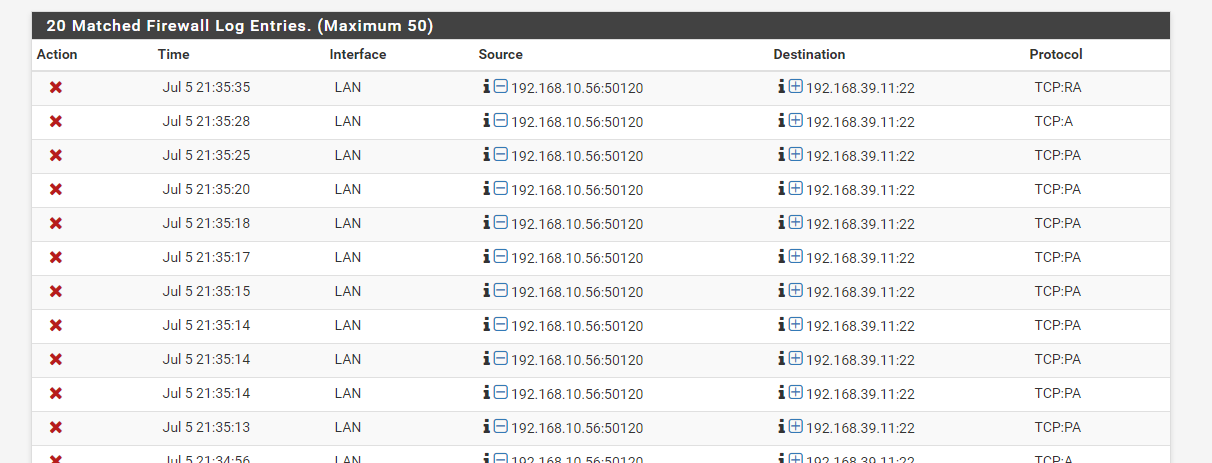
TCP:RA, TCP:A, TCP:PA blocked ?
-
Hi Guys,
I have an pfsense box with 3 NICS. WAN,LAN and DMZ. The traffic works as intended, and so does the rules. But after some time, I get disconnected (LAN->DMZ traffic), with TCP:RA,A,PA showed in the firewall logs in pfsense.
From WAN -> DMZ I have no issues...
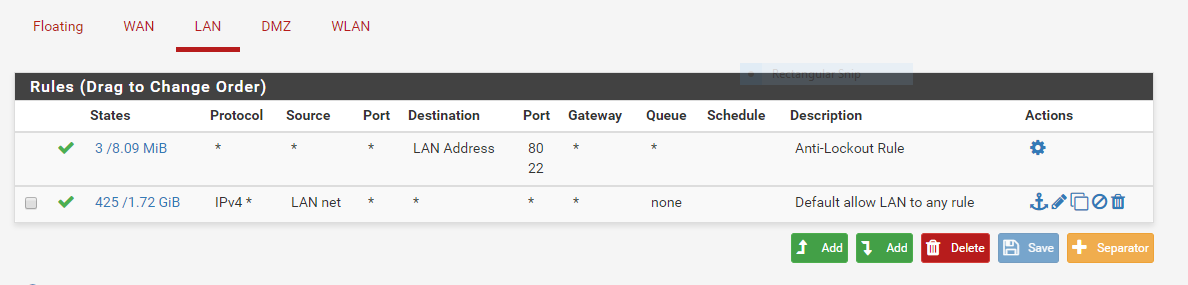
Rules LAN
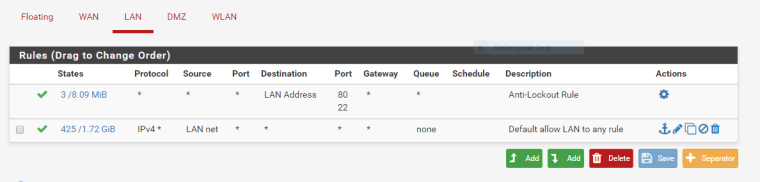
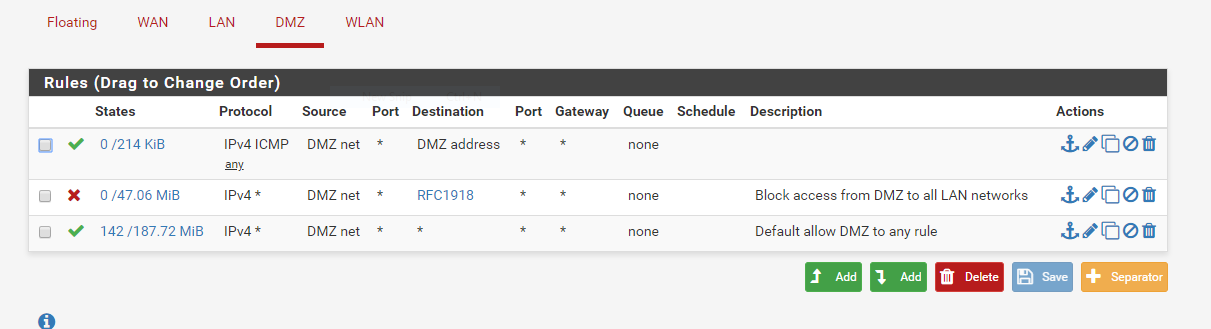
Rules DMZ
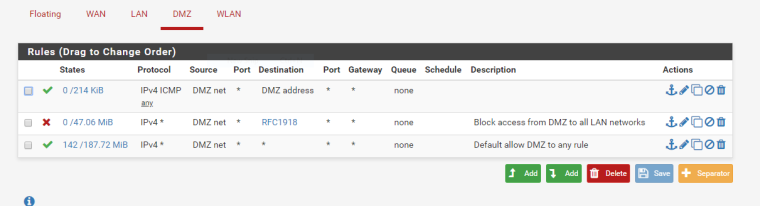
I've tried to set the firewall options to conservative, like described here, with not much luck: https://knowledge.zomers.eu/pfsense/Pages/How-to-solve-connectivity-issues-with-dropped-RA-and-PA-packets.aspx
-
Those sorts of blocks are normally a sign of asymmetrical traffic.
Or you could have dupe packets... You understand that first hit you show is RA, or RESET ACK... This basically the client saying F OFF done.. FA would be way to normally close a tcp session. But RA is can be seen sometimes depending on how the client/application is designed..
Are these devices wireless?
Once a state is closed, then yeah any other packets that are not SYN would be blocked. A firewall only creates a state with the start of a conversation.. Ie the handshake syn, syn/ack
So if firewall sees Fin and closes the state, then any other packets still being seen would be out of state and blocked.
https://www.netgate.com/docs/pfsense/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html
How exactly do you have these networks wired? Are they physical isolated with different switches, do devices use different gateways than pfsense IP? Are you using a dumb switch to try and isolate your vlans - maybe you have your vlans on your switch misconfigured and are running multiple layer 3s on the same layer 2?
-
Hi,
Thanks for the reply.No its not wireless devices. Actually the wireless devices seams to work fine. the issue seems to be only with wired devices.
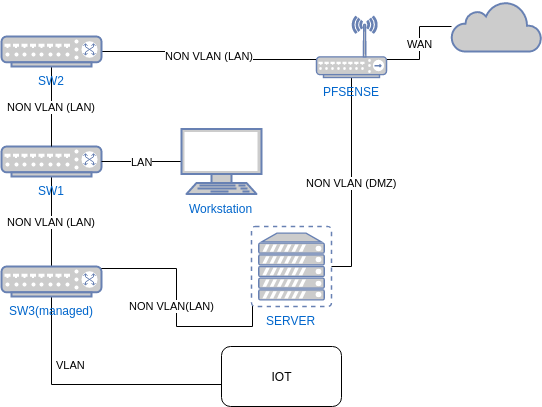
The network look like this.
Switch1 - Unmanaged
Switch2 - Unmanaged
Switch3 - ManagedPFSense has 3 NICs, (and a WLAN). WAN,LAN,DMZ.
PFSense(DMZ)<->Server(DMZ)
PFSense(WAN)<->Internet
PFSense(LAN )<->Switch2, for switch it spans to further switches.Workstation<->Switch1<->Switch2<->PFsense(LAN)
Switch1<->Switch3<->Server(LAN) -
If you wan tto work with vlans then you need a smart switch... Your dumb switch can be downsream of your smart switch and then all devices on those dumb switch would have to be on the same vlan..
Your switch 3 needs to be directly connected to pfsense and you can run vlans on those ports, then downstream from switch 3 you can put your dumb switches on any vlan you want.. But all devices on that dumb switch will be on the same vlan.
-
Yes im aware, and thats really not the case. I only use the VLAN for IOT, so its still kinda a mystery to be why this happens. Maybe it would help if I enable "Bypass firewall rules for traffic on the same interface" ?
The network look like this.
So if I go to the DMZ interface to the server, from the WS. (WS->SW1->SW2->PFSense->Server), I will get disconnected suddently, with the error from the first post.If I go to the LAN interface on the server, I will not have this issue (traffic should never go through PFSense in that case. (WS->SW1->SW3->Server).
-
You can not do that... And you have your server connected to 2 different networks.. Both with default routes I take it.. So you talk to server from lan to dmz.. He talks back via his lan connection. ASYMMETRICAL!! Now you have problems with states on the firewall.
How exactly is that IOT stuff being on a vlan? Doesn't work that way..
Is your sw3 L3 and routing? If so then your lan needs to be transit network and not have hosts on it.. Because how do they get to the vlan network without talking to their gateway on pfsense? Which causes hairpin and asymmetrical traffic, etc.
-
Oh, I see! Thx!
There is only 1 route configured on the server (default route), which is towards the LAN connection..
I thought it would take the same route back it came from, unless an route told it otherwise. :) -
@lbm_ said in TCP:RA, TCP:A, TCP:PA blocked ?:
Oh, I see! Thx!
There is only 1 route configured on the server (default route), which is towards the LAN connection..
I thought it would take the same route back it came from, unless an route told it otherwise. :)Every node in a network does their routing 100% autonomously without consulting anyone else and routing is always stateless meaning there is no memory of the previous packets that arrived or if they were part of an active connection or not.
-
Even if you have only 1 default route. When I see traffic from 192.168.x and I have an an interface in 192.168.x - then that is where you respond with.
-
@johnpoz said in TCP:RA, TCP:A, TCP:PA blocked ?:
Even if you have only 1 default route. When I see traffic from 192.168.x and I have an an interface in 192.168.x - then that is where you respond with.
Thx, it makes sense. :)
Are there any way to solve this ? Its not an big issue at all, im just curious.
-
S serbus referenced this topic on
-
S serbus referenced this topic on
-
S serbus referenced this topic on
-
S serbus referenced this topic on
-
E Elmojo referenced this topic on
-
E Elmojo referenced this topic on
-
 B bingo600 referenced this topic on
B bingo600 referenced this topic on