snort (SID 43687) blocks root DNS servers ?!
-
-
@chudak said in snort (SID 43687) blocks root DNS servers ?!:
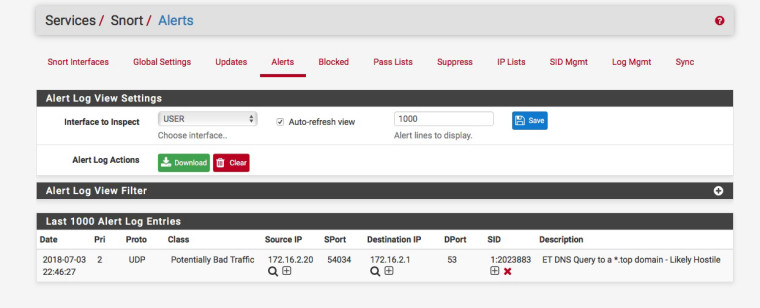
I don't see anything yet on LAN, all only on WAN.
Let's wait :)
-
-
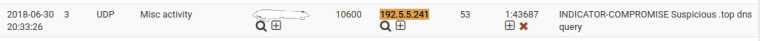
f.root-servers.net = 192.5.5.241 guessing thats from your WAN interface.
Or your hosts directly query f.root-servers.net
-
@chudak said in snort (SID 43687) blocks root DNS servers ?!:
43687
Err that rule by default is default disabled:-
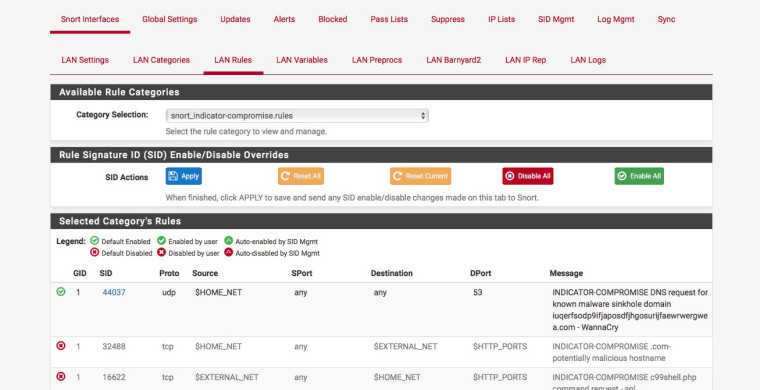
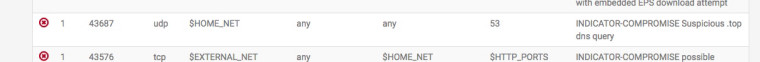
Maybe your being a bit over zealous with enabling the rules :)
The two rules do differ slightly as well:-
INDICATOR-COMPROMISE:- alert udp $HOME_NET any -> any 53 (msg:"INDICATOR-COMPROMISE Suspicious .top dns query"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|03|top|00|"; fast_pattern:only; metadata:policy max-detect-ips drop, policy security-ips drop, service dns; reference:url,en.wikipedia.org/wiki/.top; classtype:misc-activity; sid:43687; rev:2;) Emerging DNS:- alert udp $HOME_NET any -> any 53 (msg:"ET DNS Query to a *.top domain - Likely Hostile"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|03|top|00|"; fast_pattern; nocase; distance:0; threshold:type limit, track by_src, count 1, seconds 30; reference:url,www.symantec.com/connect/blogs/shady-tld-research-gdn-and-our-2016-wrap; reference:url,www.spamhaus.org/statistics/tlds/; classtype:bad-unknown; sid:2023883; rev:1; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, signature_severity Major, created_at 2017_02_07, updated_at 2017_02_07;) -
@nogbadthebad
that could be and is an answer to the initial question, alto I don't recall changing rules until recently I saw my network being blocked -
.tk domains too :)
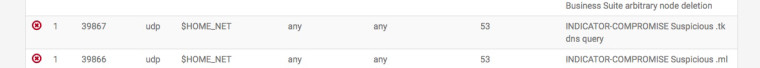
-
You can add "top" and "tk" to the DNSBL TLD Blacklist which will prevent these alerts since the DNS request will never be answered for those TLD Domains.
-
That’s interesting, added, thx
-
@bbcan177 would it make sense to black list all top domains listed here https://www.spamhaus.org/statistics/tlds/ ?
-
@chudak said in snort (SID 43687) blocks root DNS servers ?!:
@bbcan177 would it make sense to black list all top domains listed here https://www.spamhaus.org/statistics/tlds/ ?
Its not a one-size-fits-all... Most of those TLDs most users will never need to access, so I would see little issue. There is also the TLD Whitelist, where you can allow some specific domains thru that are being blocked via TLD Blacklist.
There is also this TLD list: http://toolbar.netcraft.com/stats/tlds