How to prevent OpenVPN clients from accessing local IP addresses?
-
Do they get IP addresses in your LAN range ?
-
No, a completely different subnet. (LAN is 192.168.x.x, OpenVPN clients are assigned 10.0.x.x, DNS server would be 192.168.x.1 (edit - DNS could also be reachable at 10.0.x.1))
-
Here's what I do with IPSec:-
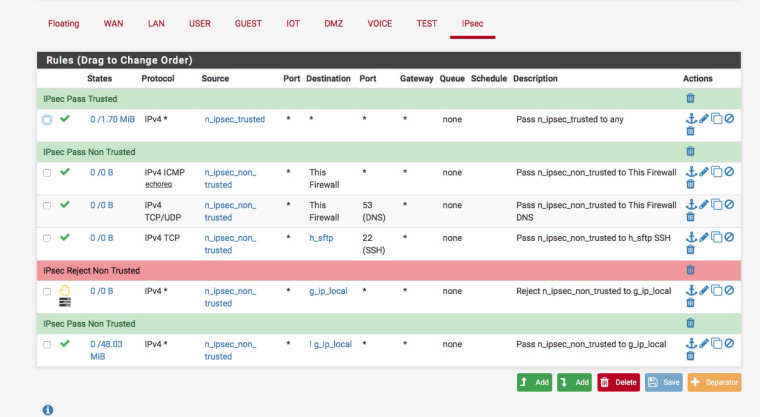
I hand out specific IP addresses to various users via FreeRadius.
n_ipsec_trusted = 172.16.8.0/25
n_ipsec_non_trusted = 172.16.8.128/25
-
I already have similar rules on the OpenVPN rules tab, but the rules do not seem to block as intended, and local access is still happening. Here is what I have:
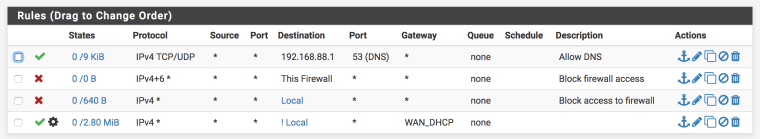
("Local" alias is all my local subnets other than the OpenVPN subnet)
Any suggestions?
-
Whats the Advanced filter rule at the bottom doing ?
Also why the gateway, do you have a multi wan set-up?
-
The only advanced option is the gateway - WAN_DHCP. I am not using a multiwan setup, but there are several outgoing OpenVPN clients. I think I stuck the gateway in there to make sure the connection went out over the WAN connection rather than the OpenVPN client connections. Is that somehow causing the issue?
-
Not sure but there is no need if you have a single wan connection.
try enabling logging on your rules and see what rule is being hit.
-
Turns out my rules work, for the most part. I was testing the connection by connecting to the VPN through my home network. When I connected outside my home lan, the rules worked as intended - DNS provided by the pfSense box, no other connections with the local subnets permitted. I am not sure why the connections were permitted when I originated from the home lan, but this is of little concern, as I would not normally be using a VPN when I am already on the network to which I am trying to connect.
-
@pfguy2018 said in How to prevent OpenVPN clients from accessing local IP addresses?:
Turns out my rules work, for the most part. I was testing the connection by connecting to the VPN through my home network. When I connected outside my home lan, the rules worked as intended - DNS provided by the pfSense box, no other connections with the local subnets permitted. I am not sure why the connections were permitted when I originated from the home lan, but this is of little concern, as I would not normally be using a VPN when I am already on the network to which I am trying to connect.
By the sound of things you've set it up as a split tunnel.
-
I am not sure why the connections were permitted when I originated from the home lan
@pfguy2018 Because the local LAN was a local subnet to the host. That traffic won't go out the VPN, but straight out the interface.
-
I get that. But the client was also able to access vlans on different subnetd when connected to the VPN server while originating from a home vlan. That is what confused me. (As noted earlier, this does not occur if connecting to the VPN server from outside the home)