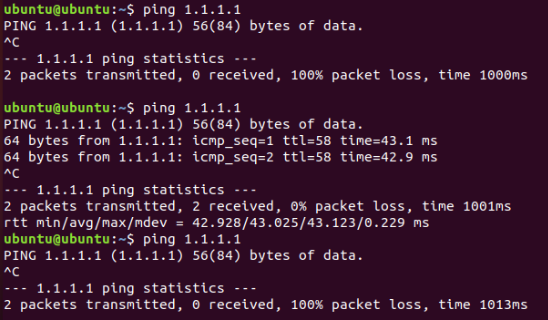
OpenVPN Client dropping every second state
-
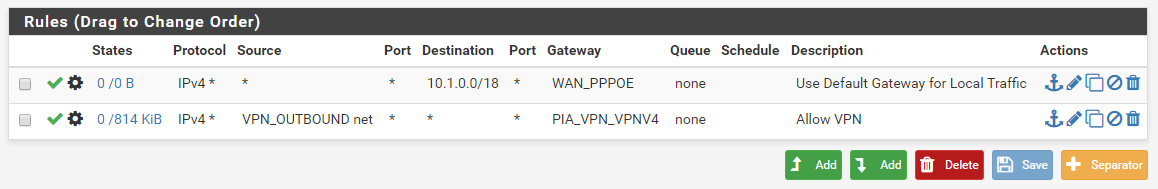
In
/tmp/rules.debugthere should also be a definition forGWPIA_VPN_VPNV4near the top, what does it show?Also, next time you try, look at the state table contents (Diagnostics > States) for states from the source or the destination to see what it looks like when it works vs when it doesn't.
-
Here's the whole thing, it shows
GWPIA_VPN_VPNV4 = " route-to ( ovpnc1 10.33.10.5 ) ". Is there a way to see more information than (Diagnostics > States)?This is what it looks like when working:
This is not working:
set limit table-entries 400000 set optimization normal set limit states 805000 set limit src-nodes 805000 #System aliases loopback = "{ lo0 }" WAN = "{ pppoe0 }" LAN = "{ em0 }" TRUSTED = "{ em0.10 }" GUEST = "{ em0.20 }" CAMERA = "{ em0.30 }" IOT = "{ em0.40 }" VM = "{ em0.50 }" VPN_OUTBOUND = "{ em0.60 }" PIA_VPN = "{ ovpnc1 }" VPN_INBOUND = "{ em0.70 }" SEG_1 = "{ em0.250 }" OpenVPN = "{ openvpn }" #SSH Lockout Table table <sshlockout> persist table <webConfiguratorlockout> persist #Snort tables table <snort2c> table <virusprot> table <bogons> persist file "/etc/bogons" table <bogonsv6> persist file "/etc/bogonsv6" table <vpn_networks> { 10.1.70.0/24 } table <negate_networks> { 10.1.70.0/24 } # User Aliases # Gateways GWPIA_VPN_VPNV4 = " route-to ( ovpnc1 10.33.10.5 ) " GWWAN_PPPOE = " route-to ( pppoe0 10.20.25.94 ) " set loginterface em0 set skip on pfsync0 scrub on $WAN all fragment reassemble scrub on $LAN all fragment reassemble scrub on $TRUSTED all fragment reassemble scrub on $GUEST all fragment reassemble scrub on $CAMERA all fragment reassemble scrub on $IOT all fragment reassemble scrub on $VM all fragment reassemble scrub on $VPN_OUTBOUND all fragment reassemble scrub on $PIA_VPN all fragment reassemble scrub on $VPN_INBOUND all fragment reassemble scrub on $SEG_1 all fragment reassemble no nat proto carp no rdr proto carp nat-anchor "natearly/*" nat-anchor "natrules/*" # Outbound NAT rules (manual) nat on $OpenVPN from 127.0.0.0/8 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.1.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.10.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.20.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.30.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.40.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.50.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.60.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.70.0/24 to any -> (openvpn) port 1024:65535 nat on $OpenVPN from 10.1.250.0/30 to any -> (openvpn) port 1024:65535 # Outbound NAT rules (automatic) # Subnets to NAT table <tonatsubnets> { 127.0.0.0/8 10.1.1.0/24 10.1.10.0/24 10.1.20.0/24 10.1.30.0/24 10.1.40.0/24 10.1.50.0/24 10.1.60.0/24 10.1.70.0/24 10.1.250.0/30 10.1.70.0/24 } nat on $WAN from <tonatsubnets> to any port 500 -> 110.174.116.92/32 static-port nat on $WAN from <tonatsubnets> to any -> 110.174.116.92/32 port 1024:65535 # Load balancing anchor rdr-anchor "relayd/*" # TFTP proxy rdr-anchor "tftp-proxy/*" # NAT Inbound Redirects rdr on pppoe0 proto tcp from any to 110.174.116.92 port 443 -> 10.1.1.1 port 444 # Reflection redirect rdr on { em0 em0.10 em0.20 em0.30 em0.40 em0.50 em0.60 em0.70 em0.250 openvpn } proto tcp from any to 110.174.116.92 port 443 -> 10.1.1.1 port 444 no nat on em0 proto tcp from em0 to 10.1.1.1 port 444 nat on em0 proto tcp from 10.1.1.0/24 to 10.1.1.1 port 444 -> 10.1.1.1 port 1024:65535 rdr on pppoe0 proto { tcp udp } from any to 110.174.116.92 port 32400 -> 10.1.50.245 # Reflection redirect rdr on { em0 em0.10 em0.20 em0.30 em0.40 em0.50 em0.60 em0.70 em0.250 openvpn } proto { tcp udp } from any to 110.174.116.92 port 32400 -> 10.1.50.245 no nat on em0.50 proto { tcp udp } from em0.50 to 10.1.50.245 port 32400 nat on em0.50 proto { tcp udp } from 10.1.50.0/24 to 10.1.50.245 port 32400 -> 10.1.50.254 port 1024:65535 # UPnPd rdr anchor rdr-anchor "miniupnpd" anchor "relayd/*" anchor "openvpn/*" anchor "ipsec/*" # block IPv4 link-local. Per RFC 3927, link local "MUST NOT" be forwarded by a routing device, # and clients "MUST NOT" send such packets to a router. FreeBSD won't route 169.254./16, but # route-to can override that, causing problems such as in redmine #2073 block in log quick from 169.254.0.0/16 to any tracker 1000000101 label "Block IPv4 link-local" block in log quick from any to 169.254.0.0/16 tracker 1000000102 label "Block IPv4 link-local" #--------------------------------------------------------------------------- # default deny rules #--------------------------------------------------------------------------- block in log inet all tracker 1000000103 label "Default deny rule IPv4" block out log inet all tracker 1000000104 label "Default deny rule IPv4" block in log inet6 all tracker 1000000105 label "Default deny rule IPv6" block out log inet6 all tracker 1000000106 label "Default deny rule IPv6" # IPv6 ICMP is not auxilary, it is required for operation # See man icmp6(4) # 1 unreach Destination unreachable # 2 toobig Packet too big # 128 echoreq Echo service request # 129 echorep Echo service reply # 133 routersol Router solicitation # 134 routeradv Router advertisement # 135 neighbrsol Neighbor solicitation # 136 neighbradv Neighbor advertisement pass quick inet6 proto ipv6-icmp from any to any icmp6-type {1,2,135,136} tracker 1000000107 keep state # Allow only bare essential icmpv6 packets (NS, NA, and RA, echoreq, echorep) pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {129,133,134,135,136} tracker 1000000108 keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {129,133,134,135,136} tracker 1000000109 keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {128,133,134,135,136} tracker 1000000110 keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type {128,133,134,135,136} tracker 1000000111 keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {128,133,134,135,136} tracker 1000000112 keep state # We use the mighty pf, we cannot be fooled. block log quick inet proto { tcp, udp } from any port = 0 to any tracker 1000000113 label "Block traffic from port 0" block log quick inet proto { tcp, udp } from any to any port = 0 tracker 1000000114 label "Block traffic to port 0" block log quick inet6 proto { tcp, udp } from any port = 0 to any tracker 1000000115 label "Block traffic from port 0" block log quick inet6 proto { tcp, udp } from any to any port = 0 tracker 1000000116 label "Block traffic to port 0" # Snort package block log quick from <snort2c> to any tracker 1000000117 label "Block snort2c hosts" block log quick from any to <snort2c> tracker 1000000118 label "Block snort2c hosts" # SSH lockout block in log quick proto tcp from <sshlockout> to (self) port 22 tracker 1000000301 label "sshlockout" # webConfigurator lockout block in log quick proto tcp from <webConfiguratorlockout> to (self) port 443 tracker 1000000351 label "webConfiguratorlockout" block in log quick from <virusprot> to any tracker 1000000400 label "virusprot overload table" # block bogon networks (IPv4) # http://www.cymru.com/Documents/bogon-bn-nonagg.txt block in log quick on $WAN from <bogons> to any tracker 11000 label "block bogon IPv4 networks from WAN" # block bogon networks (IPv6) # http://www.team-cymru.org/Services/Bogons/fullbogons-ipv6.txt block in log quick on $WAN from <bogonsv6> to any tracker 11000 label "block bogon IPv6 networks from WAN" antispoof log for $WAN tracker 1000001570 # block anything from private networks on interfaces with the option set block in log quick on $WAN from 10.0.0.0/8 to any tracker 12000 label "Block private networks from WAN block 10/8" block in log quick on $WAN from 127.0.0.0/8 to any tracker 12000 label "Block private networks from WAN block 127/8" block in log quick on $WAN from 172.16.0.0/12 to any tracker 12000 label "Block private networks from WAN block 172.16/12" block in log quick on $WAN from 192.168.0.0/16 to any tracker 12000 label "Block private networks from WAN block 192.168/16" block in log quick on $WAN from fc00::/7 to any tracker 12000 label "Block ULA networks from WAN block fc00::/7" antispoof log for $LAN tracker 1000002620 # allow access to DHCP server on LAN pass in quick on $LAN proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000002641 label "allow access to DHCP server" pass in quick on $LAN proto udp from any port = 68 to 10.1.1.1 port = 67 tracker 1000002642 label "allow access to DHCP server" pass out quick on $LAN proto udp from 10.1.1.1 port = 67 to any port = 68 tracker 1000002643 label "allow access to DHCP server" # allow access to DHCPv6 server on LAN # We need inet6 icmp for stateless autoconfig and dhcpv6 pass quick on $LAN inet6 proto udp from fe80::/10 to fe80::/10 port = 546 tracker 1000002651 label "allow access to DHCPv6 server" pass quick on $LAN inet6 proto udp from fe80::/10 to ff02::/16 port = 546 tracker 1000002652 label "allow access to DHCPv6 server" pass quick on $LAN inet6 proto udp from fe80::/10 to ff02::/16 port = 547 tracker 1000002653 label "allow access to DHCPv6 server" pass quick on $LAN inet6 proto udp from ff02::/16 to fe80::/10 port = 547 tracker 1000002654 label "allow access to DHCPv6 server" antispoof log for $TRUSTED tracker 1000003670 # allow access to DHCP server on TRUSTED pass in quick on $TRUSTED proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000003691 label "allow access to DHCP server" pass in quick on $TRUSTED proto udp from any port = 68 to 10.1.10.254 port = 67 tracker 1000003692 label "allow access to DHCP server" pass out quick on $TRUSTED proto udp from 10.1.10.254 port = 67 to any port = 68 tracker 1000003693 label "allow access to DHCP server" antispoof log for $GUEST tracker 1000004720 # allow access to DHCP server on GUEST pass in quick on $GUEST proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000004741 label "allow access to DHCP server" pass in quick on $GUEST proto udp from any port = 68 to 10.1.20.254 port = 67 tracker 1000004742 label "allow access to DHCP server" pass out quick on $GUEST proto udp from 10.1.20.254 port = 67 to any port = 68 tracker 1000004743 label "allow access to DHCP server" antispoof log for $CAMERA tracker 1000005770 # allow access to DHCP server on CAMERA pass in quick on $CAMERA proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000005791 label "allow access to DHCP server" pass in quick on $CAMERA proto udp from any port = 68 to 10.1.30.254 port = 67 tracker 1000005792 label "allow access to DHCP server" pass out quick on $CAMERA proto udp from 10.1.30.254 port = 67 to any port = 68 tracker 1000005793 label "allow access to DHCP server" antispoof log for $IOT tracker 1000006820 # allow access to DHCP server on IOT pass in quick on $IOT proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000006841 label "allow access to DHCP server" pass in quick on $IOT proto udp from any port = 68 to 10.1.40.254 port = 67 tracker 1000006842 label "allow access to DHCP server" pass out quick on $IOT proto udp from 10.1.40.254 port = 67 to any port = 68 tracker 1000006843 label "allow access to DHCP server" antispoof log for $VM tracker 1000007870 # allow access to DHCP server on VM pass in quick on $VM proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000007891 label "allow access to DHCP server" pass in quick on $VM proto udp from any port = 68 to 10.1.50.254 port = 67 tracker 1000007892 label "allow access to DHCP server" pass out quick on $VM proto udp from 10.1.50.254 port = 67 to any port = 68 tracker 1000007893 label "allow access to DHCP server" antispoof log for $VPN_OUTBOUND tracker 1000008920 # allow access to DHCP server on VPN_OUTBOUND pass in quick on $VPN_OUTBOUND proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000008941 label "allow access to DHCP server" pass in quick on $VPN_OUTBOUND proto udp from any port = 68 to 10.1.60.254 port = 67 tracker 1000008942 label "allow access to DHCP server" pass out quick on $VPN_OUTBOUND proto udp from 10.1.60.254 port = 67 to any port = 68 tracker 1000008943 label "allow access to DHCP server" # block bogon networks (IPv4) # http://www.cymru.com/Documents/bogon-bn-nonagg.txt block in log quick on $PIA_VPN from <bogons> to any tracker 11000 label "block bogon IPv4 networks from PIA_VPN" # block bogon networks (IPv6) # http://www.team-cymru.org/Services/Bogons/fullbogons-ipv6.txt block in log quick on $PIA_VPN from <bogonsv6> to any tracker 11000 label "block bogon IPv6 networks from PIA_VPN" antispoof log for $PIA_VPN tracker 1000009970 # block anything from private networks on interfaces with the option set block in log quick on $PIA_VPN from 10.0.0.0/8 to any tracker 12000 label "Block private networks from PIA_VPN block 10/8" block in log quick on $PIA_VPN from 127.0.0.0/8 to any tracker 12000 label "Block private networks from PIA_VPN block 127/8" block in log quick on $PIA_VPN from 172.16.0.0/12 to any tracker 12000 label "Block private networks from PIA_VPN block 172.16/12" block in log quick on $PIA_VPN from 192.168.0.0/16 to any tracker 12000 label "Block private networks from PIA_VPN block 192.168/16" block in log quick on $PIA_VPN from fc00::/7 to any tracker 12000 label "Block ULA networks from PIA_VPN block fc00::/7" antispoof log for $VPN_INBOUND tracker 1000011020 antispoof log for $SEG_1 tracker 1000012070 # allow access to DHCP server on SEG_1 pass in quick on $SEG_1 proto udp from any port = 68 to 255.255.255.255 port = 67 tracker 1000012091 label "allow access to DHCP server" pass in quick on $SEG_1 proto udp from any port = 68 to 10.1.250.2 port = 67 tracker 1000012092 label "allow access to DHCP server" pass out quick on $SEG_1 proto udp from 10.1.250.2 port = 67 to any port = 68 tracker 1000012093 label "allow access to DHCP server" # loopback pass in on $loopback inet all tracker 1000013161 label "pass IPv4 loopback" pass out on $loopback inet all tracker 1000013162 label "pass IPv4 loopback" pass in on $loopback inet6 all tracker 1000013163 label "pass IPv6 loopback" pass out on $loopback inet6 all tracker 1000013164 label "pass IPv6 loopback" # let out anything from the firewall host itself and decrypted IPsec traffic pass out inet all keep state allow-opts tracker 1000013165 label "let out anything IPv4 from firewall host itself" pass out inet6 all keep state allow-opts tracker 1000013166 label "let out anything IPv6 from firewall host itself" pass out route-to ( pppoe0 10.20.25.94 ) from 110.174.116.92 to !110.174.116.92/32 tracker 1000013261 keep state allow-opts label "let out anything from firewall host itself" pass out route-to ( ovpnc1 10.33.10.5 ) from 10.33.10.6 to !10.33.10.6/32 tracker 1000013262 keep state allow-opts label "let out anything from firewall host itself" # make sure the user cannot lock himself out of the webConfigurator or SSH pass in quick on em0 proto tcp from any to (em0) port { 443 80 22 } tracker 10000 keep state label "anti-lockout rule" # NAT Reflection rules pass in inet tagged PFREFLECT tracker 1000013581 keep state label "NAT REFLECT: Allow traffic to localhost" # User-defined rules follow anchor "userrules/*" pass in quick on $OpenVPN inet from any to any tracker 1533131011 keep state label "USER_RULE: OpenVPN wizard" pass in quick on $WAN reply-to ( pppoe0 10.20.25.94 ) inet proto { tcp udp } from any to 10.1.50.245 port 32400 tracker 1533131548 keep state label "USER_RULE: NAT Plex" pass in quick on $WAN reply-to ( pppoe0 10.20.25.94 ) inet proto udp from any to 110.174.116.92 port 1194 tracker 1533474939 keep state label "USER_RULE: OpenVPN VPN IN wizard" pass in quick on $WAN reply-to ( pppoe0 10.20.25.94 ) inet proto tcp from any to 10.1.1.1 port 444 tracker 1533978660 flags S/SA keep state label "USER_RULE: NAT HA Proxy" pass in quick on $LAN inet from any to 10.1.0.0/18 tracker 1533361255 keep state label "USER_RULE: Use Default Gateway for Local Traffic" pass in quick on $LAN inet from any to <negate_networks> tracker 10000001 keep state label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $LAN $GWWAN_PPPOE inet from any to any tracker 0100000101 keep state label "USER_RULE: Allow All LAN" pass in quick on $TRUSTED inet from any to 10.1.0.0/18 tracker 1533362175 keep state label "USER_RULE: Use Default Gateway for Local Traffic" pass in quick on $TRUSTED inet from 10.1.10.0/24 to <negate_networks> tracker 10000002 keep state label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $TRUSTED $GWWAN_PPPOE inet from 10.1.10.0/24 to any tracker 1533337479 keep state label "USER_RULE: Allow All - Use PPPoE" block in quick on $GUEST inet from any to 10.1.0.0/18 tracker 1533398341 label "USER_RULE: Block Local Traffic" pass in quick on $GUEST inet from 10.1.20.0/24 to <negate_networks> tracker 10000003 keep state dnpipe ( 2,1) label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $GUEST $GWWAN_PPPOE inet from 10.1.20.0/24 to any tracker 1533398097 keep state dnpipe ( 2,1) label "USER_RULE: Allow All - Use VPN" pass in quick on $CAMERA inet proto udp from any to any port 123 tracker 1534226880 keep state label "USER_RULE" block in quick on $CAMERA inet proto tcp from any to 110.174.116.92/32 tracker 1533101545 flags S/SA label "USER_RULE: Deny WAN" pass in quick on $CAMERA inet from any to 10.1.0.0/18 tracker 1533362466 keep state label "USER_RULE: Use Default Gateway for Local Traffic" pass in quick on $VM inet from any to 10.1.0.0/18 tracker 1533362552 keep state label "USER_RULE: Use Default Gateway for Local Traffic" pass in quick on $VM inet from 10.1.50.0/24 to <negate_networks> tracker 10000004 keep state label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $VM $GWWAN_PPPOE inet from 10.1.50.0/24 to any tracker 1533038333 keep state label "USER_RULE: Allow All - Use PPPoE" pass in quick on $VPN_OUTBOUND $GWWAN_PPPOE inet from any to 10.1.0.0/18 tracker 1533360955 keep state label "USER_RULE: Use Default Gateway for Local Traffic" pass in quick on $VPN_OUTBOUND inet from 10.1.60.0/24 to <negate_networks> tracker 10000005 keep state label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $VPN_OUTBOUND $GWPIA_VPN_VPNV4 inet from 10.1.60.0/24 to any tracker 1533562370 keep state label "USER_RULE: Allow VPN" pass in quick on $VPN_INBOUND inet from any to 10.1.0.0/18 tracker 1533474618 keep state label "USER_RULE: Use Default Gateway for Local Traffic" pass in quick on $VPN_INBOUND inet from 10.1.70.0/24 to <negate_networks> tracker 10000006 keep state label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $VPN_INBOUND $GWWAN_PPPOE inet from 10.1.70.0/24 to any tracker 1533474629 keep state label "USER_RULE: Allow All - Use PPPoE" block in quick on $SEG_1 inet from any to 10.1.0.0/18 tracker 1533557957 label "USER_RULE: Block Local Traffic" pass in quick on $SEG_1 inet from any to <negate_networks> tracker 10000007 keep state label "NEGATE_ROUTE: Negate policy routing for destination" pass in quick on $SEG_1 $GWWAN_PPPOE inet from any to any tracker 1533557911 keep state label "USER_RULE: Allow Internet" # VPN Rules anchor "tftp-proxy/*" -
On the states page, do not filter by interface. Instead, search for your local client IP address or the targer (e.g.
1.1.1.1). Maybe it's not leaving the interface you expect.Also check the output of
netstat -rnW, maybe somehow you have two interfaces trying to use10.33.10.5as a gateway or some other overlap. -
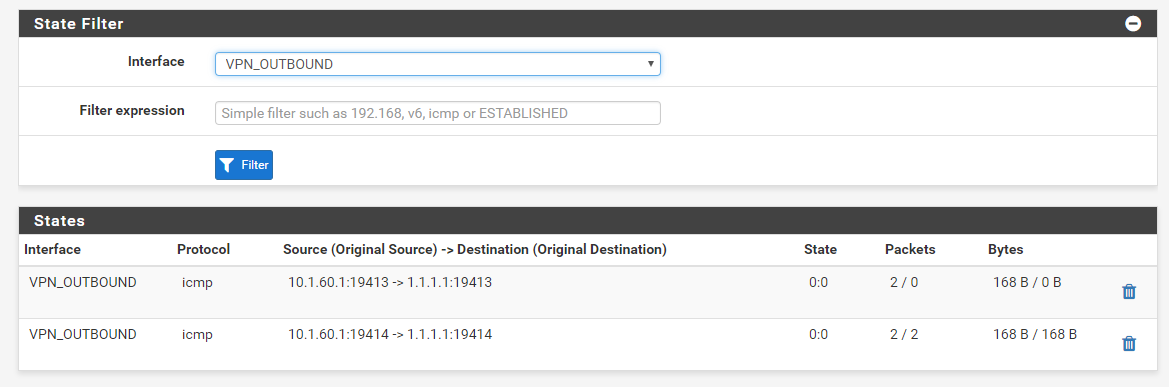
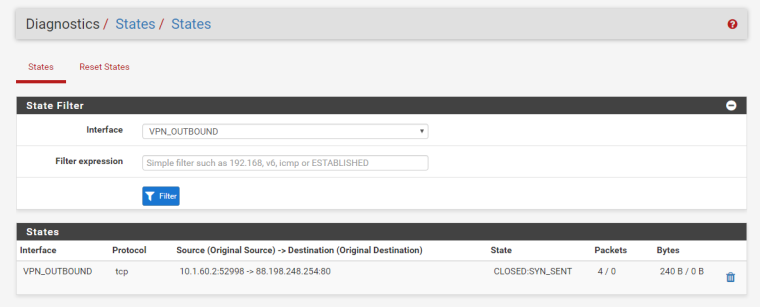
This shows the failed connection leaving
PIA_VPNwhich is expected: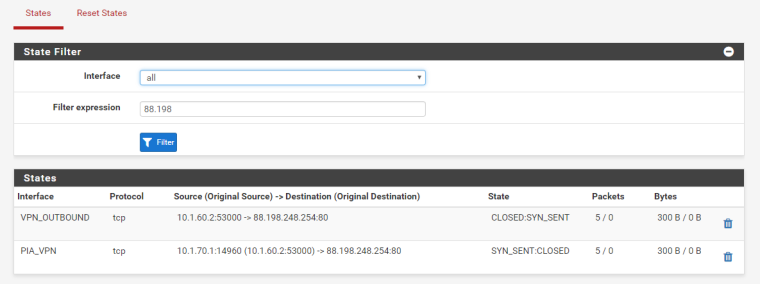
Here the established connection which also uses
PIA_VPN:
Doesn't appear to be an overlap:
Routing tables Internet: Destination Gateway Flags Use Mtu Netif Expire default 10.20.25.94 UGS 1451581 1492 pppoe0 10.0.10.1 10.33.10.5 UGHS 35305 1500 ovpnc1 10.1.1.0/24 link#1 U 47727506 1500 em0 10.1.1.1 link#1 UHS 473 16384 lo0 10.1.10.0/24 link#7 U 81380177 1500 em0.10 10.1.10.254 link#7 UHS 449 16384 lo0 10.1.20.0/24 link#8 U 544311 1500 em0.20 10.1.20.254 link#8 UHS 342 16384 lo0 10.1.30.0/24 link#9 U 299944 1500 em0.30 10.1.30.254 link#9 UHS 342 16384 lo0 10.1.40.0/24 link#10 U 0 1500 em0.40 10.1.40.254 link#10 UHS 418 16384 lo0 10.1.50.0/24 link#11 U 20793343 1500 em0.50 10.1.50.254 link#11 UHS 418 16384 lo0 10.1.60.0/24 link#14 U 108474 1500 em0.60 10.1.60.254 link#14 UHS 200 16384 lo0 10.1.70.0/24 link#15 U 0 1500 em0.70 10.1.70.1 link#16 UHS 0 16384 lo0 10.1.70.2 link#16 UH 15800 1500 ovpns2 10.1.70.254 link#15 UHS 418 16384 lo0 10.1.250.0/30 link#17 U 131423 1500 em0.250 10.1.250.2 link#17 UHS 347 16384 lo0 10.20.25.94 link#12 UH 332337 1492 pppoe0 10.33.10.5 link#13 UH 6 1500 ovpnc1 10.33.10.6 link#13 UHS 0 16384 lo0 110.174.116.92 link#12 UHS 1 16384 lo0 127.0.0.1 link#2 UH 244147684 16384 lo0 -
From the states, it looks like the traffic is exiting the firewall OK. The issue could be with PIA. Do you have two clients connected to the same account? They may be trying to load balance return traffic if your account has a static IP address and two active connections.
-
I highly doubt there is another client, but I've changed the account credentials to ensure that any device I may have had connected is removed. This hasn't fixed it so I think I may need to speak to their support in case they're familiar with this problem. I'll update this thread if I solve the problem. Thanks for your time!
-
So PIA support noticed that the Failed connections' source was 10.1.70.1 which is my OpenVPN server's network. Disabling the server fixed the issue. Now I need to determine why this is happening so I can re enable the Server. They suggested I use manual outbound NAT rather than hybrid NAT but that hasn't changed anything.
-
@ooimo said in OpenVPN Client dropping every second state:
10.1.70.0/24 link#15 U 0 1500 em0.70 10.1.70.1 link#16 UHS 0 16384 lo0 10.1.70.2 link#16 UH 15800 1500 ovpns2 10.1.70.254 link#15 UHS 418 16384 lo0For starters, it looks like you are using the same network as a tunnel network and the numbering on em0.70.
They must be different.
-
I see, do I specify the PIA client's tunnel network in the client configuration?
-
That is on an OpenVPN server, not a client.
-
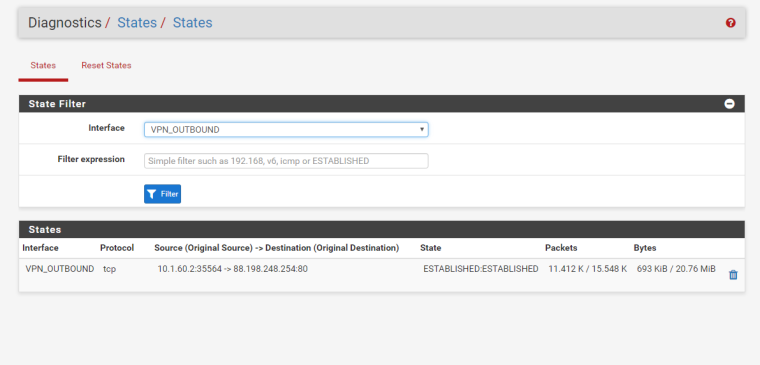
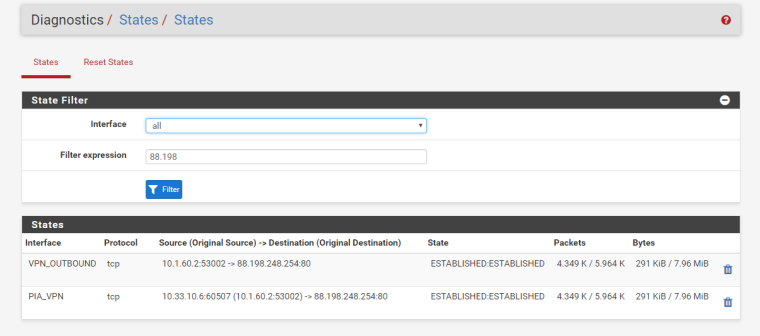
I think I solved it by changing the outbound NAT from "OpenVPN Address" to "PIA_VPN Address".
This is what the states now look like:
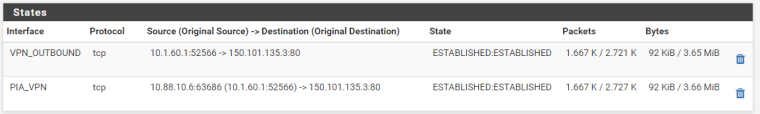
And this is the output of
netstat -rnW:Routing tables Internet: Destination Gateway Flags Use Mtu Netif Expire default 10.20.25.96 UGS 13372704 1492 pppoe0 10.0.10.1 10.88.10.5 UGHS 17379 1500 ovpnc1 10.1.1.0/24 link#1 U 51920099 1500 em0 10.1.1.1 link#1 UHS 473 16384 lo0 10.1.10.0/24 link#7 U 96185720 1500 em0.10 10.1.10.254 link#7 UHS 449 16384 lo0 10.1.20.0/24 link#8 U 1623465 1500 em0.20 10.1.20.254 link#8 UHS 342 16384 lo0 10.1.30.0/24 link#9 U 319811 1500 em0.30 10.1.30.254 link#9 UHS 342 16384 lo0 10.1.40.0/24 link#10 U 0 1500 em0.40 10.1.40.254 link#10 UHS 418 16384 lo0 10.1.50.0/24 link#11 U 26192375 1500 em0.50 10.1.50.254 link#11 UHS 418 16384 lo0 10.1.60.0/24 link#14 U 23111437 1500 em0.60 10.1.60.254 link#14 UHS 200 16384 lo0 10.1.70.0/24 link#15 U 0 1500 em0.70 10.1.70.1 link#16 UHS 0 16384 lo0 10.1.70.2 link#16 UH 0 1500 ovpns2 10.1.70.254 link#15 UHS 0 16384 lo0 10.1.250.0/30 link#17 U 184733 1500 em0.250 10.1.250.2 link#17 UHS 347 16384 lo0 10.20.25.96 link#12 UH 274490 1492 pppoe0 10.88.10.5 link#13 UH 6 1500 ovpnc1 10.88.10.6 link#13 UHS 0 16384 lo0 27.33.144.81 link#12 UHS 2 16384 lo0 127.0.0.1 link#2 UH 269295168 16384 lo0I couldn't see anything about this in the tutorial. Thanks for your help :)
-
10.1.70.0/24 still looks wrong.
-
That's the OpenVPN server's tunnel network. Clients that are connected get put in that range. What's the correct way to do it?
-
It's in the same subnet as em0.70. It shouldn't be.
-
I wasn't looking at the 10.1.70.x but yeah that does overlap.
Also "OpenVPN" is an interface group not an interface, so using it as a NAT destination may not always do what you expect, especially for outbound NAT since it would effectively round-robin in that way for outbound.
-
@jimp said in OpenVPN Client dropping every second state:
Also "OpenVPN" is an interface group not an interface, so using it as a NAT destination may not always do what you expect, especially for outbound NAT since it would effectively round-robin in that way for outbound.
Yeah I didn't realise it would round robin like that but now I do.
@derelict said in OpenVPN Client dropping every second state:
10.1.70.0/24 still looks wrong.
I removed that em0.70 interface and configured the server properly, Now that route isn't there which is good.