make a rule that stops at 23:59 and another from 00:00 to 01:00
can this not be change? its blocking internet access for the 1 minute gap/span
-
I've complained about this years ago and nothing has changed. The scheduler is clumsy and clunky. The redo of WebGUI didn't help it at all. I have no idea why it's so primitive. With other firewalls that I use, I can easily create a rule with a schedule that spans midnight or different days and apply it within the rule creation screen. No need to hop around creating multiple schedules and then multiple rules that link to the different schedules.
-
@morgion: thanks for the screenshots. I am using a block rather than a reject...perhaps that's my issue.
Here's a screenshot of my LAN rules. the SeboGroup is a collection of of IPs that I want to limit to a specific time range (6AM-11:59PM). As you can see I have another rule for "not" SeboGroup (all other devices) that is not limited to a schedule. Should I disable the default allow LAN rule?
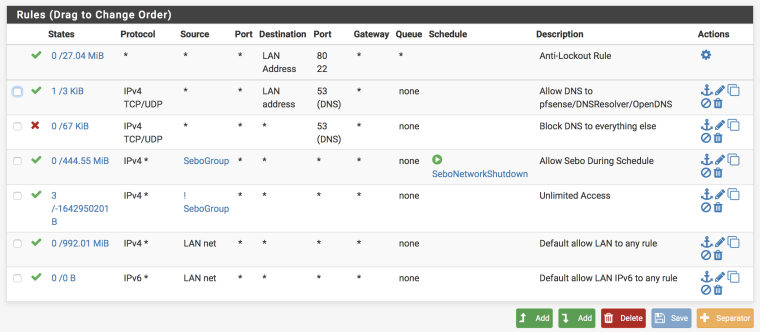
-
mine is setup as a block on the lan.. then above it i have an allow with the schedule chosen.
-
Thanks much for your quick reply ;)
So like this? (Note that the rule below the "Allow Kids During Schedule" rule is disabled):
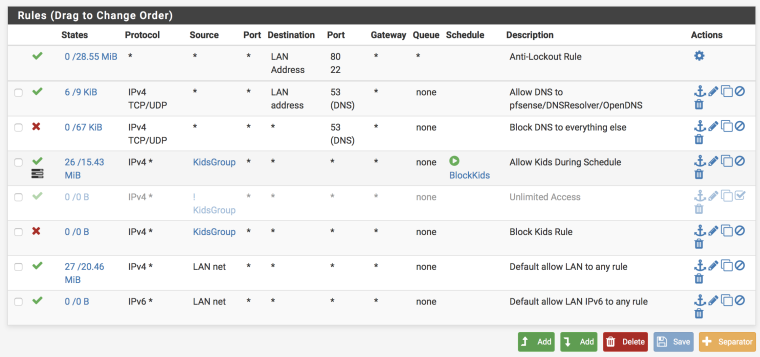
-
looks good
-
Thanks. BTW do you use Cron to fire off pfctl -k using these rules?
I've been trying for a few days to use allow rules only:
allow kidsgroup during scheduled time
allow !kidsgroup alwaysAfter setting these rules I killed all states for IP's in the kidsgroup...but no dice. I thought the preferred methodology with pfsense 2.3.x was using allow vs. block rules since block rules don't kill states?
Thanks again
PP -
Try this:
Pass kidsgroup schedule
Reject kidsgroup
Pass anyDon't block traffic with pass ! rules.
-
lets not derail the 1min of neither that cannot be in a pass/block schedule
-
@ppmax Sorry I didn't get back to you, I've been very busy that last few days.
I thought the preferred methodology with pfsense 2.3.x was using allow vs. block rules since block rules don't kill states?**
Didn't know this one, going to change to this to see if it helps with the Kill States.
-
There are no states to kill on a scheduled block rule because no states are created by block rules.
When a block rule schedule fires there is no way to know what states to kill.
When you have a scheduled pass rule that expires, all of the states that have been created by that rule are tagged so there is something to key on to kill the states created by that rule when the schedule expires.
-
That makes sense, thank you
-
I've been searching around for the answer to the one minute outage for rule application between 23:59 and 00:00. In my pfSense 2.4.4 setup, I've disabled the default allow all rule and I'm using allow rules for access (based on other guidance I've seen related to states referred to in this post as well). I have two groups of IPs, restricted and unrestricted. I have the restricted group set for 05:00-23:59, 00:00-01:00. The unrestricted group is set for 00:00-23:59. Everything loses access for the one minute between 23:59 and 00:00. Is the only answer to go back to block rules with some sort of cron to kill states (although I've not seen a definitive answer that this will work either)? That seems a bit overly complicated to achieve something so simple. Sorry if this has been solved somewhere. I just haven't been able to find it.