pfSense CA & FreeRADIUS 3 configuration problem for Wireless WPA2 Enterprise EAP-TLS device authentication
-
Hi,
I am trying to use pfSense to support EAP-TLS with WPA2-Enterprise (machine/device authentication, not user authentication) for wireless clients using FreeRADIUS and pfsense CA on my existing working pfSense instance. I believe I have configured everything correctly using a range of documentation and guides, but my initial testing with a standalone Windows 10 client is not going well. In future I also need to add Android and Apple IOS devices but want to get the Windows 10 clients working to prove the basic configuration before I go any further. I'd really appreciate any advice on where I am going wrong and have summarised below the steps I've followed, important bits of configuration and windows event log error entry:
Main components:
pfSense (2.4.3)
Freeradius 3 package
pfSense Certificate Authority
Cisco enterprise access point
Windows 10 Professional clientConfiguration Process:
-
Existing working pfSense - Added FreeRadius3 package
-
Created a new pfSense CA
- 2048bit
- sha256
- common name: internalRootCA
- Created a new certificate for freeradius
- 2048bit
- sha256e
- common name: radius.domain.local
(I went with this naming convention to support a future move to an internal domain - was this an incorrect decision ? I've replaced the real domain name with domain.local for the purpose of this internet post)
- Created a new certificate for the Windows 10 Professional Client
- 2048bit
- sha256
- common name: client001
- subject alternative name: client001
- Freeradius configuration:
-
NAS/Clients
- Added a entry for the Cisco Enterprise Wireless Access point
- Shared secret etc
- Most settings left default
-
Interface
- Created a new interface for the Cisco Enterprise Wireless Access point to use
- Most settings left default (Type - Authentication, Port 1812 etc)
-
Settings
- Left default
-
EAP
- Disable weak EAP types - Yes
- Default EAP type - TLS
- Ignore Unknown EAP Types - Yes
- Certificates for TPS:
- SSL CA Cert - internalRootCA selected
- SSL Revocation List - internalRootCA Revocation List selected
- SSL Server Certificate - radius.domain.local certificate selected
- EAP-TLS
- Left default
- All other settings default
-
Users
- None/Blank
-
Configured Cisco Enterprise wireless access point to use the freeradius server with shared secret and created a SSID with WPA2 Enterprise.
-
Exported the CA root certificate and imported into 'Trusted Root CA store' on the Windows 10 Client.
- I also created a certificate from this CA for the pfSense web interface using this root CA and tested that the Windows 10 client is successfully trusting the root CA certificate i.e. no certificate trust errors in the web browser when accessing the web interface.
- Exported the Windows 10 Desktop Client and imported into the 'Certificates - Local Computer - Personal Store'
I have checked the Microsoft 'Certificate requirements when you use EAP-TLS or PEAP with EAP-TLS' document and believe the configuration and details in the certificates meet these requirements. The only requirement I was unsure of was:
- 'The Subject Alternative Name (SubjectAltName) extension in the certificate contains the user principal name (UPN) of the user'.
- I want to do device/machine based EAP-TLS authentication therefore with no 'user' involvement. I believe Apple IOS devices may do this slightly differently and supply certificates in a user context which may require further configuration, but for now I'm focussing on Windows 10 device/machine authentication.
- Windows 10 Wireless network configuration
- Created a manual wireless network profile
- New SSID
- WPA2 Enterprise
- Authentication Type - Smart Card or other certificate
- Use a certificate on this computer - Use simple certificate selection
- Validate the server's identity by validating the certificate with the 'pfSense internalRootCA' certificate selected
- Advanced Settings - 802.1x settings
- Specify authentication mode - Computer Authentication Only
Testing results:
- When the Windows 10 client attempts to connect there are no errors/entries in the pfSense Freeradius logs - there are no entries to show any attempted authentication request. The Cisco Wireless Access point show the initial wireless client assocoation but shortly afterwards a disassocition. Finally the Windows 10 event log has the error below - my current assumption is that Windows is either expecting a different client certificate to use to authenticate, not happy with the client certificate I created or for some reason it is ignoring the client configuration to do 'Computer Authentication only' and not finding a certificate in the 'user' store.
Windows 10 Professional Event Log - WLAN-Autoconfig Failure entry when attempting to connect to the wireless network.
<Log START>
Wireless 802.1x authentication failed.Network Adapter: Network Controller
Interface GUID: {xxxxxx}
Local MAC Address: xx:xx:xx:xx:xx:xx
Network SSID: [NEW WPA2 Entperise SSID]
BSS Type: Infrastructure
Peer MAC Address: xx:xx:xx:xx:xx:xx
Identity: host/client001
User:
Domain:
Reason: Explicit Eap failure received
Error: 0x40420110
EAP Reason: 0x40420110
EAP Root cause String: Network authentication failed due to a problem with the user accountEAP Error: 0x40420110
<Log END>I hope all the above information is useful and really appreciate any advice on what is going wrong.
Thanks,
Stuart. -
-
@stuartuk said in pfSense CA & FreeRADIUS 3 configuration problem for Wireless WPA2 Enterprise EAP-TLS device authentication:
common name: client001
subject alternative name: client001I have been running eap-tls with freerad on pfsense for years. Can tell you from that is wrong.. Did you change that from the actual FQDN?
example: here is my wife's laptop authing to wireless with eap-tls
Jul 12 12:57:43 radiusd 94585 (2073) Login OK: [k-laptop] (from client uap-pro port 0 cli 74-DA-38-55-9A-FE) 192.168.2.2
-
Hi John,
Thanks for your reply, I'm glad to hear it should pretty much work out of the box and really appreciate your help with the problem.
To answer your question I did change the 'domain' to 'domain.test'. If I remember correctly the default pfSense install has 'localdomain' in the domain field ?
I've done some further testing this weekend and other than a small configuration change on the Windows 10 client I was able to get EAP-TTLS working. This suggests there is not a problem with the pfSense/Freeradius CA certificate and that the Windows 10 client was able to verify that certificate. If the Windows 10 client is happy with the CA certificate it would suggest the problem when using EAP-TLS is with the actual client/device certificate but I don't know why :) I am suspicious it is something I am doing wrong when filling in the certificate details for the Windows 10 client and Windows can't 'find' the correct certificate to use even though it was signed by the pfSense CA. I have listed below the main details of the certificate visible in Windows which I imported into the 'Local Computer\Personal\Certificate' store on the Windows 10 client.
Certificate Field - Subject:
OU = DOMAIN LOCAL
CN = COMPUTER001
E = COMPUTER001
O = Domain Local
L = GB
S = GB
C = GBCertificate Field - Subject Alternative Name:
DNS Name=COMPUTER001
DNS Name=COMPUTER001.DOMAIN.LOCALCertificate Field - Friendly Name:
COMPUTER001Would you be able to tell me what you have used for your equivalent certificate fields above relative to the client machine name and whether you are using the default pfSense Domain ? From our example log entry, is the Windows machine name of your wife's laptop 'k-laptop' and did you import the client certificate into the local machine certificate store or user certificate store ?
Thanks again,
Stuart. -
Your cert fields not going to be a problem - the type of cert would be..
Here easier to show the freerad server cert and the client (my iphone) cert since they are at the top
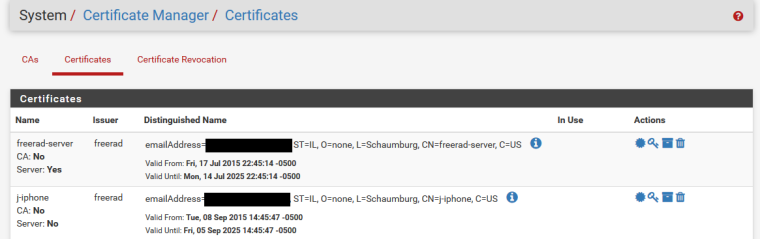
Your problem with windows is not going to let you install the cert without a password. Which the gui doesn't allow you to do.. You have to put a password on your cert. I just use openssl.. There are multiple threads about it. But if you want can screenshot my settings, and then run through putting a cert on my windows 10 desktop and authing with it.
-
Hi,
Did you eventually solve this? I am trying to do the same and gathering some information at the moment.
thanks in advance