-
@itlomb
If you are new to Snort or any IDS/IPS, then I highly recommend you run it in just alerting mode and DO NOT enable blocking. Let it run for several weeks if not a couple of months and analyze all the alerts you see. You can look them up using Google. You will then be able to whittle down the false positives for your network and can either disable those rules or suppress their alerts.Suppress in Snort means to silence or ignore the alert (and resulting block, if blocking mode is enabled). But with a suppressed rule Snort still evaluates all traffic against the rule. So you can say that wastes CPU resources. However, there can still be valid reasons for needing the rule. Maybe you want it to fire only for certain hosts (or alternatively, not fire for only certain hosts). Suppress gives you options of filtering the alerts from a given rule by source IP, destination IP and number of alerts over a specified time.
Google is your friend with an IDS such as Snort. Go have some fun doing research and learning about an IDS ...

-
As Bill said run it in alerting mode.
Dump the data from Services -> Snort -> Alerts into a spreadsheet for a baseline.
I found these to be false positives.
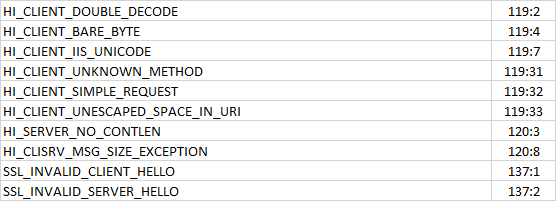
^^ didn't know this would happen when copying from a spreadsheet.

HI_CLIENT_DOUBLE_DECODE 119:2
HI_CLIENT_BARE_BYTE 119:4
HI_CLIENT_IIS_UNICODE 119:7
HI_CLIENT_UNKNOWN_METHOD 119:31
HI_CLIENT_SIMPLE_REQUEST 119:32
HI_CLIENT_UNESCAPED_SPACE_IN_URI 119:33
HI_SERVER_NO_CONTLEN 120:3
HI_CLISRV_MSG_SIZE_EXCEPTION 120:8
SSL_INVALID_CLIENT_HELLO 137:1
SSL_INVALID_SERVER_HELLO 137:2 -
Greetings.
Thank you for this insight.
So this is my question at this moment. If you see my EG below. and it is a malware threat. What is the process that i need to do?
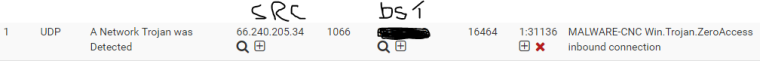 .
.Since im seeing this in the Alert logs, Is it just passing through? or is my Firewall/Snort actually doing something with it? When i hover over the + symbol my only option is to suppress. But that means its just going to ignore the alert right?
This is somewhat confusing as looking at this alert i have no clue what to do with it?
Hope this makes sense
Regards
-
If you're running snort in alerting mode its will only ever warn.
Is the dst address your WAN address or an address on your LAN ?
Surpress means allow and don't log.
Anything marked Malware / Trojan I'd try and locale the host on your LAN ASAP.
Google the SID.
https://www.snort.org/rule_docs/1-31136
-
Hi NBTB
The dst address is my WAN address.
Is there no way to have, Just like the suppress button, but this time a block button?
Regards
-
You could use IP reputation and a blacklist :-
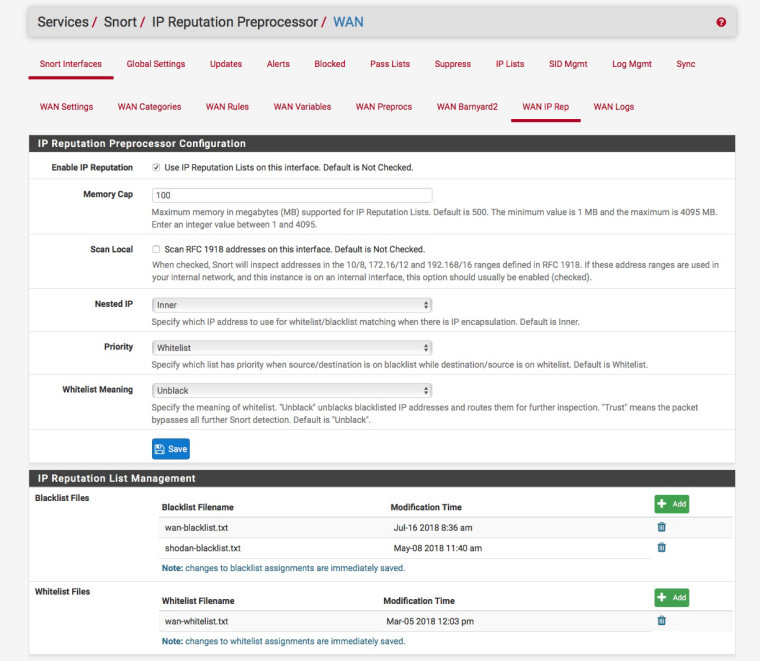
But do you have something on the LAN thats causing the issue?
Othwewise block on the WAN for all:-
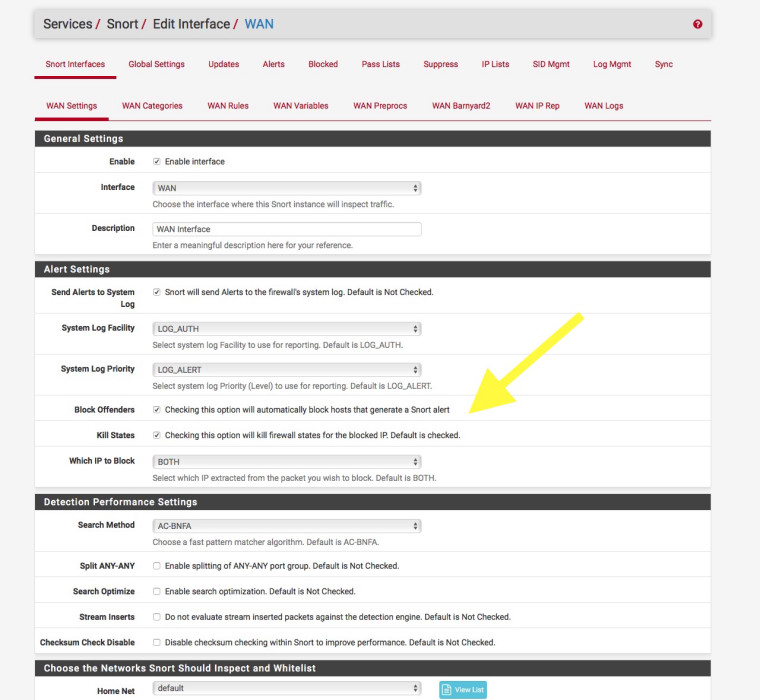
-
Hi
I have a network of 50 Users. So id need to go through each pc to do a scan.
Thanks for the advice above ill look into this.
:) -
Try adding snort on the LAN.
-
Thank you.
WIll give LAN a bash on SNORT, Not sure if this is wise though.
Regards
-
Thank you.
WIll give LAN a bash on SNORT, Not sure if this is wise though.
Regards
The traffic you're seeing on the WAN is just the normal noise on the web and is by default, blocked by pfSense.
By running Snort on the LAN, now you can easily see which computers on your network is generating the traffic that Snort is showing. Then you can take the appropriate action to either stop or allow this traffic through your pfSense.
-
Greetings.
Thank you . i have enabled the LAN and it does start making sense.
Thank you very much for all your advice. Still much to learn :)
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.