Squid-3.5.27 SSL Custom works few minutes. MITM breakdown
-
@denisk said in Squid-3.5.27 SSL Custom works few minutes. MITM breakdown:
@pfsensation
Of course installed. This configuration work few minutes - I see myself certificate in ChromeCan you check the cert on the warning message for me? I believe this is one of the reasons I gave up on Squid and permanently moved to E2 Guardian. Chrome requires that the certificate includes a SAN (Subject Alternative name) instead of a common name. My guess is that the bug I experienced still exists and that Squid is not generating the fake cert correctly with the SAN.
-
-
Chrome should be easiest, click on the "not secure" box near the URL. Then click certificate, it should open the certificate up. Check on the details tab at the top of the window and see if the certificate contains a valid Subject Alternative Name.
-
@pfsensation said in Squid-3.5.27 SSL Custom works few minutes. MITM breakdown:
Subject Alternative Name
Yes, I see the problem with Subject Alternative Name.
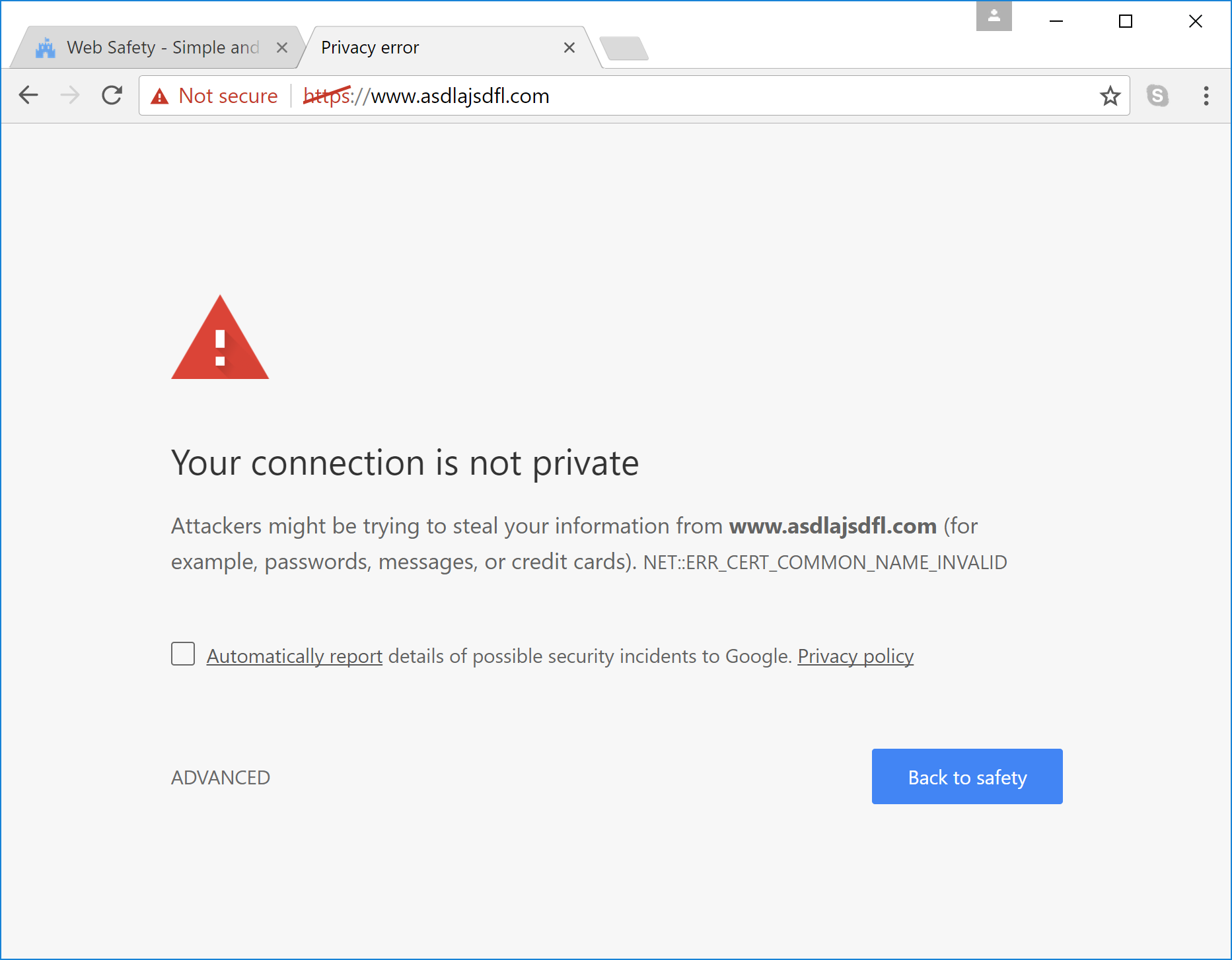
For example, website was yandex.ru:
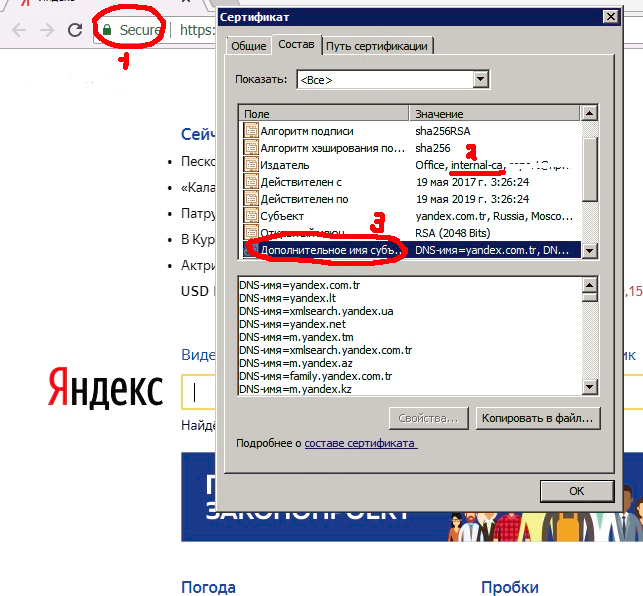
On this picture I see, what connection is secured (#1), and such certificate signed by my certificate (#2 - internal-ca), and there valid Subject Alternative Name (#3).After 15 minutes next picture:
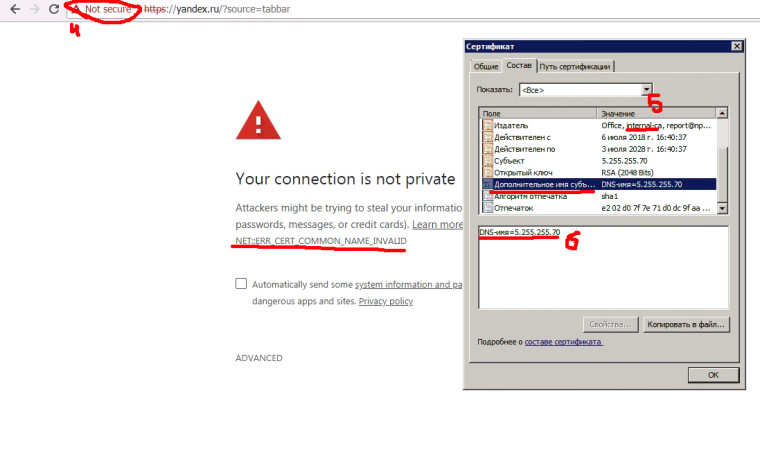
Connection is NOT secured (#4), yandex's certificate also signed by my certificate (#5), BUT Subject Alternative Name is IP address (#6).For additional information, such problem appears with other websites:
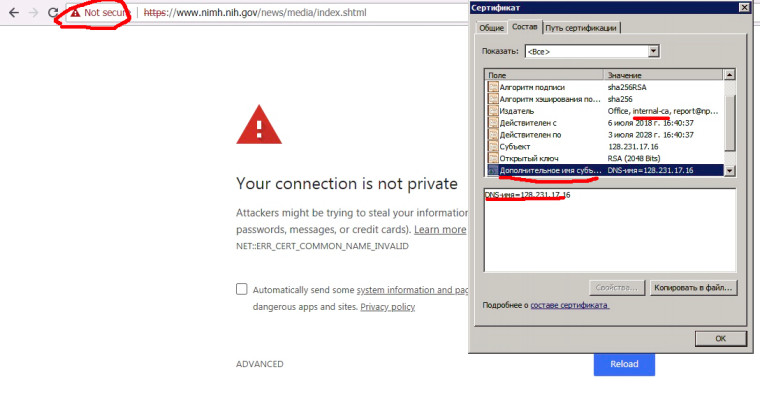
But why such problem appears through few minutes? On another object, where are the same pfSense instance, such problem doesn't appear!
-
@denisk To be honest with you, I can't tell you why Squid is such an issue. But I've identified that as an issue when I was attempting to get Squid with SquidGuard up and running myself. I've switched to E2 Guardian and have never looked back. It generates the certs without issues and works a lot better in general.
-
@pfsensation thanks for your response.
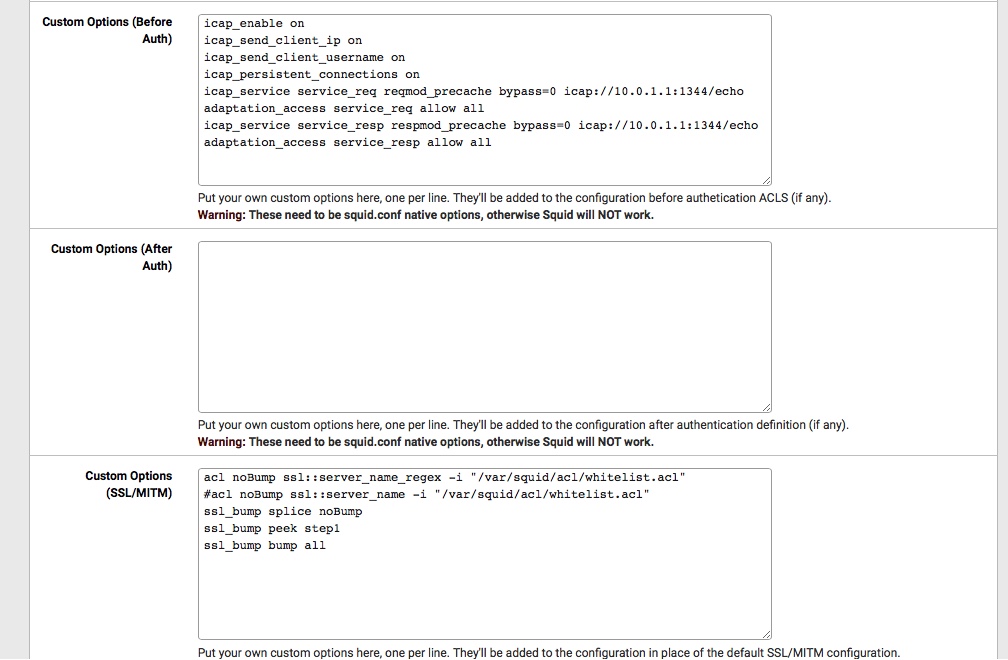
I tried e2guardian, but in it actual version appears some trouble: i need, that ALL HTTP/HTTPS traffic follows via ICAP server on another machine. In Squid, it was like:
icap_enable on
icap_send_client_ip on
icap_send_client_username on
icap_service service_req reqmod_precache bypass=0 icap://192.168.88.16:1344/echo
adaptation_access service_req allow all
icap_service service_resp respmod_precache bypass=0 icap://192.168.88.16:1344/echo
adaptation_access service_resp allow alle2guardian sends to ICAP server only requests with some content.
For me, connection with ICAP is main purpose of proxy working! -
@denisk Hmm... I haven't attempted that particular configuration. I use E2 Guardian for content filtering, but since it allows group setup I've got different configurations in place. For my use case it's perfect because it does generate those fake certs correctly and does a decent job of filtering.
For the LAN and Wi-Fi, I do full MITM and then on guest WiFi I use a equivalent to Splice all. This allows me to have CA certificates deployed onto the machines I manage. And then filter guest devices without any CA.
-
@pfsensation ok, i understand you. But i need to process any HTTP/HTTPS requests of all, users, which traffic follows through pfSense, except public WiFi, on another machine.
Squid's support responded me, that Squid-3.5 is no longer supported.
New question to pfSense developers - why users can updated squid to new version? -
@denisk I've been waiting for the updates version on pfSense too. Squid 3.5 in my usage slowed down the Internet rather than helping it speed up through caching.
-
This post is deleted!