DNS FOR VPN
-
@teknikalcrysis - thanks for the reply and info.
I will try again this upcoming weekend. Hopefully I get it this time.
I am 100% sure that the do not pull routes option is unchecked under my VPN client settings. I will double check though.
i was referring to the both the NAT > Outbound DNS Rule and the NAT Port Forward redirect rule. -
NAT>Port Forward
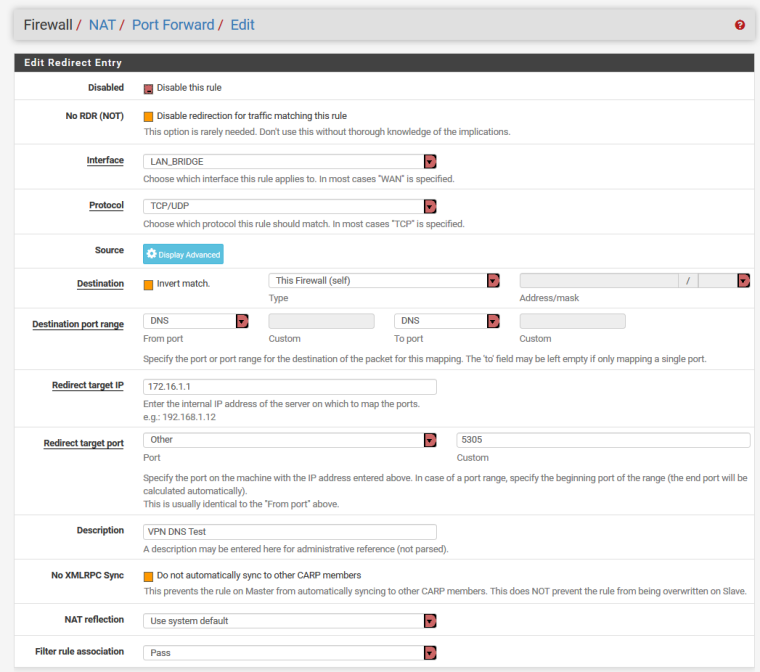
This will redirect DNS (for specific devices if you define the Source) from the LAN on port 53 to Port 5305 on pfSense, make sure you change the DNS Forwader port to 5305 as the Resolver uses 53 and you need that the sameNAT>Outbound
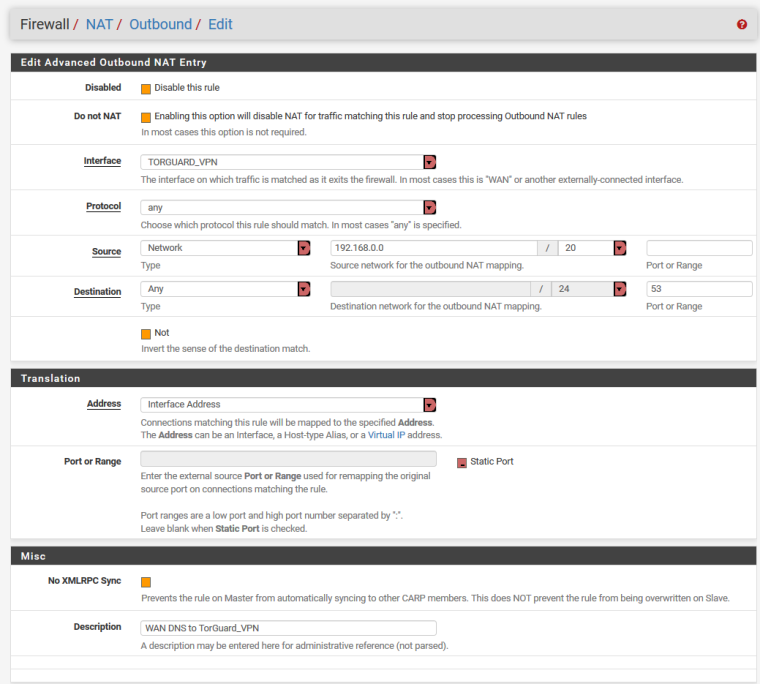
On the NAT>Outbound DNS rule, you might need to tweak it a bit to work for you...I have the source net work address set to its WAN network because its resides behind a second router of 192.168.#.#
You might need to change the source to ANY -
Hi Teknikalcrysis - apologies for replying until now but it had been busy these past couple of weeks, I only was able to work on this today. Unfortunately, it did not work, I tried to do everything as you indicated, the VPN works but I can't for the life of me figure out why the DNS leaks.
I tried the first method and then the second unbound and forwarder.
I don't have enough time these days with work and life in general (kids), things to do around the house to spend a good chunk of time on it unfortunately. I thank you for your help.
I think I will leave it as is. Good thing I had a backup to revert back :)I think I will look down the road for a good guide to show me step by step, hopefully, one will exist.
Thanks again,
OXIB. -
@OXIBQUIEH
have you tried going into the DHCP server on pfSense and assigning static mappings and then specifying specific DNS servers for each static mapping? -
@OXIBQUIEH
... Just a side comment on your DNS path to resolving, I didn't see it mentioned already;If you are using a Windows DC and DNS, have your clients point to that server first.
Then set the Windows DC/DNS server recursion to the local PiHole on your network.
Next set your PiHole to recurse out the the internet/VPN/etc. It works much cleaner and the Windows systems on your network will thank you for it.[host]----->[WindowsDC]----->[PiHole]-------{VPN tunnel}-------->[Pubic/Provider DNS service]
If you are using a IP based vpn provider, you can just point everything to that DC or Pi (incl pfSense). If the provider uses DNS name for its VPN server, then you may be able to set the pfsense DNS to your local provider/ISP, then everything else to those internal DNS servers.
-
@teknikalcrysis
Hi,
I have static mappings for all my devices. I only have the PIHOLE set as the DNS server for all the devices. That's what blocks ads on all of the devices. -
@philw
Hi Philw,
Thanks for your input.
If I have the Windows DC and DNS point first for the clien'ts, won't that make the PIHOLE unable to block ads?
When you say recursion - you mean the Forwarders tab?
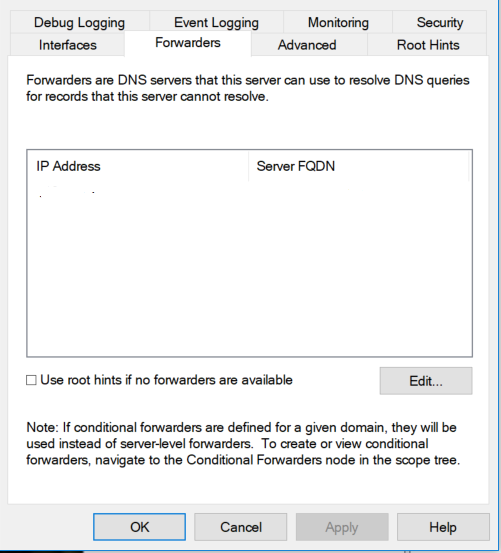
For the PIHOLE, set the VPN DNS address and one regular DNS WAN address?
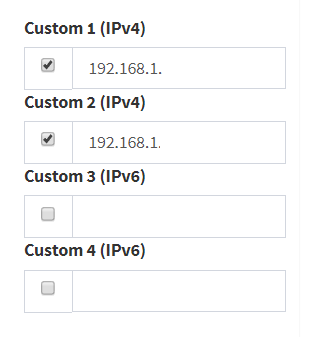
Any of these settings below on the PIHOLE need to be set?
The VPN I am subscribed to only provides on DNS server address. Right now, I have a NAT port-forward rule for DNS to redirect to that VPN IP address. And I think that's the problem, even though I have set Alias for only selected devices for the VPN, all of my devices, including the non-VPN ones are going through the VPN DNS. If I try anything else the VPN works but then the DNS leaks.
-
Yes, on the Windows DC, it would be the "Forwarders" is where you would place the PiHole IP. Remove to local IPs from the PiHole and add either your ISP DNS or the other options there (google, lvl3, etc)
So, it would work like this:
- Host needs a DNS lookup.
- Host goes to the Windows DC DNS (if it's a local DNS, it stops here and all done)
- The Windows DNS says "I don't know what www.stupiddomain.com is" (and all associated ad domains, CDNs, etc dns names) I'll check with my FORWARDER.
- Windows DNS sends the request to the PiHole
- PiHole checks the DNS against a upstream (recursive DNS host, such is ISP, Google, Lvl3, whatever you set) and provides good IP's back to the Windows DNS and bad ip's with its own PiHole IP also back to the windows DNS.
- The Windows DNS then just relays all those DNS queries IP addresses back to the host with the legit DNS/IP records and the PiHol IP for the blocked DNS records.
- Host is happy and goes to those IP's.
-
@philw
Thanks very much Philw. I will try that this week and report back.
Maybe this is what causes the other problem I cannot figure out with all the clients using the same VPN DNS.Questions - so having set the Windows DC DNS for all devices through PFSENSE under the DHCP settings, and then setting the upstream DNS on the PIHOLE, there is no need to set anything for DNS under the General Settings for PFSENSE, correct? No need to set the PFSENSE IP address either anywhere in the equation, correct?
No need to set these options below:?
Allow DNS server list to be overridden by DCHP/PPP on WAN
Do not use the DNS forwarder/DNS resolver as a DNS server for the firewall.And under DNS Resolver:
Enable forwarding mode - checked off, correct?Thanks again,
OXIB. -
@oxibquieh
Your pfSesne would still need a DNS for lookups. You can either allow it to override or use your own choosing, or even point the pf sense to the Windows DC.IF, and IF you are using the VPN for the outbound DNS connection to the internet for your pihole, and your VPN service uses a DNS name and not a IP address, it will be a problem and the VPN connection may get in a hung state (my exact issue I'm having now with not having the tunnel up and the PF sense needing DNS). I'm going to play with some settings on my own setup to see a work around for this.
-
Hi, What was the final outcome with this?
I've just set up pfsense, with a VPN, I can prevent leaks if I send ALL dns lookups to resolver and only select the VPN interface for outbound requests, but then my internet slows for all clients (especially non VPN clients), speed tests come back slow, high ping and gdrive uploads are slow. When I perform a trace route to google.com it goes through massive hops, if I remove the VPN interface from the resolver and add back in my WAN, everything works and trace route hops drop. If I add both, I get leaks.
I assume the content delivery network stuff gets messed up like one poster mentioned?
I think my only solution at the mo is to no use VPN client in pfsense, and stick to the windows/Mac clients on the machines that I'd like to use the VPN....
I'd like to add Pihole or adblocker next, so keen to understand if this got resolved.
Also how can I prevent the resolver using my fail back LTE link for dns, but still support dns when WAN is down? This all feels related and like there should be an easier way to achieve this out of the box :-)
Random brain dump - do we need to ultimately have 2 x Pihole, resolver etc. (1 for WAN 1 for VPN clients) to get around this problem? Is it a design constraint with a single resolver?