Understanding better the firewall rules
-
Again rules are evaluated TOP down, first rule to trigger wins.. NO OTHER rules are evaluated... So yes if you want to block access to something on the internet you would need to put it above some rules that says any to the internet.
Invert match is exactly that, I have mostly used them in destination rules.. They have nothing to do with inbound vs outbound on the traffic flow. The only way to do outbound rules is in the floating tab - and I would suggest you stay away from there until you fully up to speed on how to do normal rules on the interfaces themselves. You should only need floating rules if your doing something tricky.
Lets say you wanted to allow your dmz segment to go everywhere but not your other segments. So anything on the internet is fine.. So you could block specifically dest rfc1918 space above your any any rule.
Or you could have your allow rule say dest ! rfc1918, or not rfc1918 or inverted rf1918 all the same thing. Which is like saying hey as long as your not going here, its allowed but if dest is rfc1918 then rule would not trigger and wold hit the default deny rule and not go anywhere.
These can be tricky, and they can have issues with how the rules are evaluated. I would not suggest you use such rules unless your sure 100% what your doing, and then validate its working as expected.. These are more advanced sort of rules..
I would suggest if you want some network segment to not go somewhere then put in a specific deny to where that something is above where you allow to the internet with any any rule.
-
@johnpoz hello
I don't know if I am doing this right!!!!
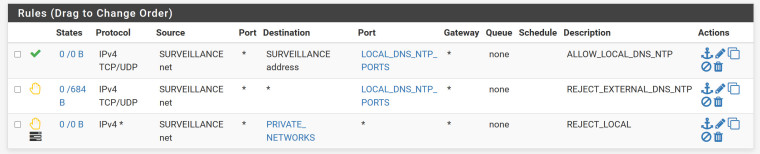
Let me explain what I need and what I have make sure I don't need
I need all the cameras to hit the pfSense interface for DNS 53 and NTP 123
What I want to make sure 1st they cannot access the pfsense web gui on ports 80,443 and ssh to 22. 2nd each cams are not aware of other hosts on it's network or any other netowrk
They will be controlled from a software on the mgmt netowork,so all I need is to resolve and get the time's rightThank you
-
@xlameee said in Understanding better the firewall rules:
2nd each cams are not aware of other hosts on it’s network
This has zero to do with pfsense. Your going to need a switch that can to private vlans for that, or if wifi then set AP to isolate clients. Different makers call it different things.
What is below that.. I don't see any allow rules - is there an allow rule for any so they can use the internet? What is in your aliases?
But from your descriptions sure that would allow access to dns and ntp on the pfsense surv IP. Then block/reject anywhere else those ports.
Then if your private networks alias includes all rfc1918 space or your other networks it would block access to those. But if you have say an any any rule below that, then it would be possible to hit the web gui on your wan IP.. Which you would assume would be public.
If you do not want stuff to get to stuff on firewall, then you should use the "this firewall" dest built in alias which would include all pfsense IPs, lan, optX, wan, etc.
-
@johnpoz alias PRIVATE_NETWORK RFC1918
alias LOCAL_DNS_NTP_PORTS ports 53 123
No dont want them to access internet
Isn't is pfSense have an built in firewall rule DENY ANY to All until PASS traffic rule is in place -
yes there is a default deny for sure.. So if you do not have an allow below that then your fine other then the rule would allow your camera to hit your web gui via the wan IP address, unless it is also a rfc1918 address.
Most the time the wan IP is public, user tend to forget this when doing rule.
But if you do not have any allow rules, what would be the point of the cam being able to do dns? Other than say looking up stuff on its own network, but you stated you didn't want the cam even knowing about other devices on its own network. So having a hard time understanding the point of allowing dns?
-
@johnpoz I want them to resolve so when I configure them or adding them into the software I can use their hostnames not an IP addresses I have lots of stuff on my networks and I am an one men show here my head kind of messed up sometimes :) I can remeber them as names but hard time remembering 30+ segmentation over 3 locations :) as an IP addresses
-
That has ZERO to do with them talking to dns.. Are you saying they are registering their dns entries?
If you want to be able to resolve them by name, setup reservations or just put in host overrides.. Only if you were having the devices themselves register in dns would you need to allow them to talk to 53.. Which I find unlikely for camera's to do.
-
@johnpoz I ahve most of my network with static mapping in the unbound of pfsense
-
Great - again then allowing your cameras to talk to 53 has ZERO to do with YOU resolving them by name.
-
@johnpoz Aren't they have to have access to port 53 or actually yes yes I understand .... My host need to have an access to port 53 because I am sending request not the camera it self. So what rules do you suggest to have so I can keep them isolated and off the internet I have to create 1 rule on the top allow OPT net to OPT address or (Firewall it self)on port 123 and on the bottom REJECT OPT net to ANY and log it. Will that do the job?
-
Allow them to sync ntp, guessing they put timestamps on their video right. Then yeah block them from doing anything else and sure log it so you can see what they are trying to do. Prob phone home most likely to china ;)
-
@johnpoz Yap !! That's what I did and it is working perfectly thank you